So long, Sonos: Meet the open-source audio system that will never die

The "official" distribution would always be available to the consumer should they decide to override the shipping firmware from the PiLe manufacturer. This would be a fallback in the event the manufacturer decided to end support for the device, becomes insolvent, or the customer prefers to use different software, for whatever reason. The official AudioPiLe software distribution would not only have a kernel that supports the necessary device drivers, but it would also have a friendly web-based UI (and potentially an app). This would not be unlike what consumer Wi-Fi routers would have, such as those made by Linksys or NetGear. But instead of strictly Wi-Fi and networking menus and settings, this software would have settings for attached subscriber streaming services and intelligent agents, such as Amazon Alexa and Google Assistant. It would have any other menus required to support whatever hardware and features that are enabled on that particular PiLe, and it would allow the user to view and diagnose underlying connectivity issues on their AudioPiLe network.
Cisco study finds huge returns for companies investing in privacy

"Privacy and accountability are central to our data-driven innovation, and have become key differentiators for our brand. This research reinforces the fact that privacy is a critical investment for forward-looking companies," Caroline Louveaux, chief privacy officer for Mastercard, said in the survey. When it comes to data breaches, companies that had mature privacy policies reported steep decreases in the number of attacks and the severity. The report found that having mature and accountable processes to manage, control, and curate data seems to help organizations avoid and limit the impact of data breaches. The length of sales delays also was directly correlated to how sophisticated your privacy programs are. "The companies that are most advanced are more than twice as likely to not have been breached last year. Only 13% of enterprises didn't get breached if they were low on the privacy scale. If you were more mature on the privacy scale, 28% were not breached," Waitman said. "You're twice as likely to have a breach-free year if you invested in privacy. Going further, among those organizations, they had less down time from breaches, with 19% less downtime, 28% fewer records breached and total breach costs down 10%."

The algorithm follows the theme of gatekeeper training but chooses the right people for the role through AI. “The idea is for our algorithm to help improve an intervention that is already being used for suicide prevention. It’s the most popular suicide-prevention intervention. It is often referred to with the initials QPR— question, persuade, refer," says Phebe Vayanos, assistant professor of industrial and systems engineering and computer science at the USC VSE. According to an official news release on the school’s website, Vayanos, also an associate director at the USC’s Center for Artificial Intelligence in Society, and PhD candidate Aida Rahmattalabi, the lead author of the study Exploring Algorithmic Fairness In Robust Graph Covering Problems, investigated the “potential of social connections such as friends, relatives, and acquaintances to help mitigate the risk of suicide". Their paper was presented at the Conference on Neural Information Processing Systems (NeurIPS) in Vancouver in December.
Digital transformation shaking confidence in SD-WAN
SD-WAN was found to do little for security. Although most respondents (66%) cite defending against malware/ransomware as a primary security challenge in 2020, only 37% claim their SD-WANs help protect locations from malware and other threats. This was despite most respondents (66%) prioritising defending against malware/ransomware. Secure mobile access, a strategic goal for IT executives, is ignored by SD-WAN. Managing mobile/remote access was the second most popular networking challenge for IT executives. More than half (52%) of respondents made enforcing corporate security policies on mobile users a primary security challenge for 2020. Yet, mobility is not included with SD-WAN. Most respondents (56%) consider SD-WAN as a way to reduce WAN costs, and network agility as it applies to sites – whether in the form of faster site deployment or increasing bandwidth – was also a popular outcome.
8 misleading AI myths — and the realities behind them

