When ‘quick wins’ in data science add up to a long fail

The nature of the quick win is that it does not require any significant
overhaul of business processes. That’s what makes it quick. But a consequence
of this is that the quick win will not result in a different way of doing
business. People will be doing the same things they’ve always done, but
perhaps a little better. For example, suppose Bob has been operating a
successful chain of lemonade stands. Bob opens a stand, sells some lemonade,
and eventually picks the next location to open. Now suppose that Bob hires a
data scientist named Alice. For their quick win project, Alice decides to use
data science models to identify the best locations for opening lemonade
stands. Alice does a great job, Bob uses her results to choose new locations,
and the business sees a healthy boost in profit. What could possibly be the
problem? Notice that nothing in the day-to-day operations of the lemonade
stands has changed as a result of Alice’s work. Although she’s demonstrated
some of the value of data science, an employee of the lemonade stand business
wouldn’t necessarily notice any changes. It’s not as if she’s optimized their
supply chain, or modified how they interact with customers, or customized the
lemonade recipe for specific neighborhoods.
Reshaping retail banking for the next normal
 Given the analytical nature of digital marketing, required skill sets differ
vastly from “old-fashioned” marketing. Its teams more closely resemble Math Men
than Mad Men. Banks’ required growth levers include digital traffic generation,
existing customer engagement, and conversion. Leading digital banks leverage
multiple marketing channels and customize strategies to customer segments, in
combination with a sharp focus on developing truly exceptional customer
journeys. Adopt more tailored customer conversations, leveraging advanced
analytics and a multichannel approach. McKinsey research confirms that customers
who receive personalized bank offers across multiple channels are more than
three times as likely to accept, compared to those receiving offers via a single
channel. Successful banks typically apply advanced analytics to identify niches
of prudent growth, accurately predicting the best loan offer recipients, whose
credit lines to increase, and who needs asset allocation assistance, thereby
building stronger relationships while simultaneously helping customers optimize
their finances.
Given the analytical nature of digital marketing, required skill sets differ
vastly from “old-fashioned” marketing. Its teams more closely resemble Math Men
than Mad Men. Banks’ required growth levers include digital traffic generation,
existing customer engagement, and conversion. Leading digital banks leverage
multiple marketing channels and customize strategies to customer segments, in
combination with a sharp focus on developing truly exceptional customer
journeys. Adopt more tailored customer conversations, leveraging advanced
analytics and a multichannel approach. McKinsey research confirms that customers
who receive personalized bank offers across multiple channels are more than
three times as likely to accept, compared to those receiving offers via a single
channel. Successful banks typically apply advanced analytics to identify niches
of prudent growth, accurately predicting the best loan offer recipients, whose
credit lines to increase, and who needs asset allocation assistance, thereby
building stronger relationships while simultaneously helping customers optimize
their finances.Advancing Your Cybersecurity Program Past the Crisis

Fortunately, there is a security model that offers guidance for addressing
such risks. It is called Zero Trust. John Kindervag, who coined this term back
in 2010, explains that this paradigm “examines information about the device,
its current state, and who is using it” when making security decisions. As
described in the recent Zero Trust Architecture document by NIST, the idea is
to narrow the sphere of trust from large networks protected by a perimeter to
components, such as endpoints and users. Zero Trust, as NIST puts it, “is a
response to enterprise trends that include remote users and cloud-based
assets.” This is the very configuration you are supporting due to the
pandemic, so even if you weren’t sure how to begin your journey toward Zero
Trust, COVID-19 forced you to advance down this path even. When you get a
chance to shift focus from tactical to the strategic planning of your security
program, look at Zero Trust guidelines from the sources and people you trust.
... The business requirements of your organization today–remote workforce,
distributed endpoints, heavy reliance on SaaS and cloud services–likely
represent the ongoing needs of the enterprise.
Lamphone attack lets threat actors recover conversations from your light bulb

Having the ability to eavesdrop on corner offices from tens of meters away
with nothing but a telescope and a video recorder is a huge feat, and a
dangerous scenario for many companies. But Lamphone is not the first attack of
its kind. Other techniques have been explored in the past, such as Gyrophone
(using mobile device sensors to recover speech from gyroscope signals) and
Visual Microphone (using video recordings to recover passive sound).
Nonetheless, the research team says Lamphone has an advantage over these
attacks because it's passive and doesn't require infecting a victim's device
with malware (unlike Gyrophone) and works in real-time and doesn't need access
to vasts computational resources to process its recorded data (unlike Visual
Microphone). The research team says that all an attacker needs to process
Lamphone data is something as simple as a laptop, which, in turn, allows
threat actors to use Lamphone to follow conversations in real-time. A
disadvantage is that the attack doesn't work against all types of light bulbs
and that results may vary, depending on the light bulb's make, model, and
technical characteristics, such as its outer glass thickness or light emission
capability.
Artificial Intelligence Decodes Speech from Brain Activity: Study

