“Enterprise Architecture As A Service” – What?

Recent success results in organizations having to deal with big decisions on ways to invest and maintain their success. Perceived failure results in a need to make decisions to address the failures. Each of these scenarios gets attention during the strategic planning process and, as pointed out in “Enterprise Architecture as Strategy” by Jeanne W. Ross, Peter Weill, and David Robertson, Harvard Business School Press, 2006, EA is a useful tool. The bottom line is that big decisions are looming and there is a perception that EA can help by defining “the organizing logic for business processes and IT Infrastructure, reflecting the integration and standardization requirements of the company’s operating model” so that “individual projects can build capabilities – not just fulfill immediate needs”. But there is another, less positive, perception out there – EA can be a money sink! It could result in tons of paper, take years, result in something outdated by the time it is finished, just to name a few concerns. Also the need for change has a timeline shorter than the perceived timeline of generating an Enterprise Architecture.
HTC’s blockchain phone is real, and it’s arriving later this year
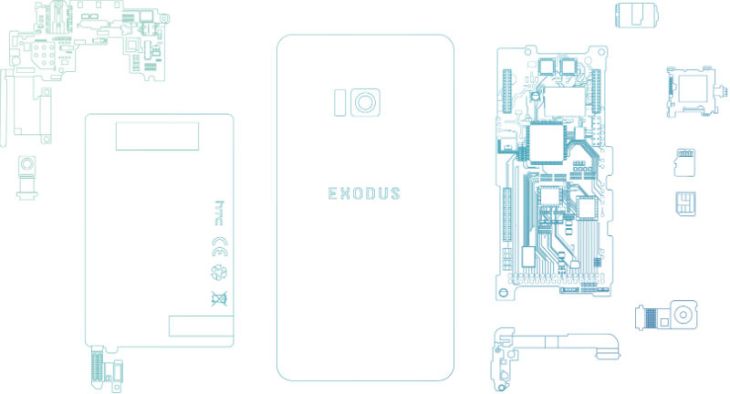
Prior to the launch, the company is partnering with the popular blockchain title, CryptoKitties. The game will be available on a small selection of the company’s handsets starting with the U12+. “This is a significant first step in creating a platform and distribution channel for creatives who make unique digital goods,” the company writes in a release tied to the news. “Mobile is the most prevalent device in the history of humankind and for digital assets and dapps to reach their potential, mobile will need to be the main point of distribution. The partnership with Cryptokitties is the beginning of a non fungible, collectible marketplace and crypto gaming app store.” The company says the partnership marks the beginning of a “platform and distribution channel for creatives who make unique digital goods.” In other words, it’s attempting to reintroduce the concept of scarcity through these decentralized apps. HTC will also be partnering with Bitmark to help accomplish this. If HTC is looking for the next mainstream play to right the ship, this is emphatically not it.
Interview: Bill Waid talks about AI ML
What is interesting about this well-known and often referenced use of AI/ML, is the potential opportunity cost. Despite the significant savings realized, the impact of declining a customer transaction that was not fraudulent leads to and even more costly unsatisfactory customer engagement and eventual attrition. To operationalize this AI/ML solution and fully realize the value, decisioning and a continuous improvement feedback loop was required. Capitalizing on the power of AI/ML, FICO has expanded both the algorithms and application of AI/ML to a broad set of solutions since 1992. Most notable is the use of ML to find predictive patterns in the ever-expanding Data Lakes our clients are collecting and using those ML findings to augment existing decisions and incrementally improve business outcomes. By deploying ML models in a way that the decision outcome could be managed and monitored to ensure accuracy, business owners could learn from the ML model and gain confidence that the model was indeed providing tangible improvement. This last innovation was a natural evolution to what FICO refers to as explainable AI (xAI).
How AI will change your healthcare experience (but won’t replace your doctor)

