The NHI management challenge: When employees leave

Non-human identities (NHIs) support machine-to-machine authentication and
access across software infrastructure and applications. These digital
constructs enable automated processes, services, and applications to
authenticate and perform tasks securely, without direct human intervention.
Access is granted to NHIs through various types of authentications, including
secrets such as access keys, certificates and tokens. ... When an employee
exits, secrets can go with them. Those secrets – credentials, NHIs and
associated workflows – can be exfiltrated from mental memory, recorded
manually, stored in vaults and keychains, on removable media, and more.
Secrets that have been exfiltrated are considered “leaked.” ... An equally
great risk is that employees, especially developers, create, deploy and manage
secrets as part of software stacks and configurations, as one-time events or
in regular workflows. When they exit, those secrets can become orphans, whose
very existence is unknown to colleagues or to tools and frameworks. ... The
lifecycle of NHIs can stretch beyond the boundaries of a single organization,
encompassing partners, suppliers, customers and other third parties.
How Ernst & Young’s AI platform is ‘radically’ reshaping operations

We’re seeing a new wave of AI roles emerging, with a strong focus on
governance, ethics, and strategic alignment. Chief AI Officers, AI governance
leads, knowledge engineers and AI agent developers are becoming critical to
ensuring that AI systems are trustworthy, transparent, and aligned with both
business goals and human needs. Additionally, roles like AI ethicists and
compliance experts are on the rise, especially as governments begin to
regulate AI more strictly. These roles go beyond technical skills — they
require a deep understanding of policy, ethics, and organizational strategy.
As AI adoption grows, so too will the need for individuals who can bridge the
gap between the technology and the focus on human-centered outcomes.” ...
Keeping humans at the center, especially as we approach AGI, is not just a
guiding principle — it’s an absolute necessity. The EU AI Act is the most
developed effort yet in establishing the guardrails to control the potential
impacts of this technology at scale. At EY, we are rapidly adapting our
corporate policies and ethical frameworks in order to, first, be compliant,
but also to lead the way in showing the path of responsible AI to our
clients.
The Truth Behind the Star Health Breach: A Story of Cybercrime, Disinformation, and Trust

The email that xenZen used as “evidence” was forged. The hacker altered the
HTML code of an email using the common “inspect element” function—an easy
trick to manipulate how a webpage appears. This allowed him to make it seem as
though the email came directly from the CISO’s official account. ... XenZen’s
attack demonstrates how cybercriminals are evolving. They are using
psychological warfare to create chaos. In this case, xenZen not only exploited
a vulnerability but also fabricated evidence to frame the CISO. The security
community needs to stay vigilant and anticipate attacks that may target not
just systems but also individuals and organizations through disinformation.
... Making the CISO a scapegoat for security breaches without proper evidence
is a growing concern. Organizations must understand the complexities of
cybersecurity and avoid jumping to conclusions. Security teams should have the
support they need, including legal protection and clear communication
channels. Transparency is essential, but so is the careful handling of
internal investigations before pointing fingers.
How CIOs and CTOs Are Bridging Cross-Functional Collaboration

Ashwin Ballal, CIO at software company Freshworks, believes that the
organizations that fail to collaborate well across departments are leaving
money on the table. “Siloed communications create inefficiencies, leading to
duplicative work, poor performance, and a negative employee experience. In my
experience as a CIO, prioritizing cross-departmental communication has been
essential to overcoming these challenges,” says Ballal. His team continually
reevaluates the tech stack, collaborating with leaders and users to confirm
that the organization is only investing in software that adds value. This
approach saves money and helps keep employees engaged by minimizing their
interactions with outdated technology. He also uses employees as product beta
testers, and their feedback impacts the product roadmap. ... “My
recommendation for other CIOs and CTOs is to regularly meet with departmental
leaders to understand how technology interacts across the organization.
Sending out regular surveys can yield candid feedback on what’s working and
what isn’t. Additionally fostering an environment where employees can
experiment with new technologies encourages innovation and problem-solving.”
2025 Is the Year of AI PCs; Are Businesses Onboard?

