Quote for the day:
“Success is most often achieved by those who don't know that failure is inevitable.” -- Coco Chanel
What CIOs Need to Know About the Technical Aspects of AI Integration
 AI systems are built around models that utilize data stores, algorithms for
query, and machine learning that expands the AI’s body of knowledge as the AI
recognizes common logic patterns in data and assimilates knowledge from them.
There are many different AI models to choose from. In most cases, companies use
predefined AI models from vendors and then expand on them. In other cases,
companies elect to build their own models “from scratch.” Building from scratch
usually means that the organization has an on-board data science group with
expertise in AI model building. Common AI model frameworks (e.g., Tensorflow,
PyTorch, Keras, and others), provide the software resources and tools. ... The
AI has to be integrated seamlessly with the top to bottom tech stack if it is
going to work. This means discussing how and where data from the AI will be
stored, with SQL and noSQL databases being the early favorites. Middleware that
enables the AI to interoperate with other IT systems must be interfaced with.
Most AI models are open source, which can simplify integration -- but
integration still requires using middleware APIs like REST, which integrates the
AI system with Internet-based resources; or GraphQL, which facilitates the
integration of data from multiple sources.
AI systems are built around models that utilize data stores, algorithms for
query, and machine learning that expands the AI’s body of knowledge as the AI
recognizes common logic patterns in data and assimilates knowledge from them.
There are many different AI models to choose from. In most cases, companies use
predefined AI models from vendors and then expand on them. In other cases,
companies elect to build their own models “from scratch.” Building from scratch
usually means that the organization has an on-board data science group with
expertise in AI model building. Common AI model frameworks (e.g., Tensorflow,
PyTorch, Keras, and others), provide the software resources and tools. ... The
AI has to be integrated seamlessly with the top to bottom tech stack if it is
going to work. This means discussing how and where data from the AI will be
stored, with SQL and noSQL databases being the early favorites. Middleware that
enables the AI to interoperate with other IT systems must be interfaced with.
Most AI models are open source, which can simplify integration -- but
integration still requires using middleware APIs like REST, which integrates the
AI system with Internet-based resources; or GraphQL, which facilitates the
integration of data from multiple sources. What is Chaos Engineering in DevOps?
 As a key enabler for high-performing DevOps teams, Chaos Engineering pushes the boundaries of system resilience. It intentionally
introduces faults into environments to expose hidden failures and validate
that systems can recover gracefully. Rather than waiting for outages to learn
hard lessons, Chaos Engineering allows teams to simulate and study these
failures in a controlled way. ... In the DevOps landscape, continuous delivery
and rapid iteration are standard. However, these practices can increase the
risk of introducing instability if reliability isn’t addressed with equal
rigor. Chaos Engineering complements DevOps goals in several ways:Reveals
Single Points of Failure (SPOFs): Chaos experiments help discover dependencies
that may not be resilient. Uncovers Alerting Gaps: By simulating failures,
teams can assess whether monitoring systems raise appropriate alerts. Tests
Recovery Readiness: Teams get real-world practice in recovery and incident
response. Improves System Observability: Monitoring behaviors during chaos
experiments leads to better instrumentation. Builds Team Confidence:
Engineering and operations teams gain a better understanding of the system and
how to handle outages. Chaos Engineering helps shift failure from a reactive
event to a proactive learning opportunity — aligning directly with the DevOps
principle of continuous improvement.
