A vision for making open source more equitable and secure

There have been multiple attempts at providing incentive structures, typically
involving sponsorship and bounty systems. Sponsorship makes it possible for
consumers of open source software to donate to the projects they favor. Only
projects at the top of the tower are typically known and receive sponsorship.
This biased selection leads to an imbalance: Foundational bricks that hold up
the tower attract few donations, while favorites receive more than they need. In
contrast, tea will give package maintainers the opportunity to publish their
releases to a decentralized registry powered by a Byzantine fault-tolerant
blockchain to eliminate single sources of failure, provide immutable releases,
and allow communities to govern their regions of the open-source ecosystem,
independent of external agendas. Because of the package manager’s unique
position in the developer tool stack—it knows all layers of the tower—it can
enable automated and precise value distribution based on actual real-world
usage.
Cognitive Overload: The hidden cybersecurity threat

Cognitive overload occurs when workers are trying to take in too much
information or execute too many tasks. This typically falls under two areas for
cybersecurity analysts: intrinsic load, the piecing together of complex
technical information to perform incident response activities; and extraneous
load, the other 97% of data in a SIEM that they must filter out, while also
handling team conversations and sidebar questions. Ultimately, cognitive
overload leads to poor performance levels, a lack of focus, and a lack of
fulfillment. This can have particularly detrimental consequences within
cybersecurity, where ransomware attacks rose 13% year-over-year – more than the
past five years combined. To boot, just under half of senior cyber professionals
(45%) have considered quitting the industry altogether because of stress. To
accommodate the needs of this critical workforce – and fill the 771,000 cyber
positions open today – companies must make easing cognitive overload a top
priority. Today, it stems from two major issues. First, organizations typically
lack direction in cybersecurity, tasking analysts with a broad and daunting:
defend our infrastructure. It’s too abstract and leaves them unsure of their
roles and responsibilities.
Medical device vulnerability could let hackers steal Wi-Fi credentials

A vulnerability found in an interaction between a Wi-Fi-enabled battery system
and an infusion pump for the delivery of medication could provide bad actors
with a method for stealing access to Wi-Fi networks used by healthcare
organizations, according to Boston-based security firm Rapid7. The most serious
issue involves Baxter International’s SIGMA Spectrum infusion pump and its
associated Wi-Fi battery system, Rapid7 reported this week. The attack requires
physical access to the infusion pump. The root of the problem is that the
Spectrum battery units store Wi-Fi credential information on the device in
non-volatile memory, which means that a bad actor could simply purchase a
battery unit, connect it to the infusion pump, and quicky turn it on and off
again to force the infusion pump to write Wi-Fi credentials to the battery’s
memory. Rapid7 added that the vulnerability carries the additional risk that
discarded or resold batteries could also be acquired in order to harvest Wi-Fi
credentials from the original organization, if that organization hadn’t been
careful about wiping the batteries down before getting rid of them.
Four Action Steps for Shoring Up OT Cybersecurity

Having proactive safeguards in place is important, but it’s also critical to
have effective reactive procedures ready to respond to intrusions, especially to
quickly restore the integrity of operations, applications, data, or any
combination of the three. Key ICS and SCADA functions should be backed up with
hot standbys featuring immediate failover capabilities should their primary
counterparts be disrupted. For data protection, automated and contemporaneous
backups are preferable; or at least they should be done at a weekly interval.
Ideally, the backup storage will be off-network and, even better, offsite, too.
The former protects backup data in case malware, such as ransomware, succeeds in
circumventing defense-in-depth and network segmentation measures and locks it
up. ... Like plant health, safety and environment (HSE) programs, cybersecurity
should be considered alongside them as a required mainstay risk-reduction
program with support from executive management, owners, and the board of
directors.
The Future of the Web: The good, the bad and the very weird

