Windows Hello is designed for both enterprises and consumers, and is gaining traction on both fronts. During Microsoft’s Ignite 2017 conferencein September, the company announced more than 37 million people were already using Windows Hello and more than 200 companies had deployed Windows Hello for Business. At the time, the largest enterprise deployment outside of Microsoft’s IT team comprised more than 25,000 users, according to the company. “Biometric fingerprint scanning is prevalent in the enterprise, but the issue is that it’s not readily used,” Moorhead said. Every major vendor has systems using Windows Hello, according to Moorhead, but market penetration is much lower than needed to start the process of replacing passwords for all Windows 10 users.
IoT: The catalyst for invisible payments
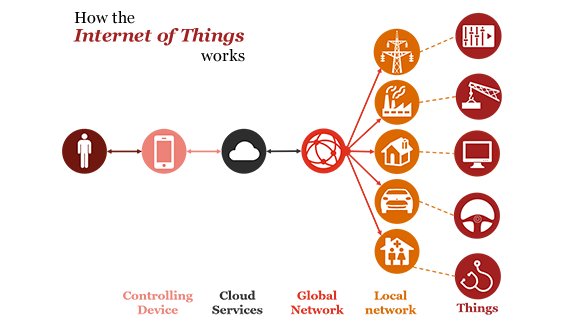
Long before the advent of today’s smart wrist wearables, we saw Hollywood’s James Bond using his watch to receive messages from headquarters, and long before any company began prototyping connected cars, we saw him in high-speed car chases by navigating through the streets in his smart car augmented with sensors. Previously the domain of fantasy, such devices are now becoming a reality as a new class of tools accessible to the government, consumers and businesses alike. The Digital Age—which makes the Industrial Revolution look tame by comparison—is upon us. The Internet of Things (IoT) has rapidly become one of the most familiar expressions across the technology domain, with the potential to fundamentally shift the way we interact with our surroundings. Everyday objects are getting smarter and connected to the internet, thereby enabling the seamless transfer of information streams between devices, networks, organisations, industries and end users.
“Private blockchain” is just a confusing name for a shared database
The key to Bitcoin’s security (and success) is its decentralization which comes from its innovative use of proof-of-work mining. However, if you have a blockchain where only a few companies are allowed to participate, proof-of-work doesn’t make sense any more. You’re left with a system where a set of identified (rather than pseudonymous) parties maintain a shared ledger, keeping tabs on each other so that no single party controls the database. What is it about a blockchain that makes this any better than using a regular replicated database? Supporters argue that the blockchain’s crypto, including signatures and hash pointers, is what distinguishes a private blockchain from a vanilla shared database. The crypto makes the system harder to tamper with and easier to audit. But these aspects of the blockchain weren’t Bitcoin’s innovation!
5 Trends to Watch in Banking Technology in 2018

APIs, artificial intelligence, easier mobile banking, new forms of security authentication and the Internet of Things will help banks modernize their technology.Of course, mobile banking is nothing new, but it is now a “table stakes” experience, especially for younger bank customers, meaning it is a bare minimum all banks must now meet. If a bank does not have a solid mobile app, they are an also-ran, industry experts and analysts say. That way of thinking will soon apply to lots of new and emerging technologies, as banks strive to keep pace with the likes of Apple, which earlier this month introduced Apple Pay Cash, allowing customers to send and receive money via Apple Pay. “The big decision-makers are really leaning on the idea of, ‘Mobile technology is taking over and there is a digital-first movement that is taking hold in the marketplace,’” says Chris George, senior vice president of client strategy at NYMBUS, a core banking modernization company.
Building the Cyberresilient Health Care Organization
The cyberrisks to the health care industry include much more than ransomware and threaten more than hospitals. Imagine a WannaCry type of attack that targets implanted medical devices, for example. The digitization of health care, which is bringing more digital products and services into more widespread use, puts health care organizations in the cybercriminal’s cross hairs. Moreover, because of the data that health care companies collect, the life-and-death nature of their services, and the increasing interconnectivity of tools and devices, cybersecurity is no longer only an IT issue. ... The potential for damage goes beyond financial malfeasance: as supply chains, manufacturing processes, and distribution channels become increasingly digitized, often with outdated devices that have limited vendor support or security management, they present a sabotage risk with potentially disastrous patient health and safety, financial, and reputational consequences.
Year In AI: Higher Education For Machines