As a key enabler for high-performing DevOps teams, Chaos Engineering pushes the boundaries of system resilience. It intentionally
introduces faults into environments to expose hidden failures and validate
that systems can recover gracefully. Rather than waiting for outages to learn
hard lessons, Chaos Engineering allows teams to simulate and study these
failures in a controlled way. ... In the DevOps landscape, continuous delivery
and rapid iteration are standard. However, these practices can increase the
risk of introducing instability if reliability isn’t addressed with equal
rigor. Chaos Engineering complements DevOps goals in several ways:Reveals
Single Points of Failure (SPOFs): Chaos experiments help discover dependencies
that may not be resilient. Uncovers Alerting Gaps: By simulating failures,
teams can assess whether monitoring systems raise appropriate alerts. Tests
Recovery Readiness: Teams get real-world practice in recovery and incident
response. Improves System Observability: Monitoring behaviors during chaos
experiments leads to better instrumentation. Builds Team Confidence:
Engineering and operations teams gain a better understanding of the system and
how to handle outages. Chaos Engineering helps shift failure from a reactive
event to a proactive learning opportunity — aligning directly with the DevOps
principle of continuous improvement.
Resilience vs. risk: Rethinking cyber strategy for the AI-driven threat landscape
 Unfortunately, many companies are similarly unprepared. In a recent survey of
1,500 C-suite and senior executives in 14 countries conducted for the LevelBlue
2025 Futures Report, most respondents said their organizations were simply not
ready for the new wave of AI-powered and supply-chain attacks. ... There's also
a certain disconnect in the survey results, with fears about AI tempered by
overconfidence in one's own abilities. Fifty-four percent of respondents claim
to be highly competent at using AI to enhance cybersecurity, and 52% feel just
as confident in their abilities to defend against attackers who use AI. However,
there's a substantial difference between the bulk of the respondents and those
few — about 7% of the total of 1,500 — that LevelBlue classified as already
having achieved cyber resilience. "An organization with a cyber-resilient
culture is a place where everyone, at every level, understands their role in
cybersecurity and takes accountability for it — including protecting sensitive
data and systems," the 2025 Futures Report explains. Most notably, none of the
100 or so organizations that LevelBlue deemed cyber resilient had experienced a
breach in the 12 months preceding the survey. Ninety-four percent of the
cyber-resilient elite said they were making investments in software-supply-chain
security, versus 62% of the total group.
Unfortunately, many companies are similarly unprepared. In a recent survey of
1,500 C-suite and senior executives in 14 countries conducted for the LevelBlue
2025 Futures Report, most respondents said their organizations were simply not
ready for the new wave of AI-powered and supply-chain attacks. ... There's also
a certain disconnect in the survey results, with fears about AI tempered by
overconfidence in one's own abilities. Fifty-four percent of respondents claim
to be highly competent at using AI to enhance cybersecurity, and 52% feel just
as confident in their abilities to defend against attackers who use AI. However,
there's a substantial difference between the bulk of the respondents and those
few — about 7% of the total of 1,500 — that LevelBlue classified as already
having achieved cyber resilience. "An organization with a cyber-resilient
culture is a place where everyone, at every level, understands their role in
cybersecurity and takes accountability for it — including protecting sensitive
data and systems," the 2025 Futures Report explains. Most notably, none of the
100 or so organizations that LevelBlue deemed cyber resilient had experienced a
breach in the 12 months preceding the survey. Ninety-four percent of the
cyber-resilient elite said they were making investments in software-supply-chain
security, versus 62% of the total group.
Can Digital Trust Be Rebuilt in the Age of AI?
