What industries need to avoid transformation limitations?

Already in 2020, we’ve seen dramatic change thanks to changing consumer
habits, a year of online-shopping, a variety of item delivery, pick-up and
return models, and store closures. These changes show no signs of slowing down
in the years ahead. Likewise, another two industries that are going to undergo
a sustained period of innovation-led change are the insurance and
transportation industries, respectively. All three will be absorbed by
broader, horizontal ecosystems. Although this change will be dramatic and may
cause some unrest at first, ultimately, it will mean happier and more loyal
customers and corporate leaders who are not under constant strain to reimagine
the business. This change is just the tip of the iceberg. Today’s successful
CEO would be wise to look at this trio of disappearing industries as canaries
in the mineshaft. The evolution from vertically-oriented industries to
horizontal ecosystems, constructed from a complex value chain of partners, has
begun. Transportation, insurance, and retail represent the three first
industries changing at a faster pace than other verticals. Any number of
sweeping technological breakthroughs — artificial intelligence (AI),
blockchain, the internet of things, and the data-crunching power of advanced
analytics — will have a similar impact on other industries.
Addressing the lack of knowledge around pen testing
Pen testing will only be truly effective if it is implemented with the right
processes, including both preparation and follow-up. Before carrying out the
test, it is important to have the scope and boundaries thoroughly documented.
This includes safeguards and processes to cover any issues that might result in
discovery, particularly when social engineering and physical security are
involved. We provide our team with Get Out of Jail Free cards that explain their
purpose and who to contact at the business to avoid a scenario like the Iowa
arrest. However, while someone at the organization must be aware of everything
the pen testers may be doing, it would be ideal that as few people as possible
know about it. It’s also important to have a clear strategy for following up
once the pen test results are in. Organizations are often fixated on the number
of issues a pen test uncovers (usually a greater number than they were
expecting). This information alone is useless, and priority should be given to
implementing a plan of action to close those gaps. Given the huge variation of
potential threats, the results of a pen test can feel overwhelming and
dispiriting.
Data Science Learning Roadmap for 2021
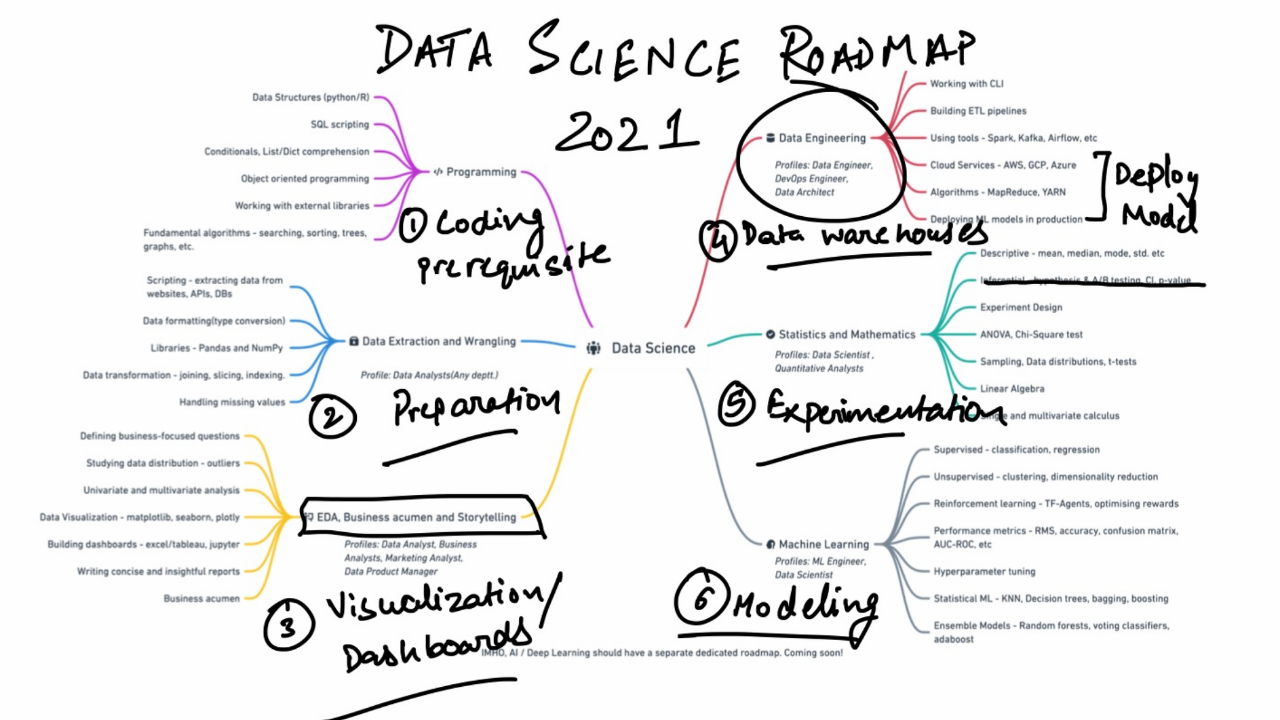
A significant part of data science work is centered around finding apt data
that can help you solve your problem. You can collect data from different
legitimate sources — scraping (if the website allows), APIs, Databases, and
publicly available repositories. Once you have data in hand, an analyst will
often find themself cleaning dataframes, working with multi-dimensional
arrays, using descriptive/scientific computations, and manipulating
dataframes to aggregate data. Data are rarely clean and formatted for use in
the “real world”. Pandas and NumPy are the two libraries that are at your
disposal to go from dirty data to ready-to-analyze data.... Data engineering
underpins the R&D teams by making clean data accessible to research
engineers and scientists at big data-driven firms. It is a field in itself
and you may decide to skip this part if you want to focus on just the
statistical algorithm side of the problems. Responsibilities of a data
engineer comprise building an efficient data architecture, streamlining data
processing, and maintaining large-scale data systems. Engineers use Shell
(CLI), SQL, and Python/Scala to create ETL pipelines, automate file system
tasks, and optimize the database operations to make them high-performance.
Donkey: A Highly-Performant HTTP Stack for Clojure
Clojure makes writing concurrent applications easy. It frees the developer
from the implications of sharing state between threads. It does so by using
immutable data structures, as described by Rich Hickey in his talk The Value
of Values: If you have a value, if you have an immutable thing, can you give
that to somebody else and not worry? Yes, you don't have to worry. Do they
have to worry about you now because they both now refer to the same value?
Anybody have to worry? No. Values can be shared. Because all objects are
immutable, they can be concurrently accessed from multiple threads without
fear of lock contention, race conditions, proper synchronization, and all the
other “fun” stuff that makes writing concurrent programs so difficult to get
right. The downside is that every mutating operation produces a new object
with an updated state. An inefficient implementation would cause a great deal
of CPU time to be wasted on copying and creating new objects and, as a result,
longer and more frequent GC cycles. Fortunately, Clojure uses a Hash Array
Mapped Trie (HAMT) to model its data structures internally. By sharing
structures that do not change, and copying only what does, it maintains
immutability and thread-safety - and does so at a minimal cost.
The UK’s struggle with digital schooling

