15 SLA mistakes IT leaders still make

SLAs have often been a point of contention — not only between providers and
customers, but within organizations themselves. “It often boils down to IT
leaders hating to read legal agreements while procurement and legal teams can
be focused on business and financial risk rather than IT dependencies or the
impact of system outages to delivering services,” says Joel Martin, cloud
strategies research vice president at HFS Research. And as companies move more
solutions to the cloud, understanding the service levels agreed to is
important to developing trusted and dependable relationships. Moreover, SLA
development and management has evolved significantly in recent years, with an
eye toward driving business value. “Service recipients have become far more
sophisticated in how they manage SLAs,” says Marc Tanowitz, managing director
with West Monroe, adding that they “are looking for end-to-end outcomes that
drive business success and recognize that the true value of SLAs is to drive
business insights and performance — rather than to reduce the cost of service
by capturing performance credits.” Nonetheless, there remain some common — and
potentially costly — SLA mistakes IT leaders can make. Following are some of
the most detrimental to the IT organization and the business at large.
Ransomware provides the perfect cover
Attackers are constantly creating new variants that evade detection by
traditional signature-based approaches. To counteract these attacks, firms need
to have defence in depth. This starts with preventing threat actors from
infiltrating the network by defending against tactics such as phishing and
malware campaigns through staff training, the use of strong passwords, 2FA, and
patch management. If a threat actor makes it onto the system, their potential
for lateral movement is limited when organizations have deployed a
least-privilege approach, where access to files and folders is limited based on
job role or seniority. Behavioral anomalies are a prime indicator that a threat
actor could be on the network. This includes encrypting or downloading large
amounts of data or user accounts trying to access restricted data. Successfully
spotting such behaviour requires correlating data from many sources, including
endpoint and network detection and response solutions. Finally, to ensure they
can recover quickly in the event of a ransomware attack, organizations must also
have robust backups that they can rely on if their network does go down.
Cisco tags critical security holes in SD-WAN software

The first critical problem–with a Common Vulnerability Scoring System rating
of 9.9 out of 10–is vulnerability in the web-based management interface of
Cisco SD-WAN vManage Software. “This vulnerability is due to improper
input validation of user-supplied input to the device template
configuration,” Cisco stated. “An attacker could exploit this vulnerability
by submitting crafted input to the device template configuration. A
successful exploit could allow the attacker to gain root-level access to the
affected system.” This vulnerability affects only the Cisco SD-WAN vManage
product, the company stated. The second critical Cisco SD-WAN Software
issue–with a CVSS rating of 9.8—could let an unauthenticated, remote
attacker to cause a buffer overflow. “The vulnerability is due to incorrect
handling of IP traffic,” Cisco stated. “An attacker could exploit this
vulnerability by sending crafted IP traffic through an affected device,
which may cause a buffer overflow when the traffic is processed. A
successful exploit could allow the attacker to execute arbitrary code on the
underlying operating system with root privileges.”
Microsoft Releases New Info on SolarWinds Attack Chain
According to Microsoft, the attackers achieved this by using a known MITRE
attack method called event triggered execution, where malicious code is
executed on a host system when a specific process is launched. In this case,
the threat actors used the SolarWinds process to create a so-called Image File
Execution Options (IEFO) registry value for running the malicious VBScript
file when the dllhost dot exe process is executed on the infected system. The
dllhost dot exe process is a legitimate Windows process for launching other
applications and systems. When triggered, the VBScript then runs another
executable that activates the Cobalt Strike DLL in a process that is
completely disconnected and separate from the SolarWinds process. The VBScript
then also deletes the IEFO registry value and other traces of the sequence of
events that happened, according to Microsoft. The full motives behind the
operation and its victims remain unclear — or at least publicly undisclosed —
though some believe it may have been for corporate espionage or spying.
FireEye, Microsoft, the US Cybersecurity and Infrastructure Security Agency
(CISA), and numerous others have described the operation as being the work of
a highly sophisticated state-backed actor.
Accessible 5G: Making it a reality
To make 5G truly accessible to businesses, customers and consumers, we need
to improve connectivity for all by eventually converging cellular and
satellite networks to provide coverage both on land and via geo-satellite.
