How next-gen cloud SIEM tools can offer critical visibility for effective threat hunting

Organizations must adopt a new cloud-centric mentality, supported by a
combination of new security solutions ready to handle the high volume and
velocity of data flowing across cloud environments. Organizations must focus
on tools such as Next-Gen SIEM, cloud-focused tools such as cloud access
security broker (CASB) and cloud security posture management (CSPM), and
modern consolidated network and security services such as secure access
service edge (SASE), which all enable modern security architecture approaches.
These scalable tools include license models not based on the volume of data
ingested but other variables, such as number of users monitored. CSPM and CASB
can help users adopt new policy enforcement practices, helping organizations
to navigate complex security settings and services from public cloud providers
and cover any gaps in visibility from the multiple IaaS, PaaS and SaaS
services adopted. Additionally, where users are operating off of personal
devices and accessing cooperate resources, SASE offerings help transition
controls such as secure web gateways to a cloud-based model from anywhere in
the world. Companies no longer need to debate losing visibility for a better
price or improved network resiliency.
Five emerging fraud threats facing businesses in 2021
Synthetic identity fraud – when a fraudster uses a combination of real and fake information to create an entirely new identity – is currently the fastest growing type of financial crime. The progressive uptick in synthetic identity fraud is likely due to multiple factors, including data breaches, dark web data access and the competitive lending landscape. As methods for fraud detection continue to mature, fraudsters are expected to use fake faces for biometric verification. These “Frankenstein faces” will use AI to combine facial characteristics from different people to form a new identity, creating a challenge for businesses relying on facial recognition technology as a significant part of their fraud prevention strategy. ... Once the stimulus fraud attacks run their course, it is predicted that hackers will increasingly turn to automated methods, including script creation (using fraudulent information to automate account creation) and credential stuffing (using stolen data from a breach to take over a user’s other accounts) to make cyberattacks and account takeovers easier and more scalable than ever before.A guide to being an ethical online investigator

It’s not just legal issues that would-be amateur online investigators need to
be aware of. Much of the online activity carried out in the wake of the
Capitol riots raises ethical questions, too. Should a person who didn’t storm
the Capitol but attended the rallies leading up to the riots be identified and
risk punishment at work? Do those who were in and around the Capitol on
January 6 automatically lose the right to privacy even if they weren’t
involved in riots? It’s worth thinking through how you feel about some of
these questions before you continue. Few are clear cut. So, where does the
information come from? “Our bread and butter is open source,” Fiorella says.
“Open-source media” refers to information that is publicly available for use.
Data archivists, or those who collect and preserve information online for
historical purposes, accessed such open-source data to save posts before they
disappeared as social media companies pushed President Donald Trump and many
of his supporters off their platforms. “If you were at the Capitol storming
and recorded video and took selfies that anyone can access, and it’s openly
available on the internet, it’s fair game,” says Fiorella.
Top Five Artificial Intelligence Predictions For 2021

Though regulation hasn’t reached a boiling point yet, AI governance will
continue to be a hot topic in 2021. As AI becomes more pervasive, more and
more stakeholders are waking up to the potential problems it introduces to the
public. In response, organizations everywhere — from the most cutting-edge to
the laggards — will be expected to deliver AI systems that are responsible,
transparent, and unbiased. But whose responsibility is it to make sure this
happens and regulates AI – the government, businesses, industry groups, or
some combination? If businesses want to regulate themselves before the
government does, they will have to take steps to ensure the data that feeds
their AI is fair and unbiased, and that their models are empathetic,
transparent, and robust. ... With several big consumer brands in the hot seat
around questionable AI ethics, most people still don’t trust AI. For many,
it’s because they don’t understand it or even realize they’re using it daily.
Consumers are getting so many AI-powered services for free — Facebook, Google,
TikTok, etc. — that they don’t understand what they’re personally giving up in
return — namely their personal data. As long as the general public continues
to be naïve, they won’t be able to anticipate the dangers AI can introduce or
how to protect themselves — unless the market better educates customers or
implements regulations to protect them.
Amid WhatsApp privacy concerns, the draft Data Protection Bill comes to mind

