Generative AI is sliding into the ‘trough of disillusionment’

“Even as AI continues to grab the attention, CIOs and other IT executives must
also examine other emerging technologies with transformational potential for
developers, security, and customer and employee experience and strategize how to
exploit these technologies in line with their organizations’ ability to handle
unproven technologies,” Chandrasekaran said. ... Autonomous AI software was
among four emerging technologies called out in the report because it can operate
with minimal human oversight, improve itself, and become effective at
decision-making in complex environments. “These advanced AI systems that can
perform any task a human can perform are beginning to move slowly from science
fiction to reality,” Gartner said in its report. “These technologies include
multiagent systems, large action models, machine customers, humanoid working
robots, autonomous agents, and reinforcement learning.” Autonomous agents are
currently heading up the slope to the peak of inflated expectations. Just ahead
of autonomous agents on that slope is artificial general intelligence, currently
a hypothetical form of AI where a machine learns and thinks like a human does.
As Fintechs Stumble, A New Breed of ‘TechFins’ Move to the Fore
TechFins have provided many points of value in recent years, but particularly in
2024 and in the near future, they will highly benefit financial institutions in
the areas of: Leveraging the power of transaction data cleansing and
analysis; Artificial intelligence (AI); Fraud prevention and cost
mitigation; Extending the personalized user experience and reliability of
the digital banking application; Transforming digital banking platforms
into a digital sales and service platform; Increasing revenues and lowering
costs for financial institutions. With financial institutions amassing high
volumes of transaction data within their ecosystems, processing and analyzing
that data is becoming a greater priority. According to the Pragmatic Institute,
data practitioners spend 80% of their valuable time finding, cleaning, and
organizing the data. This leaves only 20% of their time to actually perform
analysis on it. This is the 80/20 rule, also known as the Pareto principle.
TechFins can provide vital support to financial institutions’ data teams through
transaction cleansing, leaving them more time to build campaigns and take action
on the data.
The Developer Crisis: Mental Health, Burnout, and Retention