While 3G and 4G were primarily created to improve mobile services for mobile
device users, 5G is expected to support a much wider scope of IoT
applications. With more intelligence being packed into smart, connected
devices – we’ll need seamless connectivity and coverage. The hybrid network
will enable all types of industries, from education and healthcare to
construction and manufacturing, to not only use IoT technology to improve
services and efficiencies but remove operational complexities, such as
in-building coverage for more remote locations and black spots in
connectivity when laying foundations – think basement renovations and
housing developments in remote landscapes. As 5G-enabled smart devices and
IoT applications increase, so too will the volume of data transactions
between devices in the home: Smartphones, tablets, TVs, voice-assistance,
and white goods like refrigerators and smart ovens. The sheer volume of
applications transferring data to communicate with each other, for example,
using voice assistance to dim the lights and select a film to watch for a
night in, will require robust and seamless connectivity for the perfect
experience.
Fueled by Record Profits, Ransomware Persists in New Year
In 2020, exfiltrating data from victims before crypto-locking their systems and naming and shaming victims via leaks sites became common. Pioneered by the now-defunct Maze group in late 2019, many other groups followed suit. Those include Clop, DoppelPaymer, Nefilim, Sekhmet and, more recently, Avaddon. DoppelPaymer was also tied to an attack against a hospital in Germany, which led to a seriously ill patient having to be rerouted to another hospital. "This individual later died, though German authorities ultimately did not hold the ransomware actors responsible because the German authorities felt the individual's health was poor and the patient likely would have died even if they had not been re-routed," the FBI notes in a private industry alert issued last month. For exfiltrating data, "size doesn't matter" for attackers, Sophos says. "They don't seem to care about the amount of data targeted for exfiltration. Directory structures are unique to each business, and some file types can be compressed better than others. We have seen as little as 5GB, and as much as 400GB, of compressed data being stolen from a victim prior to deployment of the ransomware."The state of the dark web: Insights from the underground

According to Raveed Laeb, product manager at KELA, the dark web of today
represents a wide variety of goods and services. Although traditionally
concentrated in forums, dark web communications and transactions have moved
to different mediums including IM platforms, automated shops, and closed
communities. Threat actors are sharing covert intelligence on compromised
networks, stolen data, leaked databases and other monetizable cybercrime
products through these mediums. “The market shifts are focused on automation
and servitization [subscription models], aimed at aiding the cybercrime
business to grow at scale,” says Laeb. “As can be witnessed by the
exponential rise of ransomware attacks leveraging the underground financial
ecosystem, the cybercriminal-to-cybercriminal markets allow actors to
seamlessly create a supply chain that supports decentralized and effective
cybercrime intrusions—giving attackers an inherent edge.” ... “Defenders can
exploit these robust and dynamic ecosystems by gaining visibility into the
inner workings of the underground ecosystem—allowing them to trace the same
vulnerabilities, exposures, and compromises that would be leveraged by
threat actors and remediate them before they get exploited,” says Laeb.
New MIT Social Intelligence Algorithm Helps Build Machines That Better Understand Human Goals

While there’s been considerable work on inferring the goals and desires of
agents, much of this work has assumed that agents act optimally to achieve
their goals. However, the team was particularly inspired by a common
way of human planning that’s largely sub-optimal: not to plan everything out
in advance, but rather to form only partial plans, execute them, and then
plan again from there. While this can lead to mistakes from not thinking
enough “ahead of time,” it also reduces the cognitive load. For
example, imagine you’re watching your friend prepare food, and you would
like to help by figuring out what they’re cooking. You guess the next few
steps your friend might take: maybe preheating the oven, then making dough
for an apple pie. You then “keep” only the partial plans that remain
consistent with what your friend actually does, and then you repeat the
process by planning ahead just a few steps from there. Once you’ve
seen your friend make the dough, you can restrict the possibilities only to
baked goods, and guess that they might slice apples next, or get some pecans
for a pie mix. Eventually, you’ll have eliminated all the plans for dishes
that your friend couldn’t possibly be making, keeping only the possible
plans (i.e., pie recipes). Once you’re sure enough which dish it is, you can
offer to help.
