Excessive Permissions are Your #1 Cloud Threat
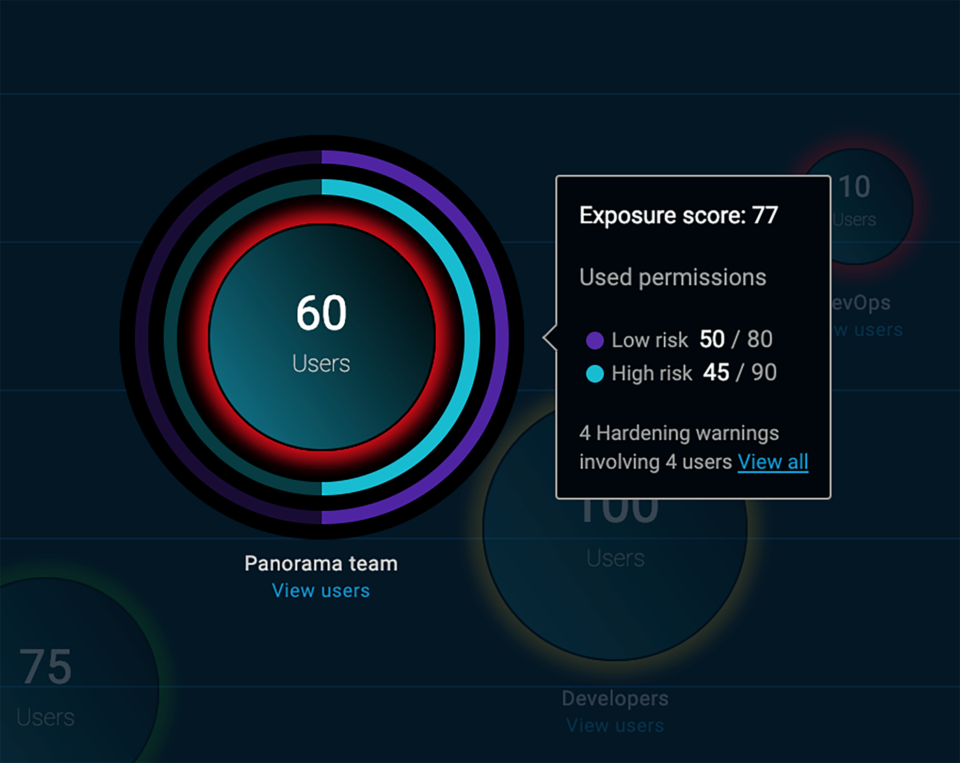
IT administrators and hackers now have identical access to publicly-hosted workloads, using standard connection methods, protocols, and public APIs. As a result, the whole world becomes your insider threat. Workload security, therefore, is defined by the people who can access those workloads, and the permissions they have. ... One of the primary reasons for migrating to the cloud is speeding up time-to-market and business processes. As a result, cloud environments make it very easy to spin up new resources and grant wide-ranging permissions, and very difficult to keep track on who has them, and what permissions they actually use. All too frequently, there is a gap between granted permissions and used permissions. In other words, many users have too many permissions, which they never use. Such permissions are frequently exploited by hackers, who take advantage of unnecessary permissions for malicious purposes. As a result, cloud workloads are vulnerable to data breaches, service violation (i.e., completely taking over cloud resources), and resource exploitation.
The most advanced hacking groups are getting more ambitious
Groups like Chafer, DragonFly, Gallmaker and others are all conducting highly-targeted hacking campaigns as they look to gather intelligence against businesses they think hold valuable information. Once attackers might have needed the latest zero-days to gain access to gain entry into corporate networks, but now it's spear-phishing emails laced with malicious contents which are most likely provide attackers with the initial entry they need. And because these espionage groups are so proficient at what they do, they have well tried-and-tested means of conducting activity once they're inside a network. "It's like they have steps which they go through which they know are effective to get into networks, then for lateral movement across networks to get what they want," Orla Cox, director of Symentec's security response unit told ZDNet.
Why blockchain may be blockchain’s best cybersecurity option

Developers should take the initiative to build their own decentralized security applications for anti-phishing, anti-malware, intrusion detection and distributed VPNs to deploy on the global blockchain. The bottom line is that it’s not enough to just trust blockchain’s security because of more transparency than other technological data security and privacy methods. Developers, miners and even enterprises need to look at the entire digital ecosystem when considering security, as every single point provides savvy hackers a weak link to exploit. As blockchain investment continues to skyrocket and the crypto markets continue to diversify – even with the recent slowdown – we will see more unique and sophisticated examples of cyber criminals penetrating blockchain’s security veneer. That’s the paradoxical ratio of technology: for as many positive innovations that tech creates, there almost is an equal amount of sinister “innovations” to match. This is most certainly true regarding blockchain. The key is to keep discussing threats to blockchain to inspire those securing it.
How Estonia became an e-government powerhouse
Estonia is among the elite group of countries in the highest echelons of the UN's E-Government Development Index (EDGI), with its citizens and public servants able to access a wide range of services online using secure digital IDs, including making payments, accessing full health records, and internet voting. Estonia has been building out its e-government since the mid-90s, not long after declaring independence from the Soviet Union. The program continues to make headlines with bold new digital initiatives, such as its e-residency program, which gives anyone living anywhere in the world the ability to receive a government-issued digital ID and full access to Estonia's public e-services. Today, 99% of the public services are available online 24/7, 30% of Estonians use i-Voting, and the country estimates the reduced bureaucracy has saved 800 years of working time.
The 11 biggest issues IT faces today