With the rise of real-time computing needs and the proliferation of IoT
devices, businesses are realizing the need to move AI closer to where the data
is - at the edge. This is where AI PCs come into play. Unlike their
traditional counterparts, AI PCs are integrated with neural processing units,
NPUs, that enable them to handle AI workloads locally, reducing latency and
providing a more secure computing environment. "The anticipated surge in AI
PCs is largely due to the supply-side push, as NPUs will be included in more
CPU vendor road maps," said Ranjit Atwal, senior research director analyst at
Gartner. NPUs allow enterprises to move from reactive to proactive IT
strategies. Companies can use AI PCs to predict IT infrastructure failures
before they happen, minimizing downtime and saving millions in operational
costs. NPU-integrated PCs also allow enterprises to process AI-related tasks,
such as machine learning, natural language processing and real-time analytics,
directly on the device without relying on cloud-based services. And with
generative AI becoming part of enterprise technology stacks, companies
investing in AI PCs are essentially future-proofing their operations,
preparing for a time when gen AI capabilities become a standard part of
business tools.
Australia’s Cyber Security Strategy in Action – Three New Draft Laws Published
Australia is following in the footsteps of other jurisdictions such as the
United States by establishing a Cyber Review Board. The Board’s remit will be
to conduct no-fault, post-incident reviews of significant cyber security
incidents in Australia. The intent is to strengthen cyber resilience, by
providing recommendations to Government and industry based on lessons learned
from previous incidents. Limited information gathering powers will be granted
to the Board, so it will largely rely on cooperation by impacted businesses.
... Mandatory security standards for smart devices - The Cyber Security Bill
also establishes a framework under which mandatory security standards for
smart devices will be issued. Suppliers of smart devices will be prevented
from supplying devices which do not meet these security standards, and will be
required to provide statements of compliance for devices manufactured in
Australia or supplied to the Australian market. The Secretary of Home Affairs
will be given the power to issue enforcement notices (including compliance,
stop and recall notices) if a certificate of compliance for a specific device
cannot be verified.
The Role of Zero Trust Network Access Tools in Ransomware Recovery

By integrating with existing identity providers, Zero Trust Network Access
ensures that only authenticated and authorized users can access specific
applications. This identity-driven approach, combined with device posture
assessments and real-time threat intelligence, provides a robust defense
against unauthorized access during a ransomware recovery. Moreover, ZTNA’s
application-layer security means that even if a user’s credentials are
compromised, the attacker would only gain access to specific applications
rather than the entire network. This granular access control is crucial in
containing ransomware attacks and preventing lateral movement across the
network. ... As a cloud-native solution, ZTNA can easily scale to meet the
demands of organizations of all sizes, from small businesses to large
enterprises. This scalability is particularly valuable during a ransomware
recovery, where the need for secure access may fluctuate based on the number
of systems and users involved. ZTNA’s flexibility also allows it to integrate
with various IT environments, including hybrid and multi-cloud
infrastructures. This adaptability ensures that organizations can deploy ZTNA
without the need for significant changes to their existing setups, making it
an ideal solution for dynamic environments.
What Is Server Consolidation and How Can It Improve Data Center Efficiency?