The rise of big technology companies over the last two decades has made the
internet more usable for most people, but has also lead to the creation of a
series of 'walled gardens' controlled by them, within which information is held
and not easily relocated. As a result, a small number of very large companies
control what you search for online, or where you share information with your
friends, or even do your shopping. Even worse, these companies have done much to
develop what is effectively 'surveillance capitalism' -- taking the information
we have shared with them (about what we do, where we go and who we know) to sell
to advertisers and others. As smartphones have become one of the key ways we
access the web, that surveillance capitalism now follows us wherever we go. And
while the rise of social media (the so-called 'Web 2.0' era) promised to make it
possible for individuals to produce and share their own content, it was still
mostly the big tech companies that remained the gatekeepers. A platform that was
once about openness seems to be dominated by big tech.
Authorization Challenges in a Multitenant System

Restricting users to the data that belongs to their tenant is the most
fundamental requirement of multitenant authorization. Tenant isolation barriers
are needed to prevent users from accessing sensitive information owned by
another account. Such a breach would erode trust in your service and, depending
on the type of exposure that occurred, could leave you liable to regulatory
penalties. Tenant identification usually occurs early in the lifecycle of a
request. Your service should authenticate the user, determine the tenant they
belong to, and then limit subsequent interactions to data that’s associated with
that tenant. ... Another complication occurs when tenants require unique
combinations of roles and actions to mirror their organization’s structures. One
org might be satisfied by admin and read-only roles; another may need the admin
role to be split into five distinct assignments. The most effective multitenant
authorization systems will flexibly accommodate customizations on a per-tenant
basis. At the application level, granular permission checks will remain the
same; however, the system will need to be configurable so tenants can create
their own roles by combining different permissions.
Deployment Patterns in Microservices Architecture
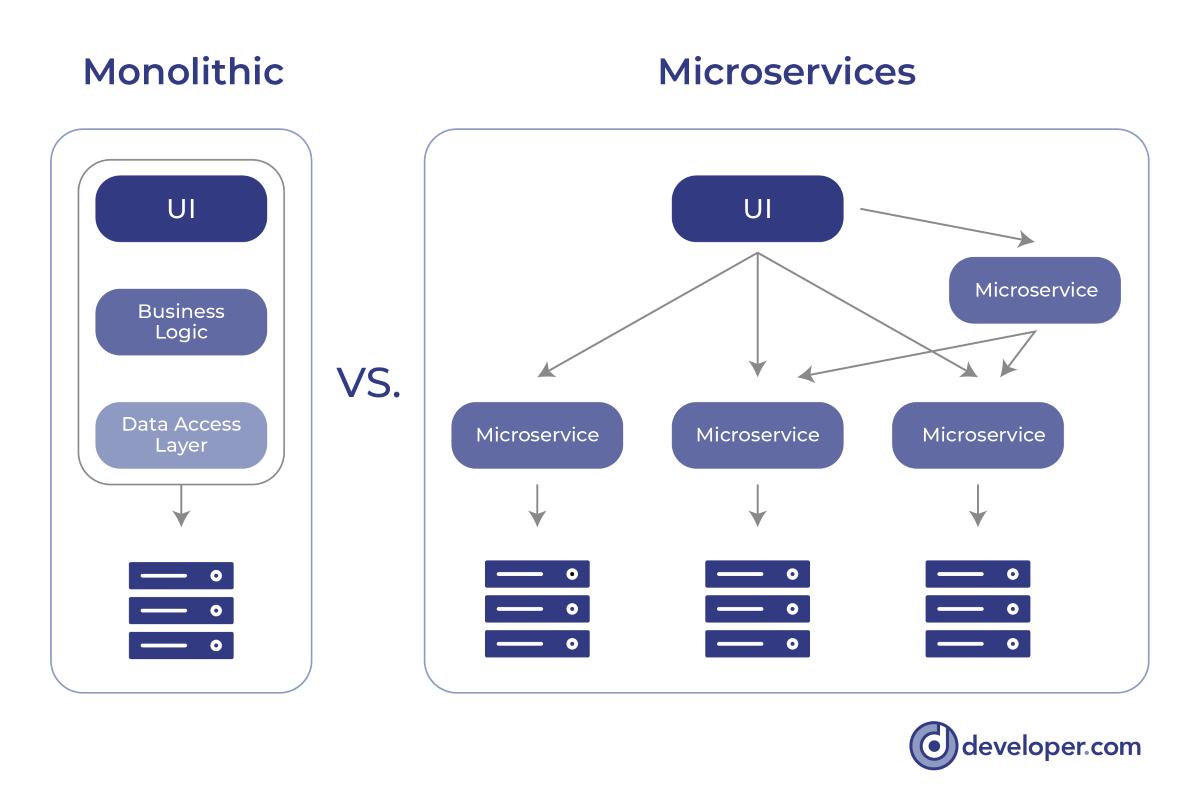
The Multiple Service Instances per Host pattern involves provisioning one or
more physical or virtual hosts. Each of the hosts then executes multiple
services. In this pattern, there are two variants. Each service instance is a
process in one of these variants. In another variant of this pattern, more than
one service instance might run simultaneously. One of the most beneficial
features of this pattern is its efficiency in terms of resources, as well as its
seamless deployment. This pattern has the benefit of having a low overhead,
making it possible to start the service quickly. This pattern has the major
drawback of requiring a service instance to run in isolation as a separate
process. The resource consumption of each instance of a service becomes
difficult to determine and monitor when several processes are deployed in the
same process. The Service Instance per Host pattern is a deployment strategy in
which only one microservice instance can execute on a particular host at a
specific time. Note that the host can be a virtual machine or a container
running just one service instance simultaneously.
Bursting the Microservices Architectures Bubble

