Zycus: Five digital transformation trends in procurement

Generating vast quantities of data, organisations need to be aware of the level
of data management required in order to successfully deliver a digital
transformation in procurement. “Not understanding the data implications may
result in budget overruns, overtime, or scope reduction in data management. Data
is a key input for many processes and decisions in modern organisations, and
underestimating its relevance can cause an inability to meet goals related to
supplier enablement or PO automation due to capacity and scope constraints,”
said Zycus. When it comes to the quality of data, process digitalisation is a
key driver. Process digitalisation reduces human error; generates greater
business insights, improves decision-making capabilities, and increase value
creation. ... “In recent years, Procurement departments have become more prone
to cyberattacks in the form of malware via a software update, attacks on cloud
services, ransomware, business email compromise, attack on supply chain, etc.,”
commented Zycus. Such threats can result in a loss of sensitive data and/or
financial losses.
Striving for a better balance in the future of work

It is worth noting that the principle of coordinated working hours in offices
grew out of working patterns in factories at a time when the technology for
business was mainly an in-person exercise. Yet, as everyone who has been through
the pandemic knows, knowledge workers no longer work that way ‚ we’re
asynchronous, remote, and international. In many senses, this change in
expectations is no change at all. Knowledge work has always been marked by a
sense of asynchronicity. People meet, talk, agree, and then go off and work in
small groups or alone. What has changed is that 65% of workers now have, and
expect, more flexibility to decide when they work. ... Perhaps one of the most
boringly predictable challenges remote workers face involves the tools they’re
asked to use. On average, workers have 6.2 apps sending them notifications at
work, and 73% of them respond to those outside of working hours, further eroding
the division between (asynchronous) work time and personal time. ... A worker
may find that they do their work at times that suit them best, but still feel
pressurized to pretend to be present the rest of the time, too.
The Metaverse can shake up Digital Commerce forever

The metaverse has already become a playground for luxury fashion brands, with
some launching their new collection in the virtual world and others partnering
up with developers to create their own bespoke games. In the near future, we
anticipate more brands to follow and break the boundaries between virtual and
physical reality to create more innovative, meaningful interactions with
consumers. We are in the very early days here and our team will be working on
many different pilots and experiments. There are several use-cases for Web 3.0
in e-commerce. For example, brands looking to connect with loyal users and fans
can provide additional value by way of gated commerce enabled through NFTs. At
the same time, brands and artists can use NFTs to build and monetize
communities. We can create immersive shopping experiences in the Virtual
Worlds/Metaverse, an ever-expanding world of real-time, with the help of virtual
spaces in 3D. We can also enable e-commerce landscapes based on the Blockchain
that will allow anyone to trade physical products on-chain.
SaaS Security Risk and Challenges
SaaS providers are unlikely to send infrastructure- and application-level
security event logs to customers’ security information and event management
(SIEM) solutions, leaving customers’ security operations teams lacking in terms
of important information. This diminishes the ability to identify and manage
potential security incidents. For example, it can be difficult to know whether
and when a brute-force password replay attack is perpetrated against a SaaS
customer user account. Such attacks could lead to undetected data breaches,
resulting in the organization being considered liable for the data leak and for
not reporting the incident to the appropriate parties (e.g., employees,
customers, authorities) in a timely manner. ... It can be challenging for
customers to understand the fundamental nature of a SaaS provider’s risk
culture. Audits, certifications, questionnaires, and other materials paint a
narrow picture of the providers’ security posture. Moreover, SaaS providers are
unlikely to share their risk register with customers, as this would reveal
excessive details about the SaaS provider’s security posture. Further, SaaS
providers are unlikely to undergo detailed customer audits due to limited
resources.
Optimize Distributed AI Training Using Intel® oneAPI Toolkits
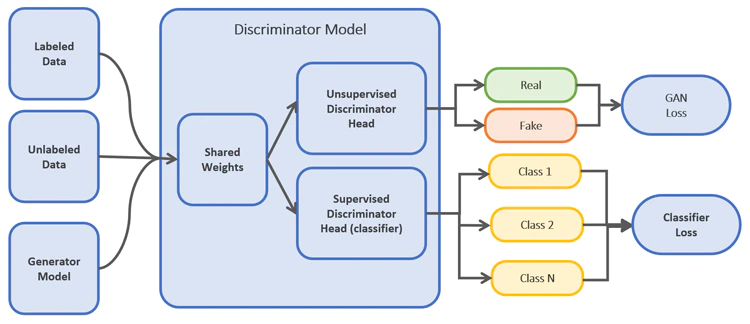
Supervised learning requires large amounts of labeled data. Labeling and
annotation must be done manually by human experts, so it is laborious and
expensive. Semi-supervised learning is a technique where both labeled and
unlabeled data are used to train the model. Usually, the number of labeled
data points is significantly less than the unlabeled data points.
Semi-supervised learning exploits patterns and trends in data for
classification. Semi-supervised learning is a technique where both labeled and
unlabeled data are used to train the model. Usually, the number of labeled
data points is significantly less than the unlabeled data points.
Semi-supervised learning exploits patterns and trends in data for
classification. S-GANs tackle the requirement for vast amounts of training
data by generating data points using generative models. The generative
adversarial network (GAN) is an architecture that uses large, unlabeled
datasets to train an image generator model via an image discriminator model.
GANs comprise two models: generative and discriminative.
The rise of adaptive cybersecurity
The desirable end state - easier said than done - is to embrace an adaptive
cybersecurity posture, supported by people, process and technology - that is
more responsive to the dynamism of today's cybersecurity landscape. As
research firm Ecosystm notes, "anticipating threats before they happen and
responding instantly when attacks occur is critical to modern cybersecurity
postures. It is equally important to be able to rapidly adapt to changing
regulations. Companies need to move towards a position where monitoring is
continuous, and postures can adapt, based on risks to the business and
regulatory requirements. This approach requires security controls to
automatically sense, detect, react, and respond to access requests,
authentication needs, and outside and inside threats, and meet regulatory
requirements." Adaptation is also likely in future to involve artificial
intelligence. A golden example of applying AI adaptively for cybersecurity
would be to be able to detect the presence of code, packages or dependencies
that are impacted by zero-days or other vulnerabilities, and to block those
threats.
The Software Architecture Handbook

