Cloud application portability remains unrealistic

Enterprises can deploy an application across multiple cloud providers to
distribute risk and reduce dependency on a single vendor. This strategy also
offers leverage when negotiating terms or migrating services. It may prevent
vendor lock-in and provide flexibility to optimize costs by leveraging the most
cost-effective services available from different providers. That said, you’d be
wrong if you think multicloud is the answer to a lack of portability. You’ll
have to attach your application to native features to optimize them for the
specific cloud provider. As I’ve said, portability has been derailed, and you
don’t have good options. A “multiple providers” approach minimizes the negative
impact but does not solve the portability problem. Build applications with
portability in mind. This approach involves containerization technologies, such
as Docker, and orchestration platforms, such as Kubernetes. Abstracting
applications from the underlying infrastructure ensures they are compatible with
multiple environments. Additionally, avoiding proprietary services and opting
for open source tools can enhance portability and reduce costs associated with
reconfigurations or migrations.
Will Data Centers in Orbit Launch a New Phase of Sustainability?

Space offers an appealing solution for many of the problems that plague
terrestrial data centers. Space-based data centers could use solar arrays to
draw power from the sun, alleviating the burden on electrical grids here on
Earth. They would not require water for cooling. They would not take up land,
disturb people or wildlife. Additionally, natural disasters that can damage or
wipe out data centers on Earth -- earthquakes, wildfires, floods, tsunamis --
are a non-issue in space. ... While the upsides of data centers in space are
easy to imagine, what will it take to make them a reality? The Advanced Space
Cloud for European Net zero emission and Data sovereignty (ASCEND) study set out
to answer questions about space data centers technical feasibility and their
environmental benefits. The study is funded by the European Commission as part
of the Horizon Europe, a scientific research program. Thales Alenia Space led
the study with a consortium of 11 partners, including research organizations and
industrial companies from five European countries. Thales Alenia Space announced
the results of the 16-month study at the end of June.
Workload Protection in the Cloud: Why It Matters More Than Ever
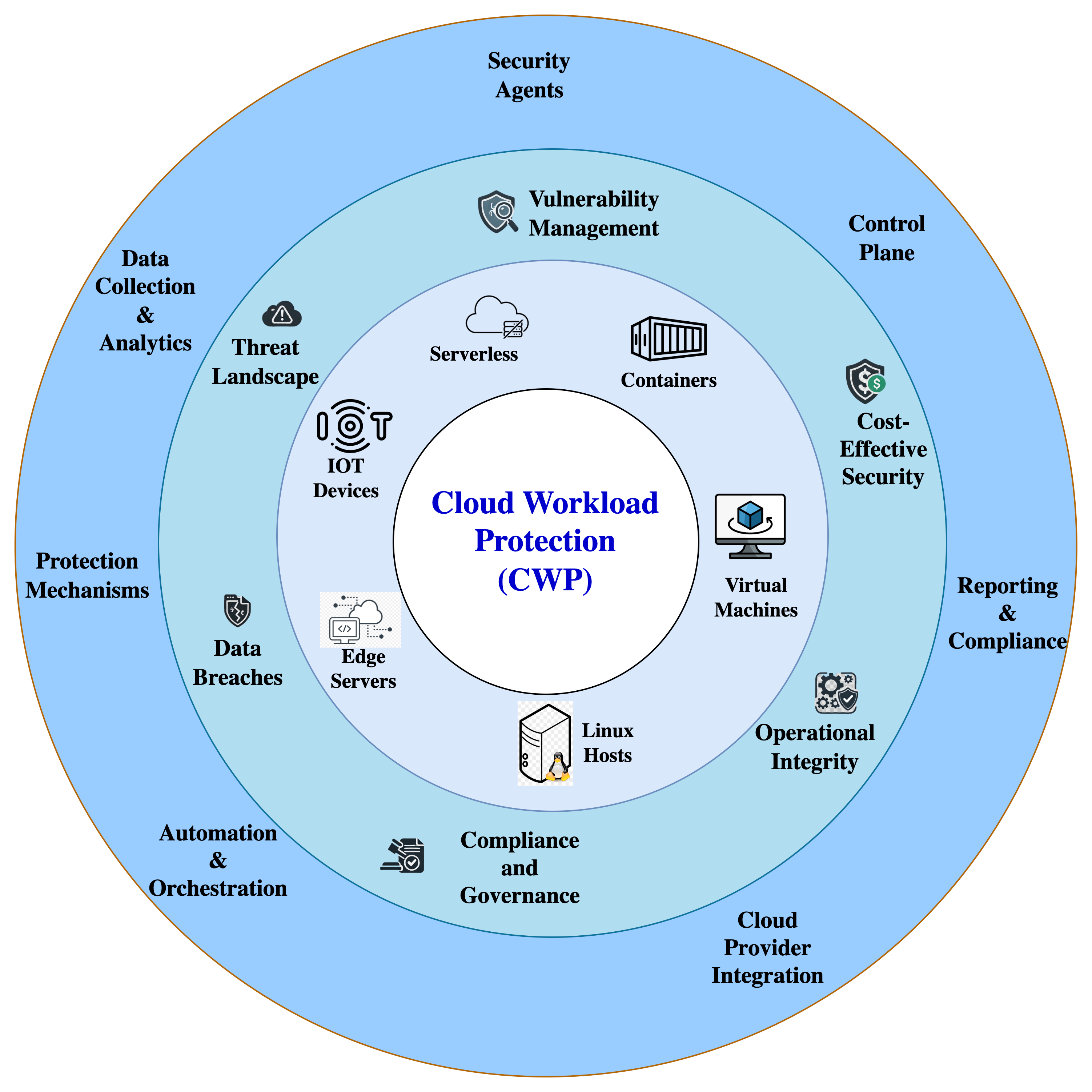
CWP is a necessity that must not be ignored. As the adoption of cloud technology
grows, the scale and complexity of threats also escalate. Here are the reasons
why CWP is critical: Increased threat environment: Cyber threats are becoming
more complex and frequent. CWP tools are crafted to detect and counter these
changing threats in real time, delivering enhanced protection for cloud
workloads exposed across various networks and environments. Protection against
data breaches and compliance: Data breaches can lead to severe financial and
reputational harm. CWP tools assist organizations in complying with strict
regulations like GDPR, HIPAA, and PCI-DSS by implementing strong security
protocols and compliance checks. Maintenance of operational integrity: It is
essential for businesses to maintain the uninterrupted operation of their cloud
workloads without being affected by security incidents. CWP tools offer
extensive threat detection and automated responses, minimizing disruptions and
upholding operational integrity. Cost implications: Security breaches can incur
substantial costs. Investing in CWP tools helps avert these risks by early
identification of vulnerabilities and threats, finally protecting organizations
from potential financial losses due to breaches and service interruptions.
How Human-Informed AI Leads to More Accurate Digital Twins