The readout of brain activity and audio of the spoken sentences were input to
an algorithm, which learned to recognize how the parts of speech were formed.
The initial results were highly inaccurate, for instance, interpreting brain
activity from hearing the sentence “she wore warm fleecy woolen overalls” as
“the oasis was a mirage.” As the program learned over time, it was able to
make translations with limited errors, such as interpreting brain activity in
response to hearing “the ladder was used to rescue the cat and the man” as
“which ladder will be used to rescue the cat and the man.” “If you try to go
outside the [50 sentences used] the decoding gets much worse,” Makin explains
to The Guardian. The BBC describes the program as learning how to decode
individual words, not just the full sentences, which makes it more likely to
accurately decode speech in novel phrases going forward. The program also
increased its accuracy when going from one participant to the next,
demonstrating plasticity in learning from multiple people. While being able to
interpret limited sentences is a step forward, it is still a far cry from
mastering English as a whole, the authors admit. “Although we should like the
decoder to learn and exploit the regularities of the language,” the
researchers write in their paper, “it remains to show how many data would be
required to expand from our tiny languages to a more general form of English.”
Facial Recognition Bans: What Do They Mean For AI (Artificial Intelligence)?

Facial recognition has also been shown to be less effective when analyzing
videos and images of minorities. “As for the issues with this technology, a
study out of MIT last year found that all of the facial recognition tools had
major issues when identifying people of color,” said Michal Strahilevitz, who
is a professor of marketing at St. Mary's College of California. “Another
study out of the US National Institute of Standards and Technology suggested
facial recognition software had far more errors in attempting to recognize
black and Asian faces than it had in recognizing Caucasian ones. This means
that black and brown people are more likely to be inaccurately identified, and
thus unfairly targeted. This may not be intentional, but it ends up having a
racial bias that is dangerous and unethical.” Yet the debate over facial
recognition can certainly get complicated and may even lead to unintended
consequences. “The moves reflect a lack of popular understanding of the
technology–the public is conflating facial recognition with body recognition
and tracking, facial analysis, facial detection, gender/age/ethnicity
recognition, biometric validation, etc. as well as misunderstanding the
difference between the use case and the technology,” said Kjell Carlsson, who
is an analyst at Forrester.
Cybersecurity As A Career Option: Here's What You Should Know

There are many cybersecurity career tracks, including GRC, Auditors, incident
responders, SOC analysts, IoT security professionals, security software
developers, cloud security experts, cyber forensic experts and cybersecurity
trainers. For example, to become an auditor or a Governance, Risk management,
and Compliance (GRC) manager, you have to make sure you know each and every
component of the security infrastructure. “GRC is like an orchestra conductor.
He or she should have an understanding of all the security components, unlike
someone who is a cloud security expert or database security manager. Because
all the security components talk to each other. So, there should be a sharing
of security intelligence and incidence reports. An auditor or GRC compliance
manager should have competence and skills, cutting across all the domains. So,
it’s very challenging because you have to learn the technology as well as the
compliance process but coming up as a lucrative career,” according to
Tathagata Datta. The majority of the investment in terms of resourcing,
planning and training happens to prevent the attack.
Emerging Virtual Realities In Industry, Government And Academia

Virtual government is both growing and evolving in terms of providing citizens
services with accessibility to .gov websites and data sources. Much of the
communications relating to health or social security benefits are now being
automated by federal agencies. Many of the best practices are being adapted
from the private sector where technologies have already been proven for
communications, and data analytics. The way government does business can
change via virtual government. Virtual procurements can offer equal access and
accessibility for vendors. The virtual government procurement landscape could
also be more transparent and lessen protest on contracts and guard against
cronyism or potential conflicts of interest. There are a multitude of benefits
for virtual connectivity and interaction in academia. Covid19 forced an
emergency response for most academic institutions to change from physical
classes to digital classes in a short period of time. Many institutions of
higher learning were already offering students and alumni the opportunity to
learn online in subjects ranging from business, history, physics, to
psychology.
M1, Airbus to pilot 5G for unmanned flights

