Managing Third-Party Risks in the Software Supply Chain

The myriad of third party risks such as, compromised or faulty software
updates, insecure hardware or software components and insufficient security
practices, expand the attack surface of the organization. A security breach in
one such third party entity can ripple through and potentially lead to
significant operational disruptions, financial losses and reputational damage
to the organization. In view of this, securing not just their own
organizations, but also the intricate web of suppliers, vendors and partners
that make up their cyber supply chain is not just an option, but a necessity.
It is needless to state that managing the third party risks is becoming a big
challenge for the Chief Information Security Officers. More to it, it may not
just be enough to maanage third-party risks but also fourth party risks as
well. ... Mapping your most critical third-party relationships can identify
weak links across your extended enterprise. But to be effective, it needs to
go beyond third parties. In many cases, risks are often buried within complex
subcontracting arrangements and other relationships, within both your supply
chain and vendor partnerships. Illuminating your extended network to see
beyond third parties is critical to assessing, mitigating and monitoring the
risks posed by sub-tier suppliers.
6G, AI and Quantum: Shaping the Future of Connectivity, Computing and Security

Beyond 6G, another transformative technology that will reshape industries in
2025 is quantum computing. This isn’t just about faster processing; it’s about
tackling problems that are currently intractable for even the most powerful
conventional systems. Think of the implications for AI training itself –
imagine feeding massive, complex datasets into quantum-powered algorithms. The
potential for breakthroughs in AI research and development is immense. This
next-gen computational power is expected to solve complex problems that were
previously deemed unsolvable, ushering in a new era of innovation and
efficiency. The impact of these developments will be felt in a range of
industries such as pharmaceuticals, cryptography and supply chains. For
instance, in the pharmaceutical sector, quantum computing is set to speed up
drug discovery. ... The rise of distributed cloud models and edge
computing will also speed up services and provide value and innovation –
placing cloud technology at the centre of every organisation’s strategic
roadmap. Leveraging cloud infrastructure allows businesses to rapidly scale AI
models, process enormous volumes of data in real-time, and generate actionable
insights that facilitate intelligent decision-making.
Advancing Platform Accountability: The Promise and Perils of DSA Risk Assessments

Multiple risk assessments fail to meaningfully consider risks related to
problematic and harmful use and the design or functioning of their service and
systems. Facebook’s 2024 risk assessment assesses physical and mental
wellbeing in a crosscutting way but does not meaningfully consider risks
related to excessive use or addiction. Other assessments more centrally
consider physical and mental well-being risks. ... Snap’s risk assessment
devotes seven pages to physical and mental well-being risks, but the
assessment fails to consider how platform design could contribute to physical
and mental well-being risks by incentivizing problematic or harmful use.
Snap’s assessment is broadly focused on risks related to harmful content. The
assessment describes mitigations to reduce the prevalence of such content that
could impact physical and mental well-being – including auto-moderating for
abusive content or ensuring recommender systems do not recommend violative
content. This, of course, is important. However, the risk assessment and
review of mitigations place almost no emphasis on risks of excessive use
actually driven by Snap’s design. Snap’s focus on ephemeral content is
presented as only a benefit – “conversations on Snapchat delete by default to
reflect real-life conversations.”
Hard and Soft Skills Go Hand-in-Hand — These Are the Ones You Need to Sharpen This Year
To most effectively harness the power of AI in 2025, leaders need to
understand it. DataCamp's Matt Crabtree describes AI literacy, at its most
basic, as having the skills and competencies required to use AI technologies
and applications effectively. But it's much more than that: Crabtree points
out that AI literacy is also about enabling people to make informed decisions
about how they're using AI, understand the implications of those uses and
navigate the ethical considerations they present. For leaders, that means
understanding biases that remain embedded in AI systems, privacy concerns, and
the need for transparency and accountability. Say you're looking to integrate
AI into your hiring process, as we have at my company, Jotform. It's important
to understand that while it can be used for tasks like scheduling interviews,
screening resumes for objective criteria or helping to organize candidate
information, it should not be making hiring decisions for you. AI still has a
significant bias problem, in addition to the many other ways in which it lacks
the soft skills required for certain, human-only tasks. AI literacy is about
understanding its shortcomings and navigating them in a way that is fair and
equitable.
The Tech Blanket: Building a Seamless Tech Ecosystem

