How Founders Kill Their Own Start-Ups

First, micro-managing founders have a hard time scaling up their ventures. A lack of empowerment inevitably creates decision bottlenecks, which hamper speed of execution, a key ingredient of scalability. Such bottlenecks also foster “firefighting”, which is when small issues keep grabbing more attention and resources than they should. Ultimately, high-level, high-impact decisions suffer neglect and progress grinds to a halt. Second, micro-management is a talent drain. Often those who are attracted to start-ups want to build something, to be part of something bigger. Millennials in particular want to have an impact. Micro-managers clip wings and can’t retain top contributors, especially creative ones. ... Third, time spent micro-managing is time spent away from a founder’s most important tasks: Thinking about the big picture, drumming up business and finding resources to make everything run smoothly. A founder’s micro-management, evidenced by high turnover, may even put off potential advisors and investors.
How the Threat Landscape Will Shift This Year
Defending against supply chain attacks will be tough because each software vendor has a different distribution mechanism and signing infrastructure, says Weston. In the past, companies could put software on a "trusted list" if it had a history of being secure. However, he says, businesses have to realize anything can change from good to bad at any time. "Getting your software sources from centralized locations where possible is one of the practical means for protecting against supply chain attacks," Weston adds. Cryptocurrency will be a growing security issue as more people adopt it. Attackers will target machines to cannibalize their resources and focus on cryptocurrencies, which are getting harder to mine in legitimate ways. Wallets will also become popular among hackers.
Most organizations struggle with finding qualified tech staff, says Todd Thibodeaux, president and CEO of CompTIA. Training them up on the clock feels equally daunting. “The good news for employers is that the majority of IT pros like what they’re doing,” Thibodeaux says. “Their jobs provide them with a sense of personal accomplishment. Their skills and talents are put to good use. They see opportunities to grow and develop in their careers — and they’re generally satisfied with their compensation and benefits.” While IT staff may enjoy their work, retraining goes a long way in keeping it that way, says Thibodeaux. “IT pros would like more resources for training and development, and more career path guidance and career advancement opportunities,” he says. “They’re also interested in having access to more tools and engaging with more technologies and applications. And they’d welcome the opportunity to work on new technology initiatives.”
Code Refactoring Techniques
Red-green refactor is the Agile engineering pattern which underpins Test Driven Development. Characterized by a “test-first” approach to design and implementation, this lays the foundation for all forms of refactoring. You incorporate refactoring into the test driven development cycle by starting with a failing “red” test, writing the simplest code possible to get the test to pass “green,” and finally work on improving and enhancing your code while keeping the test “green.” This approach is about how one can seamlessly integrate refactoring into your overall development process and work towards keeping code clean. There are two distinct parts to this: writing code that adds a new function to your system, and improving the code that does this function. The important thing is to remember to not do both at the same time during the workflow.
What is DevSecOps? Developing more secure applications
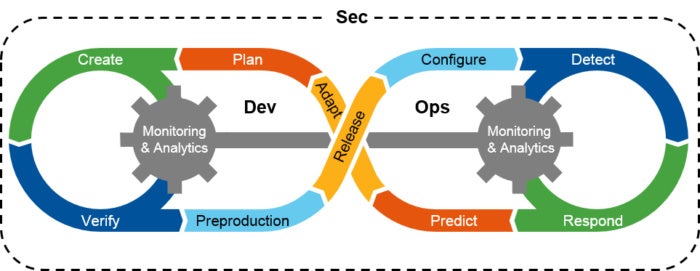
“DevOps has become second nature for agile, high-performing enterprises and a foundation for the success of their online business,” says Pascal Geenens, a security evangelist and researcher at Radware. “Continuous change in technology and consumer demand means there is a continuous cycle of updates to run that will keep a very varied set of functions from page upload times to shopping and search features up to date and running at their best.” “However, application security was mostly an afterthought, and at times perceived as a roadblock to staying ahead of the competition,” says Geenens. “Given the reliance of applications to keep operations running, bypassing security must be considered a high-risk strategy -- a distributed or permanent denial of service attack could easily catch you out. You just need to look at the implications of failing to update the Apache Struts framework as suffered by Equifax. The DevSecOps movement is designed to change this.”
The symphonic enterprise
After a decade of domain-specific transformation, one question remains unanswered: How can disruptive technologies work together to achieve larger strategic and operational goals? We are now seeing some forward-thinking organizations approach change more broadly. They are not returning to “sins of the past” by launching separate, domain-specific initiatives. Instead, they are thinking about exploration, use cases, and deployment more holistically, focusing on how disruptive technologies can complement each other to drive greater value. For example, blockchain can serve as a new foundational protocol for trust throughout the enterprise and beyond. Cognitive technologies make automated response possible across all enterprise domains. Digital reality breaks down geographic barriers between people, and systemic barriers between humans and data. Together, these technologies can fundamentally reshape how work gets done, or set the stage for new products and business models.
Aadhaar sitting duck for cyber criminals, says RBI-backed research

