Android Devices Can Now Be Used as a Security Key
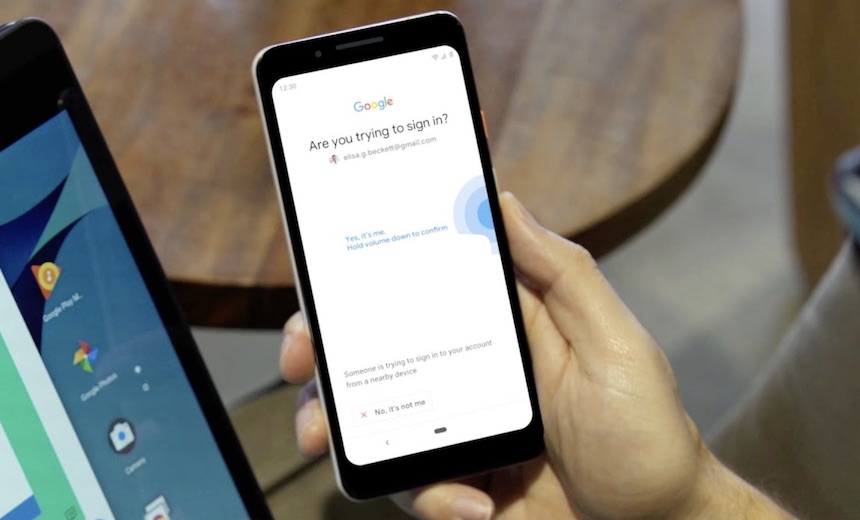
The new feature delivers what may be an easier alternative to Google's Titan Security Key, which the company introduced in September 2018. The Titan key bundle has two components, one of which slots into a computer via USB and another that authorizes a login via Bluetooth. The Titan keys became central to Google's Advanced Protection Program, which the company launched after years of attacks against activists, journalists and political campaign workers. In one of the most notable incidents, Hillary Clinton's chief of staff John Podesta saw his personal emails released in 2016 after suspected Russian hackers compromised his account. More recently, email accounts of four senior aides within the National Republican Congressional Committee were compromised for several months. The Titan keys were so successful internally at Google that they were rolled out to the public. Not one of Google's 85,000 employees accounts fell to a phishing attack after the keys were launched in early 2017, computer security writer Brian Krebs reported last year. Android devices running 7.0 and above are compatible with the new security feature that's an alternative to Titan.
How insurers can achieve data mastery
Most data and analytics IT budgets are smaller than what is needed, forcing the organization to prioritize the use cases. In the many instances when data projects are IT-led, there are not metrics in place to measure their impact on business objectives. As a result, the value of many data and analytics projects are unknown. Given the focus on data and analytics, innovative insurance CIOs expecting to develop more futurist corporate cultures by 2030 will build, buy or acquire technology and data capabilities to create new and differentiated products, services and business models — creating more competition for incumbent insurers. The investments of these innovative companies are likely to average twice what their more conservative peers make. They’ll consider data their single most important asset, and disrupt the industry by setting data mastery leaders apart from those that lag behind. These companies will find greater impact from data and analytics initiatives, and use this capability to drive new business models, such as the monetization of data.
Members of the group are government departments such as the Cabinet Office, Ministry of Defence, Ministry of Justice, NHS, Department for Work and Pensions, Department for Business, Energy and Industrial Strategy, the Foreign and Commonwealth Office, Met Office, HM Revenue and Customs, and others. Government departments will then liaise with its various suppliers – for example, Defra would talk mainly to Microsoft about cloud-related issues, as well as other companies providing similar services to the department, such as Amazon Web Services (AWS). The sustainable technology advice and reporting group also works closely with techUK on a number of issues including cloud-related measures. Progress has been reported by the government around the awareness and use of sustainable digital services and technologies, according to the latest Defra report on sustainability. The annual report said departments across government have significantly reduced staff members’ individual energy footprints to 891KWh/staff from a baseline figure of 1467 KWh/staff.
How to overcome the risk of overcorrecting
Certainly, no normal person wishes any misfortune on their fellow human, and as a frequent traveler, I have a soft spot for the hundreds of people who invest their sweat equity into allowing me to travel around the world with relative ease and comfort. However, a placard in a nice hotel that implies the very reason hotels exist— paying customers—are an entity to be regarded with deep suspicion to the point that anyone who interacts with them requires a panic button seems like a significant overreaction. While this example might seem inane to the point of comedy, we as individuals and collective organizations are likely guilty of similar transgressions. The average employee handbook at a Fortune 500 company implies that employees are one step away from thievery, gross ethical lapses, and general tomfoolery without repeated admonishments from HR to the contrary.

