Colmena, an Architecture for Highly-Scalable Web Services
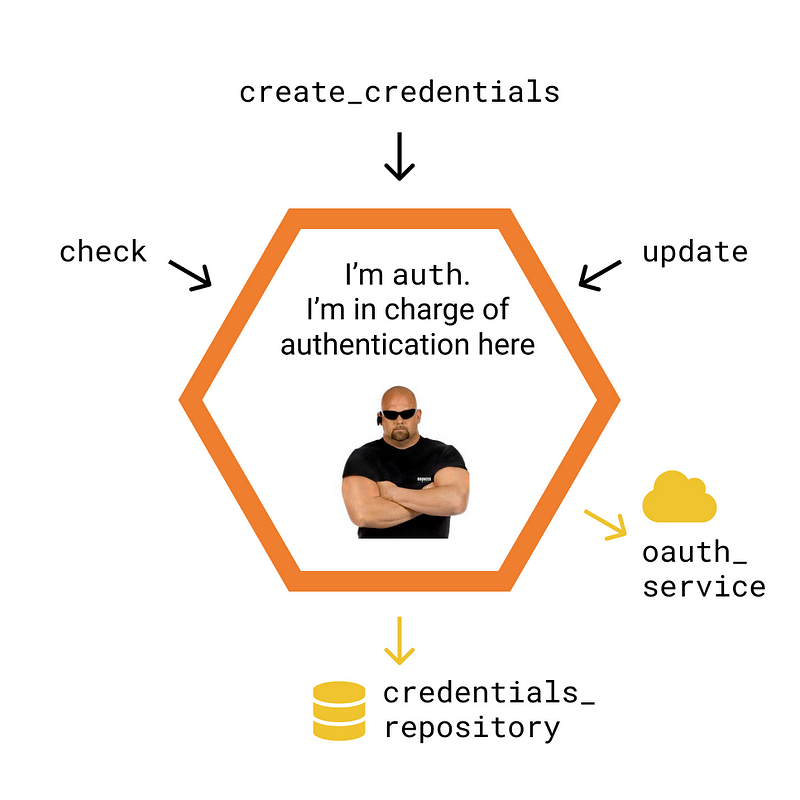
Cells are self-contained services that follow the hexagonal architecture. Each cell: Has a clear purpose and responsibility; Has some internal domain that represents, validates and transforms the cell’s state; Relies on a series of interfaces to receive input from (and send output to) external services and technologies; Exposes a public API (a contract stating what it can do). You can think of cells as very small microservices. In fact, we encourage you to try to make your cells as small as possible. In our experience, granulating your domain around entities and relationships helps you understand, test and maintain the codebase in the long run. In Colmena, changes to the domain are represented as a sequence of events. This sequence of events is append-only, as events are immutable (they are facts that have already taken place). In event sourcing, this sequence is called a “Source of truth”, and it provides: An audit log of all the actions that have modified the domain; The ability for other components (in the same or different cells) to listen to certain events and react to them.
How Millennials Should View the World of Data Science
So to summarize, here is what I feel MBA students (and business leaders) need to understand about the growing capabilities and power of Data Science: Data Science is a team sport that equally includes data engineers (who gather and prepare and enrich the data for advanced analytics), data scientists (who build analytic models that codify cause and effect and measure goodness of fit”), and business stakeholders; Embrace the “Thinking Like A Data Scientist” approach in order to determine what problems to target with data science and how to apply the resulting customer, product and operational insights to derive and drive business value; Understand how to collaborate with the data science team around the Hypothesis Development Canvas that cements the relationship between the organization’s business strategy and specific AI and Machine Learning efforts; and Gain a high-level understanding of “what” advanced analytic capabilities, such as deep learning, machine learning and reinforcement learning, can do in uncovering customer, product and operational insights buried in the organization’s data
Internet Explorer scripting engine becomes North Korean APT's favorite target in 2018
Microsoft became well aware of this component's security flaws many years ago. That's why, in July 2017, Microsoft announced that it was disabling the automatic execution of VBScript code in the latest IE version that was included with the Windows 10 Fall Creators Update, released in the fall of last year. That change meant that hackers couldn't use VBScript code to attack users via Internet Explorer in Windows 10. Microsoft also promised patches to disable VBScript code execution in IE versions on older Windows releases. That change stopped many cybercrime operations, but DarkHotel seems to have adapted to Microsoft's recent VBScript deprecation announcement. According to reports, DarkHotel apparently opted to use VBScript exploits embedded inside Office documents and did not target Internet Explorer users via the browser directly.
As part of the news conference, AMD acknowledged that Zen 4 is “in design,” meaning still on paper. Given Zen 3 is due in 2020, don’t figure on seeing Zen 4 until 2022 or so. Beyond that, the company said only it would offer higher performance and performance per watt when compared to prior generations. It’s been a good few weeks for AMD and EPYC. Last week, Oracle announced it would offer bare-metal instances on Epyc, and today Amazon Web Services (AWS) announced that Amazon Elastic Compute Cloud (EC2) will use Epyc CPUs, as well, so customers can get access today to instances running on the AMD processors. Intel noted that it, too, has an extensive relationship with AWS. So, now AMD has license deals with all of the major server vendors (HPE, Dell, Lenovo, Cisco) and almost all of the major cloud vendors. It had previously announced deals with Microsoft Azure and China’s Baidu and Tencent.
A foundational strategy pattern for analysis: MECE