Seven out of 10 developers state that job satisfaction is the most important
factor. Unplanned extra tasks and excessive overtime will have developers
looking for the door. Businesses need to make it clear to both existing and new
hires that they will do everything they can to respect these boundaries.
Developers encounter constant roadblocks in their work, so time is precious. To
help devs maintain a “flow state” (total focus on the task), businesses should
consider re-evaluating their calendars to reduce unnecessary meetings. If not
implemented, software development frameworks could help dev teams better
organize their work and progress through projects faster. As with any
operational change, feedback is critical. ... By freeing developers from
burdensome backend duties, they can stay creative and focus on developing
innovative new frontend solutions to improve a customer’s overall experience.
This makes brilliant business sense, particularly in the case of e-commerce,
where standard feature developments, which would otherwise take up tons of
developer resources, can be handled much more efficiently by a tech platform.
Vulnerability prioritization is only the beginning
Scrutiny of cybersecurity processes and performance is ratcheting up due to the
dual hammers of increased regulatory scrutiny and the brutal trend of highly
damaging attacks. The US Securities and Exchange Commission, the European Union,
the US Department of Defense, the British National Government, and the US
Cybersecurity and Infrastructure Agency have all put or are putting in place
significantly more stringent requirements for CISOs and their teams. Both the
SEC and CISA have moved to push accountability to the Board of Directors and the
C-Suite. This means that metrics alone are no longer sufficient for CISOs that
want to provide full transparency. Process transparency has become just as
critical to validate KPIs and allow auditors and the government to peer inside
what were formerly security process “bottlenecks”. These bottlenecks are highly
variable, human-centric processes, such as opening or closing a Jira ticket,
back and forth commenting in a Slack thread, pushing a pull request on GitHub,
or running a CI/CD pipeline to test and redeploy software after a patch. All can
have human path dependencies, injecting uncertainty and variability.
Authentication and Authorization in Red Hat OpenShift and Microservices Architectures
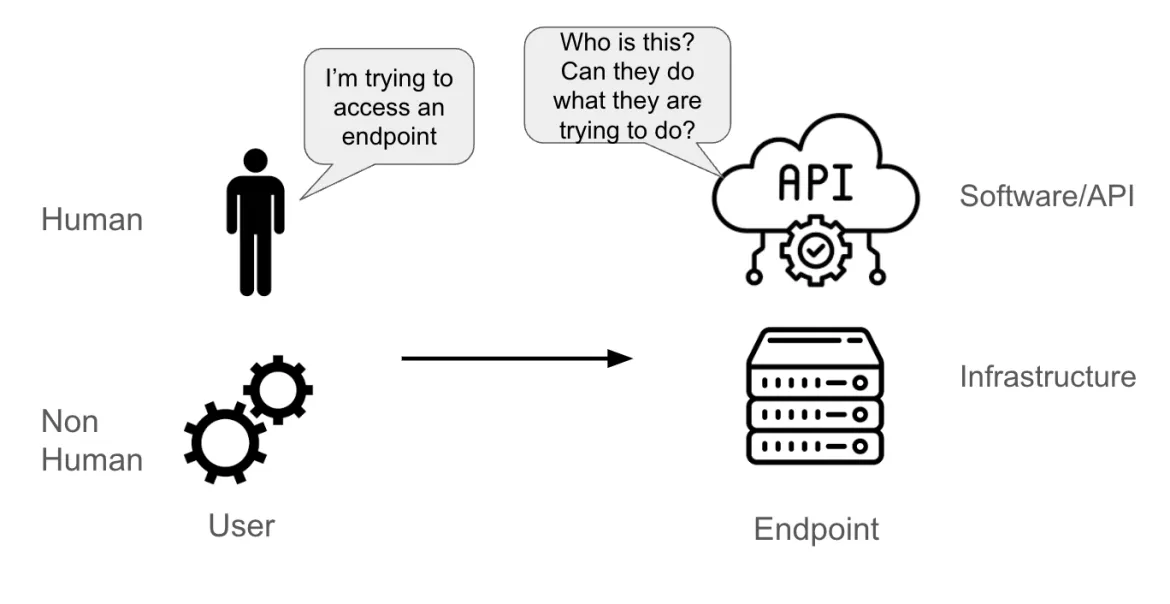
Moving up the layers and looking at the blue layer (that is, interacting with
OpenShift or Kubernetes in general) means communicating to the Kubernetes API
server. This is true for both human and non-human users, whether they're using a
GUI console or a terminal. Ultimately, all interaction with OpenShift or
Kubernetes goes through the API server. The OAuth2/OIDC combination makes
perfect sense for API authentication and authorization, so OpenShift features a
built-in OAuth2 server. As part of the configuration of this OAuth2 server, an
supported identity provider must be added. The identity provider helps the
OAuth2 server confirm who the user is. Once this part has been configured,
OpenShift is ready to authenticate users. For an authenticated user, OpenShift
creates an access token and returns that token to the user. This token is called
an OAuth access token. ... Users and Service Accounts can be organized into
groups in OpenShift. Groups are useful when managing authorization policies to
grant permissions to multiple users at once. For example, you can allow a group
access to objects within a project instead of granting access to each user
individually.
Bridging the digital divide: driving positive impact where it is needed most
There are definitely pros and cons to building rural fiber networks. On the one
hand, by nature the construction process is more complex and expensive, but this
typically means that there is little to no competition, leading to higher
customer demand and lower overbuild risk. The challenges are even more acute in
areas that qualify for Project Gigabit subsidies, with barriers including
challenging terrain, geography, and geology, which often increases costs and
extends timelines. Due to the distances being covered, rural rollouts often also
require more permits and wayleaves from multiple landowners, further increasing
complexity. Without subsidies, these projects would not be commercially viable,
but with cost cover of between 60 percent to 80 percent of capex, a defensive
position is created for contract winners, which increases returns for investors,
while also supporting some of the most neglected rural communities. In these
cases, network commercialization is also likely to be more achievable and we are
starting to see a growing evidence base of strong customer cohort penetration in
these projects which supports that thesis.
How IT Leaders Can Benefit From Active Listening

