Complexity is killing software developers

“There is more to this profession than writing code; that is the means to an
end,” Hightower said. “Maybe we are saying we have built enough and can pause on
building new things, to mature what we have and go back to our respective roles
of consuming technology. Maybe this is the happy ending of the devops and
collaboration movement we have seen over the past decade.” The market is
responding to this complexity with an ever-growing list of opinionated services,
managed options, frameworks, libraries, and platforms to help developers contend
with the complexity of their environment. “No vendor is or will be in a position
to provide every necessary piece, of course. Even AWS, with the most diverse
application portfolio and historically unprecedented release cadence, can’t meet
every developer need and can’t own every relevant developer community,” O’Grady
wrote in a 2020 blog post. That being said, “there is ample evidence to
suggest that we’re drifting away from sending buyers and developers alike out
into a maze of aisles, burdening them with the task of picking primitives and
assembling from scratch.
Securing SaaS Apps — CASB vs. SSPM
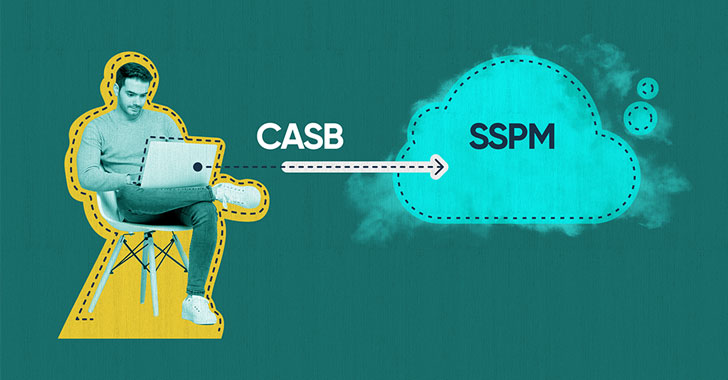
There is often confusion between Cloud Access Security Brokers (CASB) and SaaS
Security Posture Management (SSPM) solutions, as both are designed to address
security issues within SaaS applications. CASBs protect sensitive data by
implementing multiple security policy enforcements to safeguard critical data.
For identifying and classifying sensitive information, like Personally
Identifiable Information (PII), Intellectual Property (IP), and business
records, CASBs definitely help. However, as the number of SaaS apps increase,
the amount of misconfigurations and possible exposure widens and cannot be
mitigated by CASBs. These solutions act as a link between users and cloud
service providers and can identify issues across various cloud environments.
Where CASBs fall short is that they identify breaches after they happen. When it
comes to getting full visibility and control over the organization's SaaS apps,
an SSPM solution would be the better choice, as the security team can easily
onboard apps and get value in minutes — from the immediate configuration
assessment to its ongoing and continuous monitoring.
11 cybersecurity buzzwords you should stop using right now

The terms whitelist and blacklist date back to the some of the earliest days of
cybersecurity. Associating “white” with good, safe, or permitted, and “black”
with bad, dangerous, or forbidden, the phrases are still commonly applied to
allow or deny use or access relating to various elements including passwords,
applications, and controls. Cybersecurity consultant Harman Singh thinks the
terms need urgently replacing because of harmful racial overtones associated
with them, suggesting allow lists and deny lists serve the same purpose without
potentially damaging connotations linked to ethnicity and race. “This is such a
small yet significant, change” he tells CSO. “The NCSC made this conscious
change last year to avoid racial tone. Still only a handful of companies in the
industry have thought about doing this. Why don’t we all follow this example to
stamp out such terms?” In a blog post, Emma W, head of advice and guidance at
the NCSC, wrote: “You may not see why this matters. If you’re not adversely
affected by racial stereotyping yourself, then please count yourself lucky. For
some of your colleagues, this really is a change worth making.”
How to Get Started with Competitive Programming?

First and foremost what you need to do is pick out your preferred programming
language and become proficient with its syntax, fundamentals, and
implementation. You need to make yourself familiar with built-in functions,
conditional statements, loops, etc. along with the required advanced concepts
such as STL library in C++ or Big Integers in Java. There are various languages
out there that are suitable for Competitive Programming such as C, C++, Java,
Python, and many more ... What you need to know – you’ll be suggested by
some individuals that it is not necessary to learn DSA priorly for getting
started with CP and it can be done along the way however, we recommended you to
at least cover the DSA fundamentals like Array, Linked List, Stack, Queue, Tree,
Searching, Sorting, Time and Space Complexity, etc. before starting to solve
problems and doing competitive problems as it’ll help you to feel confident and
solve a majority of the problems. Without knowing Data Structures &
Algorithms well, you won’t be able to come up with an optimized, efficient, and
ideal solution for the given programming problem.
‘Trojan Source’ Bug Threatens the Security of All Code

“It is already hard for humans to tell ‘this is OK’ from ‘this is evil’ in
source code,” Weaver said. “With this attack, you can use the shift in
directionality to change how things render with comments and strings so that,
for example ‘This is okay” is how it renders, but ‘This is’ okay is how it
exists in the code. This fortunately has a very easy signature to scan for, so
compilers can [detect] it if they encounter it in the future.” The latter half
of the Cambridge paper is a fascinating case study on the complexities of
orchestrating vulnerability disclosure with so many affected programming
languages and software firms. ... “We met a variety of responses ranging from
patching commitments and bug bounties to quick dismissal and references to legal
policies,” the researchers wrote. “Of the nineteen software suppliers with whom
we engaged, seven used an outsourced platform for receiving vulnerability
disclosures, six had dedicated web portals for vulnerability disclosures, four
accepted disclosures via PGP-encrypted email, and two accepted disclosures only
via non-PGP email. They all confirmed receipt of our disclosure, and ultimately
nine of them committed to releasing a patch.”
Cloud, microservices, and data mess? Graph, ontology, and application fabric to the rescue.