MECE, pronounced "mee-see," is a tool created by the leading business strategy firm McKinsey. It stands for "mutually exclusive, collectively exhaustive," and dictates the relation of the content, but not the format, of your lists. Because of the vital importance of lists, this is one of the most useful tools you can have in your tool box. The single most important thing you can do to improve your chances of making a winning technology is to become quite good at making lists. Lists are the raw material of strategy and technology architecture. They are the building blocks, the lifeblood. They are the foundation of your strategy work. And they are everywhere. Therefore, if they are weak, your strategy will crumble. You can be a strong technologist, have a good idea, and care about it passionately. But if you aren’t practically perfect at list-making, your strategy will flounder and your efforts will fail. That’s because everything you do as you create your technology strategy starts its life as a list, and then blossoms into something else.
Many firms need more evidence of full benefits of artificial intelligence
Much of executives’ enthusiasm is justified. AI is already being deployed in a range of arenas, from digital assistants and self-driving cars to predictive analytics software providing early detection of diseases or recommending consumer goods based on shopping habits. A recent Gartner study finds that AI will generate $1.2 trillion in business value in 2018—a striking 70 percent increase over last year. According to Gartner, the number could swell to close to $4 trillion by 2022. This dramatic growth is likely reinforcing the perception among executives that such technologies can transform their respective industries. When looking at the external environment, encompassing economic, political, social, and other external developments that affect business, one-third of executives flagged positive technological disruption in their industry as a top opportunity.
Cylance researchers discover powerful new nation-state APT

The malware didn't just evade antivirus detection, however, it let itself be discovered by different antivirus vendors on preprogrammed dates, likely as a distraction tactic. "What we've got here in this case is a threat actor who has figured out how to determine what antivirus is running on your system and deliberately trigger it in an attempt to distract you," Josh Lemos, vice president of research and intelligence at Cylance, says. "That should be concerning organizations outside of Pakistan." Kill switches in malware have been seen before, such as in Stuxnet, but Cylance researchers say they've rarely seen a campaign that deliberately surrenders itself to investigators in this manner. "The White Company...wanted the alarm to sound," their report concluded. "This diversion was likely to draw the target's (or investigator's) attention, time and resources to a different part of the network. Meanwhile, the White Company was free to move into another area of the network and create new problems."
Firms lack responsible exec for cyber security
According to the report, although more people see the need for regular boardroom discussions about security, their organisations are failing to raise it sufficiently at the C-suite level. While 80% of all survey respondents agree that preventing a security attack should be a regular boardroom agenda item (up from 73% a year ago) only 61% say that it already is, which represents an increase of just 5% on last year. The report also suggests this lack of cohesion at the top of the organisation means that many are struggling to secure their most important digital assets. Fewer than half (48%) of respondents globally – 53% in the UK – say they have fully secured all of their critical data. But with the General Data Protection Regulation (GDPR) now fully in effect, this is no longer an opportunity, but mandatory, the report notes. However, companies are beginning to take control of their data as cloud computing best practices mature, with 27% reporting that the majority of their organisation’s data is currently stored on premise or in datacentres (25%).
Avoiding Business Stasis by Modernizing Ops, Architecture & More

Fear is inevitable during any modernization growth spurt. For instance, the operations team may fear that an increase in automation will lead to the loss of human expertise. Re-architecting the software may be perceived by developers as a threat to well-defined traditional team scopes and organizations. For the business owner, a poorly executed modernization takes away resources and doesn’t lead to improved agility. The concern many folks voice when they don’t know how to run or create a platform is that they don’t know what their place will be in the new organization. But what has started to become clear to those participating in our modernization effort is that their skills are being expanded — not replaced. And that enables them to take on new roles in the organization. One of the fundamental things that’s happening at StubHub is a complete change in the way we think about new ideas. The change in our stack allows us to work in any language and because we fully expect to move beyond Java and get into Go and Ruby and node.js, we can innovate and rethink our future in more ways than ever before.
C language update puts backward compatibility first

C is the foundation for many popular software projects such as the Linux kernel and it remains a widely used language, currently second in the Tiobe index. Its simplicity makes it a common choice for software applications that run at or close to bare metal, but developers must take extra care in C, versus higher-level languages like Python, to ensure that memory is managed correctly—easily the most common problem found in C programs. Previous revisions to the C standard added features to help with memory management—including the “Annex K” bounds-checking feature. However, one of the proposals on the table for C2x is to deprecate or remove the Annex K APIs, because their in-the-field implementations are largely incomplete, non-conformant, and non-portable. Alternative proposals include replacing these APIs with third-party bounds-checking systems like Valgrind or the Intel Pointer Checker, introducing refinements to the memory model, or adding new ways to perform bounds checking for memory objects.
Quote for the day:
"Leadership has a harder job to do than just choose sides. It must bring sides together." -- Jesse Jackson
No comments:
Post a Comment