The value of a DT is directly proportional to its accuracy, which in turn
depends on the data available. But data availability remains a challenge —
ironically, often in the business use cases that could benefit the most from DTs
— and it’s a big reason why DTs are still in their infancy. DTs could help guide
the expansion of current products to new market domains, accelerating R&D
and innovation by enabling virtual experimentation. But research activities
often involve exploring new territory where data is scarce or protected by
patents owned by other organizations. For example, while DTs could inform an
organization’s understanding of how a new topology may affect heavy construction
equipment or how a smart building may behave under unusual weather conditions,
there is limited data available about these new domains. ... DTs can add immense
value by reducing costs and the time it takes to develop new processes, but data
to develop these models is limited given that the work explores new territory.
Further, data-sharing across the supply chain is sharply limited due to extreme
sensitivity about intellectual property.
Leveraging AI for enhanced crime scene investigation

Importantly, as crimes are committed or solved, the algorithms and software
based on them become more sophisticated. Interestingly, these algorithms use
information obtained from various sources without any human intervention,
reducing the chances of bias or error. With the increasing use of mobile phones
and the internet, information is flooding in the form of photos, videos, audios,
emails, letters, newspaper reports, speeches, social media posts, locations, and
more. Various AI & ML-based algorithms are used to quickly analyse this
data, perform mathematical transformations, draw inferences, and reach
conclusions. This makes it possible to predict the likelihood of crimes in a
very short time, which is almost impossible otherwise. A smart city-related
company in Israel called ‘Cortica’ has developed software that analyzes the
information obtained through CCTV. This software utilizes certain AI algorithms
to recognize the faces in a crowd, identify crowd behavior and movement, and
predict the likelihood and nature of a crime. Interestingly, these intelligent
algorithms make it possible to analyze several terabytes of video footage in
minimal time and make quite precise inferences.
There are many reasons why companies struggle to exploit generative AI

