Threat Landscape for Industrial Automation Systems in H2 2017
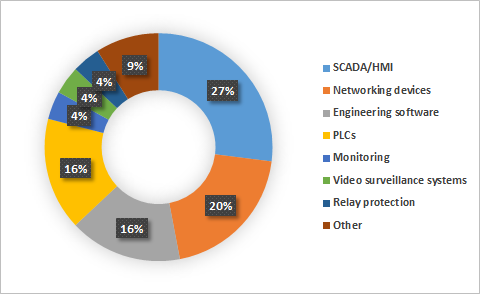
It should be noted that the CVSS base score does not account for the aspects of security that are specific to industrial automation systems or for the distinctive characteristics of each organization’s industrial processes. This is why, when assessing the severity of a vulnerability, we recommend keeping in mind, in addition to the CVSS score, the possible consequences of its exploitation, such as the non-availability or limited availability of ICS functionality that affects the continuity of the industrial process. The most common types of vulnerabilities include buffer overflow (Stack-Based Buffer Overflow, Heap-Based Buffer Overflow) and improper authentication (Improper Authentication). At the same time, 23% of all vulnerabilities identified are web-related (Injection, Path Traversal, Cross-Site Request Forgery (CSRF), Cross-Site Scripting) and 21% are associated with authentication issues (Improper Authentication, Authentication Bypass, Missing Authentication for Critical Function) and with access control problems.
Global organisations are failing to invest in much-needed security ahead of GDPR
Less than a third (31%) said they have invested in encryption, despite it being one of the few technologies named in the GDPR. Similarly, few organisations have spent money on data loss prevention (33%) or advanced technologies designed to detect network intruders (34%). A quarter of organisations (25%) claimed that limited resource are the biggest challenge to compliance, providing further insight into some of the reasons behind this under-investment. “The GDPR is clear that organisations must find state-of-the-art technologies to help repel cyber-threats and keep key data and systems secure. It’s concerning that IT leaders either don’t have the funds, or can’t find the right tools to tackle compliance,” said Simon Edwards, cyber security solution architect at Trend Micro. “Organisations need defence-in-depth combining a cross-generational blend of tools and techniques, from the endpoint to the network and hybrid cloud environment.”
To understand digital advertising, study its algorithms
Skinner invented a device, now known as a Skinner box, which standardised the process of behavioural experimentation. He used his boxes to control input stimuli (food, light, sound, pain) and then observed output behaviour in an attempt to link the one to the other. Though by no means perfect, the Skinner box was a big advance in the field. Dr Rahwan hopes to do something similar to software using what he calls a Turing box. This “box” is itself a piece of software. Place an algorithm in it, control the data inputs, measure the outcomes, and you will be able to work out exactly how it behaves in different circumstances. Anyone who wants to study an algorithm could upload it to a Turing box. The box’s software would then start running the algorithm through a standard data set of the kind it was designed to crunch. All face-recognition algorithms, for example, would be given the same scientifically validated set of faces. The algorithm’s output—in this case how it classifies different faces—would be recorded and analysed.
Where do mobile users fit in with SD-WAN as a service?

Two trends are causing network architects to take a closer look at how mobile users connect to and access company resources using modern technologies. The first is the fact that most workforces are becoming increasingly mobile in nature. Employees often have the need to work from home or on the go. These employees want to be able to seamlessly access business apps whether they're at home, at a coffee shop or in a taxi driving across town. The second trend is a movement toward the use of public cloud, as opposed the company's private data center. Common remote access network designs force users to connect to the corporate office network before accessing company resources. This is typically achieved by using remote access VPN client software. If the apps and data no longer reside on the corporate network, however, it's inefficient for users to connect to the corporate office first, only to be redirected back through the internet to public cloud resources.
Great expectations lead to a brave new world
Cloud adoption doesn't just happen; there is a reason for its use. It may be the development of a new application, it may be the end of life of existing hardware or it may be a strategic decision at the highest level. But the decision to use cloud is usually a perfect storm of factors – the current price of resources, issues in finding appropriate staff, a desire to scale and grow, or the ease of using a third party. The spark represents the 'why do this now?' The factors represent the 'why use cloud now?' A primary factor for cloud adoption is reduced costs compared with traditional models, as shown in this chart from Voice of the Enterprise: Cloud Transformation, Organizational Dynamics 2017. CIOs have great expectations with regard to the cost savings that might be achieved relative to traditional platforms. But cost isn't the only driver: The inherent nature of pay-as-you-go pricing and the scalability and time to market it enables are also major motivations, as are availability and performance.
Why Monero Is Going to War Against Big Miners
Largely referred to as monero's first move in a "war" against ASICs, the upcoming software upgrade will render the Antminer X3 ineffective. Not only that but to keep hardware manufacturers from catching up, these algorithm edits are planned to continue with bi-annual networks upgrades. Stepping back, the move is a defense of the mining made possible by monero's current algorithm, Cryptonight, which can successfully mine monero on consumer-grade laptops. Faced with competition by highly efficient ASICs, the fear is affordable laptop mining would be silenced. And that's not a development developers are taking lightly. "I will do everything in my power to help the community prevent the proliferation of centralization-inducing ASICs on the monero network," core developer Riccardo "Fluffypony" Spagni declared on GitHub. Currently issued by a sole supplier, Bitmain, concerns exist that the Antminer X3 could lead to certain kinds of attacks, namely ones in which a mining pool takes over the majority of a cryptocurrency's hashrate, creating false transaction histories, double spending coins and censoring payments.
Transparent Digital Transformations Mitigate Risk, Aid Business Objectivity

