WiFi 6 will face 5G competition

The decision about whether to put your faith in WiFi 6, or look to 5G for IoT applications, or other use-cases where there is a high density of connected devices isn't easy. Both technologies offer faster connections than their predecessors along with the ability to support more concurrent devices. On the other hand, retro-fitting devices to support either of the new standards is a massive undertaking, and then there's question of which option is the best fit. In a recent interview, Qualcomm's Rasmus Hellberg said: "We looked at all the Wi-Fi access points we have today, Then we added in millimetre wave at the exact same points. It's a big opportunity to drive millimetre wave indoors as a private network". With the number of IoT devices forecast to increase rapidly over the next few years, businesses will need to consider how to link all of those devices to existing networks. WiFi 6 seems like a safe path for transitioning from existing WiFi 4 and WiFi 5 networks. But 5G could make tasks such as comms configurations easier. Once a SIM card is programmed correctly, simply installing it would allow for devices to connect almost instantly.
What Top Innovation Leaders in Banking Have in Common
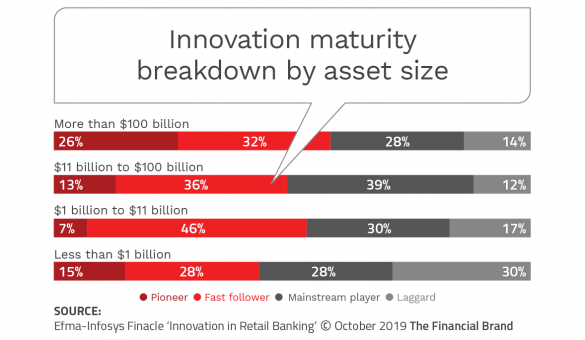
The increasing influence of non-traditional financial services companies has been driven by their ability to leverage new technology and data for an improved customer experience. According to the Innovation in Retail Banking 2019 research, as many as one-third of consumers across the world are now using at least one FinTech app, whether that’s peer-to-peer payments, financial planning, savings and investments, borrowing, or insurance. Consumers value these apps because they provide exceptional digital-first experiences, and because they seamlessly integrate with other apps that they are using. In other words, the battlefield has changed and legacy banking organizations need to respond. The most obvious way for traditional financial institutions to respond to new competition is to innovate ‘like a fintech’. While this may not be a ‘build from within’ solution, even a partnering opportunity can move the needle and either retain or acquire customers. The research done for the Innovation in Retail Banking 2019 report found that the most advanced innovators are acutely focused on improving the customer experience and are seeing results far superior than less advanced innovation firms.
Eight ways to secure your data on IoT devices

Before you get an IoT device or solution, first ensure that it is secure by design. This might not be feasible in some environments because of factors such as legacy products, price points or just because you don’t have enough details on how or if they are secured. You should reconsider acquiring an IoT device if the provider is unable to supply adequate information about the security approach of the device. In case, your IoT devices are already in place, security can be built around it. This is a usual occurrence in environments that has legacy products. You should also make sure that the manufacturer of your IoT device/s is able to provide timely patches and updates for the entire lifeline of the device. A lot of security vulnerabilities are revealed after the product has entered the market. As the lifetime for IoT devices can be as long as 10 to 20 years, its manufacturer should be able to provide you with its patches and updates for that duration. Following are the eight effective ways in which you can secure your data on IoT devices.
Analysis reveals the most common causes behind mis-issued SSL/TLS certificates
One of the conclusions that the researchers reached is that, as things stand now, Root Program’s owners have tremendous power in the PKI network and they should use it to penalize those CAs that put their welfare over that of the Public Key Infrastructure. “With just their independent decision they can end the business of a CA, especially if several Root Program’s owners are aligned with the revocation’s posture,” they noted. “Given that they are also the owners of the web browsers, they are judge, jury and executioner in the network. On the other hand, if a misbehavior is detected in a CA but not all the program’s owners agree with a mass removal of it, a removal by a sole owner may have a negative impact on this owner given the potential loss of customers that that decision may carry; therefore, if there is no consensus between Root Program’s owners, CAs may keep with their miss-practices.” They have also proposed several solutions for CAs and Root Program Owners to implement to improve trust in PKI.
Why the future of data security in the cloud is programmable

With the ability to monitor data access, govern it, and selectively protect data even from developers themselves wired into applications, there is another door that swings wide open: application portability. Many companies, from traditional manufacturing all the way to software companies themselves, are looking for ways to leverage the economics and flexibility of cloud infrastructure. For most of these companies, the number 1 and number 2 concerns as to going to infrastructure that they don’t control are security and compliance. But when a development team wires in tools to allow for the control of data regardless of where the application is deployed, the business is free to determine the best infrastructure for the application in question based on performance, cost, reliability and other IT priorities. Cloud options from platform-as-a-service all the way to serverless architecture, where IT doesn’t have to maintain any of the infrastructure stack, are all on the table. Through this lens the economic benefits of programmable data security come completely into focus. Adopting this approach, by way of example, ALTR has been able to help a business optimise its digital footprint based on delivery of technology services, not on the security of them.
Prayer Is Brexit Strategy as Services Brace for Red Tape Storm