"Aadhaar faces a number of challenges over the short and long-term. The primary challenge is to protect the data from prying and excessive profit seeking excess of the business world. It is wellknown that businesses are increasingly operating in a highly competitive world in which ethical boundaries are rapidly being pulled down. The problem is compounded because they have to satisfy their shareholders in a competitive business environment that rarely looks beyond the quarterly profits and the operational dynamics of stock market listing," it says. However, the paper says, cyber vulnerabilities of Aadhaar are a bigger concern than the possible commercial misuse of data. "In an era when cyber threats are frequent, the major challenge for UIDAI is to protect the data under its control since the biometrics is now an important national asset which has huge ramifications for various government programmes and the banking system," it says.
3 top trends that will drive ERP software development
Organizations are continuing to see the many advantages of developing a roadmap and strategy that leads to digital transformation (i.e. the ability to leverage the Industrial Internet of Things (IIoT), machine learning, AI, big data or analytics). This movement will continue to drive their approach through 2018 or organizations will face the consequences of being left behind by competitors. From an ERP perspective, the combined driving force of these innovative technologies will continue to re-shape how enterprises utilize their IT solutions to provide increased efficiency, process and productivity inside their organization – something for many have been left untapped. While the industry has been discussing many of these leading-edge technologies, here are the “big three” technologies which will play a significant role in re-shaping how we think of ERP in 2018.
How network verification differs from monitoring, and what it’s good for
In a network verification system, the intent is explicitly declared – in this case, that the external partner network should be connected to the demilitarized zone but isolated from the rest of the data center. The network verification system can then explore all possible data flows that could occur and determine if some flows will violate the intent, thus spotting the vulnerability well before the attack. Now suppose you are called early Saturday morning to fix this vulnerability by locking down firewall rules. ... Depending on the application and the access-control mistake, such a slip-up might result in an immediate red-alert outage, or it might not show up until Monday morning. Either way, traffic monitoring will see the problem only after it has already affected users. A company with a network verification system could incorporate the proposed change into its network model pre-deployment and predict that the change would violate the connectivity intent, saving you from causing an outage.
Will 2018 be the year of the chatbot? Not without human help
"A chatbot is like a baby—it needs to be nurtured and taught—you can't just set up a chatbot and let it go," Harles said. Developers should avoid getting too attached to a certain technology, and think about the reasoning for a chatbot, Harles said. The bot should set out to solve a problem for the customer, making it a useful, uncomplex tool. "Some organizations think chatbots will automate a process or avoid call center calls—but the truth is chatbots are like the advent of the ATM," Harles said. "Many thought the ATM would replace banks and tellers, but in reality, it simply created a new channel. That is what chatbots will deliver for brands—a new communication channel." But a new communication channel can come with its own issues, including potential abuse of the channel with inappropriate or unrelated questions.
Quote for the day:
"It's not what you look at that matters, it's what you see." -- Henry David Thoreau

No comments:
Post a Comment