Time for a Disaster Recovery Health Check

By law, the board and C-level officers have the responsibility of executing due
diligence and competence in the conduct of company operations and asset
securement. They do not want to see gaping holes and exposures in corporate due
diligence that are due to disaster recovery plans that fail to address new
security threats or the presence of edge technology. This board awareness can
give IT the leverage it needs to prioritize its DR plan update so the revised
plan can cover a much broader IT footprint than just the central data center --
and by doing so, address new risks. A good way to present to the board and
corporate officers a need to invest time and resources into a DR plan update is
to present the need for an update along with the risks of not doing one. This
can be accomplished by describing various disaster scenarios that have actually
happened to other organizations and explain how they could plausibly happen to
the company itself. By showing real life situations, the CIO can present the
most likely disaster scenarios and consequences and what is needed in terms of
plan revisions and investments to minimize those risks.
Mastering HTTP DDoS attack defence: Innovative strategies for web protection
The threat landscape for HTTP DDoS attacks is constantly expanding, with
attackers continually developing new techniques to evade detection. Some common
methods include using HTTP GET or POST requests to consume server resources,
leveraging malformed HTTP headers to confuse web applications, and employing
slowloris attacks that open and maintain multiple connections to the server
without closing them, eventually exhausting server resources. These attacks can
have devastating effects on businesses, including service disruption, loss of
customer trust, and significant financial losses. The need for effective
mitigation strategies has never been more critical. ... While Radware’s products
offer robust protection against HTTP DDoS attacks, it’s essential for businesses
to adopt a proactive security posture. Some best practices include:Regularly
Updating Security Systems: Ensure that all security systems are up to date with
the latest signatures and detection algorithms. Implementing Access Control
Lists (ACLs): Use ACLs to restrict access to resources, minimising the potential
impact of an attack.
5 Cybersecurity Questions Boards Can’t Afford To Ignore

When it comes to cybersecurity incident response, companies need to practice,
practice, practice. For the board, that could look like ensuring there are not
only clear steps in place for what needs to happen should an incident occur but
also ensuring that those steps have been practiced ahead of time in some sort of
tabletop exercise—similar to how you’d practice exiting the building during a
fire drill to know where to go in the event of an emergency. ... While it’s not
a requirement, some businesses have decided to add a cybersecurity or technology
expert directly to the board to guide them on risk. Businesses can decide if
this makes sense for their risk needs depending on their individual risk
profiles. Many former CISOs or former cybersecurity leaders are looking to sit
on or advise boards, as well as businesses’ own CISOs. ... Directors should also
ask themselves if they are budgeting enough for cybersecurity across the
organization. They should also work to understand what financial impacts or even
regulatory fines they could face if they don't invest in cybersecurity
appropriately or report incidents as required. Is your organization investing
enough?
Is it Already Too Late to Get Started with GenAI? No, But the Clock’s Ticking
At some point institutions will bite the bullet and let GenAI interact with
customers or with their live data. Smith believes it will be important to alert
customers when they are offered a product or process in which generative
artificial intelligence plays a role. Both staff and the public must be clear on
this and have confidence in what the bank discloses. Some consumer paranoia
exists about GenAI, but Smith says Accenture research indicates that many
customers will accept its use with their data — if they feel that they are
receiving some benefit in return. Asked for an example, Smith points to a
frequent beef about bank customer service — having to explain a situation all
over again when trying to work out a problem or address a need and being
transferred from one staffer to another. “I shouldn’t have to educate you on
what happened two days ago,” says Smith. “I want to walk in and find that you
already know.” GenAI can help with this type of situation. One last pointer from
Smith concerns the customer experience of using processes controlled by GenAI.
She says that some customer-facing GenAI provides inferior look and feel, which
can become a friction point.
Technical Debt and the Hidden Cost of Network Management: Why it’s Time to Revisit Your Network Foundations

An often-overlooked example of this growing debt is a failure to actively manage
and optimize IP addresses and Domain Name System (DNS) configurations—the very
pillars of corporate network communication. Internet service providers (ISPs) of
dedicated Internet access (DIA) to businesses would often assign blocks of
addresses to customers. If those customers ever cancel or change providers,
there's often a clean-up process to recover those resources. Businesses going
through reorganizations or mergers and acquisitions may lose track (or may never
have had good records) of IP address ranges. Security policies and routing
policies may then become outdated, leaving an IP address hijacker a window
inside the perimeter security measures. Companies using Network Address
Translation (NAT) or Carrier-Grade NAT (CGNAT) to share one IP address among
many devices may find that those functions, which edit data packets in flight,
create unexpected failure modes. Sometimes, they hide problems, such as when
malware or address snooping is happening within the boundary of the
NAT.
