Quishing is the new phishing: What you need to know
Consider the QR code aired during the Super Bowl. Now, imagine the company
behind that commercial had malicious intent (just to be clear, the company
behind that commercial did not have malicious intent). Say, for example, the
QR code displayed during the ad opened your phone's browser and automatically
downloaded and installed a piece of ransomware. Given the number of people who
watch the Super Bowl, the outcome of that attack could have been disastrous.
That's quishing. ... We've all just accepted the QR code. And, to that end, we
trust them. After all, how harmful can a simple QR code be? The answer to that
question is…very. And cybercriminals are counting on the idea that most
consumers always assume QR codes are harmless. Those same criminals also
understand that their easiest targets are those on mobile phones. Why? Because
most desktop operating systems include phishing protection. Phones, on the
other hand, are far more vulnerable to those attacks. At the moment, most
quishing attacks involve criminals sending a QR code via email.
Boardrooms losing control in generative AI takeover

The theme of people adopting GenAI within their workplaces without oversight
from IT and security teams or leadership, a trend we might reasonably term
shadow AI, is not a new one as such. Earlier this year, an Imperva report drew
similar concerns, stating that an insider breach at a large organisation
arising from someone using generative AI in an off-the-books capacity was only
a matter of time. However, given the steadily widening scope and ever-growing
capability of generative AI tools, organisations can no longer afford not to
exert, at the very least, minimal oversight. “Much like bring-your-own-device
[BYOD], gen AI offers massive productivity benefits to businesses, but while
our findings reveal that boardroom executives are clearly acknowledging its
presence in their organisations, the extent of its use and purpose are
shrouded in mystery,” said Kaspersky principal security researcher, David Emm.
“Given that GenAI’s rapid evolution is currently showing no signs of abating,
the longer these applications operate unchecked, the harder they will become
to control and secure across major business functions such as HR, finance,
marketing or even IT,” said Emm.
Privacy vs convenience – which comes out ahead?

There is a mutual responsibility between employees and employers, so trust and
openness are essential. On the one hand, employees must be discerning about
the digital tools they employ, understanding the permissions they grant and
the third parties that might gain access to their data. They also need to
accept that their personal choices can impact the security of the organization
too. This requires awareness and a commitment to regular audits of personal
digital spaces, ensuring that no unwanted entities are lurking in the shadows.
Conversely, organizations bear the responsibility of being forthright about
their data practices. Companies that are transparent about the data they
access - and, more importantly, why they access it—stand out as beacons of
integrity. This transparency extends beyond mere access; it encompasses the
entire data lifecycle, from collection to storage, usage, and eventual
disposal. By openly communicating these practices, enterprises can foster a
culture of trust with their employees – and comply with regulatory standards
too.
How to Speed Cyberattack Discovery
A fast and reliable way to identify cyber threats is with proactive threat
hunting, which utilizes human defenders armed with advanced detection and
proactive response technologies and approaches, says Mike Morris, a Deloitte
risk and financial advisory managing director via an email interview. “In
particular, threat hunting, during which human defenders actively maneuver
through their networks and systems to identify indicators of a network attack
and preemptively counter these threats, can speed the discovery of
cyberattacks.” Yet he warns that for threat hunting to function optimally,
it’s necessary that specific, relevant, and accurate intelligence is coupled
with automation to identify and mitigate the adversary’s activities. When
deploying human-based threat-hunting capabilities, it’s helpful to think about
the parallels to physical security leading practices, Morris says. “For
example, human security guards, tasked with protecting critical assets,
constantly inspect physical infrastructures and maintain the integrity of
their responsible spaces by actively patrolling and investigating,” he
explains.
The Financial Consequences of Inadequate Data Governance

Low-quality data can severely impact decision-making and operational
efficiency. Inaccurate or incomplete data can lead to flawed strategies,
missed opportunities, and ultimately, financial losses. A sales team relying
on outdated customer information could waste time on leads that have already
been converted or are no longer relevant, leading to lost sales opportunities
and financial losses. Similarly, a marketing team using incorrect customer
segmentation data could end up targeting the wrong audience, wasting
advertising budget, and missing revenue targets. These real-world scenarios
further illustrate the cost of poor data quality. The examples highlight the
tangible impact of data quality issues on an organization's bottom line. ...
Data breaches can have devastating financial consequences for organizations.
The direct costs include legal fees, fines, and customer compensation, which
can run into millions of dollars. Indirect costs, such as reputational damage
and loss of business, can be even more damaging in the long run.
Change Management for Zero Trust
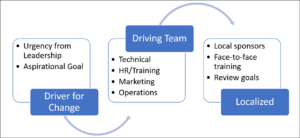
Change management isn’t any different for Zero Trust than it is for any other
big initiative. But most of us aren’t very good at change management. And
security and cybersecurity are not sexy. And most people want their security
to be minimally invasive and as unnoticeable as possible. And most leaders get
no top-line/bottom-line joy from spending money on Zero Trust initiatives. And
Zero Trust doesn’t drop new features and functionality for a product at the
end of a sprint. ... Three key areas you can focus on as you get started:Get
leadership engaged – If the culture of your organization is driven by urgency,
craft a message and plan that leverages urgency. If the culture is driven
through aspiration, use aspirational vision and goals. Either way, get
leadership on board to deliver the message. Create a communications strategy –
The strategy must include the rhythm and mode of communications, as well as
the context and content of the communications for leadership and sponsors,
leads and key centralized players, local mavens, and users. Persuasive
communication is what the marketing team does well. Get them involved.
UK Prime Minister announces world’s first AI Safety Institute