When digital trust erodes, everything from e-commerce to online communities suffers, as users approach the content with increasing skepticism. Many online communities on social platforms such as Reddit are becoming more and more dominated by bots that seem human at first glance, but they quickly show patterns designed to steer the conversation in specific ways. The implications, both for users and the platforms, are quite worrisome. ... People don’t want to connect with perfection. They want to connect with shared humanity. I recently visited one of my healthcare provider’s websites for info on a procedure and spent some time browsing through the blogs. What I wanted was to read about people sharing my concerns, about the doctors and positive outcomes, how others overcame their illnesses, or maybe a surgeon’s perspective on the procedure. Instead, I got lots of AI-generated information (it’s easy to recognize the “Chat GPT style”—bullet points, summaries, words that it tends to use) on medical conditions and procedures, but it left me cold. It felt like the machine was “AI-xplaining” to me what it thought I needed to read, not what I wanted. Prioritizing authentic communication helps invite our audiences into building a relationship, rather than a transaction. It expresses to them that we value them as visitors, as readers and consumers of our content.Industrial cybersecurity leadership is evolving from stopping threats to bridging risk, resilience
 The role of cybersecurity leadership in industrial control systems (ICS/OT) is
evolving, but not fast enough, Richard Robinson, chief executive officer of
Cynalytica, told Industrial Cyber. “We often view leadership maturity through
a Western lens. That is a mistake. The threat landscape is global, but
readiness is uneven,” Robinson said. “Many regions still operate under the
assumption that cyber threats are an ‘IT problem.’ Meanwhile, adversarial
technologies targeting control systems, from protocol-aware malware to
AI-generated logic attacks, are advancing faster than many leaders are willing
to acknowledge.” He added that “We are past the era of defending just IP
networks. Today’s threats exploit blind spots in non-IP protocols, legacy
PLCs, and analog instrumentation. Nation-states are building offensive
capabilities that bypass traditional defenses entirely, and they are being
tested in active conflict zones.” ... As the industrial CISO role becomes more
strategically focused, balancing compliance, operational integrity, and
business risk, the executives reevaluate how expectations around cybersecurity
leadership are shifting across industrial organizations. Pereira mentioned
that resilience is becoming a bigger focus.
The role of cybersecurity leadership in industrial control systems (ICS/OT) is
evolving, but not fast enough, Richard Robinson, chief executive officer of
Cynalytica, told Industrial Cyber. “We often view leadership maturity through
a Western lens. That is a mistake. The threat landscape is global, but
readiness is uneven,” Robinson said. “Many regions still operate under the
assumption that cyber threats are an ‘IT problem.’ Meanwhile, adversarial
technologies targeting control systems, from protocol-aware malware to
AI-generated logic attacks, are advancing faster than many leaders are willing
to acknowledge.” He added that “We are past the era of defending just IP
networks. Today’s threats exploit blind spots in non-IP protocols, legacy
PLCs, and analog instrumentation. Nation-states are building offensive
capabilities that bypass traditional defenses entirely, and they are being
tested in active conflict zones.” ... As the industrial CISO role becomes more
strategically focused, balancing compliance, operational integrity, and
business risk, the executives reevaluate how expectations around cybersecurity
leadership are shifting across industrial organizations. Pereira mentioned
that resilience is becoming a bigger focus. Eyes on Data: Best Practices and Excellence in Data Management Matter More Than Ever
 Despite the universal dependence, most organizations still grapple with
fundamental data challenges — inconsistent definitions, fragmented governance,
escalating regulatory expectations, and massive growth in data’s volume,
variety, and velocity. In other words — as every data professional and even
every data user understands — data is more critical than ever, and yet harder
than ever to manage effectively. It’s precisely in this high-stakes context that
best practices in data management are not just beneficial — they’re essential.
... True to its purpose, DCAM v3 is not a one-time initiative — it’s a lifecycle
framework designed to support continuous improvement and progress. That’s why
the EDM Council also created the Data Excellence Program, a structured path for
organizations to achieve and gain recognition at the organizational level for
data excellence. Given its role in driving best practices, DCAM serves as the
Program’s backbone for defining and assessing data management capabilities and
measuring participants’ progress in their journey towards long-term success and
achieving sustained excellence. ... In an era where data is both a competitive
asset and a compliance requirement, only those organizations that manage it with
rigor, purpose, and strategy will thrive.
Despite the universal dependence, most organizations still grapple with
fundamental data challenges — inconsistent definitions, fragmented governance,
escalating regulatory expectations, and massive growth in data’s volume,
variety, and velocity. In other words — as every data professional and even
every data user understands — data is more critical than ever, and yet harder
than ever to manage effectively. It’s precisely in this high-stakes context that
best practices in data management are not just beneficial — they’re essential.
