Data or Algorithms – Which is More Important?

Most of you will recognize that this was also the birth of the era of Big Data, because Hadoop for the first time gave us a reasonable way to store, retrieve, and analyze anything. The addition of unstructured and semi-structured data like text, speech, image, and video created the possibilities of AI that we have today. It also let us store volumes of ordinary data like web logs or big transactional files that were previously simply too messy to store. What you may not know, and I heard Doug Cutting himself quote at this last spring’s Strata Conference in San Jose is that the addition of unstructured and semi-structured data are not the most important feature of Hadoop. The most important feature is that it allowed many ordinary computers to function as a single computer. This was the birth of Massive Parallel Processing (MPP). If it hadn’t been for MPP the hardware we have today would never have evolved and today’s data science simply would not and could not exist.
12 Tips For Using Devops To Fuel Digital Transformation

DevOps automates software assembly, leveraging continuous integration, development and deployment, to improve customer experiences, respond faster to business needs, and ensure that innovation is balanced with security and operational needs. You can think of DevOps as agile on steroids. And it is catching on. Fifty percent of 237 organizations surveyed said they are implementing DevOps, according to Forrester Research. "The DevOps momentum is occurring within all industry sectors," analyst Robert Stroud wrote in the research report. "As we are near the end of 2017, the number of inquiries are increasingly focused on how organizations will be successful given the pressure of accelerated delivery of applications and services — without additional headcount."
CTO Perspectives: The roots of OpenStack and the multi-cloud
Every technology shift that has happened, we’ve taken our customer intimacy, our customer focus, and applied it as the shifts happened. Even to this day, it has continued to serve us well. Cloud was the biggest shift. Rackspace jumped in pretty early and it was a big shift for us when we started to build our own cloud and software for the first time. We wrote some software for our ticketing system and our customer management systems. This software was part of the product that was going to deliver the cloud, and eventually became OpenStack. That legacy has served us well, because it’s now the foundation for our public cloud and also all the work that we are doing on OpenStack private cloud. Even during the cloud era, that emphasis and focus on great customer service and great customer outcomes was important – and valuable, because we created something that we call “managed cloud”.
Four ways state and local CIOs can boost cybersecurity
IT operations in state and city government are often run by the various agencies within the government, rather than being centralized under the state’s or city’s CIO. This leads to shadow IT, with a wide range of servers, software, and hardware spread across the state and city, and no standardized way to measure their risk level or even know when systems need to be updated. IT administrators cannot share best practices, causing further inefficiencies. What’s worse than shadow IT? Shadow security — rogue systems with no security features turned on. Fortunately, some states and cities have made significant efforts toward consolidating and federating their IT, and the broader trend is toward consolidation, as NASCIO reported in its survey of state CIOs.
Why cryptocurrencies are causing an international racket
Today one of the biggest challenges faced by cyber extortionists is how they obtain the cash. In the past, they would ask victims to deposit money into bank accounts or transfer funds via the likes of Western Union, all easily traceable. Fast forward to today and we have a myriad of decentralised cryptocurrencies like Moneto, Ethereum, and the most popular Bitcoin, which offer users fast transactions with full anonymity. If you're a cyber extortionist - what's not to love? This major development can be linked to the escalation in ransomware attacks across the world, being easy to use without the need for any middleman to transact. According to a study earlier this year by 2Cambridge University, there are now over 6 million people transacting with Bitcoin, the majority of which is legitimate business.
2017: A year of highs and lows for Linux and open source