"The British people should have peace of mind that we're developing the most
advanced protections for AI of any country in the world," Sunak said. "I will
always be honest with you about the risks, and you can trust me to make the
right long-term decisions." The AI Safety Institute will assess and study
these risks — from social harms like bias and misinformation, through to the
most extreme risks of all - so that the UK understands what each new AI model
is capable of, Sunak added. "Right now, we don't have a shared understanding
of the risks that we face. Without that, we cannot hope to work together to
address them." The UK will therefore push hard to agree to the first ever
international statement about the nature of AI risks to ensure that, as they
evolve, so does shared understanding about them, Sunak said. "I will propose
that we establish a truly global expert panel to publish a State of AI Science
report. Of course, our efforts also depend on collaboration with the AI
companies themselves. Uniquely in the world, those companies have already
trusted the UK with privileged access to their models. That's why the UK is so
well-placed to create the world's first Safety Institute."
DNS Under Siege: Real-World DNS Flood Attacks

During H1 2023 there was a surge in DNS flood attacks affecting multiple
organizations around the world. Looking at the DNS attacks and their
characteristics we suspect that they belong to one or more global DNS attack
campaigns. We were able to identify significant DNS attack activity world-wide
and were able to identify correlations between attack events to different DNS
servers. ... The organizations that were targeted by these DNS flood attacks
all belong to the financial and commercial segment. We detected and mitigated
DNS flood attacks targeting banks, retailers, insurance etc. This can hint on
the DNS campaign’s agenda, and help similar organizations protect their DNS
services. ... There was a single attack vector repeating in all DNS attacks
and that is the random subdomain, also known as DNS water torture.
Interestingly, we identified different types of invalid subdomains used in the
attacks. In some cases, it was purely random with high entropy1 including case
randomization and in other cases the attack subdomains were human-readable,
but non-existent.
FTC eyes competitive practices for genAI

Generative AI is set to become one of the world’s most dominant industries.
One projection puts the market at $76.8 billion by 2030, up from a current
valuation at $11.3 billion. Goldman Sachs, for its part, boldly says the
technology could drive a 7% (or nearly $7 trillion) increase in global GDP.
Amidst all this, the FTC says issues could arise around control over one or
more of the “key building blocks” of generative AI: data, talent and
computational resources. If a single company or handful of firms controlled
one of these essential inputs, “they may be able to leverage their control to
dampen or distort competition,” the agency asserts. “And if generative AI
itself becomes an increasingly critical tool, then those who control its
essential inputs could wield outsized influence over a significant swath of
economic activity.” In particular, the agency said firms could bundle and tie
products — offering multiple products in a single package or conditioning the
sale of one product on the purchase of another, respectively.
Keys to effective cybersecurity threat monitoring

Over the past few years, attackers have adjusted their tactics, finding
success in targeting employees with the intent of stealing their credentials.
Social engineering tactics such as phishing often catch individual users out,
leading to passwords, financial information and other sensitive data being
breached. “In the past, they might have relied on attacking infrastructure
directly through vulnerabilities or brute force attacks. While they can still
happen, these attacks run a high risk of discovery before the bad actor can
get in,” explained Hank Schless, director of global security campaigns at
Lookout and host of the Security Soapbox Podcast. “Now, attackers are
targeting individuals who likely have access to large sets of valuable cloud
data. They do this with the intention of stealing those individuals’
credentials via mobile phishing attacks in order to be able to enter the
organisation’s infrastructure discreetly under the guise of being a legitimate
user. “This creates massive issues with monitoring for threats, because the
threat looks like it’s coming from the inside if an attacker is using stolen
credentials.”
Quote for the day:
"It is the capacity to develop and
improve their skills that distinguishes leaders from followers." --
Warren G. Bennis
No comments:
Post a Comment