Why Your Business May Want to Shift to an Industry Cloud Platform

Industry cloud services typically embed the data model, processes, templates, accelerators, security constructs, and governance controls required by the adopter's industry, says Shriram Natarajan, a director at technology research and advisory firm ISG, in an online interview. "This [approach] allows faster development of new functionality, better security and governance, and an enhanced and user/stakeholder experience." ... Enterprises spanning many industries can benefit significantly by moving to an industry cloud platform, Campbell says. "Businesses that are faced with many regulations and operational requirements can especially benefit from the specialized services industry cloud platforms," he notes, adding that many industry cloud platforms are preconfigured to meet specific needs, which can help accelerate the time to value realized. Many enterprises have a blinkered view on verticalized solutions, Natarajan says. "They tend to see the platforms they already have in-house and look for solutions that these platforms provide." He believes that enterprise IT and business teams can both benefit from looking at the landscape of verticalized industry cloud platforms.
FRAML Reality Check: Is Full Integration Really Practical?

While integration between AML and fraud teams is a desirable goal, experts say
it should not be viewed as the best solution. Paul Dunlop, insider risk
consultant at a financial services firm, stressed the importance of
collaboration over integration. "I am against the oversimplification of fraud
and AML integration. Banking risks are multifaceted, involving not just fraud
and AML but also cybersecurity, privacy and other domains," Dunlop said.
"Integration decision should be assessed based on the bank's maturity level,
regulatory environment and unique operational needs." "Cost should not be the
sole factor behind this decision. One must assess operational and risk
management trade-offs," he said. Meng Liu, senior analyst at Forrester, said
that despite AML and fraud being two distinct functions at present, the trend
toward more consolidated and integrated financial crime management is real. ...
Despite the differences in fraud and AML teams, some use cases, such as scams,
human trafficking and child exploitation, cry out for better collaboration,
Mitchell said. "These require shared data and aligned strategies." But
high-volume fraud detection such as check and card fraud is less suited for
joint efforts due to operational complexity.
Ransomware abuses Amazon AWS feature to encrypt S3 buckets

In the attacks by Codefinger, the threat actors used compromised AWS credentials
to locate victim's keys with 's3:GetObject' and 's3:PutObject' privileges, which
allow these accounts to encrypt objects in S3 buckets through SSE-C. The
attacker then generates an encryption key locally to encrypt the target's data.
Since AWS doesn't store these encryption keys, data recovery without the
attacker's key is impossible, even if the victim reports unauthorized activity
to Amazon. "By utilizing AWS native services, they achieve encryption in a way
that is both secure and unrecoverable without their cooperation," explains
Halcyon. Next, the attacker sets a seven-day file deletion policy using the S3
Object Lifecycle Management API and drops ransom notes on all affected
directories that instruct the victim to pay ransom on a given Bitcoin address in
exchange for the custom AES-256 key. ... Halcyon also suggests that AWS
customers set restrictive policies that prevent the use of SSE-C on their S3
buckets. Concerning AWS keys, unused keys should be disabled, active ones should
be rotated frequently, and account permissions should be kept at the minimum
level required.
How AI and ML are transforming digital banking security
By continuously learning from new data, ML improves over time, adapting to the
organization’s needs and the ever-evolving fraud tactics. This supports reducing
false positives, ensuring legitimate transactions proceed smoothly while
maintaining security. Predictive analytics also help identify potential threats
before they materialize, and fraud scoring prioritizes high-risk activities for
action. AI/ML-powered systems are scalable and effective against sophisticated
threats, such as synthetic identity fraud and account takeovers, and can monitor
multiple banking channels simultaneously. They automate detection, lowering
operational costs, and providing seamless customer experiences, thereby
enhancing trust. However, nothing is a silver bullet and considerations must be
made to things such as algorithm bias, data privacy concerns, and the need for
explainable models persist. Still, despite these potential hurdles, AI and ML
are reshaping digital banking security, equipping financial institutions
with proactive tools to counter fraud while safeguarding customer trust and
regulatory compliance. ... Advanced technologies like AI and ML are helping
institutions monitor transactions in real time, detecting anomalies and
preventing fraud without directly involving users. Meanwhile, encryption and
tokenization protect sensitive data, ensuring transactions remain secure in the
background.
The Evolution of Business Systems in the Digital Era

