4 ways to make monolithic enterprise apps feel cloud-native

Fortunately, all hope is not lost if you have an enterprise app you can't
containerize or "microservices-ize." Even if you can't "break down your
monolith"—to quote the standard advice about how to modernize legacy apps—there
are many practical steps you can take to make legacy, monolithic applications
look and feel (in most respects) like modern, cloud-native apps. ... Most
enterprise apps are compatible with the cloud in the sense that you can host
them on cloud-based virtual machine (VM) instances using services from different
cloud providers. By taking advantage of cloud hosting for enterprise apps,
organizations can also leverage cloud automation tools, such as autoscaling
policies and rules that automatically start or stop VMs. Deploying enterprise
apps in a highly scalable, automated manner becomes possible. ... Although
configuring load balancers for enterprise apps hosted in the cloud is not a
strict requirement, doing so can substantially improve application performance
and reliability. Load balancers help direct requests at application instances
best able to handle them.
What is Event Sourcing Design Pattern in Microservice Architecture? How does it work?
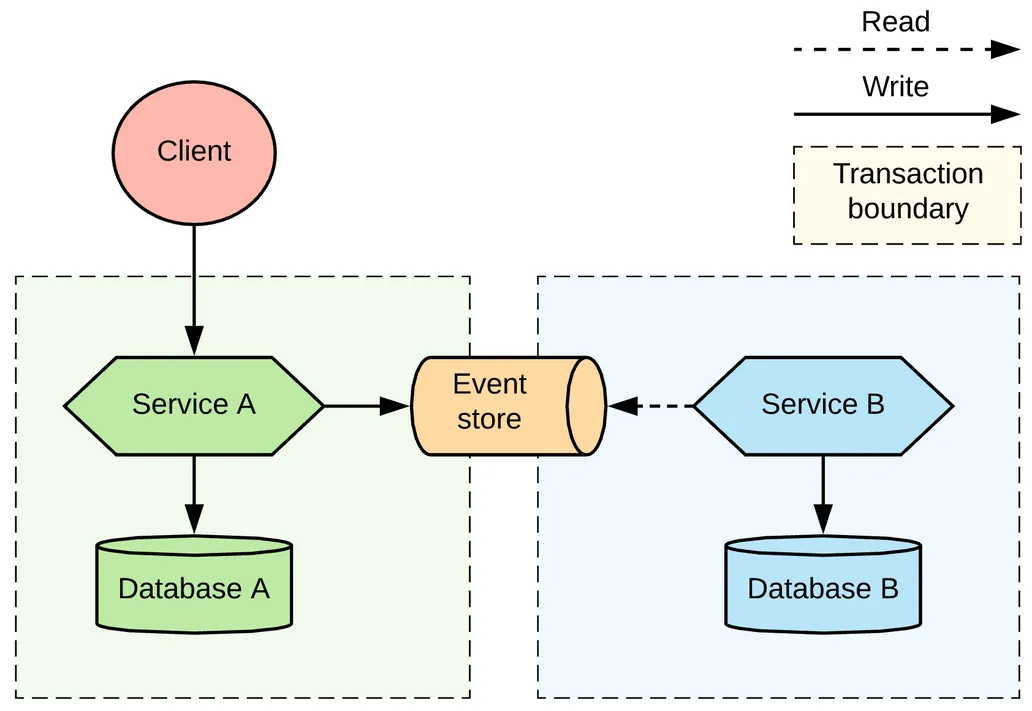
Event sourcing is a design pattern that stores the state of an application as a
sequence of events in the order that they occurred, rather than simply storing
the current state of the application. In microservice architecture, this pattern
can help in achieving better scalability, fault tolerance, and resilience.
Here’s how it works:An event is generated whenever a change occurs in the
system. The event is persisted to an event store, which is essentially a
log of all events that have occurred in the system. The current state of
the system can be reconstructed at any time by replaying all of the events in
the event store, in the order that they occurred. Each service in the
microservice architecture can have its own event store, which can be used to
maintain its own state. Services can subscribe to events that are relevant to
them and update their own state accordingly. By using event sourcing, it is
possible to achieve better fault tolerance and resilience.
Why Cloud Data Replication Matters

There are many reasons for building applications that understand replication,
with or without cloud support. These are basic topics that any developer has
had to deal with, but they are even more important when applications go global
and/or mobile. Then they need ways to keep data secure and located
efficiently. ... As you can see, data replication does not explicitly depend
on using cloud resources. Enterprises have been using their internal networks
for decades with some of the same benefits. But with the addition of
cloud-based resources, the opportunity to have extremely high availability and
performance is easier than ever. Traditional data replication has now been
extended beyond just replicating from a PC to a network or between two
servers. Instead, applications can replicate to a global network of endpoints
that serve multiple purposes. Traditionally, replication was used to preserve
data in case of a failure. For example, replicas could be copied to a node if
there was a failure, but replicas could not be used directly by an
application.
Composable Architecture - Part 1
Composable architecture refers to an architectural pattern that allows for the
creation of systems made up of small, independent, and interchangeable
components. These components can be developed and deployed independently and
can be combined together to create new applications or features. In this way,
composable architecture is similar to the concept of microservices, where a
system is broken down into small, self-contained units that can be managed and
developed independently. Today, using Module Federation, it is possible to go
beyond micro services and enable independent product squats to build robust
micro applications that can be composed into a seamless functionality for both
retail and corporate banking clients. ... By using micro frontends, banks can
break down their front-end application into smaller, independent components
that can be developed and deployed independently. This allows product squads
to work independently and develop micro apps that can be composed together on
the front end to make it seamless for the banking customer.
How to Become an Enterprise Architect