Active listening is crucial for effective leadership, says Justice Erolin, CTO
at BairesDev, a technology services company. "It strengthens team dynamics,
drives innovation, and ensures that all voices are heard," he observes in an
email interview. When IT leaders speak, particularly with business stakeholders,
they often err by assuming everyone understands the taxonomy and language being
used, Chowning observes. "This is frequently the case with technology-related
terminology that we understand well, but which business stakeholders might
define or understand much differently," she adds. "If we start from unequal or
disconnected positions, then we tend to hear something other than what the
speaker intended." IT leaders can improve collaboration by understanding team
members' perspectives and enhancing problem-solving with deeper insights, Erolin
says. It can also help build trust by making team members feel heard.
"Ultimately, leaders will be able to make better decisions through diverse
viewpoints." Erolin notes that BairesDev incorporates active listening skills
into its leadership training program, recognizing the tool's importance in
fostering a culture of trust and collaboration.
Embracing Data and Emerging Technologies for Quality Management Excellence
Traditionally, quality management has been seen through a compliance lens – a
necessary business cost to meet regulations. To unleash QM’s power as a catalyst
for ongoing business growth and customer satisfaction, a fundamental mindset
shift toward a more comprehensive, proactive approach is crucial. In the past,
quality reporting and data tracking were reactive, addressing issues after they
occurred. This fuels a fix-it-later cycle instead of prevention. The needed
cultural change is from reactive to proactive QM. Forward-thinking firms use AI
and predictive analytics to foresee problems before they arise, emphasizing
prevention and continuous improvement. However, some companies remain
regulation-focused due to deep-rooted challenges. Breaking this mold requires
realigning toward customer-centricity, building robust systems that prioritize
satisfaction and ongoing enhancement, with regulatory compliance as a natural
outcome. It’s key to see quality and regulatory goals as aligned to each other
and drivers of commercial growth, not conflicting with each other and inhibitors
to commercial growth.
The reality of AI-centric coding

“Although AI is able to solve many college problem sets and handle
small-to-medium snippets of code generation, it still struggles with complex
logic, large code bases, and especially novel problems without precedent in the
training data. Hallucinations and errors remain significant issues that require
expert engineering oversight and correction,” Nag said. “These tools are far
better at quick prototypes from scratch rather than iterating large
applications, which is the bulk of engineering. Much of the context that drives
large applications doesn’t actually exist in the code base at all.” Tom Taulli,
who has authored multiple AI programming books, including this year’s
AI-Assisted Programming: Better Planning, Coding, Testing, and Deployment,
agreed that the move to great GenAI coding efforts will catch most enterprises
off guard. "These tools will mean a change in traditional workflows, approaches,
and mindset. Consider that they are pretrained, so they are often not updated
for the latest frameworks and libraries. Another issue is the context window.
Code bases can be massive. But even the most sophisticated LLMs cannot handle
the huge amount of code files in the prompts,” Taulli said.
Is AI Making Banking Safer or Just More Complicated?

The rise of AI in fraud detection has been a game changer. Through real-time
analysis, machine learning and pattern recognition, AI tools can flag unusual
transactions and often catch fraud before it occurs. AI's capabilities in
anomaly detection allow financial institutions to be proactive, staying ahead of
cybercriminals. But AI has its flaws. One of the most significant issues is the
high rate of false positives. John MacInnes, a retired professor from Edinburgh,
encountered this new reality firsthand. He tried to send 15,000 euros to a
friend in Austria, expecting it to be a quick and routine transaction. The
process became an ordeal involving the fraud team at Starling Bank. When
MacInnes declined to provide personal messages and tax documents to prove the
legitimacy of the payment, the bank took drastic action - it froze his account.
It wasn't until media wrote about his plight that the bank admitted it went too
far and unfroze the account. This incident sheds light on a growing challenge
for banks: While caution is understandable, overly aggressive fraud prevention
can alienate the very customers they aim to protect.
Quote for the day:
"Difficulties strengthen the mind, as
labor does the body." -- Seneca
No comments:
Post a Comment