Bank Four Zeros Crucial for Banking Resilience, says Huawei
“Banking Everywhere means that, from a technology point of view, we have to make
sure that any transactions should 100% not result in any problems or risks. It’s
not easy. For example, on the Tube in London, how do you deliver 5G to enable
transactions? Banking Everywhere is easy to say, but hard to do.” Cao highlights
the high availability and easy migration of GaussDB. He says after GaussDB was
deployed in one of the biggest banks in China, the recovery time objective (RTO)
was slashed to 120 seconds – a world-leading level. He says Huawei is working on
reducing this to just 30 seconds. ... “Some banks say we are in the AI era,
some say the intelligent era, some say the open banking era, but a lot of banks
still struggle working with a traditional model. So today it is like a
multi-generational industry,” he says. “On the one hand, exciting things are
coming, like Gen AI, and we have to be prepared. We have to be realistic to see
what challenges we face today. If a bank is not resilient enough, it’s very hard
to embrace Gen AI, or any intelligent opportunities.
The Three Pillars of HIPAA Compliance
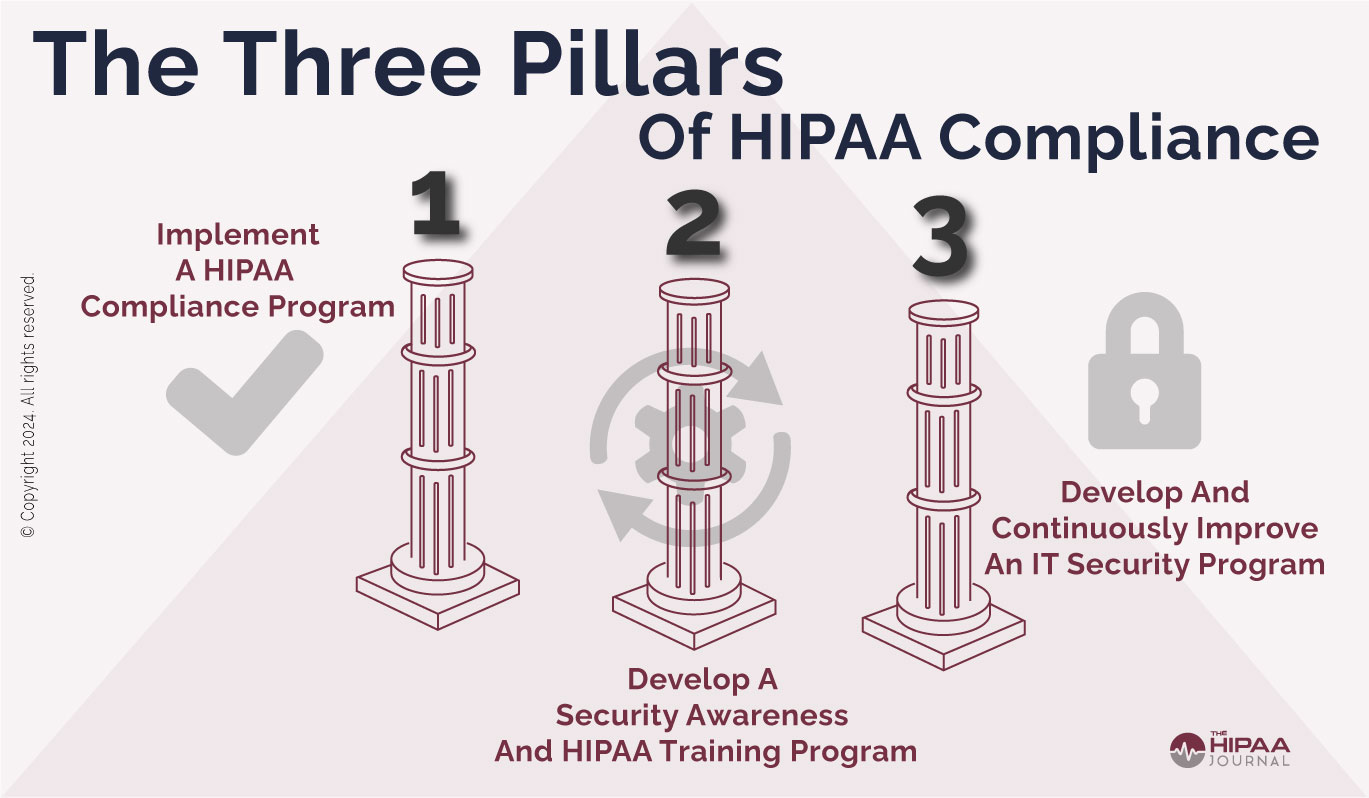
Policies and procedures must be developed on all aspects of HIPAA but not just
to allow boxes to be ticked in a HIPAA compliance checklist. That may be
sufficient to pass a very basic document review, but policies alone will not
make an organization HIPAA compliant. All members of the workforce must be
provided with the policies and must receive training relevant to their role.