Is data property? No, because then it would fall under The Sale of Goods Act.
Only if something can be physically sold, rented out or gifted, then it
becomes a property. Data is an intimate connection between the human being
and the thing in question. It has tremendous value, hence, there are always
people waiting to take it. This was a concern in Puttaswamy vs Union of India
where the Supreme Court said: “Aadhaar is a serious invasion into the right to
privacy of persons and it has the tendency to lead to a surveillance state
where each individual can be kept under surveillance by creating his/her life
profile and movement as well on his/her use of Aadhaar.” ... Not everything is
clear yet. The consent conundrum remains. With the age of majority being 18,
all contracts under this age are said to have no value. Yet, when a child
clicks “I agree”, it technically becomes a contract. Children often lie and
say they are 18 and/or claim to have parental consent. Of course, it can have
positive outcomes too. The Justice gave an anecdote of his grandson being
aware of advanced mathematical concepts thanks to one Khan Academy. Consent
should be given in a manner which is understood.
Can Cloud Revolutionize Business and Software Architecture?

The physics behind software development changed completely in the past two to
five years, Ahlawat said, with the growth of hybrid, multicloud, and edge.
“Eighty percent of enterprises today have workloads that span multiple clouds
and two out of three of them are using multiple clouds for many strategic
reasons,” he said. That means applications in today’s environment can span
data centers and clouds as well as go to the edge. Tied to this trend is the
evolution of connected devices and the Internet of Things, Ahlawat said. “Up
until a few years ago, there was still a question whether IoT was hype,” he
said. “Today we have 20 billion connected devices generating about 50
zettabytes of data a year.” Use cases on this front, Ahlawat said, include
connected homes and smart cities, which still have room to grow to become
mainstream. The further development of data and AI also affects software
development, he said. “Of all the data generated ever, 90% of that was
generated in the last two years,” Ahlawat said. “When we talk with large
software companies and enterprises, data and AI are central to their
strategies.” This is unlocking transformative use cases such as autonomous
cars and medical imaging, he said.
'Scam-as-a-Service' Scheme Spreads
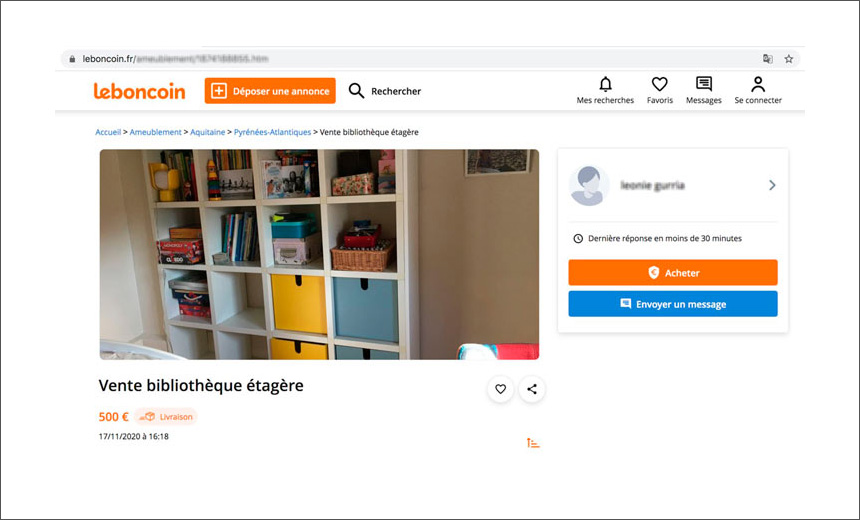
The fraudsters are posting fake online classified advertisements for products
to dupe interested buyers into visiting phishing pages, where their personal
and payment data is harvested, according to Group-IB. Although the operation
started in Russia two years ago, by early 2020, it had expanded to include 40
subgroups that have focused on targets in the U.S. and Europe, the new
research report says. Brands spoofed by the cybercriminal gang include French
marketplace Leboncoin, the Polish online brand Allegro, the Czech website
Sbazar and Romania's FAN Courier site. The report also notes the group has
expanded its operations in the U.S. and Bulgaria by mimicking FedEx and DHL
Express. ... The hackers have set up several Telegram chatbots for automated
management and expansion of the scheme, the report notes. These bots are
designed to provide scammers with ready-to-use pages mimicking popular
classified advertising, marketplace and phishing URLs. "Classiscam chatbots,
where fake pages are generated and profits are reported, are not completely
autonomous. They require ongoing technical support and moderation," says
Dmitriy Tiunkin, head of the digital risk protection department at Group-IB
Europe.
Successful Malware Incidents Rise as Attackers Shift Tactics
"That shift is really interesting because it starts to show the new reality of
the work device truly morphing into a work-and-personal device," Covington
says. "When you don't leave the house anymore, the phishing events and social
engineering events — the ways that attackers get into organizations — are not
just happening in the context of business email anymore." Others have noted
the impact of the move to remote work on security. In September, a survey of
CIOs found that 76% of the executives were worried that content sprawl put
company data at risk. An earlier survey found that about six in 10 workers
were using personal devices to work from home, and most of them considered the
devices to be secure. Wandera found a similar set of impacts from the move to
remote work, with many employees behaving differently. Because workers
traveled less, they were about half as likely to use a risky Wi-Fi connection
for work. And because personal time and work time blended together, a single
device had a greater blend of business and personal applications, says
Covington. "Honestly, they were looking to kill time," he says. "The types of
apps that we installed on work devices this year, we would not have typically
seen installed. A lot of games and a lot of productivity tools."
Drone Technology Extends Reach of Mobile IoT