... True to its purpose, DCAM v3 is not a one-time initiative — it’s a lifecycle
framework designed to support continuous improvement and progress. That’s why
the EDM Council also created the Data Excellence Program, a structured path for
organizations to achieve and gain recognition at the organizational level for
data excellence. Given its role in driving best practices, DCAM serves as the
Program’s backbone for defining and assessing data management capabilities and
measuring participants’ progress in their journey towards long-term success and
achieving sustained excellence. ... In an era where data is both a competitive
asset and a compliance requirement, only those organizations that manage it with
rigor, purpose, and strategy will thrive.
Modern Test Automation With AI (LLM) and Playwright MCP
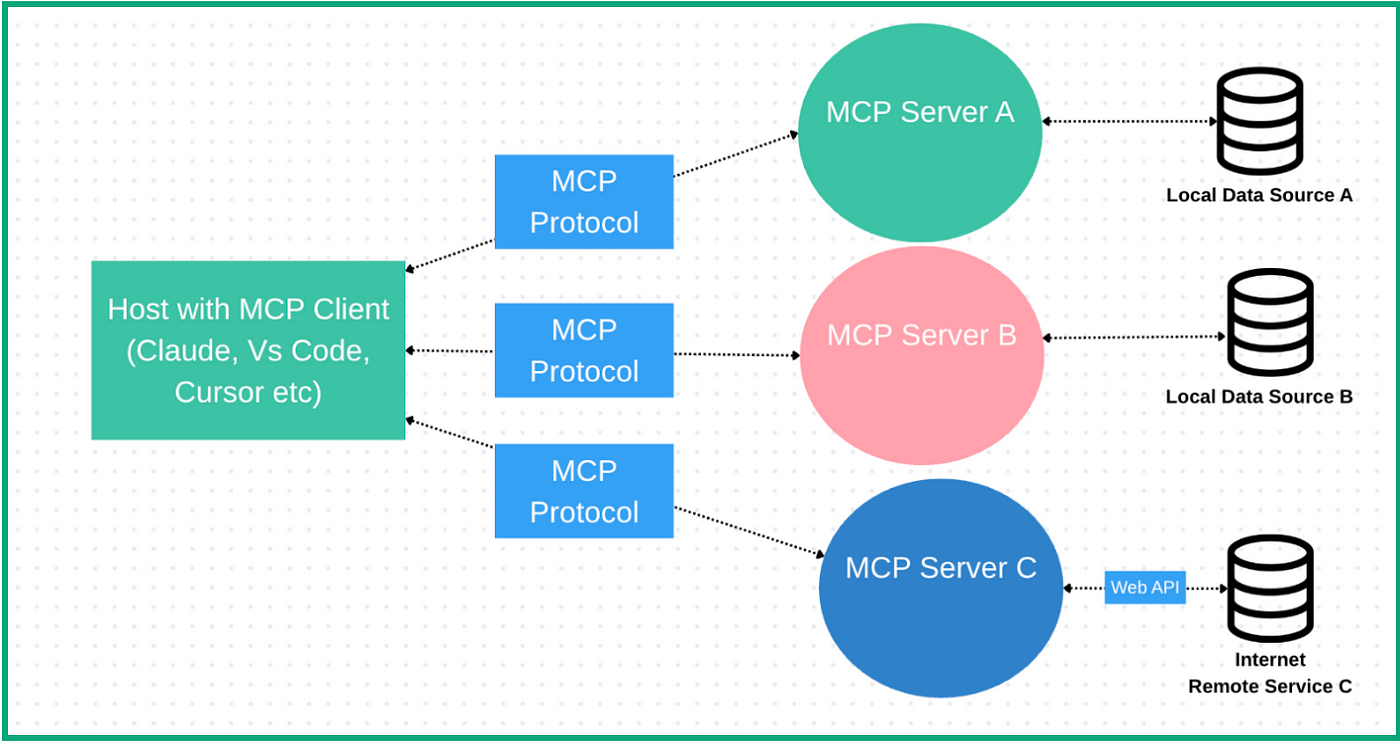 The ability to interact with the web programmatically is becoming increasingly
crucial. This is where GenAI steps in, by leveraging large language models
(LLMs) like Claude or custom AI frameworks, GenAI introduces intelligence into
test automation, enabling natural language test creation, self-healing scripts,
and dynamic adaptability. The bridge that makes this synergy possible is the
Model Context Protocol (MCP), a standardized interface that connects GenAI’s
cognitive power with Playwright’s automation prowess. ... Playwright MCP is
a server that acts as a bridge between large language models (LLMs) or other
agents and Playwright-managed browsers. It enables structured command execution,
allowing AI to control web interactions like navigation, form filling, or
assertions. What sets MCP apart is its reliance on the browser’s accessibility
tree — a semantic, hierarchical representation of UI elements—rather than
screenshot-based visual interpretation. In Snapshot Mode, MCP provides real-time
accessibility snapshots, detailing roles, labels, and states. This approach is
lightweight and precise, unlike Vision Mode, which uses screenshots for custom
UIs but is slower and less reliable. By prioritizing the accessibility tree, MCP
delivers unparalleled speed, reliability, and resource efficiency.
The ability to interact with the web programmatically is becoming increasingly
crucial. This is where GenAI steps in, by leveraging large language models
(LLMs) like Claude or custom AI frameworks, GenAI introduces intelligence into