Linux users had to suffer release after release, where next to nothing improved on the Ubuntu desktop front. This was a mistake of grand proportions and sent a lot of users scurrying to the likes of Linux Mint or Elementary OS. ... Samsung has opted to resuscitate Linux and convergence, with the help of their Galaxy line of smartphones and DeX. If you're unfamiliar with DeX, it's a dock that enables users to plug in a supported Galaxy device and enjoy a desktop experience, powered by their smartphone. In the midst of 2017 passing, Samsung made the announcement they were developing an app called "Linux on Galaxy," which would allow users to boot their favorite distribution (or multiple distributions) of Linux on their Galaxy S8+/Note8 devices, and take advantage of DeX—so a full-blown Linux desktop, powered by a smartphone.
Hacking the Autonomous Vehicle
"Today chip-tuning is already used to change the management of the engine and find additional horsepower. This is in most cases legal, but liberates the car manufacturer from its guarantee. When self-driving cars are a relevant market, it is a question of time, when programmers will offer software to ensure a higher safety for their owners, programmed preference for the passenger against the pedestrians.” In the same way that there are after-markets for computer chips that override the engine performance settings that come with the automobile out of the factory, will there evolve an after-market for technicians who can “hack” the life-and-death settings that are pre-programmed into an autonomous vehicle? We are already seeing situations where customers are resorting to “hacking” their vehicles. Farmers are hacking their John Deere tractor’s firmware
Is Your Technology Function Ready For A Digital World?
Most large companies are using digital technologies to do things such as launch apps, build e-commerce solutions and harness data to learn more about their customers. But these “quick hit” efforts inevitably fall short of their goals when they must contend with legacy IT systems and data that can’t interface with new digital apps and architectures. Data is scattered across the company, rendering it useless. Outmoded and sluggish IT operating models slow the company down. The companies that take digital to its full potential learn to integrate their front-end digital solutions with their aging legacy stack. They build technology functions that are flexible, fast, collaborative and creative–hardly the adjectives most companies use to describe their IT departments. But unlocking the true potential of technology can be transformative.
Lenses Are Being Reinvented, and Cameras Will Never Be the Same
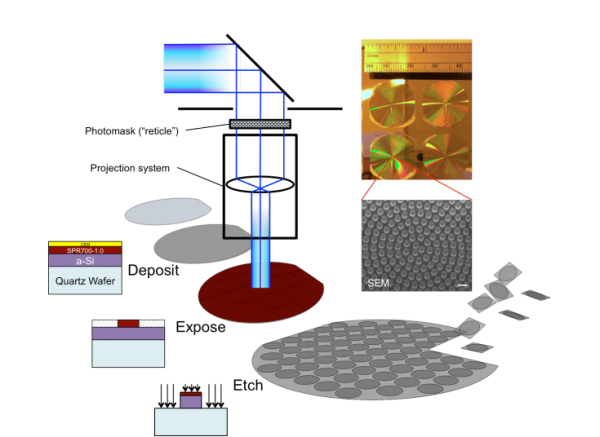
In imaging lenses, chromatic aberration must be minimized—it otherwise produces the colored fringes around objects viewed through cheap toy telescopes. But in spectrographs, different colors must be brought to focus in different places. She and co can do either. Neither do these lenses suffer from spherical aberration, a common problem with ordinary lenses caused by their three-dimensional spherical shape. Metalenses do not have this problem because they are flat. Indeed, they are similar to the theoretical “ideal lenses” that undergraduate physicists study in optics courses. Of course, physicists have been able to make flat lenses, such as Fresnel lenses, for decades. But they have always been hard to make. The key advance here is that metalenses, because they can be fabricated in the same way as microchips, can be mass-produced with subwavelength surface features.
Introducing Obevo: Get Your Database SDLC Under Control

While existing open source tools could do the job for simpler cases, they could not handle the scale and complexity of some of our existing systems. And we could not just leave these existing systems without a proper SDLC; they are critical systems with active development and releases. Thus, we developed Obevo (available under the Apache 2.0 License), a tool to handle all such use cases. Obevo’s key differentiator is the ability to maintain DB objects per file (similar to how class definitions are typically stored per file) while still handling incremental deployments. In this article, we will describe the DB Deployment problem space and then demonstrate how the object-based project structure helps us elegantly manage hundreds and thousands of schema objects for a variety of object and environment types.
Quote for the day:
“Be who you are and say what you feel, because those who mind don’t matter and those who matter don’t mind.” -- Dr. Suess
No comments:
Post a Comment