Transforming CI/CD Pipelines for AI-Assisted Coding: Strategies and Best Practices

Most source code management tools, including Git, support tagging features that
let developers apply labels to specific snippets of code. Teams that adopt
AI-assisted coding should use these labels to identify code that was generated
wholly or partially by AI. This is an important part of a CI/CD strategy because
AI-generated code is, on the whole, less reliable than code written by a skilled
human developer. For that reason, it may sometimes be necessary to run extra
tests on AI-generated code — or even remove it from a codebase in the event that
it triggers unexpected bugs. ... Along similar lines, some teams may find it
valuable to deploy extra tests for AI-generated code during the testing phase of
their CI/CD pipelines, both to ensure software quality and to catch any
vulnerable code or dependencies that AI introduces into a codebase. Running
those tests is likely to result in a more complex testing process because there
will be two sets of tests to manage: those that apply only to AI-generated code,
and those that apply to all code. Thus, the testing stage of CI/CD is likely to
become more complicated for teams that use AI tools.
Revolutionising Regulatory Compliance: AI & ML Powering The Future Of Financial Governance

The use of technology is quickly transforming how businesses handle compliance
challenges. AI helps by automating tasks like monitoring and reporting. It
quickly finds new regulatory requirements in a sea of information and ensures
adherence by the organisation. Machine learning, a type of AI, is good at
spotting patterns and unusual things, which is important for following rules. By
looking at historical data, it can predict possible risks, so companies can deal
with them early. Compliance officers can use AI tools to do routine tasks,
handle hard problems, and be more open with regulators. AI’s smart systems make
compliance work smoother and more accurate. Looking forward, AI’s contribution
to compliance seems promising. Predictive compliance management, powered by AI,
will move from reacting to problems to spotting risks early, which could save
companies from legal trouble. Real-time monitoring and personalised solutions
for each company will become common, making compliance easier and better. Also,
AI will work with other new technologies like blockchain and IoT to improve
compliance.
Codium announces Codiumate, a new AI agent that seeks to be Devin for enterprise software development

Codium hopes that Codiumate will aid developers in their workflow, speeding up
all the manual typing they would otherwise have to do, doing the “heavy lifting”
and mechanical coding work, while enabling the developer to act more as a
hands-on product manager overseeing the process and course correcting it as
necessary, almost as though it is a junior developer or new hire to the team.
The technology powering the Codiumate agent on the backend is “best of breed”
OpenAI models, according to Friedman. The company is also experimenting with
Anthropic’s Claude and Google’s Gemini. It also offers its own large language
model (LLM) designed with its AlphaCodium process that increases the performance
of other LLMs in code completion tasks. While the former is available to all
users, the latter Codium LLM is only for paying enterprise users. Friedman said
it is superior to OpenAI’s models on coding and that a “Fortune 10” company that
could not be named due to confidentiality reasons was already using it in
production.
Healthcare’s cyber resilience under siege as attacks multiply
Every healthcare organization must ensure employees are well aware of and
trained about potential threats. It’s critical to ensure they understand how to
navigate and evaluate everything that comes in. One requirement could be to only
open emails from known senders or to only open attachments if they are secure.
Many organizations’ security teams will conduct resilience tests and distribute
suspicious-looking emails to see which employees will click it. Modern spam
filters are relatively adept at weeding out risky emails, but anyone with an
inbox knows that many get through to end users. Most employers issue computers
and devices, allowing for secured settings maintained by IT departments. It’s
important to keep access and logins only to those devices and not on any
personal devices, which are typically much easier attack points to enter a
system. Maintaining robust security settings on issued machines is especially
important if the employee will be working from remote locations, including at
home, where network security tends to not be as robust as within enterprises.
Instilling the Hacker Mindset Organizationwide

