Blockchain: The Ultimate Disruptor?

What the internet did for the exchange of information, blockchain has the potential to do for the exchange of a digital asset’s value. Right now, many people in the blockchain space are talking about “tokenization,” which breaks down the ownership of an asset into digital tokens to allow wider-scale ownership of that asset. Tokenization started with initial coin offerings (ICOs) and has evolved to securitized token offerings (STOs), which have the potential to unlock the value of trillions of dollars of assets that are currently closed to the average person and make them more accessible. We’re talking about real-estate holdings, private equity, etc. When these assets are tokenized and brought into the market, it could impact the average person and how they do their financial and retirement planning, as well as where and what they choose to invest in. ... Rafia says about the wider access potential, “Currently, private equity, venture capital and other similar investments are not available to retail investors because there are a lot of regulations preventing it, as they tend to be riskier asset classes
Key in changing your enterprise is analyzing the impact of changes and planning those changes in a smart way. We do not advocate a ‘big up-front design’ approach, with huge, rigid multi-year transformation plans. Rather, in an increasingly volatile business world you need to use an interactive approach where your plans are updated regularly to match changing circumstances, typically in an agile manner. The figure below shows a simple example of dependencies between a series of changes, depicted with the pink boxes. A delay in ‘P428’ causes problems in the schedule, since ‘P472’ depends on it. Moreover, since the two changes overlap in scope (shown in the right-hand table), they could potentially be in each other’s way when they also overlap in time. This information is calculated from the combination of project schedule and architecture information, a clear example of the value of integrating this kind of structure and data in a Digital Twin.
How People Are the Real Key to Digital Transformation

Digital disruption affects all levels of the organization. Our research shows, however, that higher level leaders are generally much more optimistic about how their organization is adapting to that disruption than lower level employees. This result suggests that leaders may be overestimating how well their organization is responding. In the book, we provide a framework by which leaders can survey their employees to gauge how digitally mature their organization is against 23 traits, which we refer to as the organization’s digital DNA. Digital maturity is usually unevenly distributed throughout an organization, and we encourage organizations to use this framework to assess how it is distributed so they can begin to identify and address the areas of improvement that are most likely to yield organizational benefits. ... a single set of organizational characteristics were essential for digital maturity -- accepting risk of failure as a natural part of experimenting with new initiatives, actively implementing initiatives to increase agility, valuing and encouraging experimentation and testing as a means of continuous organizational learning, recognizing and rewarding collaboration across teams and divisions, increasingly organizing around cross-functional project teams, and empowering those teams to act autonomously.
Cachalot DB as a Distributed Cache with Unique Features
The most frequent use-case for a distributed cache is to store objects identified by one or more unique keys. A database contains the persistent data and, when an object is accessed, we first try to get it from the cache and, if not available, load it from the database. Most usually, if the object is loaded from the database, it is also stored in the cache for later use. ... By using this simple algorithm, the cache is progressively filled with data and its “hit ratio” improves over time. This cache usage is usually associated with an “eviction policy” to avoid excessive memory consumption. When a threshold is reached (either in terms of memory usage or object count), some of the objects from the cache are removed. The most frequently used eviction policy is “Least Recently Used” abbreviated LRU. In this case, every time an object is accessed in the cache, its associated timestamp is updated. When eviction is triggered, we remove the objects with the oldest timestamp. Using cachalot as a distributed cache of this type is very easy.
Enterprise Architecture: A Blueprint for Digital Transformation

Enterprise architects have a tough job. They have to think strategically but act tactically. A successful enterprise architect can sit down at the boardroom table and discuss where the business needs to go, then translate “business speak” into technical capabilities on the back end. The key to EA is to always focus on business needs first, then how those needs can be met by applying technology. It comes down to the concept of IQ (intelligence quotient or “raw intelligence”) and EQ (emotional quotient, or “emotional intelligence”). As a recent Forbes article stated, “when it comes to success in business, EQ eats IQ for breakfast.” Good enterprise architects need to have good IQ and EQ. This balance prevents pursuing the latest technology just because it’s cool but instead determining what’s the best way to meet the business need. At the end of the day, an EA should be measured by the business outcomes it’s delivering. Our approach to EA (see below) starts with a business outcome statement, and ends with governance processes to verify we’re achieving those business outcomes and adhering to the EA blueprint.
Crisis Resilience for the Board

Similar to culture oversight, boards are increasingly monitoring company technology activities, from cyber risk to disruption risk to digital transformation. Directors are asking management tough questions about technologies that are vital to the business and whether they are truly protected from the most likely and impactful risks. Beyond protecting data, the board should understand whether management is incorporating resilience into their information technology and cybersecurity strategies. To do so, directors may seek to understand how the most critical data—or that which is most vital to the business’s success—is backed up and protected, both physically and logically. Directors should understand, at a high level, what the most critical data asset sets or capabilities are to the company and the risks posed to them. Additionally, directors should ask management whether it is considering innovative technologies to both protect assets and enable quick recovery in the event of potential loss. ... Directors might also endeavor to learn about leading practices around risk management, crisis management, cyber risk, physical security, succession planning, and culture risk. This could provide a level of comfort with the risks posed to the company, as well as a degree of confidence in the company’s ability to respond.
The Cybersecurity 202: This is the biggest problem with cybersecurity research

