
IoT devices are a favorite weapon for attackers who use them to penetrate local networks and conduct other attacks. As consumers slowly learn how to protect their PCs and mobile devices, they will also need to learn how to stay safe as more of their traditional appliances go online. The security industry, too, will have to adjust to this new reality. On a related note, as it is the network that many of these devices will eventually exist on, the gradual introduction of 5G is likely to bring challenges in 2019. For example, Verizon and Samsung have already announced that they will offer 5G smartphones in the U.S. This is a key issue because the telecom industry has always had a turbulent relationship with security. For example, although operators are well aware of potential issues, 78% of telecom networks are vulnerable to attacks. SMS interception, for example, is still possible in nine cases out of 10.
How the future of work may unfold: A corporate demand-side perspective
Corporate labour demand is estimated as a function of AI diffusion at the corporate level, based on answers to a global survey covering more than 3,000 executives across 14 sectors and ten countries. The survey answers were weighted based on the relative size of companies6 . The rough data suggest that a decline in employment is not inevitable, with only 19% of answers suggesting that employment levels will be down (although only 10% of firms will systematically increase employment). The largest expectations of decline were in the sectors that are most advanced in their use of AI, such as media telecom or high-tech services, but the same is true with respect to the largest share of firms expecting to grow employment with respect to AI, suggesting that the type of AI diffusion is as important as AI itself in determining the direction of labour demand.
What Countries and Companies Can Do When Trade and Cybersecurity Overlap

Since it is not feasible to thoroughly examine the software, firmware, and hardware of every single product, what should countries and companies do to prevent cyber intrusions? One seemingly obvious approach is to exclude from import potentially dangerous products from questionable countries. But this approach requires identifying which products are dangerous and which countries are questionable — a formidable task. And such restrictions can quickly become policies, with implications for international trade and the world economy. Countries and companies need to consider their options. At present, there is no framework for understanding and categorizing the cybersecurity concerns involved in trade. Without a clear understanding, governments may implement policies that result in cyber conflicts, while businesses will struggle to keep up with how cybersecurity concerns and restrictions are evolving.
Conquering the Challenges of Data Preparation for Predictive Maintenance
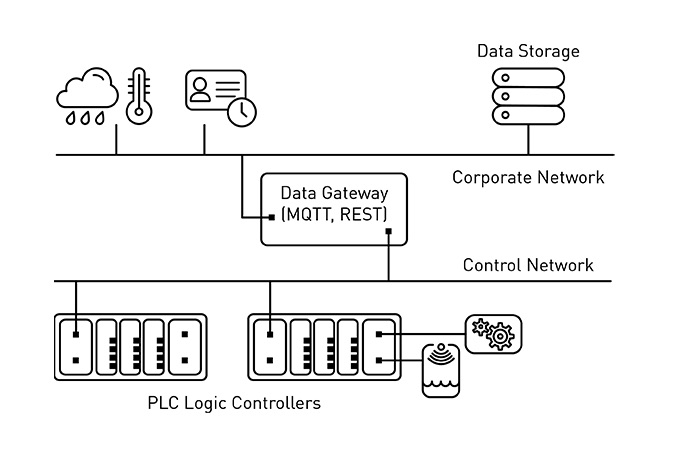
The first step required for PdM involves data acquisition. Industrial instrumentation is most often associated with measurements of physical quantities such as vibration, infrared heat, electrical current, metal particles in grease, etc. This data typically originates from sensors attached to programmable logic controllers within an industrial control network. Data gateways that bridge control and corporate networks facilitate access to that data via developer-friendly protocols, such as REST and MQTT. It’s also important to consider out-of-band data sources, such as operator logs or weather data, because they can also contain signals that correlate to failure events. Figure 1 below illustrates the interconnections between these types of data assets. Data ingestion is accomplished by processes that continuously collect and store data. These processes can be implemented as custom applications but are generally much easier to develop and manage using a dataflow management tool, such as StreamSets or Apache Nifi.
RIP ICOs: 2019 Will Be the Year of Enterprise Blockchain Tokens