Server consolidation is the process of migrating workloads from multiple
underutilized servers into a smaller collection of servers. ... although
server consolidation typically focuses on consolidating physical servers, it
can also apply to virtual servers. For instance, if you have five virtual
hosts running on the same physical server, you might consolidate them into
just three or virtual hosts. Doing so would reduce the resources wasted on
hypervisor overhead, allowing you to maximize the return on investment from
your server hardware. ... To determine whether server consolidation will
reduce energy usage, you’ll have to calculate the energy needs of your
servers. Typically, power supplies indicate how many watts of electricity they
supply to servers. Using this number, you can compare how energy requirements
vary between machines. Keep in mind, however, that actual energy consumption
will vary depending on factors like CPU clock speed and how active server CPUs
are. So, in addition to comparing the wattage ratings on power supplies, you
should track how much electricity your servers actually consume, and how that
metric changes before and after you consolidate servers.
How DDoS Botent is used to Infect your Network?
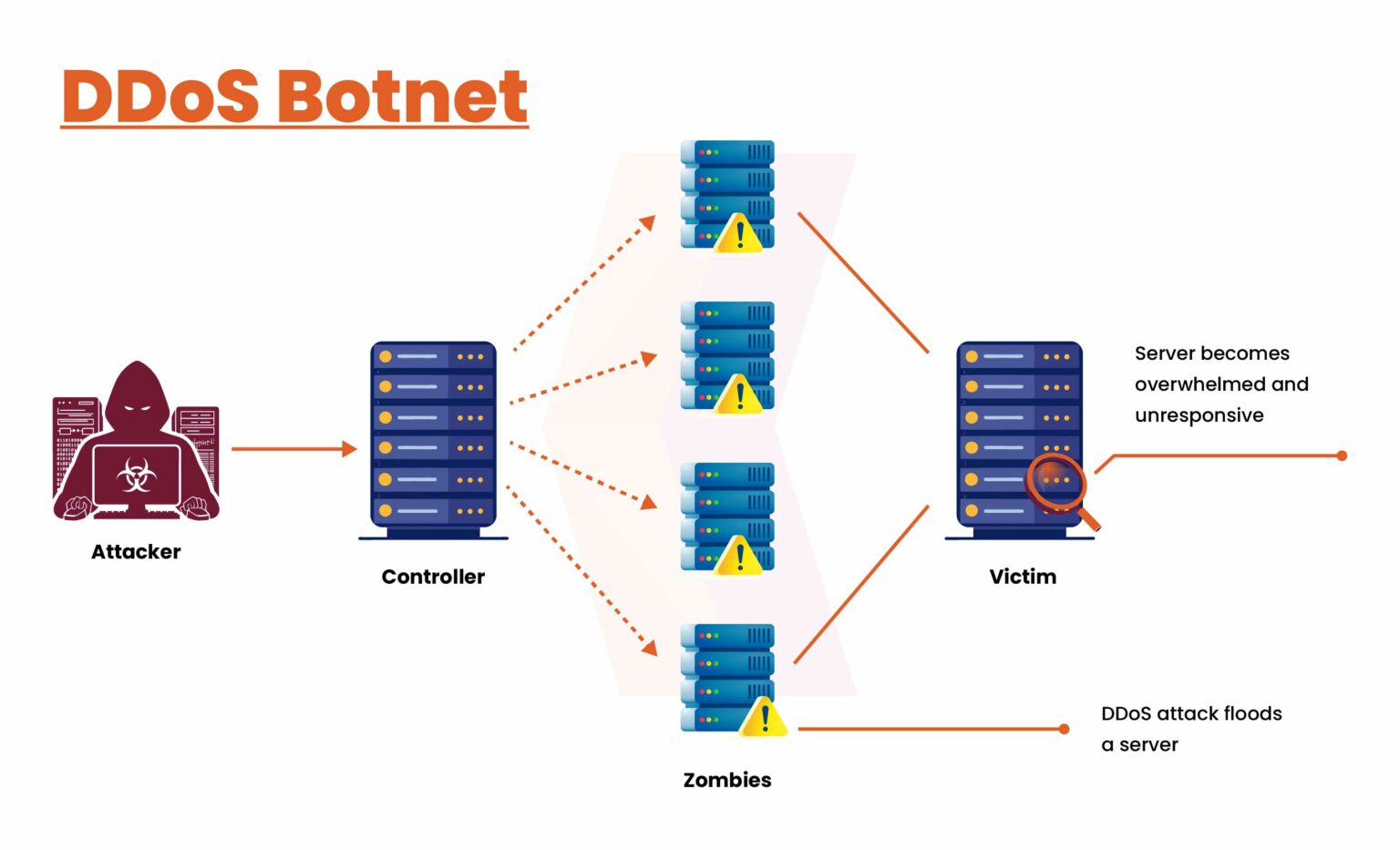
The threat posed by DDoS botnets remains significant and complex. As these
malicious networks grow more sophisticated, understanding their mechanisms and
potential impacts is crucial for organizations. DDoS botnets not only
facilitate financial theft and data breaches but also enable large-scale spam
and phishing campaigns that can undermine trust and security. To effectively
defend against these threats, organizations must prioritize proactive
measures, including regular updates, robust security protocols, and vigilant
monitoring of network activity. By implementing strategies to identify and
mitigate botnet attacks, businesses can safeguard their systems and data from
potential harm. Ultimately, a comprehensive understanding of how DDoS botnets
operate—and the strategies to combat them—will empower organizations to
navigate the challenges of cybersecurity and maintain a secure digital
environment. As a CERT-In empanelled organization, Kratikal is equipped to
enhance your understanding of potential risks. Our manual and automated
Vulnerability Assessment and Penetration Testing (VAPT) services proficiently
discover, detect, and assess vulnerabilities within your IT
infrastructure.
Banks Must Try the Flip Side of Embedded Finance: Embedded Fintech

With a one-way-street perspective on embedded finance, the idea is that if
payment volume is moving to tech companies then banks should power the back
end of the tech experience. This is a good start but the threat from fintech
companies to retail banks will only continue to deepen in the future. Customer
adoption is higher than ever for some fintechs like Chime and Nubank, for
example. A better approach would be for banks to use embedded fintech to
improve customer experience by upgrading banks’ tech offerings to retain
customers and grow within their customer base. Embedded fintech can help these
organizations stay competitive technologically. ... There are many
opportunities for innovation with embedded payroll. Banks are uniquely
positioned to offer tailored payroll solutions that map to what small
businesses today want. Payroll is complex and needs to be compliant to avoid
hefty penalties. Embedded payroll lets banks offload costs, burdens and risks
associated with payroll. Banks can offer faster payroll with less risk when
they hold the accounts for employers and payees. They can also give business
customers a fuller picture of their cash flow, offering them peace of
mind.
Quote for the day:
"Pull the string and it will follow
wherever you wish. Push it and it will go nowhere at all." --
Dwight D. Eisenhower
No comments:
Post a Comment