Instead of using wipers, Symantec reports that the group’s recent attacks are aimed at data exfiltration using vulnerabilities in a common piece of software. “The main point of entry in recent attacks has been spear-phishing emails capable of delivering malware to the recipient’s computer,” says Dick O’Brien, researcher at Symantec's Security Response. “The group has also attempted to exploit the recently patched WinRAR vulnerability attacks.” After sending phishing emails to targeted companies, the victim is encouraged to download a file, JobDetails.rar, which then tries to exploit vulnerability CVE-2018-20250 in WinRAR. A successful infection on an unpatched system allows an attacker to install any file on the computer. ... “Based on its tactics and targets, our assessment is that Elfin is a state-sponsored espionage group,” says O’Brien. “Given the nature of the group and its targets, we can only speculate that the information in question is likely to be of a strategic or economic interest to Elfin’s sponsors.”
Lexing is the process of breaking an input stream of characters into "tokens" - strings of characters that have a "symbol" associated with them. The symbol indicates what type of string it is. For example, the string "124.35" might be reported as the symbol "NUMBER" whereas the string "foo" might be reported as the symbol "IDENTIFIER". Parsers typically use lexers underneath, and then compose the incoming symbols into a syntax tree. Because lexers are called in core parsing code, the lexing operations must be reasonably efficient. The .NET regular expression isn't really suitable here, and while it can work, it actually increases code complexity while diminishing performance. Included in this project is a file called "FA.cs" that contains the core code for a regular expression engine using finite automata which resolves to the humble yet ubiquitous state machine. Finite state machines are composed of graphs of states. Each state can reference another state using either an "input transition" or an "epsilon transition".
AI and data security: a help or a hindrance?

Having the right technology in place is vital but companies need the right people to ensure it runs effectively. In a great deal of cases we’re seeing a shift in companies bringing senior security talent in-house rather than relying on external partners to bolster their security infrastructure. But organisations still have a long way to go when it comes to building security expertise from within. More than half, 52%, of respondents in a recent poll by Infosecurity Europe cited that they have a skill shortage in their organisation when it comes to preventing cyber attacks. Without the right team and technology, cyber attacks will only grow in severity. Neither can work effectively in isolation and those organisations that don’t invest in both will find out that the impact of a data breach goes far beyond fines. Businesses know that there is a high risk of cyber attacks and the majority are trying to build the right team and implement technology to tackle cyber security. But very few leaders truly understand where all data leak vulnerabilities exist and how to prevent them.
Creating HTML Layouts That Meet Web Accessibility Standards

Use ARIA landmarks across the web pages where appropriate. ARIA(Accessible Rich Internet Applications) is a comprehensive technical specification for adding accessibility information to elements that are not natively accessible (in particular, the ones developed with JavaScript, AJAX, and DHTML). With ARIA landmarks, a developer can extend HTML capabilities and apply proper semantics, i.e. properties, to UI and content elements for assistive technologies to understand these. Here is an example of how HTML semantic elements (<header>, <nav>, <main>, <footer>) are combined with ARIA role attributes (“banner”, “navigation”, “main”, “contentinfo”) to make website navigation using a screen reader easier for people with disabilities. Though most ARIA functions were recently implemented in HTML5 (and you should definitely favor these!), not all screen readers and browsers (e.g. IE) are sophisticated enough to depend on HTML semantics only.
Undertake software dependency management to reduce conflicts

