The dark web's latest offering: Disinformation as a service

The campaigns followed similar strategies to nation-state-backed disinformation campaigns, using newly created and long-established accounts on 'major social media platforms' to help spread information. In some cases, what appeared to be real users were replying to the accounts of the companies. But it isn't just by exploiting social media that those selling disinformation services on the dark web go about their business: they'll create their own articles and blogs to help push the agenda they've been provided with. ... Researchers say an article ended up being published as news on two media sources, illustrating the ease at which the information can spread. The other user also offered edits based on feedback before setting about sharing the disinformation using social media accounts, including older, more established accounts – which then had their message amplified by bots and sock-puppet accounts. Some of these accounts even went so far as to communicate with or attempt to befriend users in the targeted countries to make the campaigns more effective by encouraging real people to share the disinformation.
Phish Uses Google’s URL Decoding to Swim Past Defenses
A phishing campaign that takes advantage of Google’s ability to decode non-ASCII URL data on the fly is making the rounds – looking to fool the unsavvy by effectively hiding the website address of the campaign’s phishing page. The campaign makes use of what’s called percentage-based URL encoding – a basic URL-encoding technique in which normal ASCII characters (i.e., “abc” and “123”) are converted into a string that starts with “%” and is followed by two hexadecimal digits. When resolving such an address, Google will convert this non-ASCII format into a string that is universally accepted and understood by all web browsers and servers, on the fly. The cybercrooks are making use of this in order to trick secure email gateways (SEG) into delivering their phishing emails, by hiding the true destination of the messages’ embedded malicious links. That’s according to the Cofense Phishing Defense Center, which last week observed a specific campaign using the method.
Former Army Contractor Gets Prison Term for Insider Attack

Barrence Anthony, 40, of Waldorf, Maryland, pleaded guilty in May to a single count of unlawfully accessing a protected computer. On Friday, a federal judge in Virginia sentenced the former systems engineer to two years in prison as well as ordering him to pay $50,000 in restitution, according to court documents. For several years, Anthony worked as an engineer for Federated IT, a federal contractor that provides technology and support services for a number of different military and federal government agencies, according to the Justice Department. In this case, Federated IT built and maintained financial applications on Microsoft SharePoint instances the U.S. Army's Chaplain Corps Religious Support System, which is based in the Pentagon and provides religious services and support for soldiers, according to court documents. These instances were hosted on Amazon Web Services cloud infrastructure, the documents show. Federated IT also provided IT support services for about 9,000 people working for the Army's Chaplain Corps, documents show.
8 uses for RPA in HR operations

RPA is an ideal way to review data change requests from a ticketing system and make appropriate changes in the HRIS, which can then route through the appropriate channels for approval. The software can check changes against compliance and organizational rules to ensure they are eligible and accurate; rejected changes are sent back to be updated or routed to HR for further review. RPA can also automate data sharing between systems. Some processes require data to be uploaded into one system from another system. For example, think performance ratings for compensation planning or compensation history for variable pay processing. RPA software can automate the extraction of this data from the source system, transform it into the target system format and then upload the data into the target system. RPA software can analyze data sets -- either directly in the system or by downloading or extracting data -- and provide audited results to HR for review and eventually correction, if required.
Why quantum needs a classic approach for supremacy