“There is no fallback position as far as data is concerned, which is a bit of an oversight,” said Jack Bedell-Pearce, 4D’s CEO. You need to understand “how you’re going to be impacted when the rug is pulled from underneath your feet.” 4D helped survey businesses about data sovereignty — the location where data is stored — in the aftermath of the Brexit vote, and found that 87% were not looking at the issue. Judging by anecdotes, the figure is probably similar now, Bedell-Pearce said. Brexiteers have proclaimed that falling back on trade rules established by the Geneva-based World Trade Organization will be more than sufficient to ensure that the U.K. can continue to trade with Europe and the rest of the world. But the rules regarding services are particularly complicated and will provide less certainty to exporters. Further complicating matters is the fact the European Commission does not have exclusive authority over the EU’s internal services market as it does with goods under the customs union. That means each EU member state can impose their own services rules.
Microsoft Defender 'Tamper Protection' reaches general availability

Microsoft says that Tamper Protection "essentially locks Microsoft Defender" and prevents security settings from being changed through third-party apps and methods like: Configuring settings in Registry Editor on a Windows machine; Changing settings through PowerShell cmdlets; and Editing or removing security settings through group policies. The feature will be available for both the free version of Microsoft Defender (the one that ships with all modern Windows OS versions) but also with Microsoft Defender Advanced Threat Protection (ATP) (the commercial version, primarily employed on enterprise networks). Work on Tamper Protection began in December 2018, when it was first rolled out to Windows Insiders previews. In March this year, Microsoft rolled Tamper Protection for more tests to Microsoft Defender ATP versions. Starting today, the feature will be available for all Microsoft Defender users. Microsoft told ZDNet in a phone call last week that the feature will be enabled by default for all users in the coming weeks, in a multi-stage rollout. If users don't want to wait, Microsoft said they can also enable Tamper Protection right now.
Q&A on the Book Real-World Bug Hunting
The impact of an SQL injection vulnerability really depends on the information that a database contains. In the best case scenario, no harm is done because the database includes no sensitive information and is properly isolated for other sensitive systems. In the worst case scenario, SQL injection can be devastating if an attacker has access to extract large amounts of personally identifiable information, they can create administrative accounts for themselves on the application or can read local files from the server. An example of this is covered in the book: a SQL Injection in Drupal version 7 from 2015, which allowed for privilege escalation, arbitrary PHP execution, or other attacks depending on the configuration of the application. Content management systems and other development frameworks are only as secure as the developers creating web applications with them. It isn’t hard to introduce SQL injection vulnerabilities if you are mistakenly adding user controlled input to SQL statements. But that said, content management systems like Drupal and Wordpress and frameworks like Ruby on Rails do a great job of making it harder to introduce the vulnerability.
10 hot micro-data-center startups to watch

Data-hungry technology trends such as IoT, smart vehicles, drone deliveries, smart cities and Industry 4.0 are increasing the demand for fast, always-on edge computing. One solution that has emerged to bring the network closer to the applications generating and end users consuming that data is the micro data center. The micro data center sector is a new space filled with more noise than signal. If you go hunting for a micro data center for your business you’ll find everything from suitcase-sized computing stacks that replace a server closet to modular enclosures delivered by semi-trucks to larger units that reside at the foot of cell towers to dedicated edge data centers with standardized designs that can spring up wherever there’s demand and where real estate or access rights are available, including easements, rooftops and industrial sites. Several of the startups here started out in adjacent spaces, such as IaaS or colocation services and have only recently added micro data centers to their portfolios. Now, with the arrival of 5G, the demand for edge data centers could be ready to explode, with several of the startups below intending to drop micro data centers at the base of every 5G tower they can gain access to.
When Using Cloud, Paranoia Can Pay Off
While Google has locked down G Suite with encryption, two-factor authentication, and its emphasis on a culture focused on security, concerns still remain about situations where government can compel data disclosure, as well as whether automated scans or collected metadata can leak significant private details. "The short version is that, theoretically, Google can see anything that you can see in G Suite," says Jeremy Gillula, technology projects director with the Electronic Frontier Foundation. "Whether or not they actually do, is a totally different story." Users of any cloud productivity software generally have three threats to worry about: hackers, providers, and governments. Because both Microsoft and Google encrypt data at rest in their cloud, the information is protected against direct online attack. Steal the data, and it is still unreadable. However, online attackers have increasingly focused on stealing credentials and accessing the cloud by impersonating the authorized user. To foil such attacks, companies and individuals need to add multi-factor authentication, experts say.
Quote for the day:
"The illiterate of the 21st century will not be those who cannot read and write, but those who cannot learn, unlearn, and relearn." -- Alvin Toffler
No comments:
Post a Comment