Some qualitative remarks by executives interviewed revealed more detail on where
that lack of preparedness lies. For example, a former vice president of data and
intelligence for a media company told Rowan and team that the "biggest scaling
challenge" for the company "was really the amount of data that we had access to
and the lack of proper data management maturity." The executive continued:
"There was no formal data catalog. There was no formal metadata and labeling of
data points across the enterprise. We could go only as fast as we could label
the data." ... Uncertainty about novel regulations is also causing companies to
pause and think, Rowan and team stated in the report: "Organizations were
exceedingly uncertain about the regulatory environment that may exist in the
future (depending on the countries they operate in)." In response to both
concerns, companies are pursuing a variety of strategies, Rowan and team found.
These strategies include: "shut off access to specific Generative AI tools for
staff"; "put in place guidelines to prevent staff from entering organizational
data into public LLMs"; and "build walled gardens in private clouds with
safeguards to prevent data leakage into the public cloud."
The role of behavioral biometrics in a world of growing cyberthreats

Behavioral biometrics might be an evolving form of biometric technology, but its
foundations are already quite well established. For retail and ecommerce, for
example, the lines blur slightly between the terms, ‘behavioral biometrics’ and
‘risk-based authentication’. Behavior in this sense isn’t just how people
interact with their device, but the location they’re ordering from and to, or
the time zone and time of day they’re looking to make a purchase. The extent of
risk rises up and down relative to what is deemed ‘typical behavior’ in the
broader sense and for that individual transaction. ‘Risk’ refers to the degree
of confidence in authentication accuracy and will be key to the rise of
behavioral biometrics in other industries too, including healthcare and banking
where it is already being deployed to varying extents. It is more about the use
case and whether the risk posed is suitable for passive authentication in these
cases. In healthcare, for example, passive authentication wouldn’t be sufficient
to access patient databases, but once logged in, it could help confirm that the
same user is still active or online. ... Aside from the securitization element,
behavioral biometrics can also enable improved personalization and marketing
strategies.
Data center sustainability is no longer optional
A recent empirical investigation conducted by the Borderstep Institute, in
collaboration with the EU, revealed that digital technologies already account
for approximately five-nine percent of global electricity consumption and
carbon emissions, a number expected to increase as the demand for compute
power, driven by the rise of generative artificial intelligence (gen AI) and
foundation models, continues to grow. ... Databases are a significant
contributor to data center workloads. They are critical for storing, managing,
and retrieving large volumes of data, are computationally intensive, and
significantly contribute to the overall energy consumption of data centers on
thousands of database instances. Therefore, artificial intelligence database
tuning will be central to any sustainability strategy to increase efficiency.
... Artificial intelligence database tuning offers a revolutionary approach to
database management, enabling businesses to achieve high database performance
while minimizing their environmental impact. By observing real-time data, AI
can identify more effective PostgreSQL configurations that minimize energy
usage.
Building an Accessible Future in the Private Sector

Just like the public sector must make its services accessible to all groups,
so must the private sector. Luckily, several regulations make accessibility
a legal requirement for the private sector. The most notable is the
Americans with Disabilities Act (ADA), a federal law passed in 1990 to
prohibit discrimination against people with disabilities in many areas of
public life. Title III of the ADA considers websites "public accommodations"
and mandates that people with disabilities have equal access. However, true
digital accessibility in the modern age needs to go further to ensure all
digital products — websites, kiosks, mobile, and web applications — are
equally accessible to people with disabilities. ... Companies leading the
charge on accessibility are viewed as socially responsible and inclusive,
attributes that matter to this generation of consumers. Organizations that
value cultivating relationships with diverse customer groups often
experience stronger customer loyalty. Brands like Apple and Microsoft are
shining examples and have long been praised for providing inclusive
technology and experiences.
How to ensure cybersecurity strategies align with the company’s risk tolerance

One way for CISOs to align cybersecurity strategies with organizational risk
tolerance is strategic involvement across the organization. “By forming risk
committees and engaging in business discussions, CISOs can better understand
and address the risks associated with new technologies and initiatives, and
support the organization’s overall strategy,” Carmichael says. An
information security committee is vital to this mission, according to Carl
Grifka, MD of SingerLewak LLP, an advisory firm that specializes in risk and
cybersecurity. “There needs to be a regular assessment of not just the
cybersecurity environment, but also the risk tolerance and risk appetite,
which is going to drive the controls that we’re going to put in place,”
Grifka tells CSO. The committee operates as a cross-functional team that
brings together different members of the business, including the executive,
IT, security and maybe even a board representative on a more regular basis.
Organizations low on the maturity level probably need to meet every couple
of weeks, especially if they’re in a remediation phase and working to reduce
gaps in the security posture.
Quote for the day:
"Those who have succeeded at
anything and don’t mention luck are kidding themselves." --
Larry King
No comments:
Post a Comment