Drones are typically equipped with two types of software. The software that’s
closely coupled with the drone hardware manipulates the drone and the gear to
keep it aloft while connecting it back to an operator who controls the drone’s
flight path. The second type of software is the application—the programs that
enables the drone to complete its specific task and to gather relevant
information. Currently, there are no standards for the control or the
application software, so a potential purchaser must be aware that the
application software usually has to be customized to work with a specific
manufacturer’s drone and its basic operating system. As a result, you have to
ensure that the software you need can actually run on the drone hardware you
intended to acquire. Skydio, for example, markets some applications software,
such as Skydio 3D Scan and Skydio House Scan, with its drones, and also
partners with third-party drone software makers for other applications. And,
of course, a potential user has to confirm that the format of the data that
the drone collects and disseminates is consistent with other formats currently
used by the data analysis programs already in place. Some integration work may
be required.
What analytics can unveil about bot mitigation tactics
Shortcomings have recently come to light about even the most common and accepted
bot mitigation technologies. For example, solutions offering CAPTCHA challenges
are not only ineffective at detecting and stopping automated attacks, but they
often lead to a friction-filled experience, frustrating customers and leading to
lower conversion rates. Many online retailers and e-commerce providers will
actually forgo implementing security due to fear that this friction will have a
negative impact on sales. Bot mitigation approaches that are based on
observations from historical and contextual data (e.g., IP addresses and
analysis of known behaviors) and then rely on taking steps to block similar
behavior can often block IP addresses or stop specific user behavior that might
not actually indicate an attack (e.g., late night banking or shopping). These
methods trigger poor experiences and have been shown through analysis to not
produce the desired mitigation or prevention results. More recently, use of a
rules-based architecture to prevent attacks has grown in popularity.
Unfortunately, a rules-based solution falls short when faced with advanced AI-
and ML- equipped bots that can morph on the spot to evade an organization’s
cyber defenses.
Quote for the day:
"When building a team, I always search first for people who love to win. If I can't find any of those, I look for people who hate to lose." -- H. Ross Perot
No comments:
Post a Comment