Building AI agents with Semantic Kernel

Microsoft’s Semantic Kernel team is building on OpenAI’s Assistant model to
deliver one kind of intelligent agent, along with a set of tools to manage
calling multiple functions. They’re also providing a way to manage the messages
sent to and from the OpenAI API, and to use plugins to integrate general purpose
chat with grounded data-driven integrations using RAG. The team is starting to
go beyond the original LangChain-like orchestration model with the recent 1.01
release and is now thinking of Semantic Kernel as a runtime for a contextual
conversation. That requires a lot more management of the conversation and prompt
history used. All interactions will go through the chat function, with Semantic
Kernel managing both inputs and outputs. There’s a lot going on here. First,
we’re seeing a movement towards an AI stack. Microsoft’s Copilot model is
perhaps best thought of as an implementation of a modern agent stack, building
on the company’s investment in AI-ready infrastructure (for inference as well as
training), its library of foundation models, all the way up to support for
plugins that work across Microsoft’s and OpenAI’s platforms.
CISOs’ role in identifying tech components and managing supply chains
A big problem today is that security teams are only involved at the end of a
project as part of a “final sign-off” in many organizations. This creates
friction between developers and security engineers; both may see the other as
the root of the problem: “If these developers only wrote secure code, everyone’s
lives would be easier.” and “Oh great, the security team is going to find a
bunch of bugs and delay our launch. Again.” Organizations that involve security
teams with development during the initial stages of design and scoping and have
a few security reviews during the development process allow bugs to be addressed
early in the cycle and provide an opportunity for the security team to educate
developers on standard insecure coding practices. While no solution is perfect,
this approach – adopted by companies like Microsoft in developing HyperV – helps
avoid last-minute delays and animosity between the teams. ... Supply chain
security needs to be a priority early in the development lifecycle. At the very
least, open-source libraries and components should be audited for known
vulnerabilities, and it’s worth looking at the vulnerability history of a
component.
Navigating the Complexities of AI With a Socially Conscious Lens
The rapid spread of AI technology, while offering significant advantages, has
also given rise to several concerning trends. Bias and discrimination inherent
in AI systems can replicate and amplify existing societal prejudices, often at
the expense of marginalized groups. Privacy erosion, another critical issue,
poses risks of surveillance and data misuse. Additionally, the threat of job
displacement due to automation, security vulnerabilities, and the ethical
concerns posed by AI decision-making in sensitive areas are challenges that
require immediate and thoughtful attention. In the context of hiring and
recruiting, AI-driven bias is a significant concern. AI models, when trained on
biased historical data, can inadvertently perpetuate discrimination, making it
harder for certain groups, such as individuals with criminal records, to secure
employment. For example, background checks are normally limited to seven years,
but an AI model may contain data extending beyond that timeframe. Without proper
protections in place, candidates may be flagged for offenses that are older than
can legally be considered. This would not only impact individual lives but also
reinforce systemic inequalities.
Beyond legal compliance: Timing and path for adoption of privacy preserving data processings and collaborations for value creation

We are already witnessing notable strides in standardising the movement and
utilisation of financial and healthcare data through innovations in the
Account Aggregator (AA) framework and the Ayushman Bharat Digital Mission
(ABDM) healthcare data exchange. The systematic approach fostered by AA and
ABDM presents an opportune moment to embed privacy at the heart of system
architecture and design. In these ecosystems, Financial Information Users
(FIUs) and Healthcare Information Users (HIUs) are particularly vulnerable to
risks associated with the handling of users and business data. India stands at
a critical juncture, with the potential to revolutionise how data is
circulated through such aggregator systems. While these institutions access
data streams with user consent, there is a risk of falling into the same
conflicts observed in advanced digital economies. The crux of the issue lies
in the intricate relationship between consent, data exploitation, and the
often opaque interpretation of privacy with consent. Addressing this challenge
is essential to avoid replicating the contentious dynamics seen in more mature
digital markets and to pave the way for a more transparent, user-centric data
ecosystem.
The White House Addresses Responsible AI: AI Safety and Data Privacy

Data privacy advocates in the United States have been working toward
comprehensive privacy legislation since the late 1990s. Unlike some other
regions, such as the European Union with its General Data Protection
Regulation (GDPR), the US lacks a single, overarching law to protect
individuals' privacy rights. Right now, over 55 state and federal laws coexist
in the United States, offering various levels of privacy protections. Not only
is it a nightmare for data breach response and notification, but the
inconsistencies do Americans a disservice when it comes to adequately
protecting data privacy as it leaves gaps in protection for individuals whose
data may be handled differently depending on their location. ... The release
of the “Executive Order on the Safe, Secure, and Trustworthy Development and
Use of Artificial Intelligence,” by the Biden administration underscores the
importance of legislation that unifies the existing patchwork of regulations,
enforcement activities, and penalties under one comprehensive law. As the
White House stated in their fact sheet, "AI not only makes it easier to
extract, identify, and exploit personal data, but it also heightens incentives
to do so because companies use data to train AI systems."
Entrepreneurship is a marathon

Every business model requires the Right to Win approach. So, what I look for
in an entrepreneur is, whether he has this Right to Win attitude. What I look
for next is, whether they are long-term entrepreneurs or opportunistic
entrepreneurs. Many people want to be entrepreneurs today for the glamour and
money in entrepreneurship. Entrepreneurship is not a sprint; it is a marathon
with multiple ups and downs. And you should be able to withstand all that. You
need to have the temperament to run a marathon. Remember, in the model that I
follow now is where I don't run the business; the entrepreneurs run it. I
help, I support, but ultimately, they have to run the business. When I looked
for an entrepreneur for Bluestone.com, I had in my mind was one who can
disrupt the traditional jewellery market with technology. You may wonder what
Gaurav Singh Kushwaha, an IIT-Delhi computer science graduate, is doing in
jewellery business when he is not a jeweller. It was his ability to design
jewellery with the aid of computers and deliver exactly the same thing that
attracted me. There is a lot of technology involved in the business.
The Case for ‘Shifting Right’