“Technology moves incredibly rapidly, but you’ve got quite slow paced regulation. It became clear that we needed to address some of the regulatory concerns in the digital age, but we also put forward a fundamental recommendation about how regulation happens in the future,” he says. The proposal at the heart of the Committee’s Regulating in a digital world report, Gilbert explains, is a new Digital Authority that will make sure existing regulators are addressing key issues. The authority will also carry out a horizon scanning role, preparing for regulatory issues that could arise over time. “The job of the authority is to make sure there is nothing falling between the gaps of the existing regulators. That’s why the chief executives of the most prominent regulators in this space should sit in the same room and jointly discuss the issues,” he says. “There should then be a number of independent members, who are not part of the existing regulatory framework. There should be a powerful, independent chair who is not afraid to stand up to government and argue to parliament that more powers are needed.”
In Security, All Logs Are Not Created Equal
Of the major data breach vectors, holes in web applications – which typically have access to highly sensitive customer account information – represent the greatest percentage, according to the "2018 Verizon Data Breach Investigations Report." Unfortunately, security teams have the least visibility into web application logs. In addition, parsing web server logs is challenging because they are often in a multi-line or custom format and logged in a nonstandard way to a text file or database, as opposed to the native web server log, such as Microsoft IIS or Apache. ... Logging events from a web application firewall (WAF) already watches for potentially malicious actions. DNS server logs provide rich information about what sites users visit, and they show whether any malicious applications reach out to command-and-control sites. However, DNS also is a common tunneling protocol for exfiltrating data since firewalls typically allow the data out. DNS logs are challenging because of the volume of data, their multi-line format, and the difficulty posed in exporting them.
The Business Value of Cybersecurity

This lack of details around the quantification of the tangible value of following cybersecurity best practices is a problem. In fact, we believe it is an important reason why the issue is still shifting in and out of most boards’ radars. Gut feeling alone does not make for a strong-enough case: Top executives are increasingly asking “Show me the data”. Beyond the fact that measuring success in the cybersecurity is very hard, another issue is the stringent lack of meaningful data. This is a really big problem in the field of cyber insurance, for example, which struggles to fit its traditional actuarial models around the scarce data they can get a hold of. The reason for that is quite simple: most organizations are still very reluctant to share what they perceive as highly sensitive cybersecurity data. ... Being able to show key stakeholders in business terms what exactly is the tangible value-added of cybersecurity will be key in finally anchoring the topic at the right level of organizations. Money – and data – talk. And boards usually listen. But we’re not there yet and cybersecurity looks definitely like a promising path for data-driven research.
Reflecting on Top-Down or Bottom-Up System Design
Vernon emphasizes that both perspectives are important, but if you are thinking about bounded contexts with their ubiquitous languages you are probably taking a bottom-up approach. Then it’s important to learn what the core domain within your whole solution in, otherwise you may very well put your efforts in the wrong place. If you need to take a top-down perspective at some point, you can define an interface as a placeholder for something you do not yet understand how to communicate with. Later, this placeholder can be replaced by an implementation in a bounded context. As you do that, you also shift to a bottom-up perspective because you now need a deep understanding of the domain model within that context. For Vernon, a bottom-up approach is also an emergent approach which leads to an emergent architecture, and for him is the same as lean architecture or agile architecture and design. Trying to make your architecture immovable will not work; he believes that you will either adjust your architecture, or fail.
Government breach data highlights cyber skills misconception

“If only 36% of information security or governance staff are attending courses, it is not clear how organisations can say they are confident that their security teams have the skills and knowledge they require to be effective.” Even if is an active training programme, Hadley contended that the skills learned are out of date before people leave the classroom, creating false security and human vulnerabilities because information security professionals are lagging behind the attackers. This is because attackers, unlike businesses and charities, are free to innovate and do not have to work within the limits of the law and security budgets, while few training programmes or computer science and certification courses are geared up to be updated on a daily or weekly basis to include new threats that have been identified. “They build faster than development teams and change attacks quicker than traditional training can cope with,” said Hadley. “This is the same ‘time gap’ that plagued signature-based AV [antivirus] engines for years.

At first glance, the creation of a forum focusing on preserving human control in warfare is a step in the right direction. But Australia's Trusted Autonomous Systems Defence Cooperative Research Centre (TASDCRC) chief scientist and engineer Jason Scholz, who spoke with TechRepublic, said that while the forums have good intentions, they have not been comprehensive enough in discussing the systems of control when using a weapon. "It's not only about what can happen in terms of selecting a target and engaging it, autonomously or not, but the reliability of the weapon ... the context in which it's used, training, certification of the people and technology, authorisation, no one from a confident military sticks a weapon directly into a target without having an entire system of control," Scholz said. The most recent GGE on LAWS meeting took place in Geneva in late March, with over 90 countries in attendance. Much like the previous meetings, little progress was made about the use of lethal autonomous weapons.
Quote for the day:
"You will face your greatest opposition when you are closest to your biggest miracle." -- Shannon L. Alder

No comments:
Post a Comment