Bitcoin, Blockchain and Gold: A Year of Disruption
Genesis Mining is the largest cloud bitcoin mining company and is growing rapidly, adding 50,000 people a day, and now has more than 2 million users. HIVE has an exclusive arrangement with Genesis to operate its data centers, so HIVE offers the opportunity to invest in the cryptocurrency sector without investing in bitcoins themselves. ... Another factor is the success of the quantitative approach, which results in very low volatility. Quants have upended the market using artificial intelligence and other algorithms. Using data mining, algorithms will direct trades within seconds. Some 60% of daily trades are now quant driven, and the average holding period of a stock is about four days. So, things are moving at a much faster pace. Here’s one example: CIBC looked at 200 case studies and found that when a company’s press release had one of seven different headlines, the stock would fall 25%.
Four tips for moving to a new managed SD-WAN service provider

Knowing what went wrong can help customers specifically select a new provider to fix the problem. Perhaps the existing provider's chosen platform turned out to be a bad fit for the customer's actual WAN usage. Maybe the provider failed to meet service-level agreements. Perhaps the provider's support organization is understaffed or experiencing major turnover that affects service. Or, maybe the provider is bad at managing third parties, like last-mile connectivity providers, for example. Whatever the reason, make sure the wisdom of experience informs the selection of the new managed SD-WAN service provider. ... If the provider makes the change-over experience difficult, it loses any chance of winning other areas of your business, winning you back in the future or getting a good recommendation from you.
Small and Medium Business Security Strategies, Part 1: Introduction
This look is to be expected at this point. You might be asking something along these lines: What are secure configurations? How can I possibly understand “Limited Admin Privilege?” Seriously, what is vulnerability assessment and remediation? We are going to start slow, set realistic goals and will work together to get your network under control. So where to from here? No one has time, no one wants extra duties and everyone has to step in and participate. Based on experience, most offices, businesses, schools, et cetera have someone around who knows about computers. This person is usually the go-to resource for broken printers, blue screened workstations and internet outages. This person is an asset and should serve as a guide for this process. They can answer questions and will definitely know what a modem, switch and router look like.
5 Digital Transformation Trends for Healthcare Industry in 2018
When we are talking so much about the digital transformation in the healthcare sector, do we really know what it is and how it helps? Digital transformation is not just about buying new technologies and latest tools that can ease the process of healthcare procedures, but it is also about changing the operational process in the healthcare sector and making it more automatic and efficient. Digital transformation focuses more on information handling. If the information gathered from the modern digital devices can be channelized effectively, it can be structured to give automated responses to the existing and upcoming health problems. Merely purchasing a technology will not produce any result. There must be a plan about how we are going to use that technology to engage with the whole process of health care revamp. In some parts of the world, the planning to engage digitization with healthcare has started to produce results.
Could Blockchain Transform the Direct Selling of Insurance and Annuity Products

Currently, there is no central authority maintaining or clearing these transactions. Each broker-dealer must maintain their own book of business. For a registered broker-dealer FINRA 17a-3 regulations require the on-going maintenance of client books and records, which is a process that would be greatly simplified by allowing the client to maintain their information directly through to the ledger. This would replace the current method of mailing letters and the subsequent manual process of updating account owner and registration information. Of course, challenges remain for the wider use of DLT until solutions for issues such as scalability and the integration with legacy systems are developed. The development of APIs is necessary to provide the integration with off-chain legacy business applications. These challenges limit wider implementation of the technology.
The 6 stages of an Advanced Ransomware Threat attack

In the ransom phase, attackers deploy ransomware to data stores where target business data resides. The ransom is timed for the date when it will have the most impact, such as just before a major announcement, during mergers and acquisitions, or surrounding audits. They may use any flavor of ransomware as long as it effectively makes the data unavailable and gives the attacker the only keys to decrypt it. ... As mentioned, there is no single form of ransomware used in ARTs. Attackers may perform the encryption using custom programs or they may use a combination of ransomware variants to encrypt data on different types of devices such as Macs or Linux servers. Finally, be aware that some attackers use ARTs as a diversion. The attackers may have already stolen the data they wanted, so they manually infect the systems with ransomware, counting on the company to wipe machines and restore from backup, thus erasing any remaining evidence of the cybercriminal’s presence.
Mobile Internet is Helping Chinese Financing Soar to New Heights
As an “upstart” rising sharply in the field of the global Internet, the developmental speed of Internet finance in China is also amazing. The number of people purchasing Internet financial products has reached 500 million, and the scale of Internet asset management has seen eight-fold increase over the last 4 years. More Chinese people directly manage their financial matters on a PC and mobile device, instead of going to the bank. Practitioners of Internet finance represented by Tianhong Asset, based on the Alipay platform of the controlling shareholder Ant Financial, have realized efficient interaction and promotion both online and offline, providing their investors with a more efficient and convenient financial experience.In China’s Internet finance industry, Tianhong Asset has set up the industry’s first cloud-based De-IOE large settlement system – Tianhong Asset Management Cloud Direct Marketing System.
AI technology adoption: What’s holding us back?