test automation, enabling natural language test creation, self-healing scripts,
and dynamic adaptability. The bridge that makes this synergy possible is the
Model Context Protocol (MCP), a standardized interface that connects GenAI’s
cognitive power with Playwright’s automation prowess. ... Playwright MCP is
a server that acts as a bridge between large language models (LLMs) or other
agents and Playwright-managed browsers. It enables structured command execution,
allowing AI to control web interactions like navigation, form filling, or
assertions. What sets MCP apart is its reliance on the browser’s accessibility
tree — a semantic, hierarchical representation of UI elements—rather than
screenshot-based visual interpretation. In Snapshot Mode, MCP provides real-time
accessibility snapshots, detailing roles, labels, and states. This approach is
lightweight and precise, unlike Vision Mode, which uses screenshots for custom
UIs but is slower and less reliable. By prioritizing the accessibility tree, MCP
delivers unparalleled speed, reliability, and resource efficiency.
How to tackle your infrastructure technical debt
 The quickest win, he suggested, is the removal of “zombie servers” – those that
no one dares to turn off because their purpose is unknown. Network tools can
reveal what these servers are doing and who is using them, “and frequently, the
answer is nothing and nobody”. The same applies to zombie virtual machines
(VMs). Another relatively quick win involves replacing obsolete on-premise
applications with a software-as-a-service (SaaS) equivalent. One of Harvey’s
clients was using an unsupported version of Hyperion on an outdated operating
system and hardware. “[They] can’t get rid of it because this is used by people
who report directly to the board for the financials.” A simple solution, Harvey
suggested, was to “go to Oracle Financials in the cloud...and it’s not your
problem anymore”. Infrastructure and operations teams should also lead by
example and upgrade their own systems. “You should be able to get the CIO to
approve the budget for this because it’s in your control,” said Harvey.... A
crucial first step is to stop installing old products. This requires backing
from the CIO and other executives, Harvey said, but rules should be established,
such as: We will not install any new copies of Windows Server 2016…because it’s
going to reach end of support in 2026.
