How and where to use serverless computing

Serverless has a great attraction not just for application developers, but also for systems operations personnel, says Ken Corless, principal in the cloud practice at Deloitte Consulting. Whether offered by hyperscale cloud providers or implemented on-premise with various solutions on the market, the goal of serverless computing is the same: “ruthless automation and self-service to speed the software development lifecycle,” Corless says. For IT administrators, serverless reduces the “request-response” cycle of ticket-based workloads and allows administrators to focus on higher-level tasks such as infrastructure design or creating more automation, Corless says. There are two main use cases that Corless is seeing. One is in application development for creating modern, loosely coupled services-based applications. Both function-as-a-service (FaaS) and backend-as-a-service (BaaS)—two cloud-enabled services that achieve serverless computing—can dramatically improve the productivity of a software delivery team by keeping teams small, he says.
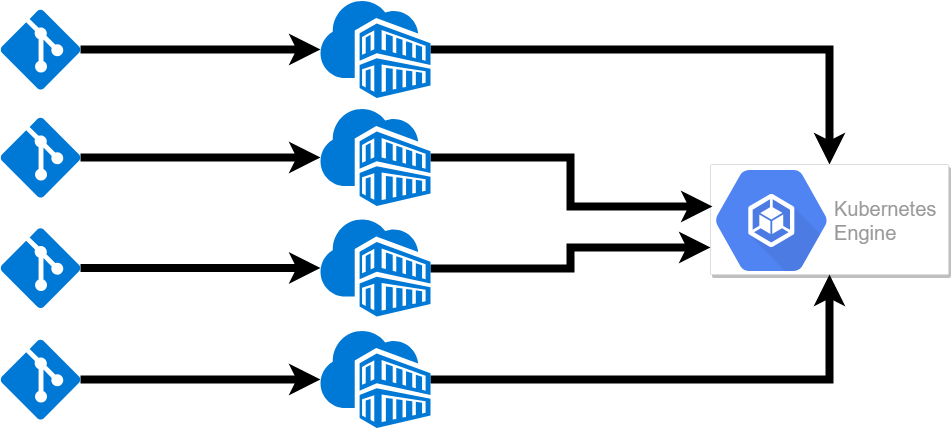
Having your application in well packaged stand-alone containers is the first step in managing multiple microservices. The next is managing all of the containers, allowing them to share resources and setting configuration for scaling. This is where a container orchestration platform comes in. When you use a container orchestration tool, you typically describe the configuration in a YAML or JSON file. This file will specify where to download the container image, how networking between containers should be handled, how to handle storage, where to push logs, and any other necessary configuration. Since this configuration lives in a text file you can add it to source control to track changes and easily include it in your CI/CD pipeline. Once containers are configured and deployed, the orchestration tool manages its lifecycle. This includes starting and stopping a service, scaling it up or down through launching replicas and restarting containers after failure. This greatly simplifies the amount of management needed.
5 Ways to Get the Most Out of Your Design Team
Building a team of solid design practitioners is just the first step towards building a successful design practice. Leaders who can create and share a vision, inspire their team and the rest of the organization, and advocate for design at the executive level are essential. Nearly two-thirds of the Level 5 companies in our study have teams led by design leaders who are directors and above, who likely have greater influence with executives, more accountability, and who are better positioned to develop strong partnerships with leaders in other functions. Ultimately, this means that the more senior the design leadership, the greater the impact on the bottom line. When compared to the Level 1 companies in our study, design leaders at the Level 5 organizations were nearly three times more likely to be involved in critical business decisions and to be peers with their counterparts in engineering and product management. They were four times more likely to own and develop key product and features with key partners, and nearly twice as likely to report directly to the CEO — underscoring the importance of empowering one’s design team within the context of the larger product team.
Processing the application in a cloud environment would require transferring all the data readings across the network. Processing at the edge, however, would eliminate the need to transfer those readings. The link between the edge and the cloud would carry only periodic reports, so it would cost less than a link that carried a constant flow of high-volume data. The tradeoff would be the continuing cost of a communication link versus the cost of locating and maintaining a processor at the edge. Processors have continued to fall in price, so edge computing will be less expensive than cloud computing in many cases. But each application is different, and organizations must carefully study before choosing an option. ... An edge computing facility can be located within a warehouse, refinery or retail store, but other options are also available. In the past few years, micro modular data centers (MMDCs) have grown in popularity. An MMDC is a complete computing facility in a box, and it contains everything included in a data center: processors, network, power, cooling and fire suppression, as well as protection from electromagnetic interference, shock and vibration.