An enterprise architect must effectively serve as a central nervous system of
the business, making sure its various organs operate in a greater harmony –
even when these local channels are out of communication with each other. As
you might expect, this almost always comes down to a continuous stream of
meetings that scale anywhere from big-picture issues like roadmap orientation
and long-term strategies to more nuts-and-bolts implementation and putting out
fires. ... While the broad skill set and think-outside-the-box mindset
entailed in the job allows for some degree of flexibility, recruiters for
potential enterprise architects typically look for an undergraduate degree in
computer science or related discipline. Enterprise architects with a master’s
degree will have even more solid prospects. Job candidates are expected to
have a minimum of five years in the IT field – preferably a decade or more.
... As enterprise architects continue to become more sought after, an aspiring
professional will benefit from a resume with certification in skills that
custom-fit the position in question.
Tracking the Evolving Cybersecurity Jobs Landscape for 2023
For someone who is looking to start out in cybersecurity, a direct admit role
to security is rare, especially as it bypasses the potential growth and
opportunities to learn from other positions. Combs recommends finding a path
through systems administration or another foundational area that provides
contextual information to build on. “You can’t protect an entity if you don’t
understand the systems that comprise the entity,” he says. Even as
professionals become more experienced in cybersecurity, they must remain
committed to their specialization with or without constant acknowledgment of
their success. ... “On your best day, nothing happened. And then on your worst
day, one shift where something happened, everybody’s like, ‘Why did you let
this happen?’ But you’re like, ‘Nothing happened all those other days!’” With
more open-source learning and professional development resources available
than ever, Combs advises up-and-coming professionals to take advantage of all
of them, but advises against bootcamps that make assertions of guaranteed
employment.
Cybersecurity experts argue that pausing GPT-4 development is pointless

Despite concerns about the societal risks posed by generative AI, many
cybersecurity experts are doubtful that a pause in AI development would help
at all. Instead, they argue that such a pause would provide only a temporary
reprieve for security teams to develop their defenses and prepare to respond
to an increase in social engineering, phishing and malicious code generation.
... “We need a new class of AI trust, risk and security management [TRiSM]
tools that manage data and process flows between users and companies hosting
LLM foundation models. These would be [cloud access security broker] CASB-like
in their technical configurations but, unlike CASB functions, they would be
trained on mitigating the risks and increasing the trust in using cloud-based
foundation AI models,” Litan said. As part of an AI TRiSM architecture, users
should expect the vendors hosting or providing these models to provide them
with the tools to detect data and content anomalies, alongside additional data
protection and privacy assurance capabilities, such as masking.
Overcoming obstacles to introduce zero-trust security in established systems
Even small and midsize enterprises have undergone significant changes in
recent years. To become more flexible, they embraced trends like remote work,
BYOD, decentralized IT, and moved their operations to the cloud. It is not an
exception that a business has no private network but naturally still has
systems, apps, data and employees that need protection from still growing
online threats. When balancing the security of this new reality with the needs
of remote workforce, it is not only about the technology, which should be easy
to use, reliable and not disturbing to the user, but also about employee
education. Employees should be trained in new policies so that they don’t
resist the new security procedures, but actively contribute to them. To give
an example, multifactor authentication should not be seen as a nuisance but a
standard part of logging in and second nature to all employees. Regular
phishing drills should be conducted to train workers in spotting and reporting
them.
Tech Titans: The crossroads of humanity and technology

“You cannot escape technology – tech is intertwined no matter what we do; it
has become a utility like water, heat, and electricity. Not having access to
technology can be detrimental to having access to the essentials of daily
life. We need to work together to ensure that everyone – especially the
underserved and disenfranchised communities – have access to technology.” ...
But technology by itself is not the only deterrent, Hannah noted. Even if
technology is available, the cost could be a challenge in such communities –
especially when for those who struggle to provide necessities like food.
Literacy in these communities is another key challenge. Pegues characterizes
digital redlining as a socio-economic problem at the crossroads of humanity
and technology, which triggered a question about technology’s ability to
combat digital redlining. While acknowledging that “old habits are hard to
break,” Pegues also called out the possibility of detecting and addressing the
algorithms that advance this practice.
Why AI Could be Critical in Reducing the Court Backlog
Today, nearly every criminal investigation includes a substantial digital
evidence component, whether that be texts, WhatsApp messages, emails, internet
browser histories, or data from GPS devices and fitness trackers. Research
conducted by the University of Exeter in conjunction with the UK police force,
found that digital forensics are now used in over 90% of criminal cases. But
our ever-growing digital footprint presents a significant challenge for
criminal defence lawyers who now need to review unprecedented volumes of data
ahead of trial. Legal teams that fail to thoroughly analyse all this
information are at risk of not meeting evidentiary thresholds, as in the case
of Liam Allan, where 40,000 text messages were omitted from evidence and
caused the case to fall apart at the last minute. The pandemic may have
prompted the UK courts to revise traditional methods of working and embrace
new technology, such as video conferencing software for remote trials, but
there is still much work to be done.
Quote for the day:
"A leader or a man of action in a
crisis almost always acts subconsciously and then thinks of the reasons for
his action." -- Jawaharlal Nehru
No comments:
Post a Comment