Embrace and extend Excel for AI data prep
Google has come out with a Chrome extension called GPT for Sheets, which allows
users to manipulate data with conversational language; Microsoft says it will
integrate ChatGPT into all of its products, with Bing first. Microsoft recently
invested $10 billion in OpenAI, the creators of ChatGPT. But as exciting (and
sometimes disappointing) as ChatGPT applications may be, there’s a much more
mundane—and promising—approach to machine learning that’s already available. ...
This is the technical process of converting data from one format, standard, or
structure to another, without changing the content of the data sets, in order to
prepare it for consumption by a machine learning model. Data prep is the
equivalent of janitorial work, albeit incredibly important work. Transformation
increases the efficiency of business and analytic processes, and it enables
businesses to make better data-driven decisions. But it’s difficult and
time-consuming unless the user is familiar with Python or the popular query
language SQL.
Digital forensics and incident response: The most common DFIR incidents

SOCs already make use of automation as much as possible, as they need to deal
with telemetry, but automation for digital forensics is different, as it mostly
needs data processing by orchestrating, performing and monitoring forensic
workflows. Half of DFIR professionals indicate that investments in automation
would be greatly valuable for a range of DFIR functions, as workflows still rely
too much upon the manual execution of many repetitive tasks. More than 20% of
the survey respondents indicated automation would be mostly valuable for the
remote acquisition of target endpoints, the triage of target endpoints, and
processing of digital evidence, as well as documenting, summarizing and
reporting on incidents. ... A field under such rapid evolution needs informed
and decisive leadership to set strategies and direct resources in an efficient
way. Leaders influence the way DFIR professionals can efficiently access data
sources they need, which is often difficult, as more than a third of the survey
respondents indicated.
DDoS Attacks Becoming More Potent, Shorter in Duration

Microsoft says TCP reflected amplification attacks are becoming more prevalent
and powerful, and more diverse types of reflectors and attack vectors are
typically exploiting "improper TCK stack implementation in middleboxes, such as
firewalls and deep packet inspection devices." In reflection attacks, attackers
spoof the IP address of the target to send a request to a reflector, such as an
open server or middlebox, which responds to the target, such as a virtual
machine. The latest TCP reflected amplification attacks can reach "infinite
amplification" in some cases. In April 2022, a reflected amplified SYN+ACK
attack on an Azure resource in Asia reached 30 million packets per second and
lasted 15 seconds. "Attack throughput was not very high, however there were 900
reflectors involved, each with retransmissions, resulting in high pps rate that
can bring down the host and other network infrastructure," the report says.
How the Economic Downturn Has Affected Security Funding, M&A
"The first thing that happens when you go into a down economic cycle is:
Everybody goes on defense," Ackerman says. "They rationalize the platform, make
sure it's stable and right-size for the market. Once that foundation is
established, then they go on offense. I think you're going to see an
acceleration of M&A activity by the big guys as they get through this
consolidation and rationalization process." DeWalt expects industrial control
systems and OT security to get lots of attention from the investment community
in 2023 given the technology's lack of penetration and volume of attacks against
industrial, non-IT networks. Network and infrastructure security had the
fifth-highest level of M&A and financing activity in 2022, including a $125
million Series C funding round for critical infrastructure firm Fortress. DeWalt
says the Russia-Ukraine war has led to increased attention on data management as
data wipers, data poisoning and the poisoning of AI algorithms become ways to
foment misinformation and disinformation.
Yes, Virginia, ChatGPT Can Be Used to Write Phishing Emails

Script kiddies in particular have been asking if ChatGPT might help them build
better malware for free. Results have been extremely mixed. "Right now, I
think it's a novelty," says John Kindervag, creator of zero trust and senior
vice president of cybersecurity strategy at ON2IT Group. But as AI gets
better, he says, "probably it will allow the attackers to craft more
sophisticated attacks, and it will toast everybody who is not paying
attention." So far, at least, the fervor over AI chatbots being used to build
a better cybercrime mousetrap is claptrap, says security researcher Marcus
Hutchins, aka MalwareTech. ... Criminals needn't bother to use AI chatbots,
which are trained on publicly available code. Instead, they can go to the
source. "If someone with zero coding ability wants malware, there are
thousands of ready-to-go examples available on Google" and GitHub, Hutchins
says. Another rising concern is that criminals will use AI chatbots to craft
better phishing email lures, especially outside their native language.
The Evolution of APIs: From RESTful to Event-Driven
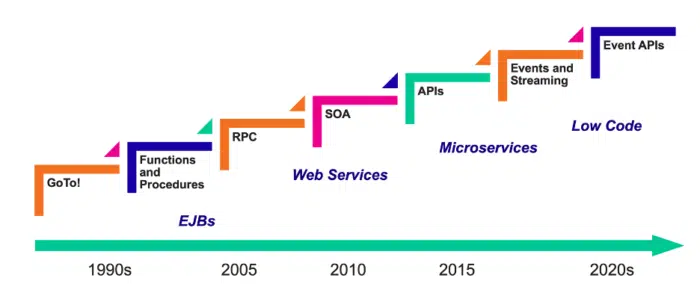
Synchronous microservice limitations can be overcome through asynchronous
interaction, event-driven architecture, and event-enabling traditional
microservices. Taking advantage of the constant flow of business and technical
events by acting on them promptly. As awareness of the importance of events
and event-driven architecture (EDA) grows, architects and developers are
exploring ways to integrate events into microservices. However, successful
adoption of EDA also requires a change in mindset and approach from business
stakeholders, product owners, and architects. This shift involves moving from
a data-centric approach to one that uses events to drive business decisions
and logic. Full event-native adoption is necessary to fully leverage the
benefits of events throughout the various stages of the business. Modern APIs
are predominantly based on microservices, but events and event-driven
architecture (EDA) are becoming increasingly important. The future of APIs
lies in combining the strengths of APIs and EDA to create
Event-Driven-APIs.
Scotland launches data strategy for health and social care