One problem that comes up when implementing microservices is that the
communication with front-end apps gets more complex. Now we have many servers
responsible for different things, which means front-end apps would need to
keep track of that info to know who to make requests to. Normally this problem
gets solved by implementing an intermediary layer between the front-end apps
and the microservices. This layer will receive all the front-end requests,
redirect them to the corresponding microservice, receive the microservice
response, and then redirect the response to the corresponding front-end app.
The benefit of the BFF pattern is that we get the benefits of the
microservices architecture, without over complicating the communication with
front-end apps. ... Horizontally scaling on the other hand, means setting up
more servers to perform the same task. Instead of having a single server
responsible for streaming we'll now have three. Then the requests performed by
the clients will be balanced between those three servers so that all handle an
acceptable load.
The Rise of Domain Experts in Deep Learning
Nowadays, a lot of it is people who are like, “Oh, my god, I feel like deep
learning is starting to destroy expertise in my industry. People are doing
stuff with a bit of deep learning that I can’t even conceive of, and I don’t
want to miss out.” Some people are looking a bit further ahead, and they’re
more, like, “Well, nobody is really using deep learning in my industry, but I
can’t imagine it’s the one industry that’s not going to be affected, so I want
to be the first.” Some people definitely have an idea for a company that they
want to build. The other thing we get a lot of is companies sending a bunch of
their research or engineering teams to do the course just because they feel
like this is a corporate capability that they ought to have. And it’s
particularly helpful with the online APIs that are out there now that people
can play around with — Codex or DALL-E or whatever — and get a sense of, “Oh,
this is a bit like something I do in my job, but it’s a bit different if I
could tweak it in these ways.” However, these models also have the unfortunate
side effect, maybe, of increasing the tendency of people to feel like AI
innovation is only for big companies, and that it’s outside of their
capabilities.
Q&A: Dropbox exec outlines company's journey into a remote-work world

"Underneath virtual first is a number of tenets that define how we think about
the future of work. One of those is ‘asynchronous by default,' the idea being
that if we're going to have people working remotely, that shouldn't mean they
spend eight hours a day on video calls. Instead, at Dropbox, you're measured
on your output and the impact that you make, rather than how many meetings you
can sit in. "That then led us to think about how much time we should be
spending in meetings, and as a result, we rolled out something called ‘core
collaboration hours’ where employees reserve four hours each day to be
available for meetings. That means there’s times when you're open to meet with
your team or anyone else in the company, but also that you've got those other
four hours in the day to focus on the work that you need to do. "Does that
mean you wouldn't flex that to meet with somebody who's in a different time
zone or something else? Absolutely not. It's your time to manage as an
individual, because we're measuring you on the impact and output that you're
making.
India poised to be at the center of metaverse-based gaming

Much before metaverse became popular, VR games like Minecraft and Roblox had
captivated scores of young gamers. The immersive gaming experience delivered
by AR/VR and the rapid growth of devices powered by AR/VR and XR has further
accelerated the growth of metaverse to the current level. Meanwhile, the
growth of high-speed Internet has acted as the catalyst driving this
transformation. While VR heads top the list of gaming devices in the
metaverse, mobile phones, gaming PCs, gaming consoles, and hearable/wearables
are also evolving to suit the demands of metaverse applications. Metaverse
also blends games with other apps like live streaming, cryptocurrencies, and
social media, creating several possibilities for players to transact across
the ecosystem chain. For example, gamers can use the NFTs/cryptocurrencies in
metaverse to purchase digital assets, which they can preserve for another
game, maybe from a different publisher. Thus players will earn greater value
for money while also enjoying a near-real world gaming experience with
possibilities never imagined before.
Quote for the day:
"Most people live with pleasant
illusions, but leaders must deal with hard realities." --
Orrin Woodward
No comments:
Post a Comment