Generally speaking, a quantum computer does not offer the precision of a classical computer architecture, which relies on binary, 0 and 1, yes and no decisions. Stefan Woerner, global leader for quantum finance and optimisation at IBM, said: “Classical computers use binary optimisation and make many yes/no decisions that have to be correlated. Whenever you add a binary variable to the problem, you double the number of checks.” In practice, this means that when attempting to solve a problem that has several variables, the computations needed to run these correlations grows exponentially. However, Woerner added: “Some problems can be formulated in a way similar to quantum chemistry.” This is the domain of quantum computing and, for companies like IBM, it can be applied in areas such as quantum mechanics, genomics, supply chain optimisation and financial risk models.
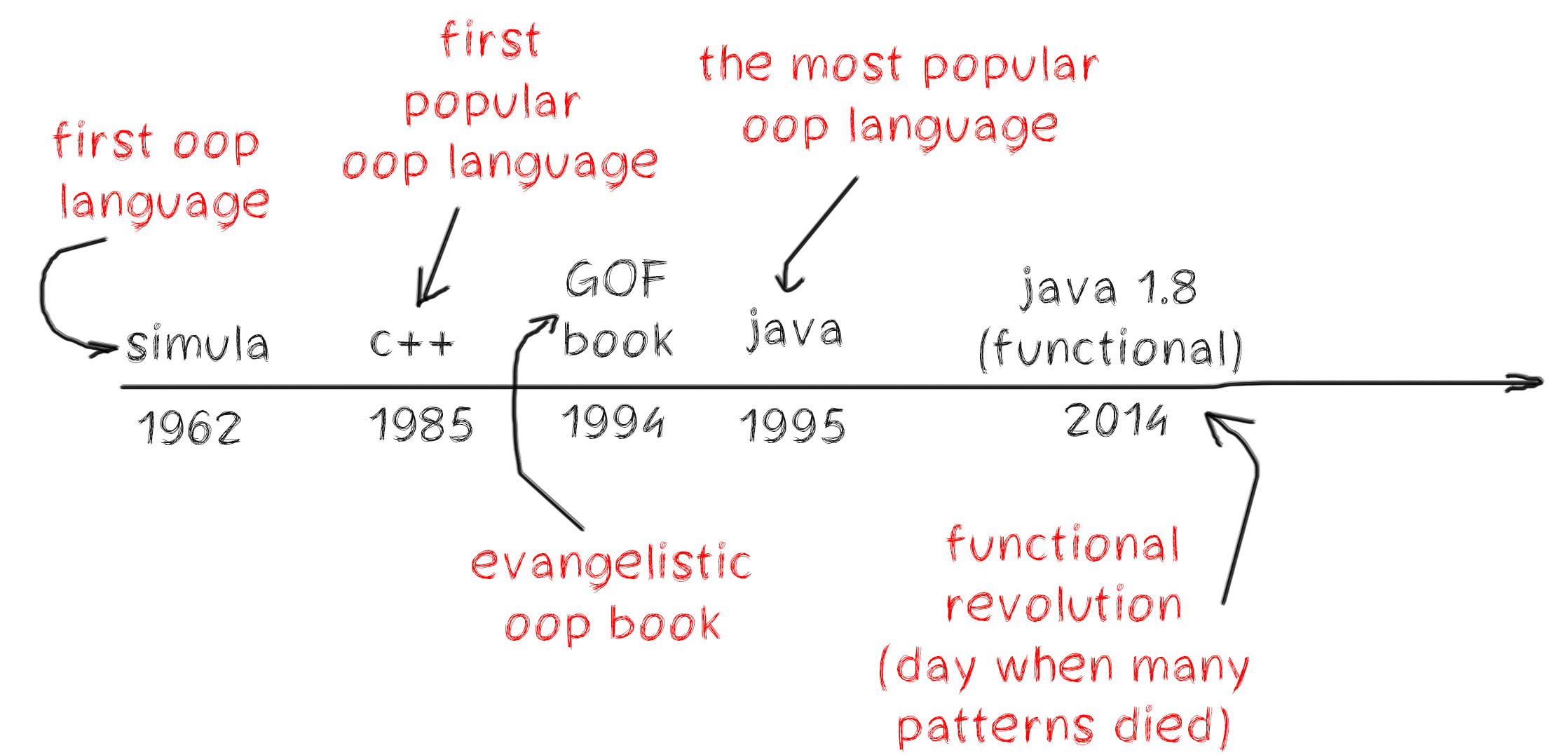
For the last 20 years, Java has become the most popular object-oriented language. It conquered the enterprise world and still has one of the biggest communities. Now industrial development exists only because of the object-oriented paradigm (OOP). But here, I want to bring up skepticism about its fundamental paradigm. First, let's return to the past when Java didn't exist. ... Unfortunately, the majority of enterprise projects become unsupportable quite rapidly. As a consequence, many enterprise projects are facing a constant migration process and unacceptable timelines. And sometimes, bug-fix estimation takes more time than simply re-writing from scratch. In addition, the word "legacy" scares IT employees more than ever before. According to my experience (more than 30 enterprise projects), the key problem is the project's architecture, which looks like a mess of patterns than anything else. Often, many patterns are used inappropriately or without any purpose, and this is all so that they can follow "modern OOP trends," sometimes referred to as the OOP cargo cult.
How to become an Alexa developer: A cheat sheet