“There is a huge digital divide and it is getting worse with schools being
shut down due to Covid-19. Teachers and school leaders are trying their best
to continue with online teaching by providing resources, virtual check-ins
and recorded lessons,” said EdTech adviser and consultant Joysy John, who
added that many children cannot access these services due to a lack of
technology or connectivity. “There are many new initiatives like Oak
National Academy, National Tutoring Programme and free resources from Edtech
companies, but these benefit those who already have digital access. So the
digital divide is going to get wider unless the government thinks of a more
holistic approach and provides disadvantaged parents with additional
financial and educational support.” Once the lockdown was announced,
education secretary Gavin Williamson outlined a number of plans for remote
education, including the mandate for schools to provide a set number of
hours of “high-quality remote education for pupils”. This is of no help to
those without access to online learning, so the government has tried to
address the digital divide causing disparity in home schooling during
pandemic lockdowns by giving laptops to those from under-privileged
backgrounds – something it began doing in the UK’s first lockdown.
SolarWinds Hack Lessons Learned: Finding the Next Supply Chain Attack
It is interesting to note that FireEye's initial detection of the SolarWinds
compromise didn't find complex lateral movement, or even data exfiltration.
What triggered FireEye's deeper investigation, according to reports, was an
unusual remote user login from a previously unknown device with an IP address
in a suspect location. It was only upon further review that FireEye discovered
the intrusion and ultimately traced it back to SolarWinds. This scenario, now
all too real for thousands of enterprises around the world, underscores the
importance -- if not necessity -- of having behavioral analytics as a key
component of contemporary enterprise cybersecurity product
architectures. Behavioral analytics supercharges threat detection by not
only analyzing event input based on activity from users and devices, but also
by using machine learning, statistical analysis and behavioral modeling to
correlate and enrich events. World-class behavioral analytics technology can
factor in a wide variety of data points -- such as peer groups, IP
association, personal email addresses, and kinetic identifiers like badge
reader activity -- to identify a malicious intrusion by stitching together a
half dozen or more events that, by themselves, would seem benign.
How IT must adapt to the emerging hybrid workplace

