Enterprise digital transformation leaves data security behind

Thales suggests that in the rush to adopt new solutions — of which the majority of survey respondents said sensitive data is used in tandem with digitally transformative technologies — encryption and protection is not as high on the priority list. While sensitive corporate or customer data is linked to new digital solutions in 97 percent of cases, fewer than 30 percent of these same respondents said that encryption is being used within these environments. According to the survey, enterprise players that are aggressively overhauling their systems with new technologies are skating on the thinnest ice, with 28 percent running the highest risk of experiencing a data breach by ignoring suitable security standards in their enthusiasm. However, there are a few areas in which encryption usage is in above-average use. In total, 42 percent of organizations using IoT, 47 percent of businesses using container technology, and 45 percent of companies which have adopted Big Data solutions use encryption in some form or another.
Digital banking can give a boost to your bank’s bottom line.
By expanding their digital footprint, banks can reduce costs and boost financial performance while meeting consumer demand for a more streamlined and personalized customer experience. The closer you get to digital native, the more substantial the cost reductions and the greater the corresponding increase in ROE. That doesn’t mean going digital native is the right answer for every bank. Whatever you choose, the solution needs to be in line with your long-term strategy. After all, each bank has a different set of core capabilities, and not all banks are prepared for a full digital transformation. The right answer for one bank might be the wrong answer for another. ... The simplest approach is to modify the front end only, focusing on the primary ways a customer interacts with a bank. Largely a cosmetic fix, the bank designs an appealing mobile app and web interface but keeps the organization’s workflows, culture, and back-end infrastructure intact. We understand the appeal of this approach. For an organization that needs a quick win, it’s certainly the fastest route.
Pro Tips for Developer Relations

One thing I like to do from time to time is what I call a Mashup Presentation. It requires zero content creation but requires demo creation. When I do something like this, it involves simply curating existing content from other presentations, and then work on a demo that uses most if not all pieces described in the material. It is a good way to compact and connect interesting topics and present to developers, so they don’t need to figure out the intrinsic connections between the ideas. Plus, consumes less time. A second tip is to contact the regional sales field when traveling, to find opportunities to meet with customers/prospects. May sound salesy, but it actually shows itself as a great source of real-world ideas to be covered in the future. Plus, it brings the advocate down to Earth. Finally, I like to reuse as much material as possible, whether from myself or from others. What matters is presenting something that will be never-heard-of to the audience, doesn’t matter if it is something that was created in 2001. To me, advocacy is more about bringing information than "creating information."
What the fintechs think about open banking’s progress?
“Banking data is shared via APIs, which allows two pieces of software to talk to each other and share information. Whilst these APIs already exist, there is technically a long way to go before they can be used widely. This is the limiting factor on the uptake of open banking currently, and as the technology improves, more services and products will spring up. The initial uptake of open banking has been more of a trickle than a flood. That said – there is lots of support and encouragement in existence to help providers and users start to explore the possibilities of Open Banking. Fluidly has recently been the winner of a £200,000 prize fund organised by Nesta. The fund is specifically aimed at companies who are transforming small business banking via Open Banking. Funds like this will accelerate the uptake of Open Banking as it helps to get new products built more quickly and raises the profile of what’s now available for consumers and businesses.”
McLaren: Digital transformation on and off the track

A great example of how this transformation impacted our business is how it empowered the technology underpinning our racing team. On each Formula 1 car there can be up to 300 sensors that communicate from once per lap to 150 times a second. That data which reached terabytes per race is now sent via a hyper-converged infrastructure from the pitlane garage to engineers, strategists and drivers. That trackside infrastructure has to be robust enough to be installed operated and then moved to over 21 global locations. The same data is transferred in real-time back here to the McLaren Production Centre. Within the cool calm centre of our mission control, the data becomes the driving force behind our simulations, strategy options and data-driven precisions. This system of data-driven collaboration relays on our cloud-based apps and infrastructure and storage solutions. In McLaren, regarding IT, we look to apply these principles across our group and have found that it can be applied to many other businesses.
Three Elements Of Next-Generation Data Management For Financial Services

A data hub can help you gain a holistic view of data assets, manage data across the full IT landscape, and integrate data into a unified view. By building the platform around a data hub, you can increase transparency of and access to all data assets, which increases agility and the speed of innovation. Critical data hub functionality includes: Open architecture foundation, allowing the hub to connect data no matter where it is physically located – in the cloud, on-premise, in Hadoop, or on cloud object storage; Data sharing and discovery across the enterprise; Single view for data asset management, supporting data analysis and governance (including pipelining, orchestration, and monitoring); Elimination of the need for centralization of data and mass data movement to a single data store; Support for complex data processing operations, such as machine learning-based analysis; Governance and orchestration for data refinement and enrichment; and Metadata catalog management, improving the visibility of data assets across the landscape. As financial services leaders increasingly realize that more trusted, connected, and intelligent data contributes to digital transformation,
The DDoS that wasn’t: a key takeaway for web domain security