“The way we work is changing,” said Jonathan Christensen, chief experience officer at Symphony. “Collaboration platforms and other innovations bring positive improvements that enable more flexibility and better work-life balance. But a more casual approach to workplace communications, and digital habits in general, presents major security risks. “Employees won’t keep secure practices on their own, and employers must consider how they will secure workforce communication over messaging and collaboration tools, just like they did with email.” The research also uncovered other trends that put employers at risk, including the fact that 51% of respondents are using collaboration platforms to discuss social plans, 44% are sharing memes and photos, and 18% admitted using them to ask a co-worker out on a date. This ease of communication poses a danger of creating a casual attitude to workplace communications, said the study report, because 29% admitted talking badly about a client or customer, 19% had shared a password
WannaCry Stopper Pleads Guilty to Writing Banking Malware
Hutchins, a British national, was arrested by the FBI in the U.S. and charged on Aug. 2, 2017, just before he was set to fly back to the U.K. after attending the Black Hat and Def Con security conferences. He has remained in the U.S. since then, continuing to work for Los Angeles-based Kryptos Logic, a security consultancy, where he specializes in reversing malware. Hutchins' guilty plea was filed Friday in federal court in Wisconsin. Hutchins pleaded guilty to two counts of developing and distributing malicious software aimed at collecting data that would aid in fraudulently compromising bank accounts. Each count carries a maximum penalty of five years in prison, a $250,000 fine and one year of supervised release. Hutchins could also be subject to a restitution order. As a result of his guilty plea, prosecutors have agreed to drop eight other counts against him that were lodged in a superseding indictment.
Open architecture and open source – The new wave for SD-WAN?

Cloud providers and enterprises have discovered that 90% of the user experience and security problems arise due to the network: between where the cloud provider resides and where the end-user consumes the application. Therefore, both cloud providers and large enterprise with digital strategies are focusing on building their solutions based on open source stacks. Having a viable open source SD-WAN solution is the next step in the SD-WAN evolution, where it moves to involve the community in the solution. This is similar to what happens with containers and tools. Now, since we’re in 2019, are we going to witness a new era of SD-WAN? Are we moving to the open architecture with an open source SD-WAN solution? An open architecture should be the core of the SD-WAN infrastructure, where additional technologies are integrated inside the SD-WAN solution and not only complementary VNFs. There is an interface and native APIs that allow you to integrate logic into the router. This way, the router will be able to intercept and act according to the traffic.
How 5G could shape the future of banking
“5G will begin to unlock some interesting things that we've dreamt about or imagined for some time,” said Venturo, the chief innovation officer at U.S. Bank. “5G is exponentially more powerful than 4G; it has such low latency and such high bandwidth that for a lot of applications, it will make a lot of sense to use 5G instead of Wi-Fi.” Jeremy K. Balkin, head of innovation, retail banking and wealth management at HSBC USA, has a similarly enthusiastic take. “Banking today is an experience that our customers want when, where and how they choose," he said. "The benefits of 5G networks offer next-generation mobile internet connectivity, faster speeds and more reliable connections on smartphones and other devices, which we believe will benefit all consumers.” 5G may help Venturo revive projects in his innovation lab he has had to set aside because network technology could not support them.
Developer Skills for AI

What AI allows developers to do is things in the code that cannot be done algorithmically. And that is the magic. A certain problem in the AI space, like looking at a photo and determining whether it contains a cat or a dog, has been solved. Five years ago, it was next to impossible to do. Today it's trivial to do. The beauty of AI/ML is the ability to look at a massive data set and find patterns that a human would never find by looking at it. As a developer, we are accustomed to writing code that takes an input applies an algorithm and produces a known output. That's what programming is all about to a large degree. with ML, we turn that on its head a little bit, we don't know the algorithm, we don't even have an algorithm. Instead, we build an ML model, we give it the inputs, and we give it the outputs, the inputs might be here are hundred million credit card transactions that have actually taken place, the outputs are the ones that were fraudulent.
Debunking the Discourse Around Cloud Security
The apprehension with which cloud safety is met is nothing short of ironic given the fact that in many ways, the cloud is actually more secure than on-premise, largely due to cloud providers collectively investing more into security controls than businesses can on their own. Take AWS for example. Its infrastructure hasn't been hacked in years, which is very good going, especially considering attackers are constantly targeting its infrastructure. So what’s the key to cloud security? First things first, choose established public cloud players that you can rely on. They often have the resources and expertise to protect their own infrastructure. However, in terms of education, what we need is a complete paradigm shift when it comes to cloud safety, the key to which lies in understanding the shared responsibility model. The shared responsibility model is universal among cloud providers: they ensure their infrastructure will be secure, but customers need to ensure whatever they do in the cloud is secure.
Quote for the day:
"You may be good. You may even be better than everyone esle. But without a coach you will never be as good as you could be." -- Andy Stanley


No comments:
Post a Comment