5G: Opportunities and Challenges for Electric Distribution Companies
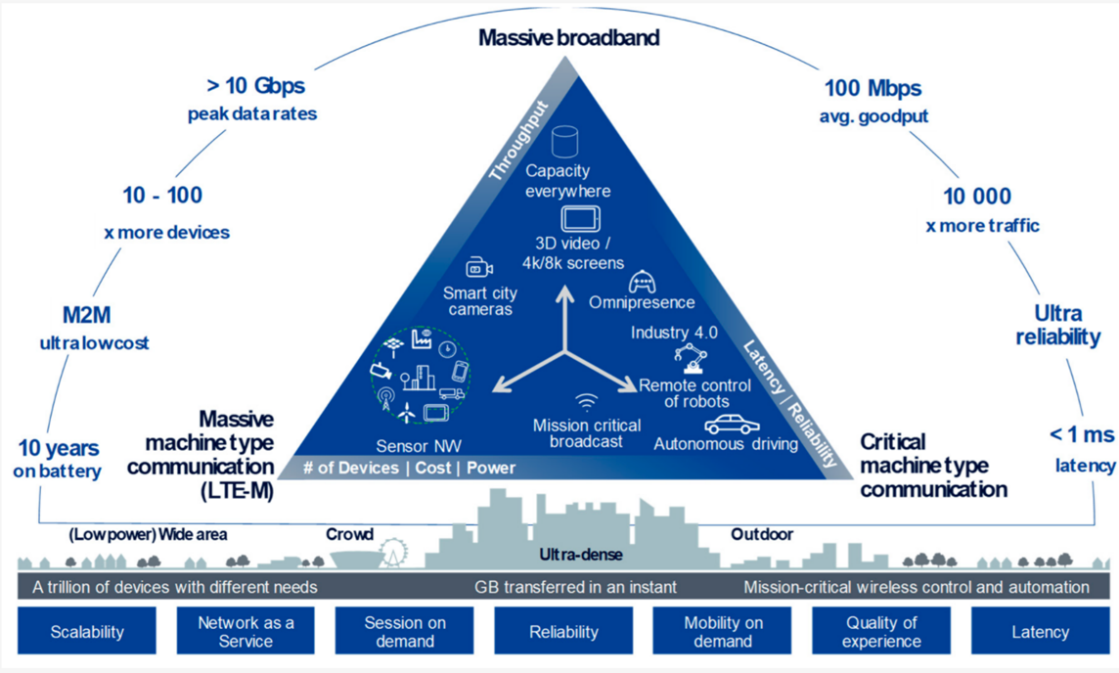
While the primary focus for this new technology from a common carrier’s
perspective seems to center around broadband services, the most likely areas
that will be important to electric utilities will be the increased capacity
to support field area network needs for connected grid devices. The "Grid of
Things" will greatly benefit from the connectedness afforded by the larger
IoT. "We plan to leverage our AMI network for connectivity needs, but that
may change as we deploy more 'grid-edge' devices," said an executive of a
mid-sized mid-Atlantic utility. Low-latency services potentially offer the
opportunity to leverage this technology to support mission critical
applications, such as protective relay management, SCADA, and substation
communications. "Use of 5G can potentially provide SCADA and other system
data over a cellular network versus a hard-wired solution through fiber or
copper," said a general manager of a Connecticut public utility. The high
data rate mmWave wireless broadband services may be applied to
augmented/virtual reality (AR/VR), an area where some utilities like Duke
Energy and EPRI are actively leveraging, and unmanned aerial vehicles (UAVs)
that will improve asset management and visualization.
Financial institutions can strengthen cybersecurity with SWIFT’s CSCF v2021
SWIFT created the CSP to support financial institutions in protecting their
own environments against cybercrime. The CSP established a common set of
security controls, the Customer Security Controls Framework (CSCF), designed
to help users secure their systems with a list of mandatory controls,
community-wide information sharing initiatives, and security features on their
payment infrastructure. The CSCF is designed to evolve based on threats
observed across the transaction landscape. The CSCF’s controls are centered
around three overarching objectives: Secure your environment; Know and
limit access; and Detect and respond. The updated CSCF v2021
includes changes to existing controls and additional guidance and
clarification on implementation guidelines. The newest version includes 31
security controls, 22 mandatory controls, and 9 advisory controls. Mandatory
controls must be implemented by all users on the user’s local SWIFT
infrastructure. Advisory controls are based on recommended best practices
advised by SWIFT.
Quote for the day:
"Education is what survives when what has been learned has been forgotten." -- B. F. Skinner
No comments:
Post a Comment