The quickest win, he suggested, is the removal of “zombie servers” – those that
no one dares to turn off because their purpose is unknown. Network tools can
reveal what these servers are doing and who is using them, “and frequently, the
answer is nothing and nobody”. The same applies to zombie virtual machines
(VMs). Another relatively quick win involves replacing obsolete on-premise
applications with a software-as-a-service (SaaS) equivalent. One of Harvey’s
clients was using an unsupported version of Hyperion on an outdated operating
system and hardware. “[They] can’t get rid of it because this is used by people
who report directly to the board for the financials.” A simple solution, Harvey
suggested, was to “go to Oracle Financials in the cloud...and it’s not your
problem anymore”. Infrastructure and operations teams should also lead by
example and upgrade their own systems. “You should be able to get the CIO to
approve the budget for this because it’s in your control,” said Harvey.... A
crucial first step is to stop installing old products. This requires backing
from the CIO and other executives, Harvey said, but rules should be established,
such as: We will not install any new copies of Windows Server 2016…because it’s
going to reach end of support in 2026.
Why Every Business Leader Needs to Think Like an Enterprise Architect
Enterprise architecture provides the structure and governance for effective digital transformation, laying the groundwork for innovation such as AI models. Vizcaino said that SAP will soon have successfully established an AI copilot mode to provide expansive process automation, helping workers make decisions more quickly and effectively. Even as companies enhance automation in this way, leaders’ core responsibilities will largely remain the same: creating business, sustaining business, and creating competitive advantage. It’s how they go about doing this in the age of AI that will look a bit different. Many different types of assets and techniques optimized by data and AI — as enabled by enterprise architecture — will become more valuable moving forward. ... While leveraging AI to automate processes is a key area of current innovation, future innovation will involve optimizing the ways in which those AI investments are orchestrated. Enterprise architecture is not a skill, but rather a discipline that should be infused across all departments of an organization, Vizcaino added. The silos of the past should be avoided in the ways that organizations restructure their operations; instead, inculcating an enterprise-architecture mindset within all business units can serve to bring stakeholders from across an organization together in service of shared technology goals.Building Supply Chain Cybersecurity Resilience
 Supply chain cybersecurity threats are diverse, and the repercussions severe.
How can retail and hospitality organizations protect themselves? To help fend
off social engineering attacks, make cybersecurity education a priority. Train
everyone in your organization, from top to bottom, to spot suspicious activity
so they can detect and deflect phishing schemes. Meanwhile, verify all software
is up to date to prevent cyber attackers from exploiting network
vulnerabilities. It’s also wise to regularly audit your third-party vendors’
security postures to screen for risks and find areas for improvement. In
addition to your third-party vendors, turn to your fellow retail and hospitality
organizations. The best defense against cyber attackers is putting up a united
front and bolstering the entire supply chain. You can collaborate with other
retailers and hoteliers via RH-ISAC, the global cybersecurity community, created
specifically to help retail and hospitality organizations share cyber
intelligence and cybersecurity best practices. Its new LinkSECURE Program offers
a membership for small- to mid-size vendors and service providers to help those
with limited IT or cyber resources mature their cybersecurity operations. The
new program gives every participant an evaluation of their cybersecurity
posture, along with a dedicated success manager to guide them through 18
critical security controls and safeguards.
Supply chain cybersecurity threats are diverse, and the repercussions severe.
How can retail and hospitality organizations protect themselves? To help fend
off social engineering attacks, make cybersecurity education a priority. Train
everyone in your organization, from top to bottom, to spot suspicious activity
so they can detect and deflect phishing schemes. Meanwhile, verify all software
is up to date to prevent cyber attackers from exploiting network
vulnerabilities. It’s also wise to regularly audit your third-party vendors’
security postures to screen for risks and find areas for improvement. In
addition to your third-party vendors, turn to your fellow retail and hospitality
organizations. The best defense against cyber attackers is putting up a united
front and bolstering the entire supply chain. You can collaborate with other
retailers and hoteliers via RH-ISAC, the global cybersecurity community, created
specifically to help retail and hospitality organizations share cyber
intelligence and cybersecurity best practices. Its new LinkSECURE Program offers
a membership for small- to mid-size vendors and service providers to help those
with limited IT or cyber resources mature their cybersecurity operations. The
new program gives every participant an evaluation of their cybersecurity
posture, along with a dedicated success manager to guide them through 18
critical security controls and safeguards.
No comments:
Post a Comment