“There are a whole lot of possible barriers that will come to the fore if an organization asks their lawyers about it,” Moore said. “It turns out that many of those risks, on deeper inspection, can be mitigated and overcome. But there has to be institutional will to do it.” One irony of this problem is that the cybersecurity community has been hyper-focused on information sharing in recent years — but the focus has been on companies sharing hacking threats from the past day or two so they can guard against them. The government has championed these threat-sharing operations and facilitates them through a set of organizations called information sharing and analysis centers and information sharing and analysis organizations. That sort of sharing has a clear benefit for companies because it helps them defend against threats that may be coming in the next hour or day. But companies have made less progress on sharing longer-range cybersecurity information that can help address more fundamental cybersecurity challenges, Moore said.
The Connection Between Strategy And Enterprise Architecture (Part 3)
Business capabilities connect the business model with the enterprise architecture, which is composed of the organizational structure, processes, and resources that execute the business model. It is a combination of resources, processes, values, technology solutions, and other assets that are used to implement the strategy. ... business capabilities comprise a fundamental building block that enables and supports the business transformation initiatives companies are undertaking to remain relevant in the constantly changing marketplace. Companies that excel in mapping their existing capabilities and creating a road map to close the gap in their future capabilities are most likely to remain ahead of the competition by responding effectively to industry and market dynamics. Therefore, the way we connect the company’s high-level strategic priorities and objectives to the resources, processes, and ultimately the system landscape that execute the strategy is by mapping and modeling the necessary capabilities.
Leading Innovation = Managing Uncertainty
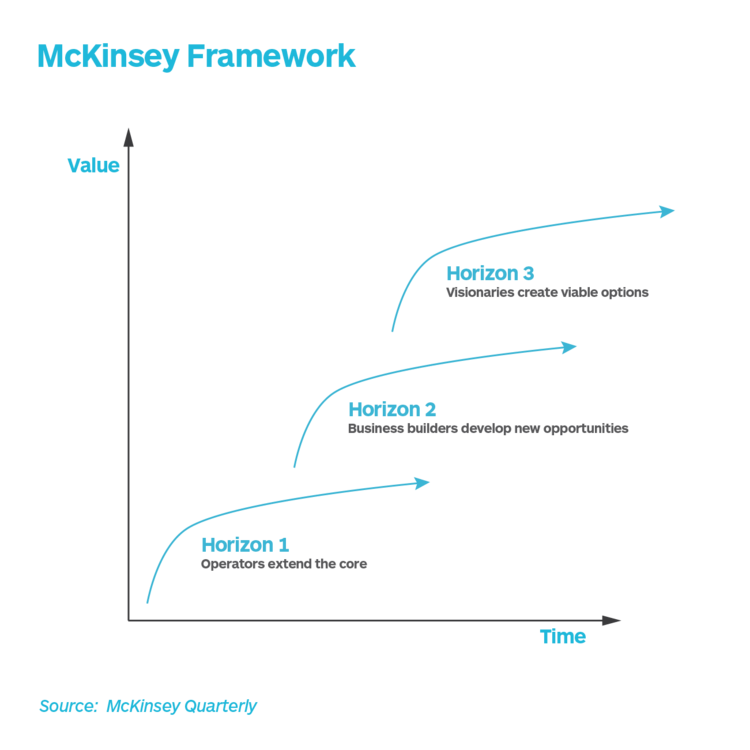
Uncertainty is the central characteristic of innovation. While generating new ideas and inventing new technologies is important, it is even more important for innovators to identify the unknowns that have to be true for their ideas and technologies to succeed in the market. We can only claim to have succeeded at innovation when we find the right business model to profitably take our idea or technology to market. At the strategy level, there are several frameworks that have been developed to help leaders understand their product and service portfolios and make decisions. These frameworks use different dimensions that hide in plain sight, the real challenge that leaders are facing - i.e. managing uncertainty. ... The McKinsey framework is perhaps the most popular of them all. This framework maps two dimensions of value and time to create three horizons. The nearest horizon is Horizon 1 where we extend the core and generate value for the company straight away. In Horizon 2, we build businesses around new opportunities with potential to impact revenues in the near term. The farthest horizon is Horizon 3 where visionaries work on viable options that will only deliver value to the company after several years.
Cloud Security Architectures: Lifting the Fog from the Cloud
The user behavior analytics (UBA) security solutions oriented primarily to the insider threat have matured and are commonplace. ... This data is crucial for forensics analyses when a major breach has been detected. There isn’t a comparable mature technology yet for the cloud where users have migrated their work. The successful UBA technology teaches security professionals how to properly architect new enterprise systems with users’ cloud behaviors in full view. The core approach for the cloud is to gather data from cloud storage logs, extract features and carefully architect sets of indicators that detect likely breaches. Cloud logs can reveal, for example, when file extensions are changed, what documents are downloaded and to where, whether a document has been downloaded to an anonymous user, and when an unusually high number of documents are downloaded to an odd geolocation. These are all early indicators of potential breach activity.
Quote for the day:
"Leaders need to be optimists. Their vision is beyond the present." -- Rudy Giuliani

No comments:
Post a Comment