When we talk about shifting right, it’s not meant to be in place of shift
left when it comes to ensuring secure software. Shifting right comes more
into focus when you think about deployment. The greatest benefit of shifting
right is the ability to see what software will actually look like once
deployed while developers are still shaping and creating it. ... There are a
myriad of issues that aren’t necessarily caught in the earlier stages of
development, meaning that shifting left doesn’t cover everything. CI/CD
code-checking can be performed earlier, but that doesn’t always create a
full fix for problems. Issues often never even manifest until the software
is actually deployed. So, why wouldn’t we check for that too? ... The phrase
“shifting right” sounds innately counterintuitive to the shift-left
mentality all software developers understand at the offset. But in reality,
and in practice, putting these processes together ensures the best possible
security and quality of your software. It’s critical to test early and find
mistakes under real-world conditions. That way you’re ensuring the same high
levels of quality and you’re protected from later issues by understanding
how software looks at the end of the development cycle.
The Need for Secure Cloud Development Environments
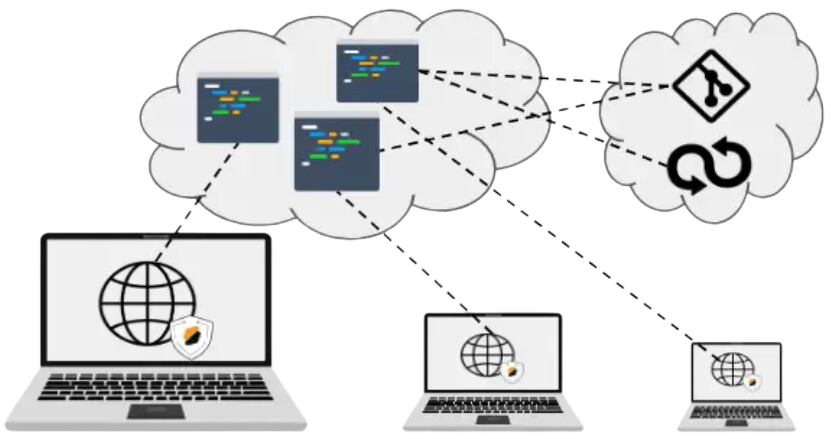
Some of the popular interactive patterns explored by vendors are peer-coding
and the sharing of running applications for review. Peer coding is the
ability to work on the same code at the same time by multiple developers. If
you have used an online text editor such as Google Docs and shared it with
another user for co-editing, peer-coding is the same approach applied to
code development. This allows a user to edit someone else's code in her
environment. When running an application inside a CDE-based coding
environment, it is possible to share the application with any user
immediately. In a classic setting, this will require to pre-emptively deploy
the application to another server, or share a local IP address for the local
device, provided this is possible. This process can be automated with CDEs.
CDEs are delivered using a platform that is typically self-hosted by the
organization in a private cloud or hosted by an online provider. In both
cases, functionalities delivered by these environments are available to the
local devices used to access the service without any installation.
HPE’s corporate emails breached by Russian state-sponsored actor ‘Cozy Bear’

It’s not known if this is part of a coordinated campaign targeting US tech
giants, or if it was separate factions within Midnight Blizzard or Cozy Bear
working on unique missions. “Beginning in late November 2023, the threat
actor used a password spray attack to compromise a legacy non-production
test tenant account and gain a foothold, and then used the account’s
permissions to access a very small percentage of Microsoft corporate email
accounts, including members of our senior leadership team and employees in
our cybersecurity, legal, and other functions, and exfiltrated some emails
and attached documents,” Microsoft said in a blog post disclosing the
attack. Password spraying is a brute-force cyberattack where attackers use a
common password across many accounts to bypass lockout policies. “The recent
Microsoft breach and disclosure brings to the forefront two challenges: no
one is immune (even global organizations) from threat actors, and as an
organization, it will take time to put any fixes in place,” said Ravi
Srinivasan, CEO, of cyber security firm Votiro. “Anytime a threat is
detected, it’s costly and time-consuming to remediate.”
Agent Swarms – an evolutionary leap in intelligent automation

During the rapid evolution of AI, there emerges a concept that promises to
redefine the very essence of automation. Agent Swarms, inspired by the
remarkable collective behaviors of nature’s most efficient creatures, are
poised to revolutionize our approach to complex problem-solving. As AI
accelerates at a breakneck pace, the urgency to harness the potential of
Agent Swarms becomes increasingly apparent. These autonomous software
agents, working collaboratively in a decentralized fashion, are not just a
technological marvel; they are an imperative response to the escalating
complexity of today’s challenges. In a world where healthcare, finance,
urban planning, agriculture, and countless other sectors grapple with ever
more intricate issues, the demand for intelligent automation that can adapt
and excel has never been more pressing. Agent Swarms, with their capacity
for decentralized control and collective intelligence, and their promise of
autonomous decision-making – have emerged as the answer to this urgent call.
We humbly acknowledge our journey as thought leaders and practitioners in
intelligent automation and AI.
Quote for the day:
"Success is nothing more than a few
simple disciplines, practiced every day." -- Jim Rohn
No comments:
Post a Comment