Visibility is a foundational principle that suggests you can't secure what you
don't know about. Lack of a security team's visibility is a gold rush for
hackers because they typically infiltrate an organization's network via hidden
or sneaky entry points. If you don't have visibility, there will undoubtedly be
a way in. Without visibility into all traffic within an organization's
infrastructure, threat actors can continue to lurk in the network and grant
themselves access to the organization's most sensitive data. With 93% of malware
hiding behind encrypted traffic but only 30% of security professionals claiming
to have visibility, it's no wonder that there were more ransomware attacks in
the first half of 2023 than in all of 2022. Once a cybercriminal has made their
way into the network, time is limited. Only with visibility can the
cybercriminal be stopped from wreaking havoc and gaining access to company data.
When cybersecurity professionals can better understand the mysterious nature of
hackers and how they work, they can better protect their own systems and
valuable customer data. It's critical to stay vigilant not only when it comes to
major security issues, but also with minor lags in security best practice.
Separating the signals from the noise in tech evolution
With technology trends extensively covered across all forms of media, IT leaders
often get questions or advice from well-meaning senior colleagues on what trends
to adopt. However, not every trend warrants immediate attention or even playing
catch-up if you’re late to the party. Wise leaders often opt to be “smart
laggards” who focus on adopting and scaling the trends that really matter to
their organizations. And they focus on demonstrating value quickly or stopping
pilots or initiatives that are not delivering. ... In the current environment of
uncertainty, marked by persistent macroeconomic challenges, global
fragmentation, and growing cybersecurity challenges, tech leaders shared their
perspectives on risks and resilience. More than one described reinventing the
technology function and its value proposition in times of crisis, taking a
“through-cycle mindset”: pushing forward in times of crisis rather than
retrenching, and focusing on long-term value creation to help the company emerge
stronger when conditions change. We also discussed how dashboards should balance
short- to mid-term KPIs with long-term value delivery.
Navigating risks in AI governance – what have we learned so far?
In the face of a regulatory void, several entities have taken it upon
themselves to establish their own standards aimed at tackling the core issues
of model transparency, explainability, and fairness. Despite these efforts,
the call for a more structured approach to govern AI development, mindful of
the burgeoning regulatory landscape, remains loud and clear. ... However, an
AI Risk and Security (AIRS) group survey reveals a notable gap between the
need for governance and its actual implementation. Only 30% of enterprises
have delineated roles or responsibilities for AI systems, and a scant 20%
boast a centrally managed department dedicated to AI governance. This
discrepancy underscores the burgeoning necessity for comprehensive governance
tools to assure a future of trustworthy AI. ... The patchwork of regulatory
approaches across the globe reflects the diverse challenges and opportunities
presented by AI-driven decisions. The United States, for example, saw a
significant development in July 2023 when the Biden administration announced
that major tech firms would self-regulate their AI development, underscoring a
collaborative approach to governance.
Unlocking Personal and Professional Growth: Insights From Incident Management
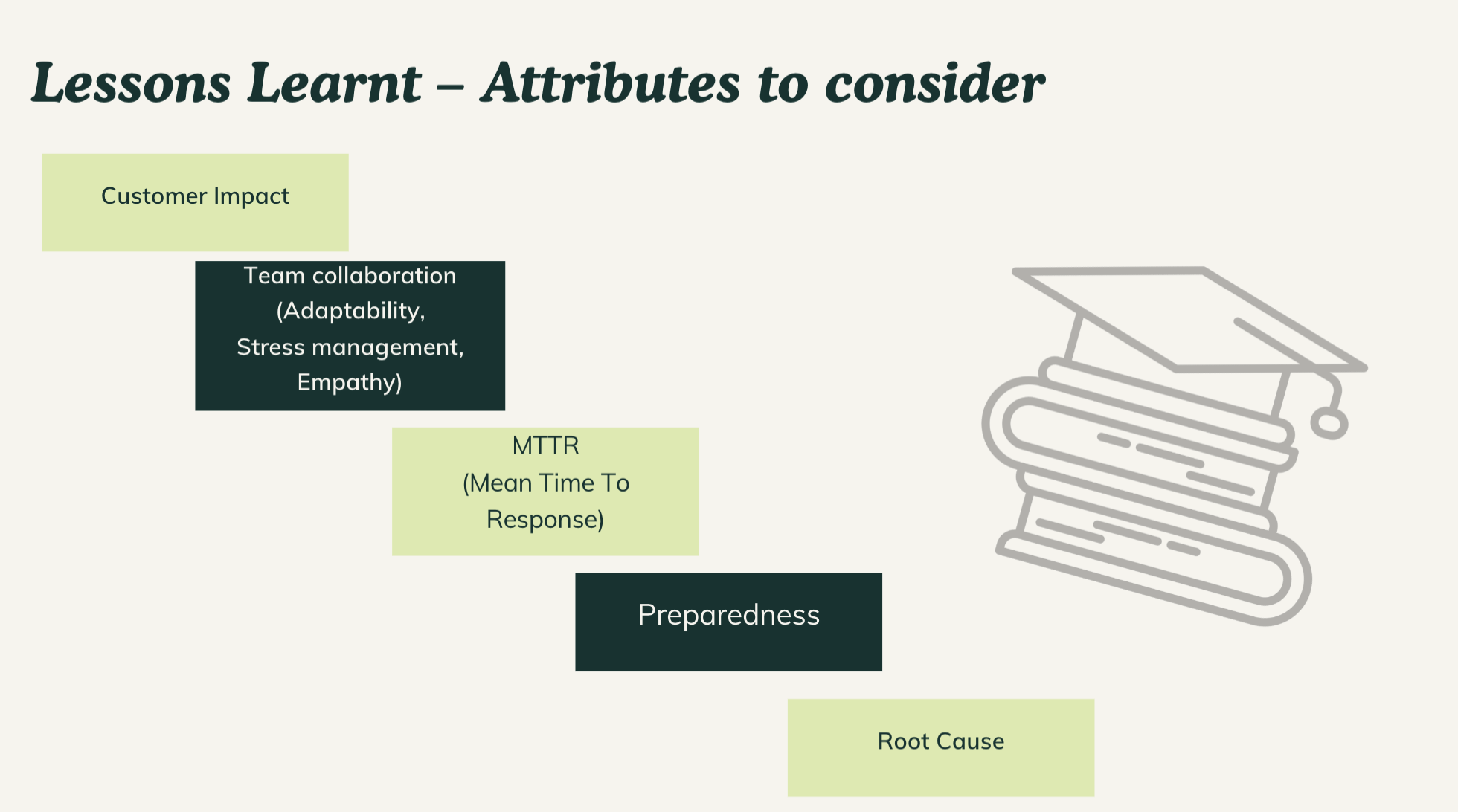
The skills and lessons gained from Incident Management are highly transferable
to various aspects of life. For instance, adaptability is crucial not only in
responding to technical issues but also in adapting to changes in personal
circumstances or professional environments. Teamwork teaches collaboration,
conflict resolution, and empathy, which are essential in building strong
relationships both at work and in personal life. Problem-solving skills honed
during incident response can be applied to tackle challenges in any domain,
from planning a project to resolving conflicts. Resilience, the ability to
bounce back from setbacks, is a valuable trait that helps individuals navigate
through adversity with determination and a positive mindset. Continuous
improvement is a mindset that encourages individuals to seek feedback, reflect
on experiences, identify areas for growth, and strive for excellence. This
attitude of continuous learning and development not only benefits individuals
in their careers but also contributes to personal fulfillment and
satisfaction.
How to build a developer-first company