The buzz surrounding microservices in recent years doesn't reflect the sudden
emergence of the microservices concept at that time, however. Microservices
architectures actually have a long history that stretches back decades. But they
didn't really catch on and gain mainstream focus until the early-to-mid 2010s.
So, why did everyone go gaga over microservices starting about ten years ago?
That's a complex question, but the answer probably involves the popularization
around the same time of two other key trends: DevOps and cloud computing. You
don't need microservices to do DevOps or use the cloud, but microservices can
come in handy in both of these contexts. For DevOps, microservices make it
easier in certain important respects to achieve continuous delivery because they
allow you to break complex codebases and applications into smaller units that
are easier to manage and easier to deploy. And in the cloud, microservices can
help to consume cloud resources more efficiently, as well as to improve the
reliability of cloud apps.
New Survey Shows 6 Ways to Secure OT Systems

A fundamental principle of OT security is the need to create an air gap between
ICS and OT systems and IT systems. This basic network cybersecurity design
employs an industrial demilitarized zone to prevent threat actors from moving
laterally across systems, but the survey finds that only about half of
organizations have an IDMZ within their OT architecture, and 8% are working on
it. The healthcare, public health and emergency services sectors were especially
behind. Nearly 40% of respondents in those sectors don't have plans to implement
an IDMZ. Implementing a DMZ is a basic best practice, Ford says. "The risk is
lateral movement where breach can move from IT to OT or vice versa, or from
low-value network assets to high-value network assets," Ford says. "The more
attackers can penetrate your infrastructure, the greater damage and downtime
they can cause. Segmentation in DMZ, demilitarized zones, provide an air gap
between IT and OT, and additional segmentation can further protect
business-critical assets with strong access controls, firewalls and policy rules
based on zero trust."
Wearable devices: invasion of privacy or health necessity?

Dangling a carrot of free technology is a way to engage customers, but
protection is vital should wearable technology be compromised. This data isn’t
simply name, address and payment details, but potentially highly personal data
about an individuals’ wellbeing. The insurance industry will need to develop
solutions that help protect the policyholder, and reassure the individual that
their data is secure. With GDPR, UK-GDPR and other regulations globally to be
highly considered, insurers are spending considerable time and investment in
ensuring data is well protected. The ubiquitous nature of wearables has helped
increase engagement with insurance, and customers have been introduced to the
numerous health benefits of using these devices. If you’ve already got a device
tracking your wellbeing, why would you not want a doctor also doing the same? By
becoming an extension to the wearable itself, wearable insurance is likely to be
generally accepted by customers.
Quote for the day:
"Different times need different types of
leadership." -- Park Geun-hye
No comments:
Post a Comment