While AI adoption is beginning to prove its usefulness in many industries, it needs to have access to the right data in order have meaningful impact. Strong data quality underpinning machine learning will amplify the efficiency of organisation, and never has the phrase ‘quality in, quality out’ been more relevant. While organisations have mountains of data to sift through, strong data quality underpinning machine learning will amplify the efficiency of your business. In terms of critical success factors, context sits right alongside data quality. Chatbots are a good example of efficient machine learning currently in implementation, and of the importance of context in producing a useful outcome. While the term ‘self-learning’ is often subscribed to AI it can be misleading. It is only by acquiring more data over time and understanding the context in which this information can be accurately used that AI can improve overall performance and start to deliver real business value
Cloud API And Management Platforms & Middleware Market To Increase

Cloud API and management platforms and middleware market is fast picking up pace due to wide adoption of mobile and cloud applications for back-end services and wide adoption of microservices based architectures by enterprises. These applications comprise of small, independent processes that communicate via API, thereby creating demand for cloud API and management platforms. Emergence of Internet of Things also has a pivotal role to play in the growth of cloud API market as more number of connected devices requires more analysis and monitoring at a fast rate that can be done through cloud APIs. In addition to this several start-ups and small scale enterprises are adopting assemble from components methodology that enables end users to use APIs to connect apps to IT assets, resulting in growth in usage of cloud APIs.
New Seagate tech promises to double hard drive speeds
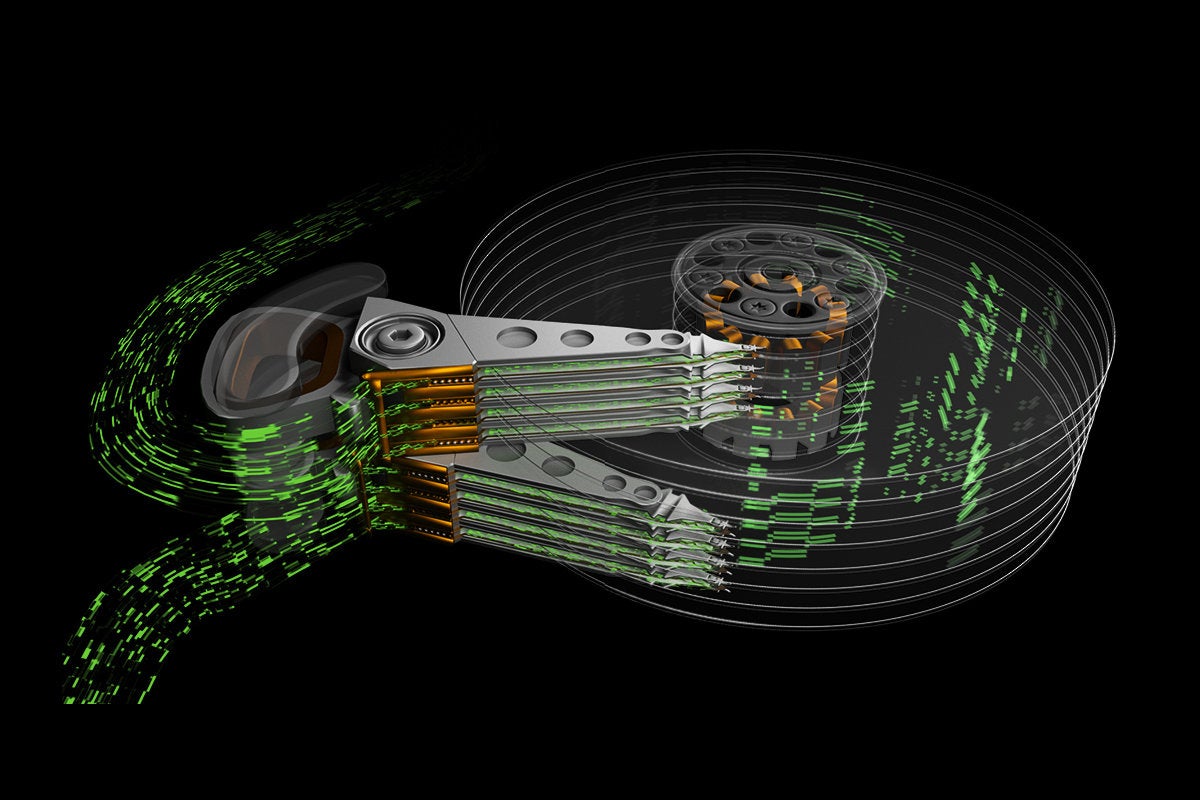
Seagate has a high-density technology in the works called Heat-Assisted Magnetic Recording (HAMR), set to launch next year and in volume in late 2019, that will deliver hard disks of 20TB and more. Western Digital has something similar in the works at roughly the same timeframe. These drives will have up to eight storageplatters, and performance overall will suffer if the network is choking while waiting for data to load. “Capacity is only half of the solution. If the ability to rapidly access data doesn’t keep pace with all that capacity, the value potential of data is inhibited. Therefore, the advancement of digital storage requires both elements: increased capacity and increased performance,” Seagate said in its blog. The only way to make hard drives faster was to make them read and write faster without spinning the disk at a higher speed, so the multiple actuator drive technology makes sense.
Quote for the day:
“Learning does not make one learned: there are those who have knowledge and those who have understanding. The first requires memory and the second philosophy.” -- Alexandre Dumas
No comments:
Post a Comment