“The initial wave of AIOps did revolve our event management systems to perform noise reduction based on correlating alerts, like grouping of similar alerts,” said Ciaran Byrne, vice president of product strategy for OpsRamp, developer of AIOps software. This was a significant step forward, given that noise has long hindered the usability of event management systems. But even greater benefits are on the horizon. “The next wave has broadened to other areas of IT Operations such as automation and monitoring/observability,” Byrne said. “Use cases would include intelligent routing of tickets or automation based on learned patterns.” ... Early on, AIOps was perceived as being a “black box,” i.e. a mysterious system that generated output without providing insights into what the underlying algorithm did and why. However, over time we are seeing these solutions mature, and more “white box” approaches that are gaining trust and adoption. “While some systems don’t provide transparency, increasingly software vendors and AI systems are providing more visibility into why they did what they did,” said OpsRamp’s Byrne.
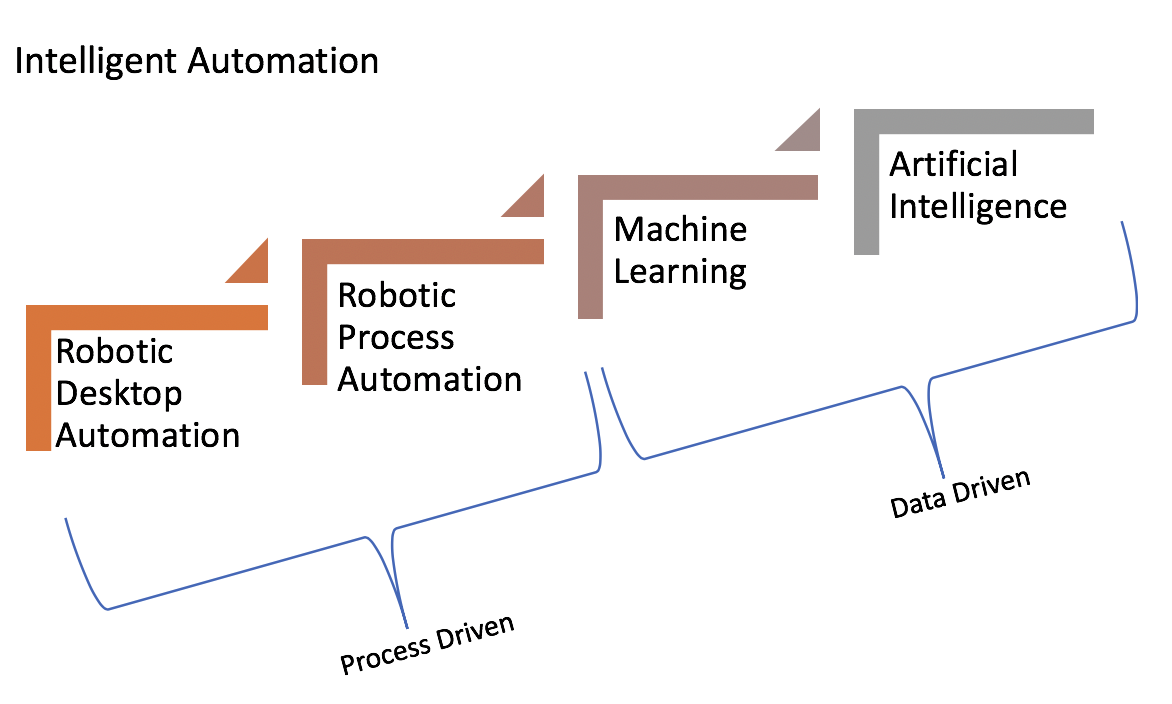
Intelligent Automation is a term that can be applied to the more sophisticated end of the automation-aided workflow continuum consisting of Robotic Desktop Automation, robotic process automation, machine learning, and artificial intelligence. Depending on the type of business, companies will often employ one or more types of automation to achieve improved efficiency and effectiveness. As you move along the spectrum from process-driven automation to more adaptable data-driven automation, there are additional costs in the form of training data, technical development, infrastructure, and specialized expertise. But the potential benefits in terms of additional insights and financial impact can be greatly magnified. To remain competitive and efficient, businesses now must contemplate adding machine learning and artificial intelligence to traditional RP in order to achieve intelligent automation. ... Current AI and machine learning models differ from human intelligence in part because they depend entirely on their initial training data and usually do not have an automatic and recursive mechanism to absorb and process new data for course correction i.e. continuous retraining.
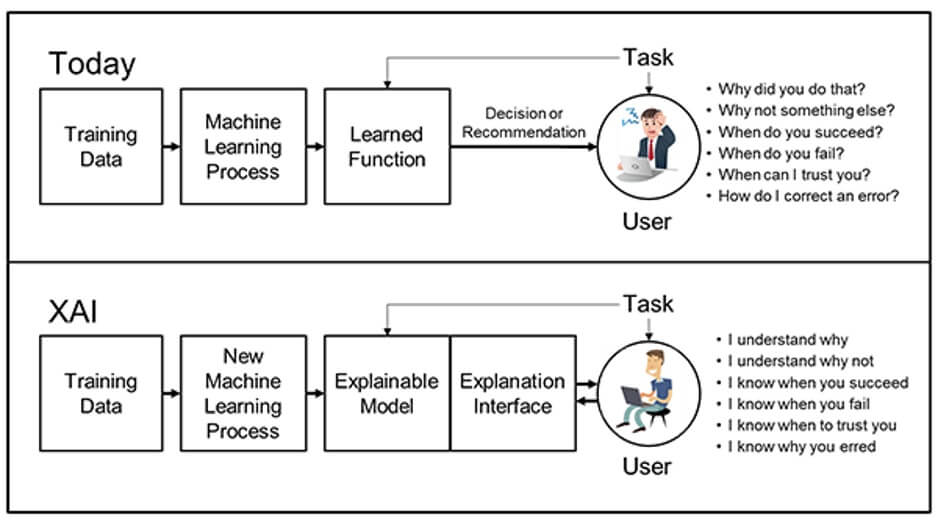
Ensuring that bias in algorithms and data sets is accounted for is only the first step. Engineers must be certain that AI systems are properly performing the tasks they claim to address, hopefully in the ways in which developers intended. In an ideal world, one could draw scrutable lines from characteristics of underlying data sets to the conclusions drawn from them. Nonetheless, increasingly complex algorithms often give rise to unexpected or even undesired results that cannot be traced back to their source. There is an argument to be made for some form of licensure being required in order to implement certain "black box"-style architectures, and perhaps outlawing them in the context of particular applications (e.g. military, pharmaceutical, criminal justice). The movement toward explainable AI (XAI) is rooted in precisely these concerns. DARPA has made strides toward establishing such a standard that paves the way for what they call "third-wave AI systems." There were a number of libraries and toolkits released in 2019 that exist to further the cause of XAI.
IoT security: Your smart devices must have these three features to be secure

