Most cloud-based genAI performance stinks

Generative AI systems often comprise various components. They include data ingestion services, storage, computing, and networking. Architecting these components to work synergistically often leads to overcomplexity, where performance issues, determined by the poorest performing components, are different from isolating. I’ve seen poorly performing networks and saturated databases. Those things are not directly related to generative AI, but they can cause performance problems, nonetheless. ... Protecting AI models and their data against unauthorized access and breaches goes without saying, especially in cloud environments where multitenancy is common. Too many performance issues raise security risks. In many instances, security mechanisms, such as encryption, introduce performance issues that if not resolved will worsen as the data grows. Architecture and testing are your friends here. Take some time to understand how security affects generative AI performance. ... Related to security is adherence to data governance and compliance standards. They can impose additional layers of performance management complexity. Much like security, we need to figure out how to work with these requirements.
Using AI and responsibility for data privacy
If the AI is a self-hosted solution without a connection to application programming interfaces (API) or other data flow to the developer/provider or other third parties, the user is likely to remain solely responsible under data protection law. The fact that the AI provider initially programmed and provided the AI system and determined the technical functionality and the algorithms used by the AI can hardly be sufficient for the AI provider to be held (co-)responsible. It is correct that with the programming the AI provider already specifies the data processing (the means) initiated later by the user, which the user adopts in the context of the subsequent concrete data processing. However, this is the case with all software and therefore cannot be deemed decisive for the role of the controller. If, on the other hand, the AI is a Software-as-a-Service (SaaS) or AI-as-a-Service and the AI provider is still involved in the data processing initiated by the user, the AI provider is at least one potential additional operator in the circle of possible controllers. However, this does not automatically make the AI provider the controller of the data processing carried out by the AI within the meaning of the GDPR.
Transformative technology trends coming to the fore in 2024

Human machine interface (HMI) will transform the way people behave in various
scenarios – this includes how drivers interact with their cars, engineers work
with heavy machinery, laboratory technicians operate in hazardous environments,
and much more. Advanced HMI won’t all be about gesture recognition, however.
Expect to see greater adoption of natural voice interfaces around the world, as
AI enables more native language interactions with virtual assistants and
chatbots. This should finally break the barrier that kept millions (if not
billions) of potential customers away from technologies such as home assistants,
which only operate in a few selected languages. ... We also need to keep a
watchful eye on Gen AI for more nefarious reasons too. There is a high
probability that malicious actors will also co-opt this technology to create
computer viruses – leading to a surge in malware. AI is not the only cyber
security concern, however. We are also seeing major developments in quantum
computing. This could enable hackers to break encryptions that would currently
take years to break, within minutes.
Business privacy obligations hard to understand

Jo Stewart-Rattray, Oceania Ambassador, ISACA said the results are worrying and
are cause for major concern globally, particularly around budget deficits, low
confidence and lack of compliance clarity. “Every organisation in ANZ and across
the world, from SMEs through to enterprise, has a responsibility to protect the
privacy of its customer and stakeholder data, and many governments including
Australia’s Federal government, are updating legislation to ensure best
practice,” said Ms Stewart-Rattray. “It is paramount that organisations
understand what is expected of them in order to devise an effective privacy
policy and implement accordingly. Then will they be able to realise the benefits
of embedding privacy practices in digital transformation from the outset,
including customer loyalty, reputational and financial performance.” ... “When
privacy teams face limited budgets and skills gaps among their workforce, it can
be even more difficult to stay on top of ever evolving and expanding data
privacy regulations and even increase the risk of data breaches,” says Safia
Kazi, ISACA principal, privacy professional practices.
US-based cloud companies may need to reveal client details

The proposed change can restrict the pace of innovation in the Chinese AI
ecosystem as the Chinese AI developers may be subjected to greater scrutiny by
the US Government. “On the other hand, for local alternatives like Baidu ERNIE,
Alibaba Tongyi Qianwen, Tencent Hunyuan, Huawei Pangu, Zhipu GLM, and Baichuan,
this becomes important leverage for them to focus on their innovation despite
the performance gap. It will also force Chinese vendors and enterprises to
further prioritize localization, accelerating the evolution of AI software and
hardware ecosystem in the long run,” said Charlie Dai, Vice President and
Principal Analyst at Forrester. The restrictions may have implications for the
global AI ecosystem as well. “In general, this will cast a shadow over the
global AI ecosystem. Firstly, foreign companies, particularly those from China,
may face greater scrutiny and oversight from the US government. This increased
attention could lead to delays, additional costs, and potential restrictions on
the development and deployment of AI applications,” Dai said. In addition, the
requirement to disclose sensitive information about technology, data usage, and
business operations can raise significant concerns about IP protection.
Great security or great UX? Both, please
A security step-up should be used only for higher-risk scenarios, such as:
anomalous behavior or sensitive actions like purchasing a product, changing
passwords or account information, or inputting financial details into a form.
The average user of a B2B SaaS app should go months without running into a
security step-up. Recognize when they make sense and get rid of those that
don’t. Fewer steps are more secure because users will not become numb to the
situation. In contrast, sparsely used step-ups will be perceived as an
indication of a riskier environment or action that requires more care. Be smart,
as well, about when you have strong enough information not to warrant a step up.
For example, if a user logs in with strong 2FA like a security token and
immediately goes into a sensitive process, a step-up may not be warranted
because the session is short, and the authentication is recent. How you do a
step up, as well, is crucial. First, tell the user why you are asking for
additional information. Second, make it easy for them to follow the process by
explaining precisely what will happen in the step-up and providing visual cues
like breadcrumbs.
Mastering the data science gamble: Strategies for success in a volatile landscape

