Top 8 cybersecurity predictions for 2022

As organizations face new regulations, there will be a demand for resident
compliance officers to help navigate through the complex and evolving dictates.
“Compliance officers will certainly rise on the recruiters' agenda as regulatory
bodies mandate there be a 'single throat to choke,'" says Liz Miller, an analyst
from Constellation Research. “Although, that’s exactly the opposite of what we
need. What we do need are skilled tacticians and strategies, which can be
trusted voices and leaders within (and across) an organization, capable of
translating the complexity of new (and constantly shifting) global regulations
into real business value for everyone from the CEO to the mailroom.” ... With a
major chunk of the global workforce forced to work from home by the pandemic,
there is an upsurge in the usage of software that allows supervisors to monitor
employees at all times. This has upset the remote working ecosystem to some
extent, escalating employee distress. “Tattleware (also bossware) will degrade
employee experience by 5% and increase insider threats in 2022,” according to a
security prediction report by Forrester.
Attackers Exploit Flaw in Google Docs’ Comments Feature

The campaign appears to signify a ramp up in attacks to exploit the Comments
feature of Google’s collaboration apps for malicious intent – attacks that
likely will continue if left unchecked, researchers said. June was the first
time Avanan researchers identified threat actors hosting phishing attacks from
within Google Docs, delivering malicious links aimed at stealing victims’
credentials. At the time, they identified it as a novel exploit of the app.
Then, in October, as previously mentioned, researchers identified threat actors
exploiting the Comments feature for the first time, followed by December’s
flurry of attacks, which were reported to Google on Jan. 3 “using the resulting
phishing via email through Google’s built-in tools,” Fuchs wrote. Avanan
recommends that users cross-reference the email address in the comment to ensure
it’s legitimate before clicking on a Google Docs comment. They also recommend
standard “cyber hygiene” when reviewing comments, including scrutinizing links
and inspecting grammar, according to the report.
Cybersecurity training isn't working. And hacking attacks are only getting worse

Part of the problem is that, for many businesses, cybersecurity isn't ingrained
into everyday operations and employees are only asked to think about it when
doing annual cybersecurity training -- leaving companies at risk from
cyberattacks the rest of the year. "I think one of the most important things to
realise is most of the education and training done, it's not very effective,"
Stuart E. Madnick, professor of information technology and engineering systems
at MIT Sloan Executive Education told ZDNet Security Update. "The 30-minute
video you're obligated to watch once a year doesn't do the job". According to
Madnick -- who has been at M.I.T. since 1972 and has served as the head of MIT's
Information Technologies Group for more than 20 years -- organisations need to
build a culture of cybersecurity that actively involves everyone. If people have
a greater understanding of how their organisation falling victim to a
cyberattack could affect them, it could lead to everyone being more careful when
it comes to cybersecurity.
How to Build Scalable Data and AI Industrial IoT Solutions in Manufacturing
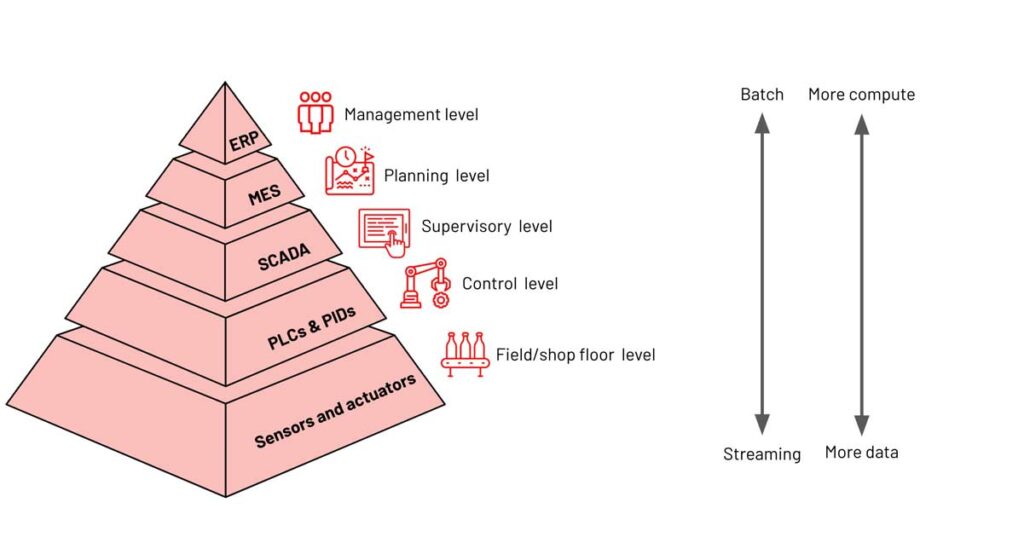
The importance and growth of the IIoT technology stack can’t be underestimated.
Validated by several leading research firms, IIoT is expected to grow at a CAGR
of greater than 16% annually through 2027 to reach $263 billion globally.
Numerous industry processes are driving this growth, such as automation, process
optimization and networking with a strong focus on machine-to-machine
communication, big data analytics and machine learning (ML) delivering quality,
throughput and uptime benefits to aerospace, automotive, energy, healthcare,
manufacturing and retail markets. Real-time data from sensors helps industrial
edge devices and enterprise infrastructure make real-time decisions, resulting
in better products, more agile production infrastructure, reduced supply chain
risk and quicker time to market IIoT applications, as part of the broader
industry X.0 paradigm, enables ‘’connected’’ industrial assets to enterprise
information systems, business processes and the people at the heart of running
the business.
FinTech in 2022: the Big Regression?
The next few years will see a Big Regression. It started in China when the $300
billion IPO of Ant Group was dismantled. Now it is clearly happening in Europe
and America. What is the Big Regression? It is the reversal of technology
progress. It’s not that people will reject technology. It’s governments and
regulations. In fact, it is likely that FinTech will be affected by the Big Tech
fall-out. As governments crack down on the FATBAGs, they will also have a
magnifying glass on the FinTech unicorns and their brethren. They may like some
of it but, specifically in FinTech, the Big Regression will be a thing as
regulators dismantle some of the unregulated markets that they now want to
regulate. We’ve seen it already with P2P lending stalling and, in some markets,
failing. By way of example, Zopa has just given up P2P lending. Then we see it
in crowdfunding, when Kickstarter is finding it hard to kick or start. And we
can see the governments getting more and more of a squeeze on everything from
BNPL to cryptocurrency exchanges and bitcoin mining.
Steering innovation toward the public good
Innovation should be shaped in ways that help America win the 21st century, with
transportation systems and infrastructure that make communities more
competitive, adaptable, and resilient. Our innovation strategy must support
workers, knowing that our choices will help to define whether any given
technological development meets its potential to create economic benefits for
all. A good innovation strategy allows for experimentation and learns from
setbacks, because these are indispensable parts of the scientific method that
underpin all invention and discovery. Our approach to innovation should center
on opportunities to collaborate, recognizing the distinct but related roles of
the public, private, and academic sectors. And finally, our policies should be
flexible and adapt as technology changes, because we can’t prepare for an
evolving future with policy that only makes sense under present or past
conditions. These principles will help us to ensure that the enormous potential
of U.S. transportation innovation benefits our nation and its people.
How is the role of the CTO evolving?