Carol Sinclair, chair of the Scottish government’s data board for health and
social care, said in the strategy’s foreword that the aim is to “empower
citizens and staff” through ensuring data supports the delivery of health and
social care services. “Public trust and the ethical use of data for public
good is central to this strategy,” she said. “We are working alongside
colleagues across government to ensure the principles of Open Government are
followed as we define and publish key, ethically sound and publicly trusted
principles to support the unlocking of the social and economic value
associated with the use of public sector personal data in the service of the
people of Scotland.” For health and social care staff, the strategy aims to
improve discoverability, accessibility, interoperability and reusability,
making it easier to access data across organisations. The Scottish government
is already working on the replacement of the Community Health Index (CHI)
system, a platform which has been in place since the 1970s.
How to Have More Effective Conversations With Business Stakeholders About Software Architecture
One big barrier to effective conversations about technical decisions that need
business input is that development teams and business stakeholders speak
different languages. To be more precise, when techies talk about technology,
business people tune out. What they need to do is frame discussions in terms
of how technical choices will affect business outcomes - something business
stakeholders do care about. ... The metaphor helps, to a point, but an even
better approach is to describe how addressing a technical issue will enable
the organization to achieve a business outcome that they could not otherwise
do. Or how not addressing a technical issue will impair the business outcomes
that the organization can achieve. This conversation works both ways. When
there is a major shift in business priorities, such as the organization
deciding to exit a specific market, or needing to respond to regulatory
mandates, describing the shift in terms of business outcomes helps everyone
understand the impact.
6 precautions for CIOs to consider about ChatGPT

“The success of ChatGPT in a consumer capacity is clear. And since its
language model is effectively trained on all the text on the web, the output
is so fluent that it can be challenging, if not impossible, to decipher
whether the author is human or a bot. But in a higher-stakes enterprise
context, the fluency of the response creates a false sense of trust for the
user: It looks right. It sounds right. But if you run the numbers, it might be
wrong. When you’re trying to make your friends laugh, accuracy doesn’t matter
at all. But when trying to make a decision that could impact lives and
livelihoods, that unreliability can have catastrophic consequences. In a
sense, ChatGPT is similar to Google Translate. While Google Translate is great
for travel and other casual use cases, an enterprise won’t trust it to
faithfully translate their marketing materials for new geographies or their
contracts for international agreements. The stakes are just too high to gamble
on a statistical model. Successful applications will require organizations to
train and fine-tune a model like ChatGPT on proprietary enterprise information
to help it interpret and produce the “language” used within that organization.
'New Class of Bugs' in Apple Devices Opens the Door to Complete Takeover

The findings are another puncture wound in the perception that Apple devices
are somehow inherently more secure than PCs or Android devices. "Since the
first version of iOS on the original iPhone," Emmitt explained, "Apple has
enforced careful restrictions on the software that can run on their mobile
devices." The devices do this with code signing. Functioning somewhat like a
bouncer at a club, iPhone only allows an application to run if it has been
cryptographically signed by a trusted developer. If any entity — a developer,
hacker, etc. — wishes to run code on the machine, but they're not "on the
list," they'll be shut out. And "as macOS has continually adopted more
features of iOS," Emmitt noted, "it has also come to enforce code signing more
strictly." As a result of its strict policies, Apple has earned a reputation
in some corners for being particularly cyber secure. Yet that extra stringency
can only extend so far. "I think that there is a misconception when it comes
to Apple devices," says Mike Burch, director of application security for
Security Journey.
Quote for the day:
"To command is to serve : nothing
more and nothing less." -- Andre Marlaux
No comments:
Post a Comment