It turns out that the first killer app of the internet was not email. It was the ridiculously simple web page. The first killer app of blockchain is the ridiculously simple token. A token is a mere smart contract that encapsulates the rules governing the exchange of an asset. Once this contract can be generated from an underlying legal contract and shown to execute in line with the legal contract, regulated, legally sound applications of blockchain become possible. This is a big deal. It turns out, all economic activity, micro or macro is built on top of legal contracts. Unfortunately, because of information asymmetries, cost of enforcement, the risk of disputes and uncertainty in legal systems, the cost of contracting in too many transactions can exceed the benefit of the transaction. Smart contracts that execute in line with legal contracts provide evidence of state on-chain and ship with dispute resolution systems can dramatically reduce the costs of contracting and the cost of enforcement, unlocking economic activity across industries and economies.
SaaS Business Models Analyzed

One thing startups and SMBs should keep in mind when working on an idea they want to implement in the form of SaaS is good user feedback and testing before product launch. I know from personal experience that companies in the SaaS space often want to put a product out there before it is really ready to go mainstream and let the market handle it. They do not have patience to wait for critical feedback in the form of beta testing or focus groups ahead of launch. This can turn potential customers or early adopters away and it may be hard bringing them back later once they have the distaste for the product. A free trial mitigates this in many ways and is really the most important thing along with a good user interface companies should be looking at when launching a product. Trials will let users know they can opt out of the product anytime and the best ones for SaaS
IT Operations and Developers – Can’t We All Just Get Along?
Although old habits die hard, IT Ops and Dev need to realize they will benefit from an improved relationship. The survival of your business could very well depend on it. If your company can’t develop and innovate fast enough, your competition will overtake you. For example, ten years ago, who would have thought you could buy a mattress in a box and have it shipped to your door? Even more surprising, who imagined a service to have your teeth straightened—without expensive and time-consuming dental visits? Just take some pictures, send in a mold, and you’ll be sent a new set of aligners monthly to achieve your perfect smile. Your IT Ops team needs to understand and acknowledge the efficiency and productivity gains the Dev team needs through feature releases. Likewise, your Dev team knows they need to partner with IT Ops to ensure they have the resources they need to deliver services faster.
Enterprise Agility in the Norwegian Government
One huge enabler for business alignment has been our new application architecture. We are working hard to move away from a complex architecture, with a lot of dependencies and mainframe solutions to self-developed applications that are Java-based - which all use NAV’s container platform, NAIS (NAV = The Norwegian welfare and labor administration). Microservices are responsible for functionality and data within their area. Events and data become available for other services and for analysis through data streams. These data streams create loose couplings. Our efforts with people, processes and the application architecture now make it possible for us to work in business domains, based on life events. In short, teams within the domains can work decoupled from other teams, gaining development speed and without project overhead. Each of these domains will be led by the business side, and will consist of several functional product teams, with one goal – to deliver value within their field.
The overall point here is that these shifts are to be expected over time. However, anticipating shifts -- and building in instrumentation to know about them -- separates the best programs from the merely adequate. So how can we build this level of understanding and future-proofing into our programs? To begin with, there is no shortage of risk models and measurement approaches, systems security engineering capability models (e.g. NIST SP800-160 and ISO/IEC 21827), maturity models, and the like -- but the one thing they all have in common is establishing some mechanism to be able to measure the overall impact to the organization based on specific controls within that system. The lens you pick -- risk, efficiency/cost, capability, etc. -- is up to you, but at a minimum the approach should be able to give you information frequently enough to understand how well specific elements perform in a manner that lets you evaluate your program over time.
Stop the Presses: Don't Rush Tribune Ransomware Attribution
The appearance of Ryuk led some media outlets to rush to connect the attribution dots and suggest that North Korea had attempted to disrupt U.S. newspapers. That's because Ryuk's code shares numerous similarities with Hermes ransomware, as software and hardware IT firm Check Point Software noted in a report released in August. The U.S. government later incorporated that information into its own alert about Ryuk. "Our research led us to connect the nature of Ryuk's campaign and some of its inner-workings to the Hermes ransomware, a malware commonly attributed to the notorious North Korean APT Lazarus Group, which was also used in massive targeted attacks," Check Point says in its August report. But Check Point emphasized that Ryuk's reuse of Hermes code proves nothing.
Quote for the day:
"Success is not how high you have climbed, but how you make a positive difference to the world." -- Roy T. Bennett


No comments:
Post a Comment