Many connected devices are shipped with simple, default passwords which in many cases can't be changed, while some IoT product manufacturers often lack a means of being contacted to report vulnerabilities – especially if that device is produced on the other side of the world. In addition to this, it's been known for IoT products to suddenly stop receiving support from manufacturers, and by providing an exact length of time that devices will be supported will allow users to think about how secure the product will be in the long-term. If products don't follow these rules, the new law proposes that these devices could potentially be banned from sale in the UK. "Whilst the UK Government has previously encouraged industry to adopt a voluntary approach, it is now clear that decisive action is needed to ensure that strong cyber security is built into these products by design," said Warman. "Our new law will hold firms manufacturing and selling internet-connected devices to account and stop hackers threatening people's privacy and safety. It will mean robust security standards are built in from the design stage and not bolted on as an afterthought," he added.
Met Police to launch facial recognition operationally

“This is an important development for the Met and one which is vital in assisting us in bearing down on violence. As a modern police force, I believe that we have a duty to use new technologies to keep people safe in London,” said assistant commissioner Nick Ephgrave. “We are using a tried-and-tested technology, and have taken a considered and transparent approach to arrive at this point. Similar technology is already widely used across the UK, in the private sector. Ours has been trialled by our technology teams for use in an operational policing environment.” The MPS said the technology, which is provided by Japan’s NEC Corporation, will be deployed in locations where “intelligence suggests we are most likely to locate serious offenders”, and that the cameras will be focused on small, targeted areas to scan passers-by.
AutoInsights: Leveraging a platforms approach

For a picture of what this translates to in terms of everyday business, consider the Wipro AutoInsights platform—a modern, connected vehicle platform designed to meet the needs of progressive auto Original Equipment Manufacturers (OEMs) and various stakeholders in their journey towards digital transformation offering connected experiences to their customers. Automotives have a long ownership lifecycle, on an average around 10 years. This brings an opportunity for automakers to provide services (as experiences) to their customers beyond just offering a great vehicle. These services have the potential to touch customers at every interaction, deliver an experience which is relevant to their needs and re-iterate the value of the automaker’s brand. Consumers are known to be drawn to brands which deliver on their needs consistently and AutoInsights offers a great platform for OEMs to do so.
Quote for the day:
"Coaching isn't an addition to a leader's job, it's an integral part of it." -- George S. Odiorne
No comments:
Post a Comment