Any developers or businesses that want to build out and utilize intelligent, voice-powered services will be affected by advances and changes that are being driven by Amazon Alexa. Alexa is built using artificial intelligence (AI) technologies, but Sobolewski said that would-be developers don't need a background in natural language understanding or speech recognition to get started. Additionally, there are beginner tutorials available as well, so even very junior software engineers can start working with the platform. Non-developers can build their own simple skills using predetermined frameworks called Alexa Skill Blueprints, which were revealed in April 2018. Amazon also offers Alexa SDKs for Node.js, Java, and Python, as well as an ASK Toolkit for Visual Studio Code, making it easy for developers to build Alexa skills using familiar languages and IDEs. Alexa is not confined to home and consumer use cases. Alexa for Business provides functionality for professional/productivity use cases, and Alexa for Hospitality provides the Alexa experience in hotels for controlling in-room devices, playing music, and contacting the hotel for guest services, among other features.
Enterprise Guide to Multi-Cloud Adoption
Multi-cloud may appeal to organizations that want as many choices as possible to exploit the cloud. Using multiple cloud providers offers core advantages, which in the past worked as disadvantages. Now, enterprises can avoid vendor lock-in, they can pick and choose/mix or match strengths of cloud providers to their specific needs, they see more reliability and less down time by spreading their bets, and they can uphold stronger data governance and security. But it’s been a painful process to get there. All this doesn’t mean enterprises are giving up on private or hybrid cloud, which, by the way hybrid cloud is often used synonymously with multi-cloud by some people. Multi-cloud is a subset of hybrid cloud. Companies are struggling to get the most value out of cloud in general, and multi-cloud may be the answer for some. In a recent column for InformationWeek, Kishore Durg, a senior managing director of Accenture Cloud, wrote that “when it comes to realizing the value of cloud … ”
The 7 Biggest Technology Trends In 2020 Everyone Must Get Ready For Now

Technology is currently transforming healthcare at an unprecedented rate. Our ability to capture data from wearable devices such as smartwatches will give us the ability to increasingly predict and treat health issues in people even before they experience any symptoms. When it comes to treatment, we will see much more personalized approaches. This is also referred to as precision medicine which allows doctors to more precisely prescribe medicines and apply treatments, thanks to a data-driven understanding of how effective they are likely to be for a specific patient. Although not a new idea, thanks to recent breakthroughs in technology, especially in the fields of genomics and AI, it is giving us a greater understanding of how different people’s bodies are better or worse equipped to fight off specific diseases, as well as how they are likely to react to different types of medication or treatment. Throughout 2020 we will see new applications of predictive healthcare and the introduction of more personalized and effective treatments to ensure better outcomes for individual patients.
Interview: James Smith, director of digital, Nationwide Building Society
As part of its digital journey, the company needs access to a wide talent base. To this end, the building society will open its first major technology hub in London next year to give it access to the IT professionals it needs to continue its digital journey. The new digital innovation hub will add 750 tech jobs, and the building society is also expanding operations in its home town of Swindon, which currently houses all its 3,500 technology operations staff. In total, Smith manages about 1,500 staff in the digital team. There are about 5,000 IT staff at Nationwide in total. Its people are organised around the work, with squads aligned to particular domains, using agile principles and focusing on digital, says Smith. ... Part of this additional investment will see Nationwide use AI technology and big data to help it understand customers so it can provide additional services, such as money management. This will involve working with financial technology (fintech) suppliers.
Quote for the day:
"Leaders speak truth into people who believe lies about themselves." -- Orrin Woodward
No comments:
Post a Comment