10 mistakes rookie CIOs make — and how to avoid them

Most CIOs have likely heard that “culture eats strategy for breakfast,” the famous quote from management guru Peter Drucker. But rookie CIOs don’t often take that message to heart, according to both researchers and experienced CIOs. “One of the rookie mistakes is not truly understanding your business, culture, and organizational fabric,” says Richard A. Hook, executive vice president and CIO of Penske Automotive Group and CIO of Penske. “Everyone is focused on their 100-day plan, but the reality is the pace of that plan and composite will vary between organizations. Get to know your peers, their teams, your team, and the overall organization before taking a too-aggressive approach. In the end, organizations win with the best people, be sure you know your teams and deeply understand the business before acting too harshly.” Jackson agrees, saying new executives should assess their department’s culture and the organization’s overall culture early on. This, he explains, lets leaders know how to adjust and change so they can be most effective moving forward.
EU Cyber Resilience Act sets global standard for connected products

The EC said the new rules would rebalance security responsibility towards
manufacturers who will be made to ensure they conform to the new requirements,
ultimately benefiting end-users across the EU by enhancing transparency,
promoting trust, and ensuring better protection of basic rights to privacy. The
EC acknowledged the act is likely to become an international point of reference
beyond the EU’s internal market, and Keiron Holyome, BlackBerry vice-president
for the UK and Ireland, Eastern Europe, Middle East and Africa agreed with this
view. “Today, as the EU launches its Cyber Resilience Act to protect European
consumers and businesses from the risks caused by insecure digital products, the
UK must sit up and take notice. This act should not be viewed as a European
requirement, but in fact a new global standard,” said Holyome. “The EU’s new act
further highlights that British organisations must take action, particularly
when it comes to the use of potentially insecure smart devices for home working.
... Although smart devices may seem innocent, bad actors can easily access home
networks with connections to company devices – or company data on consumer
devices – and steal intellectual property worth millions.
Hybrid workers don't want to return to the office. But soon, they might have to

No doubt many leaders will be paying attention to how major tech companies are
reacting to the situation. Apple, for instance, has laid off a number of
recruiters and plans to curb hiring next year to help it weather an uncertain
economic climate. Meta, Microsoft and Google have also announced plans to slow
hiring, and all four tech giants have made moves to get their workers into the
office on a more regular basis in recent months. Asking employees to return to
the office as a reaction to financial uncertainty feels more like a return to
what feels familiar than a practicable way of overcoming the challenges ahead.
While doing so might help leaders regain a sense of control and run the business
as a much tighter ship, it's not necessarily going to help improve productivity
or engagement. ONS data suggests that 78% of employees who work from home in
some capacity report a better work-life balance, and taking this away will not
win employers any favours. Workers might also choose to return to the office if
working from home gets significantly more expensive.
When openness doesn’t matter

“Open is better…unless it isn’t,” notes software exec James Urquhart, who has
done his share of work with open source companies. The key to figuring out the
“isn’t” in a particular case is to look at the practical effects of a given
strategy. Lightbend and Akka founder Jonas Bonér stressed that the company’s
decision to change the Akka license was because the current model simply wasn’t
sustainable. He says, “With Akka now considered critical infrastructure for many
large organizations, the Apache 2.0 model becomes increasingly risky when a
small company solely carries the maintenance effort.” To prod these large
organizations to pay for their use of Akka, the company turned to the BSL 1.1 as
“a form of productive and sustainable open source” that is “easy to understand,
provides clear rules, and is enforceable.” Not everyone will like it. Some of
the more vocal members of the open source Illuminati have castigated Lightbend
for this decision. But rather than criticize, why not simply observe? If it’s
truly a bad strategy, it will fail, and both Lightbend and other companies will
learn from that failure, and there will be less re-licensing with licenses that
are perceived to be less open.
Hacker Accessed LastPass Internal System for 4 Days