Since dependencies can take numerous forms, it's easy to end up with too many. When software depends on many packages or components, the application might have significant compatibility problems and can be plagued by long downloads, plus require lots of storage space. Similar problems occur with long dependency chains, where components depend on other components, and so on. Dependencies can conflict when multiple applications rely on different, incompatible versions of the same dependency. For example, if an application depends on component A.1 and another application depends on component A.2 but apps cannot install A.1 and A.2 together, a conflict occurs, and many conflicts are more convoluted than this example. In such circumstances, both apps cannot run on the same system at the same time, or the application with the older dependency might need an update to use the current dependency. Circular dependencies can affect software applications or constituent components.
Advancing OpenCL™ for FPGAs
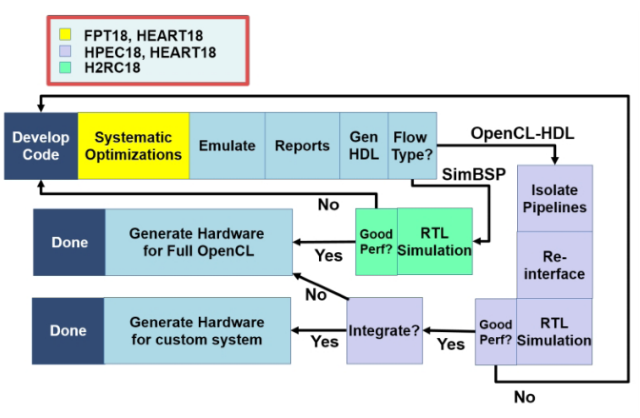
Intel has created Intel® FPGA SDK for OpenCL™ technology, which provides an alternative to HDL programming. The technology and related tools belong to a class of techniques called high-level synthesis (HLS) that enable designs to be expressed with higher levels of abstraction. Intel FPGA SDK for OpenCL technology is now in widespread use. Amazingly for longtime FPGA application developers, the performance achieved is often close to―or even better than― HDL code. But it also seems apparent that achieving this performance is often limited to developers who already know how the C-to-hardware translation works, and who have an in-house toolkit of optimization methods. At Boston University, we’ve worked on enumerating, characterizing, and systematizing one such optimization toolkit. There are already a number of best practices for FPGA OpenCL documents. This work augments them, largely by applying additional methods well known to the high-performance computing (HPC) community2. In this methodology, we believe we’re on the right track.
We are spending a lot of R&D time and effort figuring out what does that look like in our world. In our human resources products, we call it augmented intelligence. You can look at the data; you can discern certain things that are going on with your workforce such as diversity. Where you can get into augmented intelligence in a human capital management environment, you can literally train the product to tell you things about the workforce doing ongoing analytics. “With Intacct, we’ve talked a lot about artificial intelligence. When dealing with the close [for bookkeeping] especially for publicly traded companies, what if you could—over time through artificial intelligence—just always have an ongoing close? So it was never a monolithic event? Transactions were always updated. You had triggers that showed you potentially fraudulent transactions. You’re cleaning up your books as you go along. There is no notion of a period end close. You’re always closing. You could teach an AI engine how to do a continuous financial close. Those are the kinds of things we are trying to bring to bear within our products.
The fresh recognition given to the pioneers of artificial intelligence, computer scientists Yoshua Bengio, Geoffrey Hinton and Yann LeCun with the Turing Award, an honour that is better known as technology industry’s version of the Nobel Prize has established that the world is acknowledging the relevance of emerging tech. AI has become a part of DNA for tech giants like Google. To maintain the sanctity of this technology and address the concerns around the ethics revolving around the growth of artificial intelligence, the company has created an Advanced Technology External Advisory Council to keep AI in check and shape the "responsible development and use" of AI in its products. Apart from being the fastest growing technologies in science, AI has taken the crown for being the front-runner for digital transformation, which has become a major part of every company’s agenda; 40 per cent of which is expected to be met by employing artificial intelligence. Smart assistants are fostering decision making procedure in diverse fields, from medicine, IT and education too.
Critical Magento SQL injection flaw could be targeted by hackers soon
Due to its popularity and the sensitive customer data it processes, the Magento platform is an attractive target for hackers and has been targeted in widespread attacks many times in the past. The number of attacks against online shops in general has increased over the past year, with some groups of hackers specializing in web skimming -- injecting rogue scripts on computers to capture credit card details. SQL injection vulnerabilities allow injecting data into or reading information from databases. Even if this particular flaw can't be used to infect a website directly, it can potentially give attackers access to accounts on a site. That access can then be used to exploit one of the other privilege escalation or code execution flaws that were patched in this release and which require authentication. "Unauthenticated attacks, like the one seen in this particular SQL Injection vulnerability, are very serious because they can be automated — making it easy for hackers to mount successful, widespread attacks against vulnerable websites," the Sucuri researchers warned.
C# Futures: Deferred Error Handling
In order to use deferred error handling, a new compiler directive called “exception mode” is used. This switches the current function between structured exception handling and the new deferred mode. When using the deferred mode, the Exception.LastException property can be used to determine if an error has occurred. This stores only the most recent error, so if multiple errors occurred, all but the last will be lost. This has caused some concern, as it would mean one should check LastException after each line, which would be contrary to the goal of reducing the amount of code needed. To address this, an amendment to the proposal is to replace LastException with a stack is under consideration. ... The use of both structured and deferred error handling in the same function can be problematic from a compiler standpoint. Deferred mode fundamentally changes the way the code is compiled, much like how C# implements closures and async/await without CLR support.
Quote for the day"
"Real leadership is being the person others will gladly and confidently follow." -- John C. Maxwell





No comments:
Post a Comment