2017 was the year “rules-based” became a dirty word in AI. Rules-based algorithms do exactly what one may expect: they follow rules, nothing more, nothing less. They are based on past observation. While they’re good at going through lots of data really fast, they cannot exercise any sort of discretion. If a fraudster figured out the rules and started to work around them, rules-based AI couldn’t catch him, because to that machine, the bad guy would appear to be playing by the rules. Only after a human identified the pattern and fed the machine a new set of rules would it be able to catch the fraudster. A platform like, say, Fraugster, analyzes and learns from transactions in real time, collecting over 2,000 data points, such as name, email address and billing and shipping address. All of this data is then sent to be analyzed by the company’s artificial intelligence engine, which then reviews each transaction’s data individually for signs of fraud.
Blockchain and Voting
A public ledger of plain votes is a terrible idea, since that makes vote selling trivial. A public ledger of vote tracking numbers of sorts is better for privacy, though it doesn’t really provide actual verifiability that the contents of the ballot weren’t tampered with. Clearly, we need something more, and that something simply isn’t provided by a distributed ledger. Then there’s the need to check voter eligibility, a critical piece of global verifiability. No matter what technology we use, we need a clear list of eligible voters, and each voter should get to vote only once. Ultimately, the list of eligible voters is set in a centralized way: it’s produced by the State. There’s nothing distributed about voter eligibility. Even when there is federation / delegation to individual counties, like in the US, there is a centralized effort to cross-check that a voter isn’t registered in multiple counties.
Automating machine learning puts analytical models on autopilot

The trend makes sense, Schubmehl said, because the benefits of machine learning are so obvious, yet the highly educated data scientists needed to develop machine learning applications are so scarce. Every enterprise stands to benefit from becoming more data-driven, yet developing capabilities internally is expensive and time-consuming. "There is a shortage of data scientists, so that makes it more challenging," he said. "This idea of low-code or no-code AI is really a great capability. Automated machine learning helping to drive the enterprise is really where our research is pointing to." Still, that doesn't mean that automating machine learning automatically delivers a return on investment. Schubmehl described it as a hand-and-glove situation. In this analogy, data is the hand and software is the glove. If the data isn't there, the software can't accomplish much.
Bitcoin's Academic Pedigree
How can you build a ledger for use in an environment like the Internet where participants may not trust each other? Let's start with the easy part: the choice of data structure. There are a few desirable properties. The ledger should be immutable or, more precisely, append only: you should be able to add new transactions but not remove, modify, or reorder existing ones. There should also be a way to obtain a succinct cryptographic digest of the state of the ledger at any time. A digest is a short string that makes it possible to avoid storing the entire ledger, knowing that if the ledger were tampered with in any way, the resulting digest would change, and thus the tampering would be detected. The reason for these properties is that unlike a regular data structure that's stored on a single machine, the ledger is a global data structure collectively maintained by a mutually untrusting set of participants.
Getting Started with Microservices in SpringBoot

If you are not already using Microservices, you are safely out of the early adopter phase of the adoption curve, and it is probably time to get started. In this article, we will demonstrate the essential components for creating RESTful microservices, using Consul service registry, Spring Boot for all the scaffolding, dependency injection, and dependencies, Maven for the build, and both Spring REST and Jersey/JaxRS Java RESTful API. Over the last two decades, enterprise has become very agile in our SDLC process, but our applications tend to still be rather monolith, with huge jars supporting all of the varied APIs and versions in play. But nowadays there is a push towards more Lean, DevOps-ey processes, and functionality is becoming “serverless”. Refactoring to Microservices can decouple code and resources, make builds smaller, releases safer, and APIs more stable.
Quote for the day:
"Leaders always choose the harder right rather than the easier wrong." -- Orrin Woodward

No comments:
Post a Comment