Every individual in a healthcare organization has a role to play in making their
organization HIPAA compliant and must be trained to allow them to perform their
duties in a HIPAA-compliant way. Employees should not have to guess how HIPAA
applies. In addition to training, employees must be made aware of the sanctions
policy and the repercussions of HIPAA violations and the sanctions policy must
be enforced. HIPAA calls for training to be provided during the onboarding
process, regardless of whether a new hire is a seasoned healthcare professional
or is new to the industry. It is the responsibility of the compliance officer to
ensure that appropriate training programs are developed and that all members of
the workforce receive adequate training.
And herein lies the problem, says Ma: When business stakeholders seek to
understand EA’s value proposition, or even check the status of a project, they
may get different answers depending on whom they ask. It’s the
three-blind-men-describing-an-elephant problem: The man who feels the tail
describes an animal very different from the one described by the man feeling
the abdomen, or by the one feeling the ears and tusks. Though the variety in
their descriptions may reflect the function’s comprehensiveness, to the
uneducated executive, it sounds like misalignment. ... First, the full-stack
architect could ensure the function’s other architects are indeed aligned, not
only among themselves, but with stakeholders from both the business and
engineering. That last bit shouldn’t be overlooked, Ma says. While much
attention gets paid to the notion that architects should be able to work
fluently with the business, they should, in fact, work just as fluently with
Engineering, meaning that whoever steps into the role should wield deep
technical expertise, an attribute vital to earning the respect of engineers,
and one that more traditional enterprise architects lack.
What is cloud native and how can it generate business value?

Cloud-native workloads are conceived with the cloud in mind, focusing on
scalability, agility, and application independence. Building applications
directly in the cloud is a core component of agile development and DevOps
practices, allowing developers to quickly update their stack to meet business
needs. A definitive example of cloud-native workloads would be microservices,
in which different elements of an application run in parallel as independent
services, communicating via application programming interfaces (APIs). ...
“Companies who deliver cloud services have demonstrated that they can … free
us up from having to manage infrastructure hands-on,” Purcell tells ITPro. In
the “old days,” Purcell explains, a prospective provider of cloud-native
services would have had to rent property, procure hardware, and have a core IT
team capable of establishing a framework to deliver the application. “By
running it in the cloud … you just don't have to do any of that,” Purcell
says. Because the main public cloud providers continue “building for
builders,” as Purcell puts it, cloud native continues to be a dominant
concept. Of course, applications in the private cloud can be cloud native as
well.
Why It’s Time to Rethink Generative AI in the Enterprise
One of the biggest changes is the increasing availability of foundation models
beyond those supplied by companies that specialize in generative AI services.
In addition to open-source models that have been released by companies like
Meta and Google, we’re now seeing vendors like SAP developing their own
foundation models. Crucially, these models will provide greater opportunity
for enterprises to custom-model operations by injecting their own parameters
to control the context in which the model operates. In some cases, they can
also train or retrain models on custom data. ... Integrating AI models with
all the data that exists in a business is a complex task, not least because it
is often unclear which dataset is most relevant for a specific use case. For
instance, when querying sales data, should the model be prompted using data
from the ERP system, the CRM, a manually prepared spreadsheet, or something
else? To tackle this issue, businesses are likely to adopt what I refer to as
“data dispatchers.” A data dispatcher is an integration tool that efficiently
exposes data to GenAI services in an efficient way, making it easy for
enterprises to leverage their data for custom model training.
Quote for the day:
"Great achievement is usually born of
great sacrifice, and is never the result of selfishness." --
Napoleon Hill
No comments:
Post a Comment