The days of disconnected platforms are over. In 2025, businesses will embrace
platform interoperability to ensure that knowledge and data flow seamlessly
across departments. Think of your organization’s technology as a woven
blanket—each tool and system represents a thread that, when tightly
interwoven, creates a strong, cohesive layer of support that covers your
entire company. ... Building a seamless ecosystem begins with establishing a
framework for managing distributed information. By creating a Knowledge Asset
Center of Excellence, organizations can define norms for how data and
knowledge are shared and governed. This approach fosters collaboration while
allowing teams the flexibility to work in ways that suit their unique needs.
... As platforms become more interconnected, ensuring robust security becomes
critical. Data breaches or inaccuracies in one tool can ripple across the
ecosystem, creating significant risks. Leaders must prioritize tools with
advanced security features, such as encryption and role-based access controls,
to protect sensitive information while maintaining seamless interoperability.
Strong data governance policies are also essential. By continuously monitoring
data flow and usage, organizations can safeguard the integrity of their
knowledge assets while promoting responsible collaboration.
WebAssembly and Containers’ Love Affair on Kubernetes

WebAssembly is showing promise on Kubernetes thanks to the fact that
WebAssembly now meets the OCI registry standard as OCI artifacts. This enables
Wasm to meet the Kubernetes standard and the OCI standard for
containerization, specifically the OCI artifact format. It also involves
compatibility with Kubernetes pods, storage interfaces and more. In that
respect, it’s one step toward using Wasm as an alternative to containers.
Additionally, through containerd, WebAssembly components can be distributed
side by side with containers in Kubernetes environments. Zhou likened this to
a drop-in replacement for the unit’s containers, integrating with tools such
as Istio, Dapr and OpenTelemetry Collector. ... When running applications
through WebAssembly as sidecars in a cluster, the two main challenges involve
distribution and deployment, as Zhou outlined. A naive approach bundles the
Wasm runtime into a container, but a better method offloads the Wasm runtime
into the shim process in containerd. This approach allows Kubernetes
orchestration of Wasm workloads. The OCI artifact format for WebAssembly,
enabling Wasm components to use the same distribution mechanisms as
containers, is responsible for the distribution part, Zhou said.
Training Employees for the Future with Digital Humans

Digital humans leverage a host of advanced technologies, large language
models, retrieval-augmented generation, and intelligent AI orchestrators,
among them. They also use unique techniques like kinesthetic learning, or
“learning by doing,” alongside on-screen visuals to better illustrate more
complicated topics. Note that digital humans are not like traditional chatbots
that follow structured dialog trees. Instead, they can respond dynamically to
the employee's inputs to ensure interactions are as lifelike as possible. ...
By allowing employees to apply their training in real-world scenarios, digital
humans help them keep more information in a shorter amount of time, reducing
traditional training timelines significantly. As a result, businesses will
spend less money and time reskilling personnel. The training possibilities
with digital humans are vast, helping employees learn to use new technologies
and systems. In a sales setting, personnel can practice using new generative
AI-powered customer service tools while a digital human pretends to be a
customer. Digital humans could also help engineers in the automotive space
learn how to use machine-learning solutions or operate 3D printing
machines.
From Silos to Synergy: Transforming Threat Intelligence Sharing in 2025

Put simply, organizations must break down the silos between ALL teams involved
in security. This is not just about understanding the organization’s cyber
hygiene, but it is also about understanding the layers that an attacker would
have to get through to exploit and conduct potentially nefarious activities
within the business. Once this insight is gained this enables teams to work
through requirements and align the CTI program for specific stakeholders. This
means that both offense and defense teams are working together, mapping out
the attack path and gaining a better understanding of defense. Doing this will
provide a better understanding of offense as teams scout to look at what could
be effective, going to the next layer to consider what might be vulnerable and
whether they have mitigating controls in place to provide any additional
prevention. ... In the past, teams working on-site together would document
their work on a whiteboard. Now, with the advent of remote working, there are
fewer opportunities to share in person, and a plethora of communication
channels that lead to knowledge fragmentation as different people use
different tools such as Slack or other messaging platforms, or would just
share intelligence one-on-one.
Explained: The Multifaceted Nature of Digital Twins