Data integration may not sound as deliciously intriguing as AI or machine
learning tidbits sprinkled on vanilla apps. Still, it is the bread and butter of
many, the enabler of all cool things using data, and a premium use case for
concepts underpinning AI, we argued back then. The key concepts we advocated for
then have been widely recognized and adopted today in their knowledge graph and
data fabric guise: federation and semantics. Back then, the concepts were not as
widely adopted, and parts of the technology were less mature and recognized.
Today, knowledge graphs and data fabrics are top of mind; just check the latest
Gartner reports. The reason we're revisiting that old story is not to bask in
some "told you so" self-righteousness, but to add to it. Knowledge graphs and
data fabrics can, and hopefully will, eventually, address data integration
issues. ... The final part of the process is orchestrating services, i.e.
executing, coordinating, and deploying them, in the right order and with the
right parameters, wherever they may be - on-premises, in the cloud, or in
containers. That creates what Duggal called an "application fabric", as an
extension of the notion of a data fabric.
Chaos Engineering Made Simple
The shift toward cloud native technologies has enabled the development of more
manageable, scalable and dependable applications, but at the same time it has
brought about unprecedented dynamism to critical services. This is due to the
multitude of coexisting cloud native components that have to be managed
individually. Failure of even a single microservice can lead to a cascading
failure of other services, which can cause the entire application deployment to
collapse. ... LitmusChaos was created with the primary goal of performing chaos
engineering in a cloud native manner, scaling it as per the cloud native norms,
managing the life cycle of chaos workflows and defining observability from a
cloud native perspective. Chaos experiments help achieve this goal by
injecting chaos into the target resources, using simple, declarative manifests.
These Kubernetes custom resource (CR) manifests allow for an experiment to be
flexibly fine-tuned to produce the desired chaos effect, as well as contain the
experiment blast radius so as to not harm other resources in the
environment.
Future of Blockchain: How Will It Revolutionize The World In 2022 & Beyond!
In an ever-evolving world, one of the most relevant use cases for blockchain
right now is cryptocurrencies, and it is here to remain that way for some
time. However, an even more exciting future is emerging in blockchain
technology: non-fungible tokens (NFTs). NFTs are a revolutionary new way of
buying and selling digital assets that represent real-world items. All NFTs
are unique and can’t be replaced or swapped — they can only be purchased,
sold, traded, or given away by the original owner/creator of that asset. NFTs
could power a whole new wave of digital collectibles, from rare artwork to
one-of-a-kind sneakers and accessories. They could also be used in place of
items in video games or other virtual worlds. ... Blockchain could replace
this system with a digital identity that is safe, secure, and easy to manage.
Instead of proving who you are by recalling some personal, arbitrary piece of
information that could potentially be guessed or stolen, your digital identity
is based on the uniquely random set of numbers assigned to each user on a
blockchain network.
Quantum computers: Eight ways quantum computing is going to change the world
For decades, researchers have tried to teach classical computers how to
associate meaning with words to try and make sense of entire sentences. This
is a huge challenge given the nature of language, which functions as an
interactive network: rather than being the 'sum' of the meaning of each
individual word, a sentence often has to be interpreted as a whole. And that's
before even trying to account for sarcasm, humour or connotation. As a result,
even state-of-the-art natural language processing (NLP) classical algorithms
can still struggle to understand the meaning of basic sentences. But
researchers are investigating whether quantum computers might be better suited
to representing language as a network -- and, therefore, to processing it in a
more intuitive way. The field is known as quantum natural language processing
(QNLP), and is a key focus of Cambridge Quantum Computing (CQC). The company
has already experimentally shown that sentences can be parameterised on
quantum circuits, where word meanings can be embedded according to the
grammatical structure of the sentence.
Anomaly Detection Using ML.NET
As the name suggests, it is about finding what is abnormal from what you
expect in your day-to-day life. It helps identify data points, observations,
or events that deviate from the normal behavior of the dataset. There are now
many distributed systems where monitoring their performance is required. A
considerable amount of data and events pass through such systems. Anomaly
detection gives possibilities to determine where the source of the problem is,
which significantly reduces the time to rectify the fault. It also allows us
to detect outliers and report them accordingly. These all applications have
one common focus that I have mentioned earlier - outliers. These are cases
where the data points are distant from the others, do not follow a particular
pattern, or match known anomalies. Each of these data points can be useful for
identifying these anomalies and responding correctly to them.
Quote for the day:
"Different times need different types
of leadership." -- Park Geun-hye
No comments:
Post a Comment