The modern CTO must instead be bold enough to become an early adopter — at least
much of the time. Goldman Sachs and Bank of America are two brands that took the
early adoption route with blockchain technology. Those brands and others have
plenty of valid reasons for doing so. For example, according to one study,
blockchain could reduce operational costs at banks by more than a
quarter. Tristan Jervis, co-leader of the global technology team at Russell
Reynolds Associates, also notes that bringing new technologies into the picture
means taking a customer-centric view. He explains: “Business models are shifting
to adapt to the needs of a more tech-centric, collaborative and agile
organisation — and the role of technology leadership is evolving in tandem. “To
make this happen, technology officer roles are moving from a supportive function
to becoming key enablers of a company’s transformation agenda and strategy. In
[business to consumer] and [business to business] companies alike, this means
bringing the customer into the centre of everything they do, and understanding
the entire customer lifecycle from front-end to back-end, rather than sitting in
technology or digital silos.”
What Is NEAR Protocol? The Sharded Layer 1 Blockchain Explained
NEAR Protocol’s approach to solving the Blockchain Trilemma is by implementing
a horizontal scaling feature called sharding. It works by splitting a
blockchain node network into smaller partitions known as “shards.” Each shard
consists of its own data and can be used to process transactions in unison
with other shards, increasing the overall throughput of the network. Thanks to
its shard technology, it claims it can process up to 100,000 transactions per
second, outpacing other rival smart contract platforms by some distance. While
sharding is not unique to NEAR Protocol (Ethereum also plans to implement
sharding on the completion of Ethereum 2.0), it has built on the concept by
developing dynamic re-sharding. On NEAR, instead of the number of shards being
static, the network will regularly adjust the number supported based on user
demand. By dynamically adjusting the number of shards used, NEAR can reduce
the average cost of using the network while maintaining the potential for high
transaction throughput.
4 Robotic Process Automation (RPA) trends to watch in 2022

“Intelligent automation” has been an on-again, off-again buzz phrase in the
RPA world. It’s on again, perhaps permanently. The term usually refers to a
mix of technologies, including RPA, low-code and no-code development tools,
and AI/ML. It also implicitly refers to the reality that RPA on its own is not
“smart” – it can’t learn on its own (as with some ML models, for example) or
adjust to things like UI changes without human intervention. Intelligent
automation is often an aspirational vision of how more basic forms of process
automation can complement more advanced cognitive technologies, and the other
way around. To this point, the potential has outpaced the reality. The RPA
market has been quite competitive rather than community-oriented, as has the
broader automation and AI industry. But true intelligent automation will by
definition require a collaborative approach, according to Jon Knisley,
principal consultant for process and automation excellence at Fortress IQ.
Knisley sees an increased focus on the need for a cooperative intelligent
ecosystem in 2022.
Getting Rid of Wastes and Impediments in Software Development Using Data Science
Impediments and wastes have the following relationship: a waste could be an
impediment, or could result in an impediment. An outdated manual, for
instance, is not an impediment per se, but it could lead to a rework caused by
some misdirection. On the other hand, waiting for some management approval is
an impediment and waste at the same time. ... The result was a waste model
that contained 22 wastes grouped into six categories and a map that
demonstrated the relationship among wastes. The categories were: product,
process, information and communication, product, process, and organization.
The subsequent deliverables were a method and software that helped with the
detection of wastes. Based on the information provided by the software, it is
possible to understand what is going on, which wastes were found, and
investigate the root cause of wastes. The next phase was the creation of a
method that included an algorithm and software that implemented the
algorithm.
Quote for the day:
"A leader does not deserve the name
unless he is willing occasionally to stand alone." --
Henry A. Kissinger
No comments:
Post a Comment