Typical traffic forwarded to the domain before the incident contained both GET and POST requests. However, the 'malicious' traffic was only sending a stream of POST requests. "Examining all the POST requests hitting the customer's URL showed that the User-Agent fields were not being forged or otherwise altered, boosting the confidence researchers had for their conclusion that a Windows-oriented tool was responsible for this massive flood of requests," the cloud service provider says. To give the firm time to work out what was doing on, SOCC was able to mitigate most of the strange requests over the next 28 hours, leading to the discovery that the traffic smashing the URL was "the result of a warranty tool gone haywire." Buggy code, and not a botnet, was the problem. The warranty tool's errors meant that it sent constant POST requests to the domain automatically and with enough frequency to potentially take down the website. A fix was created and deployed quickly by the vendor at fault for the tool which resolved the issue.
Data Loss Prevention – Human error, insider threats and the in-between
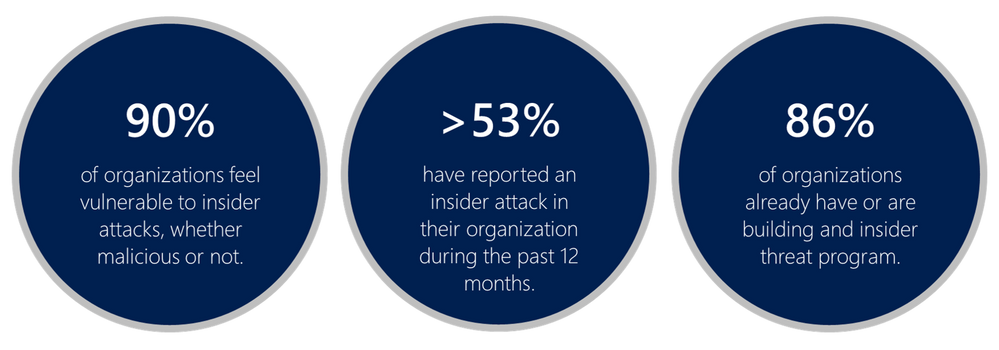
While employees in the modern workplace are getting increasingly technologically savvy, and are finding new tools to improve their productivity, they aren’t always aware of the security implications of their actions. Many of our customers are leveraging Microsoft Information Protection solutions to classify, label and protect their data. To minimize the impact on end users and their ability to be productive, these organizations often choose to empower their users to label documents themselves, by providing automatic suggestions but not auto-labeling or -protecting documents. A user can inadvertently label a document containing highly confidential information with a low sensitivity label that applies minimal access restrictions. Since the file is already encrypted, it will not be scanned by the DLP solution, but might still be accessible to unauthorized people. A bigger threat with a much higher potential for damage, is the malicious insider.
How secure is Android? Separating the myths from the facts

Google’s effort has been to continually harden the Android platform. Security is an ongoing enterprise, evidenced by new innovations like an improved security model for biometrics and industry-leading capabilities that protect sensitive information on a secure, dedicated chip. An important top-line defense is through Android’s monthly security updates. Devices that are part of the Android Enterprise Recommended program receive the monthly Android security patch, guaranteed within 90 days of release. Another key innovation is the Titan M chip found in Pixel 3. The chip is integrated into Android’s Verified Boot process, ensuring the bootloader, the program that validates and loads Android, is running the correct version. This prevents bad actors from moving the device to a more vulnerable version of Android clandestinely. While debuting on the Pixel, the security community will be able to audit Titan through the open-source firmware. Google Play Protect, the world’s largest mobile threat-detection service, defends against Internet-borne threats and potentially harmful apps (PHAs).
Cybersecurity Staffing in Crisis: What Can You Do?

Many enterprises find it easy to think of cybersecurity professionals as stemming exclusively from the STEM fields. In many ways this makes sense; IT security obviously builds itself on technology and algorithms, which would be second nature to those interested in the hard sciences. However, being too selective in the security hiring process contributes to the cybersecurity staffing crisis; it means enterprises turn away perfectly qualified candidates for not having the “right” degrees. STEM skills can strengthen your cybersecurity posture, of course. However, your InfoSec team requires other skills such as collaboration, communication, adaptability, and creativity to be fully well-rounded. What matters in a candidate may not be the knowledge of information technology but the capability of learning about technology in a productive manner. Additionally, you need to make sure you draw upon a diverse pool of information security professionals. Drawing only from a homogenous pool contributes to the cybersecurity staffing crisis.
Quote for the day:
"Leadership involves finding a parade and getting in front of it." -- John Naisbitt
No comments:
Post a Comment