How human robot collaboration will affect the manufacturing industry
Traditional manufacturing systems frequently struggle to adjust to shifting
demands and product variances. Human-robot collaboration gives flexibility,
which is critical in today’s market. Robots are easily programmed and
reprogrammed, allowing firms to quickly alter production lines to suit new
goods or design changes. This adaptability is critical in an era where
customer preferences shift quickly, and companies are trying to work in line
with the shifting preferences of the customers. ... While the initial
investment in robotics technology may be significant, the long-term cost
savings from human-robot collaboration are attractive. Automated procedures in
the manufacturing industries lower labor costs, boost productivity, and reduce
errors to a great extent, resulting in a more cost-effective manufacturing
operation. ... There is a notion that automation will replace human
occupations, on the contrary, the collaboration is intended to supplement
human abilities. Human workers may focus on critical thinking,
problem-solving, and creativity by automating mundane and physically demanding
jobs.
Mastering System Design: A Comprehensive Guide to System Scaling for Millions
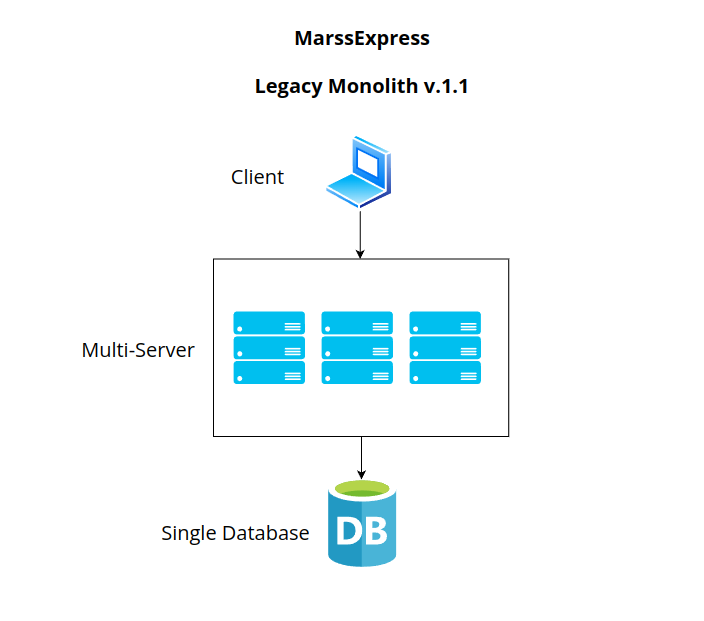
Horizontal scaling emerges as a strategic solution to accommodate increasing
demands and ensure the system’s ability to handle a burgeoning user
base. Horizontal scaling involves adding more servers to the system
and distributing the workload across multiple machines. Unlike vertical
scaling, which involves enhancing the capabilities of a single server,
horizontal scaling focuses on expanding the server infrastructure
horizontally. One of the key advantages of horizontal scaling is its
potential to improve system performance and responsiveness. By distributing
the workload across multiple servers, the overall processing capacity
increases, alleviating performance bottlenecks and enhancing the user
experience. Moreover, horizontal scaling offers improved fault tolerance
and reliability. The redundancy introduced by multiple servers reduces the
risk of a single point of failure. In the event of hardware issues or
maintenance requirements, traffic can be seamlessly redirected to other
available servers, minimizing downtime and ensuring continuous service
availability. Scalability becomes more flexible with horizontal
scaling.
Backup admins must consider GenAI legal issues -- eventually

LLMs requiring a massive amount of data and, by proxy, dipping into nebulous
legal territory is inherent to GenAI services contracts, said Andy Thurai, an
analyst at Constellation Research. Many GenAI vendors are now offering indemnity
or other legal protections for customers. ... "It's a [legal] can of worms
that enterprises can't afford to open," Thurai said. Unfortunately for
enterprise legal teams, the need to create guidance is fast approaching.
Lawsuits by organizations such as the New York Times are looking to take back IP
control and copyright from the OpenAI's proprietary and commercial LLM model.
Those suits are entirely focused on the contents of data itself rather than the
mechanics of backup and storage that backup admins would concern themselves
with, said Mauricio Uribe, chair of the software/IT and electrical practice
groups at law firm Knobbe Martens. The business advantages of GenAI within
backup technology are still unproven and unknown, he added. Risks such as patent
infringement remain a possibility. Backup vendors are implementing GenAI
capabilities such as support chatbots into their tools now, such as Rubrik's
Ruby and Cohesity's Turing AI. But neither incorporates enterprise customer data
or specific customer information, according to both vendors.
CFOs urged to reassess privacy budgets amid rising data privacy concerns
The ISACA Privacy in Practice 2024 survey report reveals that only 34% of
organizations find it easy to understand their privacy obligations. This lack
of clarity can lead to non-compliance and increased risk of data breaches.
Additionally, only 43% of organizations are very or completely confident in
their privacy team’s ability to ensure data privacy and achieve compliance
with new privacy laws and regulations. ... To address the challenges outlined
in the survey, organizations are taking proactive steps to strengthen their
privacy programs. Training plays a crucial role in mitigating workforce gaps
and privacy failures. Half of the respondents (50%) note that they are
training non-privacy staff to move into privacy roles, while 39% are
increasing the usage of contract employees or outside consultants.
Organizations are also investing in privacy awareness training for employees.
According to the survey, 86% of organizations provide privacy awareness
training, with 66% offering training to all employees annually. Moreover, 52%
of respondents provide privacy awareness training to new hires.
Cisco sees headway in quantum networking, but advances are slow