Systems of Record (SORs) serve as the foundation of organizational
infrastructure, storing essential data such as customer information, financial
transactions, and operational processes. These systems are designed to maintain
structured and reliable records, ensuring data integrity, compliance, and
security. They play a critical role in regulatory reporting, audits, and
operational consistency. ... Systems of Engagement (SOEs) are the digital front
doors of modern businesses, facilitating seamless and interactive communication
with customers and employees. They go beyond simple data storage and retrieval,
focusing on creating dynamic and personalized experiences across various
channels. SOEs prioritize customer-centric approaches, ensuring businesses can
deliver dynamic and interactive communication. ... Systems of Intelligence
(SOIs) represent the pinnacle of data-driven decision making. Built upon the
foundation of Systems of Record (SORs) and Systems of Engagement (SOEs), SOIs
leverage the power of artificial intelligence (AI) and machine learning (ML) to
transform raw data into actionable insights. Unlike their predecessors, SOIs go
beyond simply identifying patterns and trends. They possess the ability to
predict future outcomes and even prescribe optimal courses of action.
Gen AI strategies put CISOs in a stressful bind

One of the most problematic gen AI issues CISOs face is how casual many gen AI
vendors are being when selecting the data used to train their models, Townsend
said. “That creates a security risk for the organization.” ... generative AI’s
penetration into SaaS solutions makes this more problematic. “The attack
surface for gen AI has changed. It used to be enterprise users using
foundation models provided by the biggest providers. Today, hundreds of SaaS
applications have embedded LLMs that are in use across the enterprise,” said
Routh, who today serves as chief trust officer at security vendor Saviynt.
“Software engineers have more than 1 million open source LLMs at their
disposal on HuggingFace.com.” ... All this can take a psychological toll on
CISOs, Townsend surmised. “When they feel overwhelmed, they shut down,” he
said. “They do what they feel they can, and they will ignore what they feel
that they can’t control.” ... “The bad actors are feverishly working to
exploit these new technologies in malicious ways, so the CISOs are right to be
concerned about how these new gen AI solutions and systems can be exploited,”
Taylor said.
How Enterprises and Startups Can Master AI With Smarter Data Practices

For enterprises, however, supplying AI systems with the data they need to
thrive is more complicated by several orders of magnitude. There are two main
reasons for this: First, enterprises don’t have the same information
aggregation ability in the consumer AI world. Consumer AI companies can use
any public data on the web to train their AI models; think of it as an entire
continent of information to which they have unfettered access. On the other
hand, enterprise data exists within minor, disparate, and oftentimes
disconnected information archipelagos. Additionally, enterprises are working
with many types of data, including relational data from operational systems,
decades of poorly organized folders of documents, and audio and numeric data
from payroll and financial systems. Further, enterprises must contend with
additional layers of regulatory complexity regarding handling personal and
private data. To build impactful AI tools, an enterprise’s algorithms must be
fed or trained on specific data sets that span multiple sources, including the
company’s human resources, finance, customer relationship management, supply
chain management, and other systems.
Yes, you should use AI coding assistants—but not like that

AI is a must for software developers, but not because it removes work. Rather,
it changes how developers should work. For those who just entrust their coding
to a machine, well, the results are dire. ... Use AI wrong and things get
worse, not better. Stanford researcher Yegor Denisov-Blanch notes that his
team has found that AI increases both the amount of code delivered and the
amount of code that needs reworking, which means that “actual ‘useful
delivered code’ doesn’t always increase” with AI. In short, “some people
manage to be less productive with AI.” So how do you ensure you get more done
with coding assistants, not less? ... Here’s the solution: If you want to use
AI coding assistants, don’t use them as an excuse not to learn to code. The
robots aren’t going to do it for you. The engineers who will get the most out
of AI assistants are those who know software best. They’ll know when to give
control to the coding assistant and how to constrain that assistance (perhaps
to narrow the scope of the problem they allow it to work on). Less-experienced
engineers run the risk of moving fast but then getting stuck or not
recognizing the bugs that the AI has created. ... AI can’t replace good
programming, because it really doesn’t do good programming.
AI Tools Amplify API Security Threats Worldwide