The implications for IT are many: extended support desk hours;
remote-support and remote-management tools; work-specific user training;
cloud enablement of all software possible; appropriate security for
distributed work; enabling multiple forms of collaboration and related
activities like scheduling, whiteboarding, and availability tracking;
provisioning equipment to home-based workers and/or supporting
employee-provided equipment; aiding Facilities in modernizing building
technologies to avoid touch-heavy surfaces; and partnering more closely with
HR for policy enablement and enforcement and for appropriate monitoring. ...
The workforce will not all work in the traditional office or company
location, nor will they all be remote. Many people will work from home, but
many people still need to work in a corporate facility, such as a production
line, data center, retail store, shipping center, lab, or even traditional
office. And there are employees whose work is location-agnostic but who
can’t work at home due to lack of space or insufficient internet access.
Gartner’s Adnams estimates that — although it varies by industry — about
half of the workforce in advanced economies will need to work in a corporate
facility, 25% to 30% will work permanently at home
Spotlight on home-office connectivity intensifies in 2021

"As the pandemic wears on, we are seeing organizations solidifying their
plans for remote working, including adding more sophisticated hardware and
software for work from home, with primary drivers including security and
productivity," said Neil Anderson, senior director of network solutions at
World Wide Technology, a technology and supply chain services company. "For
IT, this means quickly assessing and deploying new cloud-based security
models and building trust quickly in a solution," Anderson said. "We're also
seeing a lot of interest in experience monitoring and optimizing software to
put better analytics in place around what the home-office employee app
performance is like and how to make it better." While individuals have
limited options to speed up their home-office connectivity, IT can step in
to provide enterprise-grade services to high-value workers for whom every
minute with clients, customers, and coworkers counts, wrote Jean-Luc
Valente, Cisco vice president, product management, enterprise routing and
SD-WAN, in a blog post about the future of home office
connectivity. "The high-value workforce needs superior connectivity
that makes working at home just as fluid as being in the office with
consistent connectivity and performance. ... " Valente stated.
Competition and Markets Authority battles with cookies and privacy

The CMA said it had been considering how best to address legitimate privacy
concerns without distorting competition in discussions of the proposals with
the Information Commissioner’s Office (ICO), through the Digital Regulation
Cooperation Forum. As part of this work, the CMA said it had been in
discussions with Google to gain a greater understanding of the proposed
browser changes. The current investigation will provide a framework for the
continuation of this work, and, potentially, a legal basis for any solution
that emerges. Andrea Coscelli, chief executive of the CMA, said: “As the CMA
found in its recent market study, Google’s Privacy Sandbox proposals will
potentially have a very significant impact on publishers like newspapers, and
the digital advertising market. But there are also privacy concerns to
consider, which is why we will continue to work with the ICO as we progress
this investigation, while also engaging directly with Google and other market
participants about our concerns.” The CMA said it has an open mind and has not
reached any conclusions at this stage as to whether competition law has been
infringed.
Verizon CEO Talks 5G, Drones, and Compute at the Edge at CES
The move to the higher capacity broadband standard has been trumpeted by
others as the beginning of a new frontier with huge amounts of data moving
wirelessly. Vestberg said the speed of 5G would reveal new possibilities that
transform the world from playing video games to receiving deliveries. “Mobile
edge compute will allow businesses to get things done more quickly and
easily,” he said. Vestberg talked up the upload and download speeds of
Verizon’s 5G Ultra Wideband network, which he said sees peak throughputs of at
least 10 times faster that the 4G standard and more than 4 gigabits under
ideal conditions. The extremely low lag of 5G, Vestberg said, could eventually
make extremely delicate procedures such as remote surgery possible. He also
expects the new broadband standard to ramp up the population of connected
wireless devices. “In the future, 5G could support more devices than ever
before,” Vestberg said. “Up to one million per square kilometer.” The wireless
connections could also be support on devices moving more than 500 kmph, he
said, allowing users to maintain signal on highspeed vehicles such as commuter
trains, aerial drones, or self-driving cars.
Quote for the day:
"Authority without wisdom is like a heavy ax without an edge -- fitter to bruise than polish." -- Anne Bradstreet
No comments:
Post a Comment