One of the most significant pitfalls companies face is the blind adoption of
data science merely because it is the industry buzzword. Visionary
implementation should not be about following trends; it should be about
understanding the unique needs of the business and aligning data science
initiatives with strategic goals. Companies need a clear roadmap, a vision
that transcends the charm of technology trends and fads. Without a precise
vision, data science initiatives are equivalent to a ship without a
destination, drifting aimlessly amidst the digital sea. A well-defined
strategy, coupled with risk mitigation techniques, ensures that data science
efforts are not futile ventures but powerful tools driving tangible outcomes.
Moreover, the landscape of data science is ever-changing. Adopting an agile
approach, where hypotheses are tested rapidly, allows for quick iterations and
adjustments. Being nimble in experimentation provides the flexibility to adapt
models in response to evolving market demands. Rapid prototyping and
experimentation allow businesses to fail fast, learn, and refine their
approaches swiftly.
Ransomware’s Impact Could Include Heart Attacks, Strokes & PTSD
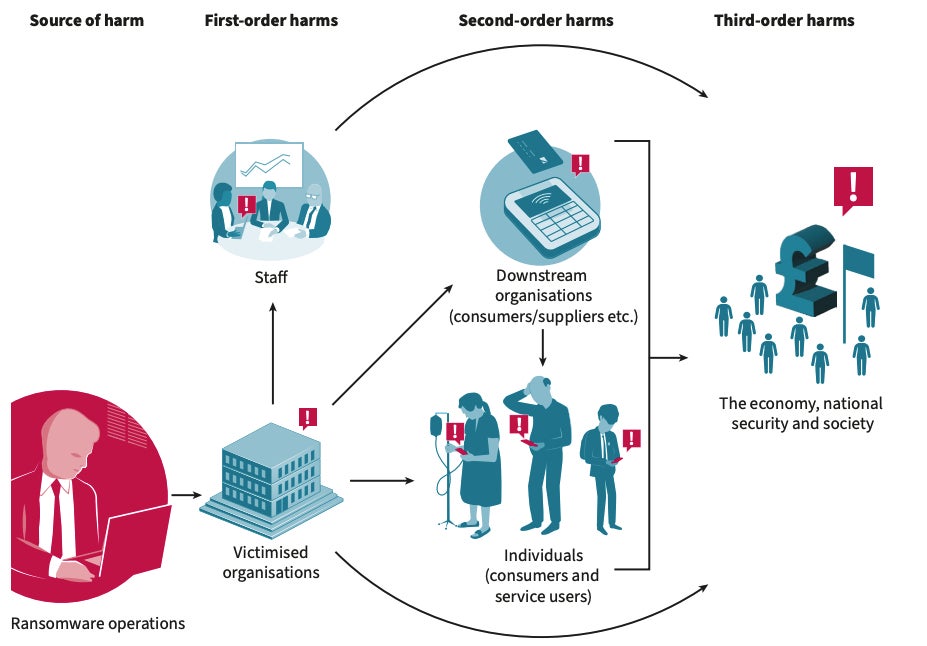
The psychological harm of ransomware attacks on staff is intense and is often
overlooked. Considerable stress for the individuals involved in responding to
ransomware attacks can lead companies to hire a post traumatic stress disorder
support team. Higher levels of employees suffer from stress due to financial
concerns, while middle management suffers from stress caused by extremely long
workdays, including particularly stressful communications with the threat
actor. IT teams are the main victims, as they suffer from extreme workday
conditions and feel a direct responsibility for protecting the organization’s
systems. ... Victims of ransomware attacks rarely share their experiences. In
the best case, companies share an incident response report publicly to help
other organizations improve their defense but also often to show their
customers that they have handled the threat in a responsive way, yet a lot of
organizations stay silent for various reasons: reputational concerns, fear or
legal reasons. ... As stated by the RUSI in the report, “there is a real human
impact to ransomware attacks that is yet to be fully grasped and measured.”
Distributed Applications Need a Consistent Security Posture

With applications and APIs being made available across clouds and on-premises
data centers, a comprehensive approach to security must include an
authentication platform that is flexible and extensible and that functions
with the various clients required to use it. The zero trust security model
framework requires per-application authentication instead of a single
network-level authentication that gives access to all. It doesn’t matter if
you choose a third-party identity provider or go the service provider route,
but it’s important to provide a consistent authentication experience.
Application end users get confused when they encounter different login
experiences across different applications, and this allows attackers to
attempt to capture credentials from unsuspecting employees and customers. Many
developers build the authentication layer into their applications and APIs,
which leads to security posture inconsistencies due to varying skill levels
among developers, lack of standardization and haphazard policy enforcement,
and also increases development time and costs significantly.
We Have Only Begun To Scratch The Surface Of AI’s True Innovative Power
The potential applications that will arise through AI “are vast and can
potentially transform various industries—from healthcare and education to
finance and retail," says Huang. AI-driven applications such as ChatGPT or AI
Copilot "are redefining user access to information, enabling a more efficient
and intuitive experience in place of traditional methods such as web
searching. The advance of multi-modal AI models has created a new paradigm of
opportunities for businesses around context generation and retrieval." It
means there will be new and far more intuitive ways of dealing with computers.
With recent AI progress in large language models, "in addition to voice and
video generation, we will likely see new businesses, focused on providing more
natural and human-centric interactions between humans and machines, sprouting
up," Huang predicts. Business leaders across the spectrum recognize that we
are only starting to recognize what AI — fused with other concepts — can
deliver. “AI can act as a powerful tool for serendipity, connecting disparate
information and fostering unexpected discoveries,” says Bownes.
Quote for the day:
"Leadership is a matter of having
people look at you and gain confidence, seeing how you react. If you're in
control, they're in control." -- Tom Laundry
No comments:
Post a Comment