Providing a great developer experience—by enabling our customers to easily add
auth flows and user management to their apps—leads to a great end-user
experience as the customer’s customers seamlessly and securely log in.This
kind of virtuous cycle exists at many developer-focused companies. When
building a successful developer-first business, it’s critical to tie together
the similarities between the customer experience and the developer experience
while clearly delineating the differences. ... When helping developers build
their customer experience, we emphasize building onboarding and authentication
flows with the best user experience in mind. That includes reducing friction,
like the use of passwordless methods and progressive profiling, and creating
an embedded in-app native experience to avoid needless redirections or
pop-ups. Our developer experience includes an onboarding wizard that sets up
their project and login flows in a few clicks. We offer a drag-and-drop visual
workflow editor to easily create and customize their customer journey. We also
provide robust documentation, code snippets, SDKs, tutorials, and a Slack
community for troubleshooting.
How to fix the growing cybersecurity skills gap

Organizations looking to upskill their cybersecurity professionals should
consider adjusting and reorganizing key workflows to give the entire security
team — aside from just the CISO — ample time to research emerging threats and
remain up to date on what the ramifications of these threats may be. By
automating repetitive tasks for these team members or restructuring key
processes and timelines, the entire team, from CISO to analyst, can have more
time to dedicate towards staying ahead of industry trends and cyber-attacks,
ultimately strengthening the organization’s ability to detect and respond to
threats in the long run. Giving employees time and space to be curious and
explore the latest threat intelligence, commentary and insight — including
topic-based tabletop exercises or red teaming — will yield significant
dividends in understanding the organization's true security posture and
preparedness. In today’s cybersecurity landscape, companies must strive to be
a learning-forward organization. Tangible adoption of this principle must go
beyond formal skills and training — every encounter your teams have with a
threat or an attack is a learning opportunity.
Quote for the day:
"Though no one can go back and make a
brand new start, anyone can start from now and make a brand new ending." --
Carl Band
No comments:
Post a Comment