The two partners will collaborate alongside Infocomm Media Development
Authority (IMDA) and Maritime and Port Authority of Singapore (MPA) to conduct
the coastal trials, and will be run on M1's 5G standalone network at the
Singapore Maritime Drone Estate. The necessary permits and approvals first
would be acquired from the relevant agencies before any flight trials were
conducted, they said. Apart from providing the 4G and 5G network support, M1
would also collect data to assess the performance and coverage of mobile
network in the operating areas, as well as carry out network parameter
optimisation and the implementation of interference minimisation methods. The
telco also would evaluate the use of 4G and 5G technologies to facilitate
enhanced geo-location positioning for all phases of unmanned aircraft systems
flight using network-based data, which it said was more precise than current
Global Navigation Satellite Systems technologies. The telco would also assess
network performance enhancements in connection stability, uptime, and data
throughput when aggregating between 4G and 5G networks.
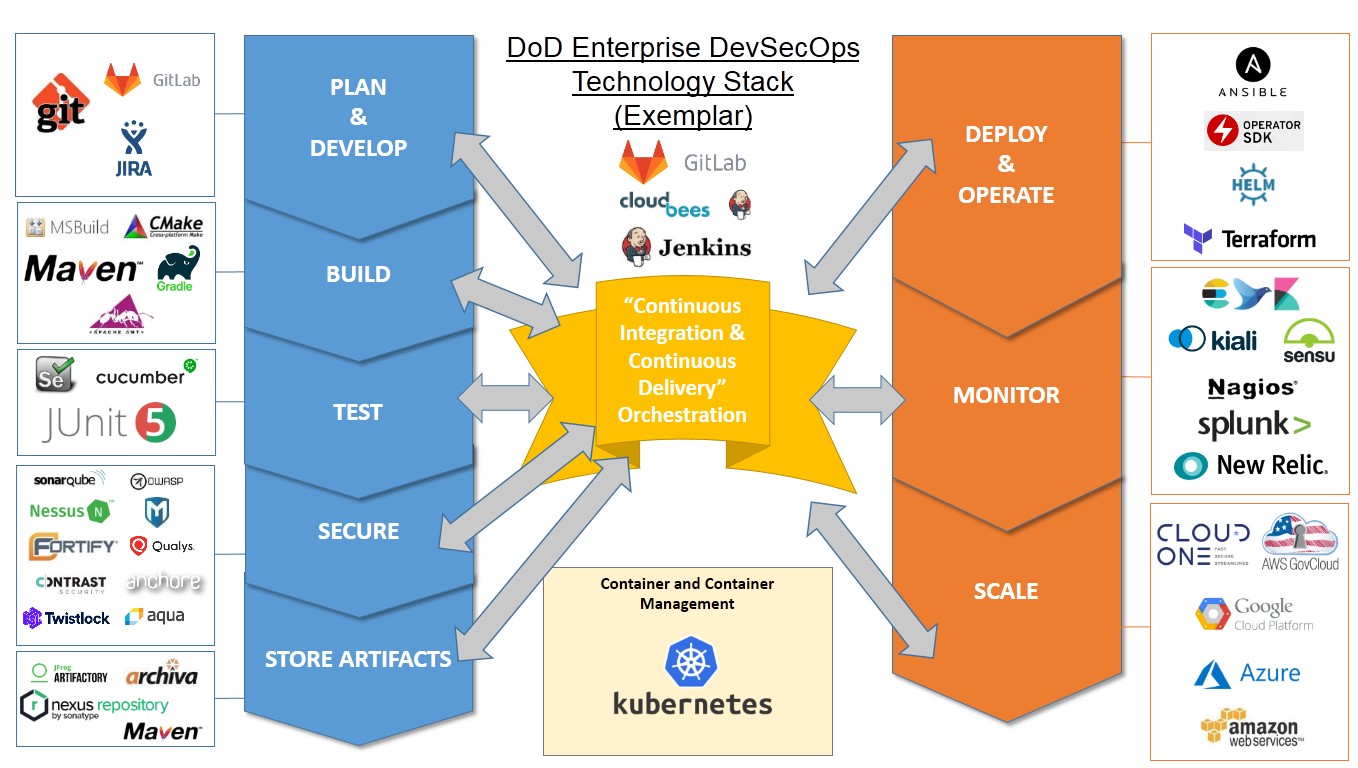
The Defense Department's Journey with DevSecOps

Cloud Native Computing Foundation has released a new case study of the
DoD's approach to DevSecOps that looks at how they used Kubernetes clusters
and other open-source technologies to speed up the releases. While most of
the information was already available from the DoD and in their
presentations, the CNCF has summarized the venture in one place. The
Department of Defense has created their Enterprise DevSecOps reference
design which defines the gates on the DevSecOps pipeline so that warfighters
can create, deploy and operate software applications in a secure, flexible
and interoperable manner. Releases, which once took as long as three to
eight months, now can be achieved in one week. DevSecOps is a set of
automated tools, services and standards that enable programs to develop,
secure, deploy and operate applications in a secure, flexible and
interoperable fashion. The DoD effort was spearheaded by Nicolas M.
Chaillan, chief software officer of the U.S. Air Force and Peter Ranks,
deputy chief information Officer for Information Enterprise, DoD CIO.
Quote for the day:
No comments:
Post a Comment