Techniques such as machine learning enable healthcare providers to analyze large amounts of data, allowing them to do more in less time, and supporting them with diagnosis and treatment decisions. For example, suppose you feed a computer program with a large amount of medical images that either show or do not show symptoms of a disease. The program can then learn to recognize images that may point towards the disease. For example, researchers at Stanford developed an algorithm that helps to evaluate chest X-rays to identify images with pneumonia. This doesn’t mean, however, that the radiologist will no longer be needed. Instead, think of AI as a smart assistant that will support doctors, alleviating their workload. This is also how we approach AI at Philips: we work together with clinicians to develop solutions that make their lives easier and improve the patient experience. That’s why we believe in the power of adaptive intelligence. It’s not really about AI per se – it’s about helping people with technology that adapts to their needs and extends their capabilities.
Machine learning will redesign, not replace, work
"Any manager could take this rubric, and if they're thinking of applying machine learning this rubric should give them some guidance," he said. "There are many, many tasks that are suitable for machine learning, and most companies have really just scratched the surface." ... Since a job is just a bundle of various tasks, it's also possible to use the rubric to measure the suitability of entire occupations for machine learning. Using data from the federal Bureau of Labor Statistics, that's exactly what they did—for each of the more than 900 distinct occupations in the U.S. economy, from economists and CEOs to truck drivers and schoolteachers. "Automation technologies have historically been the key driver of increased industrial productivity. They have also disrupted employment and the wage structure systematically," the researchers write. "However, our analysis suggests that machine learning will affect very different parts of the workforce than earlier waves of automation … Machine learning technology can transform many jobs in the economy, but full automation will be less significant than the reengineering of processes and the reorganization of tasks."
Reinventing The Enterprise - Digitally
Through autonomization and emergence, self-tuning firms create significant advantages. They can better understand customers by leveraging data from their own ecosystems and platforms to develop granular insights and automatically customize their offerings. They can develop more new, marketable products by experimenting with offerings and leveraging proprietary data. And they can implement change more quickly and at lower cost by acting autonomously. The benefits of autonomization and emergence well exceed those that can be realized from digitization programs aiming to increase efficiency or product innovation alone. They are compounded by self-reinforcing network and experience effects: better offerings attract more customers and more data; experimentation brings knowledge that increases the value of future experimentation. One example of a self-tuning organization is Alibaba. Not only does its e-commerce platform provide a sea of user data, but the company uses it to generate real-time insights in a granular manner.
Two studies show the data center is thriving instead of dying

The top reasons for such investment are security and application performance (75% of respondents) and scalability (71%). It also found that 53% of respondents intend to increase investment in software-defined storage, 52% in NAS and 42% in SSD ... IHS noted that new technologies such as artificial intelligence and containers are gaining traction, traditional data center apps, such as Microsoft Office (22%), collaboration tools such as email, SharePoint, and unified communications (18%), and general-purpose IT apps (30%) are still being used. The second survey comes from SNS Telecom & IT, a market research firm based in Dubai, UAE. It attributes the growth in big data and the subsequent massive inflow of all sorts of unstructured data as the reason for investment in IT equipment by the financial services industry. “As this Big Data construct expands to include streaming and archived data along with sensor information and transactions, the financial sector continues its steady embrace of big data analytics for high-frequency trading, fraud detection and a growing list of consumer-oriented applications,” said the authors.
Despite the security measures you've taken, hacking into your network is trivial
Closing security vulnerabilities and establishing effective cybersecurity policies and procedures is going to require more than just better technology. Effective security will demand a complete change of attitude by every employee, executive, and individual operating a computing device. Security must become the priority, even at the expense of convenience. Confirming results reported in other studies, the Positive Technologies research showed that more than a quarter of employees still inexplicably clicked a malicious link sent to them in an email. Despite extensive training and retraining, employees--regardless of industry or level of technical knowledge--continue to operate with an almost unconscious lack of security awareness. Until this cavalier attitude toward protecting company data changes, phishing attacks and authentication circumvention will continue to plague the modern enterprise.
The Economics Of AI - How Cheaper Predictions Will Change The World

Key to this, they argue, will be whether human AI “managers” can learn to differentiate between tasks involving prediction, and those where a more human touch is still essential. When I met with Joshua Gans – professor of strategic management and holder of the Jeffrey S Skoll Chair of Technical Innovation and Entrepreneurship at the University of Toronto – he gave me some insight into how economists are tackling the issues raised by AI. "As economists studying innovation and technological change, a conventional frame for trying to understand and forecast the impact of new technology would be to think about what the technology really reduces the cost of," he tells me. "And really its an advance in statistical methods – a very big advance – and really not about intelligence at all, in a way a lot of people would understand the term ‘intelligence.' ... “When I look up at the sky and see there are grey clouds, I take that information and predict that it’s going to rain. When I’m going to catch a ball, I predict the physics of where it’s going to end up. I have to do a lot of other things to catch the ball, but one of the things I do is make that prediction.”
Creating a Defensible Security Architecture
Controls should not only face the Internet but implemented to secure authorized access from internal assets to internal assets. Basic adjustments such as this allow for far superior prevention controls and, more importantly, detection controls. Think about this for a moment: If a computer on a subnet or zone A attempts to talk to any system found in zone B and the system from A is not allowed, then the connection will be denied, and you will be notified of that. Basic firewall rules aren't rocket science, but they are highly effective controls. Modern challenges also must be overcome. For instance, consider an intrusion detection/prevention device, web proxy, data loss prevention sensor, network antivirus, or any other Layer 7 network inspection solution. These are all crippled by network encryption. Your brand-new shiny NGFW may not be configured to handle 70%+ of the traffic going through it. Basically, without understanding technologies like Secure Sockets Layer (SSL) inspection, SSL decrypt mirroring, HTTP Strict Transport Security (HSTS), certificate transparency, HTTP Public Key Pinning (HPKP), how can you handle modern encryption?
Quote for the day:
"Technology makes it possible for people to gain control over everything, except over technology." -- John Tudor
No comments:
Post a Comment