In the shift to hybrid work, don’t overlook your in-person workforce

As companies think through their workforce strategies, taking a few critical steps can help. First, make sure that the in-person cohort receives the same amount of consideration as remote and hybrid workers. New ways of working clearly pose challenges in terms of productivity, but there is a real risk in senior leaders focusing most of their time and attention on remote-work issues. Second, measure employee sentiment, over time, to understand which factors are successful in boosting engagement and morale among the in-person workforce, and where the organization can improve. Third, look for ways to increase the autonomy of in-person workers. Encourage them to make suggestions about how their work can be done better, and empower them to act on those suggestions. Create some degree of flexibility in terms of scheduling. For example, enable workers to have more say in setting schedules, and allow workers to trade shifts. Fourth, invest in upskilling initiatives; they are a key driver of empowerment and engagement.
Caught in the crossfire of cyber conflict
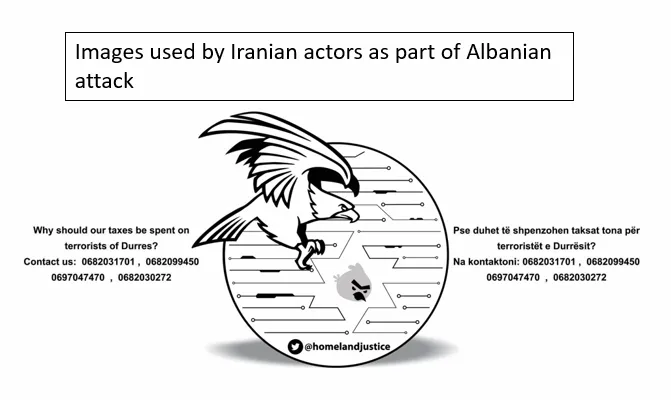
Cyber events are now routinely crossing thresholds that would have been viewed
as increasingly risky 20 years ago. The result is that offensive cyber
operations are now manageable for countries such as the US but are now
catastrophic for smaller countries that are thrust into the cyber conflict
space. The potential scale of this effect likely makes smaller countries ideal
targets for sophisticated actors looking to demonstrate their capabilities.
Iran appears to have stronger evidence on Israel’s role in the ‘Predatory
Sparrow’ campaign (the two countries have been exchanging attacks for years)
but opted to attack Albania’s government for harbouring the MeK—using the
disruptive incident to send a message to Iran’s enemies. This incident is
chilling because it shows the spread of sophisticated cyber capabilities, and
the growing intent to conduct such operations. Most theories around cyber
conflict have kept the US as a key player in such conflicts—‘Predatory
Sparrow’ and Iran’s response have shown that this is outdated.
How DevOps Practices will Expedite AI Adoption?

Although AI has developed and revolutionized many corporate processes, there
are still obstacles to overcome because it necessitates a lot of human labor.
Getting a dataset, training it, cleaning it, and making predictions appear
increasingly tricky. A different problem is creating a fluid generalized
training pattern or transferring a specific approach from one situation to
another. Businesses could adapt their operational procedures to achieve more
noticeable outcomes, such as the DevOps culture, which results in practical
development, deployment, and operation pipeline. ... DevOps and IT teams must
work closely to achieve this; as a result, a central repository for model
artifacts is required, and ML engineers must redesign the production model.
Thus, a smooth collaboration between the IT, DevOps, and data scientists teams
is crucial. MLOps, or machine learning operations, is a different way of
describing the confluence of people, processes, practices, and underlying
technology that automate the implementation, monitoring, and management of
AI/ML models in production in a scalable and thoroughly controlled manner.
India: Crucial cyberwarfare capabilities need to be upgraded
The world has seen many cases of cyber-attacks in espionage and sabotage. Many
significant cyberattacks in the military and civil spaces have occurred in
recent months. APT41, a Chinese state-sponsored hacking group, allegedly
hacked into six US state governments between May 2021 to February 2022.
Another Distributed Denial of Service (DDoS) attack in the preceding month was
the cyber-attack on Israeli government websites. While the government has said
this was the cyber-attack Israel has faced, investigations are yet to
determine the source of the attack. Similarly, a targeted cyber-attack
campaign on Russian research institutes was discovered in June 2021. The
target was research institutes under the Rostec Corporation, whose primary
expertise is the research and development of highly technological defence
solutions. In India, researchers detected a new ransomware that made its
victims donate money to the needy. However, this ransomware, called Goodwill,
also acts maliciously by causing temporary or even permanent loss of company
data and the possible closure of a company’s operations and finances.
The API gateway pattern versus the Direct client-to-microservice communication
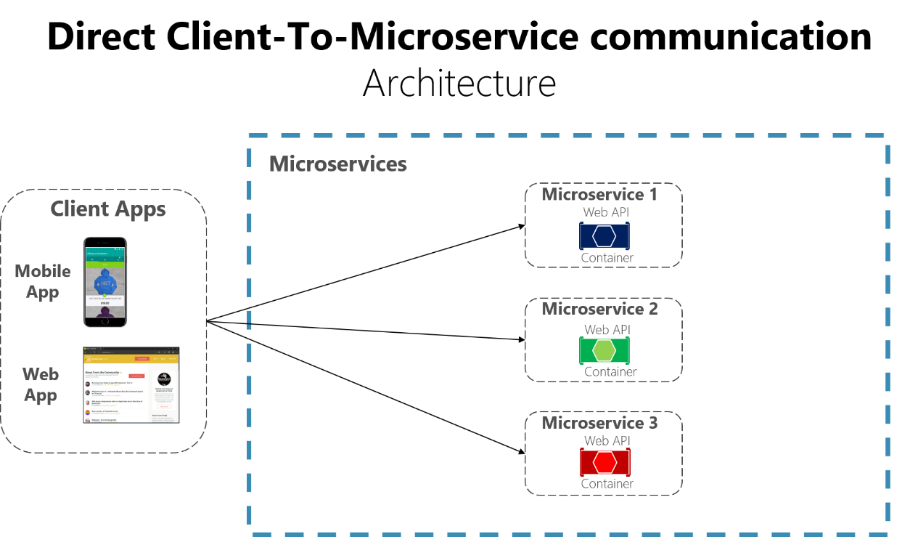
In a microservices architecture, the client apps usually need to consume
functionality from more than one microservice. If that consumption is
performed directly, the client needs to handle multiple calls to microservice
endpoints. What happens when the application evolves and new microservices are
introduced or existing microservices are updated? If your application has many
microservices, handling so many endpoints from the client apps can be a
nightmare. Since the client app would be coupled to those internal endpoints,
evolving the microservices in the future can cause high impact for the client
apps. ... When you design and build large or complex microservice-based
applications with multiple client apps, a good approach to consider can be an
API Gateway. This pattern is a service that provides a single-entry point for
certain groups of microservices. It's similar to the Facade pattern from
object-oriented design, but in this case, it's part of a distributed system.
The API Gateway pattern is also sometimes known as the "backend for frontend"
(BFF) because you build it while thinking about the needs of the client
app.
Why Choose a NoSQL Database? There Are Many Great Reasons