“Security professionals must be extra vigilant with detection and training against these threats,” says John Samuel, CIO at CGS. “This year, companies will need to introduce AI-based protection systems to be able to contain any such attacks introduced by this next-gen tech.” Grinnell says AI wasn’t a factor in the most notable attacks of the last year, but he expects that to change. “I believe 2019 will bring the first of many AI-driven attacks on U.S. companies, critical infrastructure and government agencies,” he says. “Let’s hope I’m wrong.” Forward-thinking organizations are now implementing privacy by design in their products, but making sure those efforts meet GDPR standards is an ongoing concern. Google, for example, just saw a record fine by French regulators over how the company collects data. “U.S. businesses will need to consider a GDPR-type policy to protect citizens even before any regulations are enacted,” Samuel says. “Ultimately, there must be international guidelines to ensure customer privacy and protection on a global scale to allow for easier compliance.”
Setting expectations and preparing for a new breed of cyberattacks
Lateral movement is a method used by cyberattackers to move through a network, as they search for the essential data that is the eventual target of the breach. Continuing to hide in plain sight, cybercriminals are leveraging non-malware / fileless attack methods to do this, which is the biggest indicator that attackers aren’t just focused on one component of an organization, but are seeking additional targets as they infiltrate the network. In order for today’s organizations to prepare for these threats to security, they first need to solve the problem of visibility. True endpoint visibility should allow you to “turn back the clock” and see exactly what happened on the endpoint at a specific date. To understand how significant this capability is, we found that an organization with 10,000 endpoints is estimated to see more than 660 attempted cyberattacks per day.
Can work allocation algorithms play fair?

Allocating work by algorithm is not an inherently bad idea, according to James Farrar, chair of United Private Hire Drivers, a branch of the Independent Workers Union of Great Britain, who has co-led legal action against Uber for drivers’ rights. Many drivers working for conventional minicab companies pay a fee for the privilege (Uber takes a percentage, typically 20-25%), only to see controllers giving the best jobs to their friends, ordering them to collect their takeaway food and even demanding bribes. “People didn’t just walk away from those operators, they ran to Uber,” Farrar says. But the company’s algorithms create their own problems. Uber tells prospective drivers that “there’s no office and no boss”, adding that “with Uber, you’re in charge”. Farrar says this is not reflected in the ways the company’s algorithms allocate jobs and influence driver behaviour.
Unactioned data subject access requests could lead to legal action
A Talend report published in September 2018 found that only 30% of organisations are able to fulfil DSARs within the GDPR’s 30-day deadline. This shows how difficult it is to maintain an effective DSAR process. Requests have increased substantially since the GDPR took effect, while the deadline to respond has decreased and the amount of information that must be provided has increased. It’s no surprise, therefore, that many organisations are looking for help. The GDPR DSAR Support Service, provided by our sister company GRCI Law, is a perfect example of how you can simplify the process. GRCI Law’s experienced data privacy lawyers and DPOs (data protection officers) will manage the process on your behalf to ensure that requests are completed in accordance with the GDPR’s requirements.
How managed network services are evolving to simplify the global WAN

The first step toward evolving the managed network services market was network function virtualization (NFV). “When the service providers were facing the need to streamline their operation, move faster, respond faster, they took an approach of virtualizing appliances,” says Yovel. “Think about all the different network functions that used to be in the old network—next-generation firewalls, various orchestration solutions, VPN solutions, and so on. They virtualized all these boxes, but that didn't change the core dynamic of the network itself. Each function coming from different vendors still had its own management interface, plus its own scaling and sizing environment. The fact the appliance was virtualized didn’t change that. They still had the same problem with the centralized architecture as in the past.” Consider the example of virtualizing a firewall. Mobile users still need to connect over the internet over long distances to some firewall in some location to get the security they need. The fact that the firewall is virtualized doesn’t change that dynamic.
Microservices With CQRS and Event Sourcing
Microservices are independent, modular services that have their own layered architecture. When microservices share the same database, the data model among the services can follow relationships among the tables associated with the microservices. ... A shared database is not recommended in a microservices-based approach, because, if there is a change in one data model, then other services are also impacted. As part of microservices best practices, each microservice should have its own database. ... The limitation of this approach is that transaction management cannot be properly handled. If customer data is deleted, the corresponding order also has to be deleted for that customer. Though this can be achieved with workarounds, like calling a delete service in the Order service, atomicity is not achievable in a straight forward way. This needs to be handled with customization.
Quote for the day:
"The world_s greatest achievers have been those who have always stayed focussed on their goals and have been consistent in their efforts." -- Roopleen
No comments:
Post a Comment