In order to stay competitive, business leaders need to ensure their organisations embrace new technologies, which are already digitally transforming their organisation and industry. However, without an accurate foundation of knowledge about their existing IT infrastructure, their technology procurement decisions will always be risky. Digital Transformation occurs in two ways. Firstly, organisations implement incremental improvements that help parts of the organisation to better perform their fundamental business tasks. Secondly, the organisation completely changes the way it does business—by adjusting its business model or taking advantage of new markets or products—which has the potential to transform the industry and disrupt several others. All large organisations run complicated IT systems that contain a mix of hardware, software and services from a variety of vendors. Making fundamental changes to any such system can result in unexpected side-effects, complications and costs.
The Power of Doubt in Software Testing
It starts with being skeptical of ourselves, with knowing our own biases. We can't trust our eyes, ears or even our memories. Realise that we get fooled easily, on a daily basis. Knowing that we are easy to fool keeps us on our toes, and forces our mind to work harder. I also try to be skeptical of what the majority believes. When you share your opinion with others, it becomes difficult to change your mind. It’s hard to argue against what everyone else believes, conventional wisdom and "accepted truths”. When one person posits a belief, there can be disagreement or debate. But when more than one person agrees that something is the truth, this often shuts down our own inquiry. My adventures in skepticism taught me that we should also be skeptical of certainty. The feeling of certainty is a tricky thing. Scientific studies have shown that, despite how certainty feels, it is neither a conscious choice nor even a thought process. Certainty arises out of brain mechanisms that, like love or anger, function independently of reason.
6 Myths CEOs Believe About Security

Part of the reason for the nihilistic belief that hackers and malware can never be fixed is that the world thinks that hackers are all brilliant, can’t-be-stopped, super geniuses. This romantic ideal is readily promoted in Hollywood films that often show the hacker taking over the entire world’s computers by easily guessing passwords into any system they are presented with. Movie hackers outsmart everyone and can launch nuclear missiles and erase people’s digital identities with a few keystrokes. This mistaken ideal is believed because most people that get hacked or infected with malware aren’t programmers or IT security people. To them it’s sort of like a magical event that must have required Lex Luthor superpowers. The reality is that most hackers are average joes with average intelligence and are more akin to plumbers and electricians than Einstein. Hackers just know how to accomplish a particular trade using particular tools passed down by previous tradespeople, but instead of plumbing and electricity, it’s computer hacking.
Behavior-tracking security tech gaining traction at banks

“The thing about most of these behavioral biometrics is that they’re passive. They’re happening in the background and the end user doesn’t feel intruded upon,” said Kathleen Peters, Experian’s senior vice president of global fraud and security. BioCatch is now exploring other use cases, like authenticating new customers at the time of sign up, said Frances Zelazny, vice president of marketing at BioCatch. It is also expanding into other industries, such as payroll processing and insurance, she said. ... Increasingly, companies in need of fraud prevention are asking their service providers whether they also offer those same behavioral biometrics protections. “If you’ve worked with product managers, you know it takes a while to integrate those capabilities and things that show up on product road maps, but we’re actually seeing these capabilities being integrated with other solutions and they’re live,” Pascual said. “That tells you that in this short time frame since BioCatch came into existence, how much interest there really is.”
Quote for the day:
"A bad habit never disappears miraculously; it's an undo-it-yourself project." -- Abigail Van Buren
No comments:
Post a Comment