The breach investigation was carried out in partnership with cybersecurity firm
Mandiant and uncovered that the threat actor's activity was limited to a
four-day period until the incident was contained. Further investigation from
LastPass and Mandiant determined that the threat actors gained access to the
development environment using a developer's compromised endpoint. "While the
method used for the initial endpoint compromise is inconclusive, the threat
actor utilized their persistent access to impersonate the developer once the
developer had successfully authenticated using multifactor authentication,"
Toubba says. Toubba acknowledges that the threat actor was able to access the
development environment but failed to access any customer data or encrypted
password vaults. Toubba also says that the LastPass development environment is
physically separated from other environments, including the production area, and
has no customer data or encrypted vaults. The notification also says that the
company does not have access to the master passwords used by the customers, and
without having the master password, no one can decrypt vault data as part of the
company's "zero-knowledge security model."
Double-transmon coupler will realize faster, more accurate superconducting quantum computers
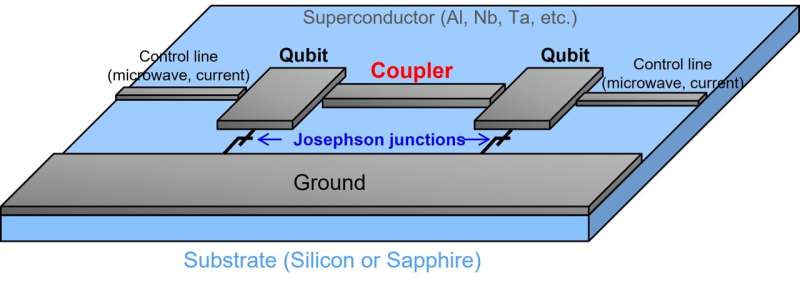
Toshiba has recently devised a double-transmon coupler that can completely
turn on and off the coupling between qubits with significantly different
frequencies. Completely turning on enables high-speed quantum computations
with strong coupling, while completely turning off eliminates residual
coupling, which improves quantum computation speeds and accuracy. Simulations
with the new technology have shown it realizes two-qubit gates, basic
operations in quantum computation, with an accuracy of 99.99% and a processing
time of only 24 ns. Toshiba's double-transmon coupler can be applied to
fixed-frequency transmon qubits, realizing high stability and ease of design.
It is the first to realize coupling between fixed-frequency transmon qubits
with significantly different frequencies that can be completely switched on
and off, and to deliver a high-speed, accurate two-qubit gate. The technology
is expected to advance the realization of higher-performance quantum computers
that will contribute in such areas as the achievement of carbon neutrality and
the development of new drugs.
Automation Gains a Foothold, But How to Scale It Is the Challenge

“Going forward, automation should be the focus at each business group and
department – it must be a mandatory part of business planning,” he explains.
Each C-level executive should provide a plan of how much automation each
quarter/year they plan to implement to reduce the number of resources their
division needs. They should also come up with tangible KPIs that will impact
cost reduction and generate savings for sustained growth. Butterfield says
this focus must come from the board as a priority item, enabled through
technology and implemented by all. “AI and automation are as much a capability
as a technology – therefore, even if someone is taking responsibility, the
organization will only be successful if everyone is aligned,” he says. Freund
says that while automation involves a broad set of stakeholders across both
business and IT, it’s not always easy to get them all on the same page.
Depending on the organization, a technical leader like an enterprise architect
might spearhead the automation process by kicking off a proof of concept
(PoC), organizing a team to execute it, and presenting the results to business
stakeholders.
Computational Aesthetics in Robotics Design and Automation
Robotic informatics studies how robots interact with their surroundings and
how this affects the aesthetics of their design. It considers such questions
as how to create visually appealing robots and how to ensure that they behave
in an aesthetically pleasing way. Though research is still ongoing in this
area, there are already some promising results. For example, a study shows
that people respond more favorably to visually engaging robots with
well-designed features. That may help increase efficiency and productivity in
the industry while creating a more positive image for robotics technology. One
of the main ways computational aesthetics impacts robotics programming is by
providing new methods for designing and improving robots. Such new methods are
artificial intelligence (AI), machine learning (ML), and deep learning (DL).
All these methods involve teaching computers to do things that were once
impossible for them. ML, in particular, is a form of AI that allows computers
to learn from experience and improve their performance over time based on this
experience. DL is similar to ML.
6 tips for successfully leading software developers

Developers’ will to create is strong, but it can be hard to perceive as
creativity is often obscured by the technological nature of development.
Developers communicate with a strange patois of acronyms that hide the
artistic spirit behind it. Learning to perceive and nurture that spirit is a
special kind of leadership that developers will appreciate. Just the awareness
of the creative life of developers is important. Not only will it help to
understand where they are coming from, but it will lead to policies and
decisions that support that creativity and out of that will come real
bottom-line benefit. The space and time to innovate will lead to better
software that handles the vicissitudes of business. You need the human
creativity of your developers captured in the half-machine/half-thought medium
of code to be agile. Perhaps the most important feature for the leader to bear
in mind here is in realizing the attachment that developers have to their
work. Affection might be a better word than attachment. Building a thing that
feels beautiful and worthy in itself has its own momentum.
Are we experiencing cloudflation?

Many critics cite the lack of a sound cloud finops program to monitor, track,
and govern costs. The rudimentary problem right now is that companies have
little or no insight into any cloud costs before they get the bill. In other
words, if having a finops program scores a 9 out of 10 in terms of cloud cost
management maturity, these companies are still at a 1 or 2. This state exists
because most enterprises did not see cloud coming—or coming as rapidly as it
did due to the pandemic. As a result, they did not allocate budget and
resources to manage cloud costs: the hard costs such as cloud computing bills
for services, as well as soft costs such as the many expensive humans now
needed to keep cloud-based systems running. Here’s the good news: Implementing
even a rudimentary finops strategy with cloud cost monitoring and controls
will quickly pay for itself. Moreover, it will do so without diminishing cloud
services. It accomplishes noninvasive cost savings partly by implementing
basic housekeeping tasks, such as shutting down unused instances where the
meter is still running or optimizing the use of cloud resources that lack
current cost management, with options to automate as deeply as desired or
required.
Quote for the day:
"Hold yourself responsible for a
higher standard than anybody expects of you. Never excuse yourself." --
Henry Ward Beecher
No comments:
Post a Comment