Beyond operational improvements, digital twins also drive innovation at scale.
Large enterprises with multiple R&D hubs can test new designs or processes
in a virtual environment before deploying them globally. For example, an
automotive company developing an electric vehicle can simulate how it will
perform under different driving conditions, regulatory frameworks and consumer
preferences in diverse markets - all within a digital twin. ... Building and
maintaining a digital twin requires significant investment in IoT
infrastructure, cloud computing, AI and skilled personnel. For many companies,
particularly small and medium-sized enterprises, these costs can be
prohibitive. A McKinsey study highlights that digital maturity - the ability
to effectively integrate and utilize advanced technologies - is often a key
barrier. Seventy-five percent of companies that have adopted digital-twin
technologies are those that have achieved at least medium levels of
complexity. Large enterprises can justify the cost of digital twins by
applying them across multiple facilities or product lines, but for smaller
companies, the benefits may not scale as effectively, making it harder to
achieve a return on investment.
Design Patterns for Building Resilient Systems
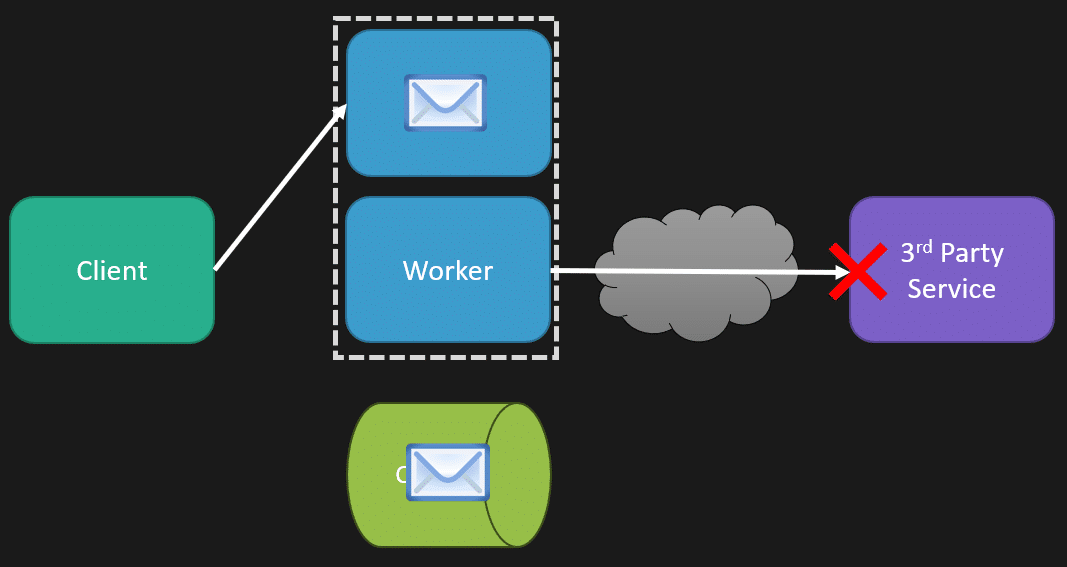
You may have some parts of your system that are degrading performance and may
be affecting cascading failures everywhere. So that means that when your
client requests a specific part that’s working fine, it’s great, but you want
to stop immediately what’s causing the fire. That way, you have different load
balancing rules that I’ve defined here to say, okay, this part of our system
is degrading performance; it’s starting to affect everything else, and it’s
cascading failures. We’re just going to stop it so you can’t even make a
request to this route because it’s the one causing all the issues. Having your
clients handle that failure to that request gracefully can be incredibly
important because then the rest of your system can still work. Maybe some
particular routes you’re defining aren’t going to work; some parts of your
system will just be unavailable, but it’s not taking down the entire thing.
Ultimately, what I’m talking about there is bulkheads. ... Now, while the
CrowdStrike incident didn’t directly affect me, it sure did indirectly because
I knew about it right away from the alarms based on metrics. When used
correctly within context, design patterns allow you to build a resilient
system. Now, everything we had in place for resilience helped; they worked.
But as always, when something like this happens, it makes you re-evaluate
specific individual contexts.
Quote for the day:
"Great leaders do not desire to lead
but to serve." -- Myles Munroe
No comments:
Post a Comment