Cisco has said that it envisions quantum data centers that could use classic
LAN models to tie together quantum computers, or a quantum-based network that
transmits quantum bits (qubits) from quantum servers at high-speeds to handle
commercial-grade applications. “Another trend will be the growing importance
of quantum networking which in 4 or 5 years – perhaps more – will enable
quantum computers to communicate and collaborate for more scalable quantum
solutions,” Centoni stated. “Quantum networking will leverage quantum
phenomena such as entanglement and superposition to transmit information.” The
current path for quantum researchers and developers is to continue to grow
radix, expand mesh networking (the ability for network fabrics to support many
more connections per port and higher bandwidth), and create quantum switching
and repeaters, Pandey said. “We want to be able to carry quantum signals over
longer distances, because quantum signals deteriorate rapidly,” he said. “We
definitely want to enable them to handle those signals within a data center
footprint, and that’s technology we will start experimenting on.”
Navigating the Digital Transformation: The Role of IT
While many acknowledged engaging with the six core elements of the Rewired
framework, few participants considered themselves frontrunners in significant
progress. This underscores the complexity and ongoing nature of digital
transformation, necessitating continuous adaptation across leadership,
culture, and technology. Organizations are directing efforts towards both
front-end (customer experience) and back-end (operational optimization),
recognizing the interconnected nature of digital transformation. Success
stories include consolidating Robotic Process Automation (RPE), Artificial
Intelligence (AI), and low-code development within a single organizational
department. This integration facilitates synergies and holistic advancements
in digital capabilities. The evolving nature of ERP transformations was also
discussed, with a shift towards continuous improvements and a focus on
operating models and ways of working, moving beyond purely technological
considerations. The insights from this roundtable underscore the multifaceted
nature of digital transformation.
Harvard Scientists Discover Surprising Hidden Catalyst in Human Brain Evolution

“Brain tissue is metabolically expensive,” said the Human Evolutionary Biology
assistant professor. “It requires a lot of calories to keep it running, and in
most animals, having enough energy just to survive is a constant problem.” For
larger-brained Australopiths to survive, therefore, something must have
changed in their diet. Theories put forward have included changes in what
these human ancestors consumed or, most popularly, that the discovery of
cooking allowed them to garner more usable calories from whatever they ate.
... The shift was probably a happy accident. “This was not necessarily an
intentional endeavor,” Hecht posited. “It may have been an accidental side
effect of caching food. And maybe, over time, traditions or superstitions
could have led to practices that promoted fermentation or made fermentation
more stable or more reliable.” This hypothesis is supported by the fact that
the human large intestine is proportionally smaller than that of other
primates, suggesting that we adapted to food that was already broken down by
the chemical process of fermentation.
Digital Personal Data Protection Act marks a new era of business-friendly governance

Surprising the business community, the DPDP Act 2023 removed the data
localization requirements, marking a significant departure from the previous
iterations of the Act. The earlier DPDP Bills required certain categories of
personal data to be stored and processed within the country. The provision
faced staunch global opposition, particularly from the US, which criticized
India's requirements as discriminatory and trade distortive. In contrast, the
DPDP Act, 2023 adopts a more inclusive approach, granting firms autonomy in
the choice and location of cloud services for storing and processing personal
data of their users. By prioritizing cost-effectiveness and competitiveness
for the firms, the removal of data localisation requirements signals a more
accommodating government stance. In addition to scrapping data localization
requirements, the DPDP Act 2023 also allows unrestricted cross-border transfer
of Indian users’ personal data abroad, barring certain destination countries.
Firms would not be required to conduct post-transfer impact assessments or to
ensure that the destination country has similar data protection standards–
mandated in other jurisdictions like the EU and Vietnam.
Cybersecurity: The growing partnership between HR and risk management

HR professionals themselves can also be attractive targets to bad actors. The
access they have to sensitive employee and company data can be a goldmine for
hackers, putting a target on the back of those within the HR organization. As
such, HR leaders should put proactive, pre-breach policies in place for their
own functional colleagues. Policies might include contacting internal and
external parties who ask for changes to sensitive information, such as invoice
numbers, email passwords, direct deposit details, and software updates. They
should also include policies for remote workers and incidence response. ...
When you purchase cyber insurance, you get access to pre-breach planning and
policy templates, which for many organizations, is just as important as the
breach coverage. While the optimal amount of insurance depends on many factors
— including size, revenues, number of employees and access to confidential
information — HR organizations of all sizes and structures benefit from
pre-breach planning and policymaking.
IT services spending signals major role change for CIOs ahead

“This evolution in what CIOs do, the value proposition they bring to the
company, is evident in the long-term playout. But it is not yet as evident to
the CIOs themselves,” Lovelock said. He sees CIOs still thinking they are
riding the same talent waves of the past, facing a temporary problem that they
will solve: that their staff will come back, that hiring will resume, that
attrition rates will decline, and that they will be able to attract the skills
they need at prices they can afford. “It doesn’t look like they will ever be
able to do that. There are too many things IT staff with these key resources
and skills are looking for that are outside of the CIO’s control to deliver,”
he said. With increasing reliance on IT services and consulting to deliver
outcomes ranging from commoditized customer support to differentiating
generative AI implementations, the CIO role may soon become less about being
that one-stop shop for business support, overseeing project and products
developed in-house, and more about weaving together myriad services undertaken
by an increasingly heterogeneous mix of talent sources, predominantly beyond
the CIO’s direct purview.
Quote for the day:
''Thinking is easy acting is
difficult, and to put one's thoughts into action is the most difficult thing
in the world.'' -- Johann Wolfgang von Goethe
No comments:
Post a Comment