The financial implications of API breaches prove substantial. According to
Kong's report, 55% of organizations experienced an API security incident in
the past year. Among those affected, 47% reported remediation costs exceeding
$100,000, while 20% faced expenses surpassing $500,000. Gartner's research
underscores this urgency, highlighting that API breaches typically result in
ten times more leaked data than other types of security incidents. ... While
AI technologies, particularly LLMs, drive unprecedented innovation, they
introduce new vulnerabilities. These advanced tools enable attackers to
exploit shadow APIs, bypass traditional defenses and manipulate API traffic in
unexpected ways. The survey indicates that 84% of leaders predict AI and LLMs
will increase the complexity of securing APIs over the next two to three
years, emphasizing the need for immediate action. Despite 92% of organizations
implementing measures to secure their APIs, 40% of leaders remain skeptical
about whether their investments will adequately counter AI-driven risks. The
regional disparity in preparedness stands out: 13% of U.S. organizations
acknowledge taking no specific measures against AI threats, compared to 4% in
the U.K.
From AI Assistants to Swarms of Thousands of Collaborating AI Agents: Is Your Architecture Ready?
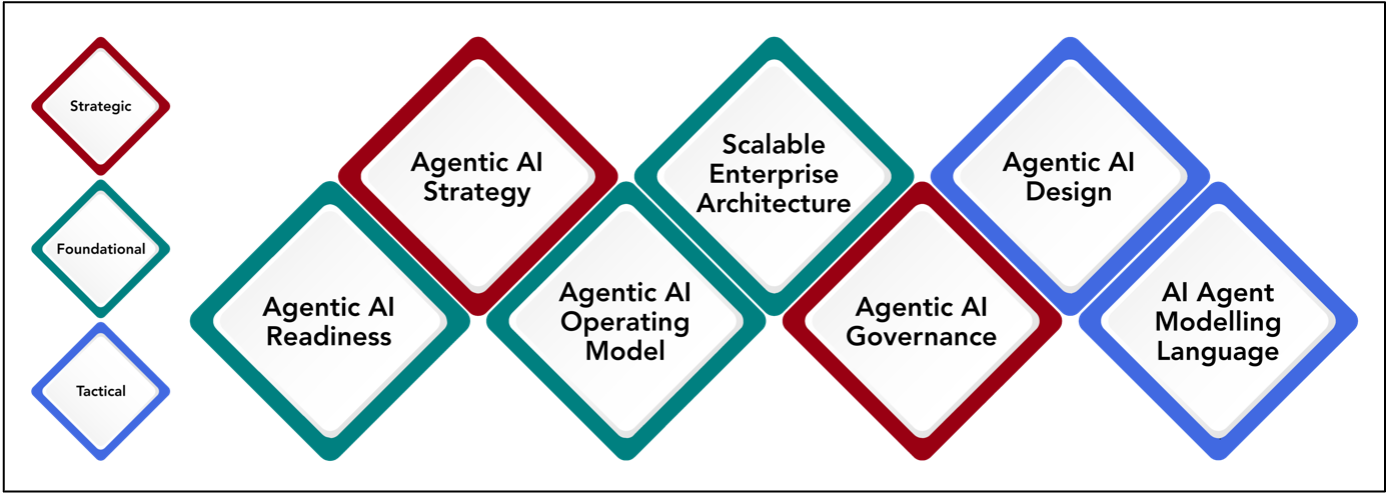
Agentic AI is likely to create most issues in some areas more than others. The
Agentic Architecture Framework identifies seven areas that will require more
support in the forms of new or updated frameworks, tools and techniques to
support Agentic AI capability-building and architecture development. ...
Agentic AI Strategy begins with defining a clear target state across the
Agentic AI maturity dimensions and levels. This step establishes the
organization’s AI aspirations and provides a benchmark for future
transformation. Once the target state is identified, the next step involves
conducting a GAP analysis to determine the differences between current
capabilities in the previous step, and the organization’s ambition. With these
gaps clarified, organizations can then focus on identifying and quantifying
high-impact AI use cases that align with business objectives and support
progression toward the target state. ... The Agentic AI Operating Model
defines how AI systems, people, and processes work together to deliver value.
It focuses on integrating AI into the organization’s core operations, ensuring
that AI agents operate seamlessly within new and existing workflows and
alongside human teams.
Quote for the day:
"No person can be a great leader
unless he takes genuine joy in the successes of those under him." --
W. A. Nance
No comments:
Post a Comment