Speed is critical to innovation, but so is flexibility. A core principle of
agile development is responding quickly to change. Often when the requirements
change, the data model also needs to change. With relational databases,
developers often have to formally request a “schema change” from the database
administrators. This slows down or stops development. By comparison, a NoSQL
document database fully supports agile development because it is schema-less
and does not statically define how the data must be modeled. Instead, it
defers to the applications and services, and thus to the developers as to how
data should be modeled. With NoSQL, the data model is defined by the
application model. Applications and services model data as objects (such as
employee profile), multivalued data as arrays (roles) and related data as
nested objects or arrays (for instance, manager relationship). Relational
databases, however, model data as tables of rows and columns — related data as
rows within different tables, multivalued data as rows within the same
table.
Securing the Internet of Things

Unlike humans, who need to be able to access a potentially unbounded number of
destinations (websites), the endpoints that an IoT device needs to speak to
are typically far more bounded. But in practice, there are often few controls
in place (or available) to ensure that a device only speaks to your API
backend, your storage bucket, and/or your telemetry endpoint. Our Zero Trust
platform, however, has a solution for this: Cloudflare Gateway. You can create
DNS, network or HTTP policies, and allow or deny traffic based not only on the
source or destination, but on richer identity- and location- based controls.
It seemed obvious that we could bring these same capabilities to IoT devices,
and allow developers to better restrict and control what endpoints their
devices talk to (so they don’t become part of a botnet). ... Security
continues to be a concern: if your device needs to talk to external APIs, you
have to ensure you have explicitly scoped the credentials they use to avoid
them being pulled from the device and used in a way you don’t expect.
Modern Enterprise Data Architecture
In traditional architecture development, data modeling is the simple task of
deriving data elements from requirements, depicting the relation between the
entities through entity relationship (ER) diagrams, and defining the
parameters (data types, constraints, validations) around the data elements.
This means that data modeling is done as a single-step activity in a
traditional architecture by defining the data definition language (DDL)
scripts from requirements. ... A database acts as the brain for an IT
application because it serves as the central store for data being transacted
and referenced in the application. Database administrators (DBAs) handle
database tuning, security activities, backup, DR activities, server/platform
updates, health checks, and all other management and monitoring activities of
databases. When you use a cloud platform for application and database
development, the aforementioned activities are critical for better security,
performance, and cost efficiency.
Data privacy can give businesses a competitive advantage

It is a similar story of a competitive edge waiting to be revealed through
compliance when it comes to protecting personal data. The fines that
non-compliance brings are perhaps one of the most-reported aspects of the new
regulation. Serious breaches can cost a company €20m, or 4 per cent of global
annual revenue per offence, but the Information Commissioner’s Office (ICO)
has been very clear it has no intention to scapegoat businesses using these
powers. The GDPR is very clear that data has to be held and processed securely
and though the law does not outline how, Article 32 provides a clear
prescription for what is expected. The ICO’s advice is that processing the
minimum amount of personally identifiable information possible is a good
start. Then, storing it securely and in an encrypted form makes sense. In
certain circumstances, anonymising data so it can collectively provide insight
without revealing identities is another tactic many organisations are using.
Securing data so it cannot be hacked is a worthy end in its own
right.
7 Metrics to Measure the Effectiveness of Your Security Operations

The main objective of a resilient security operations program should be
lowering an organization's MTTD and MTTR to limit any damage done by a cyber
incident to your organization. MTTD measures the amount of time it takes to
discover a potential security threat. This metric helps you understand the
effectiveness of your organization's security operations and your team's speed
and ability to recognize a threat. Therefore, the goal is to keep this metric
as low as possible in order to reduce the impact of a compromise on your
organization. Meanwhile, MTTR helps you measure the time it takes to respond
to a threat once it is detected. A higher response time indicates that a
compromise could lead to a damaging data breach. The goal is to speed up your
response and decrease your risk, just like MTTD. Both MTTD and MTTR are key
metrics to measure and improve your team's capabilities since it is crucial to
track the effectiveness of your team as your organization's maturity grows.
Like any fundamental business operation, to mature your organization you
should measure operational effectiveness to determine whether your
organization is reaching its KPIs and SLAs.
Quote for the day:
"Leadership is the art of giving
people a platform for spreading ideas that work" -- Seth Godin
No comments:
Post a Comment