AI Demands More Than Just Technical Skills From Developers

Unlike in the past, when developers took instructions from a team lead and
executed tasks as individual contributors, now they’re outsourcing
problem-solving and code generation to AI tools and models. By partnering with
GenAI to solve complex problems, developers who were once individual
contributors are now becoming team leads in their own right. This new workflow
requires developers to elevate their critical-thinking skills and empathy for
end-users. No longer can they afford to operate with a superficial
understanding of the task at hand. Now, it’s paramount that developers
understand the why that is driving their initiative so that they can lead
their AI counterparts to the most desirable outcomes. ... Developers are now
co-creating IP. Who owns the IP? Does the prompt engineer? Does the GenAI
tool? If developers write code with a certain tool, do they own that code? In
an industry where tool sets are moving so quickly, it varies based on what
tool you’re using, what version of the tool, and what different tools within
certain vendors even have different rules. Intellectual property rights are
evolving.
Embracing Neurodiversity in IT Workplace to Bridge Talent Gaps

To accommodate neurodiversity effectively, organizations must adopt a
multifaceted approach. This includes providing tailored support and resources
to neurodiverse employees, such as flexible work arrangements, assistive
technologies, and specialized training programs. Additionally, fostering open
communication and creating a supportive network of colleagues and mentors can
help neurodiverse individuals feel valued and empowered to contribute their
unique insights and perspectives. ... The first step, according to Leantime
CEO and co-founder Gloria Folaron, is to create a cultural expectation of
self-awareness — from leadership to human resources. "The self-awareness can
extend across any biases you might have, relationships, or negative
experiences or reactions that exist inside. It's a self-checking mechanism,"
she said. The second benefit of this is that, for many neurodivergent
individuals, they have not been well-supported in the past — they've been
forced to create their own systems to fit into more traditional work
environments. By promoting even employee-level self-awareness, they become
empowered to start thinking about their own needs.
Ransomware recovery: 8 steps to successfully restore from backup

Use either physical write-once-read-many (WORM) technology or virtual
equivalents that allow data to be written but not changed. This does increase
the cost of backups since it requires substantially more storage. Some backup
technologies only save changed and updated files or use other deduplication
technology to keep from having multiple copies of the same thing in the
archive. ... In addition to keeping the backup files themselves safe from
attackers, companies should also ensure that their data catalogs are safe.
“Most of the sophisticated ransomware attacks target the backup catalog and
not the actual backup media, the backup tapes or disks, as most people think,”
says Amr Ahmed, EY America’s infrastructure and service resiliency leader.
This catalog contains all the metadata for the backups, the index, the bar
codes of the tapes, the full paths to data content on disks, and so on. “Your
backup media will be unusable without the catalog,” Ahmed says. Restoring
without one would be extremely hard or impractical. Enterprises need to ensure
that they have in place a backup solution that includes protections for the
backup catalog, such as an air gap.
Complying with PCI DSS requirements by 2025
Perhaps one of the most significant changes in terms of preventing e-commerce
fraud is the requirement to deploy change-and-tamper-detection mechanisms to
alert for unauthorized modifications to the HTTP headers and the contents of
payment pages as received by the consumer browser (11.6.1). Most
e-commerce-related cardholder data (CHD) theft comes from the abuse of
JavaScript used within online stores (otherwise known as web-based skimming).
Recent research has shown that most website payment pages have 100 different
scripts, some of which come from the merchant itself and some from third
parties, and any one of these scripts can potentially be altered to harvest
cardholder data. Equally, this could be the payment page of a payment service
provider (PSP) which a merchant redirects to, or uses a PSP generated inline
frame (iframe), making this an issue that is also relevant to PSPs. The ideal
scenario is to reduce this risk by knowing what is in use, what is authorized
and has not been altered, which is the principle aim of requirement 6.4.3.
This mandates the inventory of scripts, their authorization, evidence that
they are necessary and have been validated.
Inside CISA's Unprecedented Election Security Mission

Despite ongoing efforts by foreign adversaries to influence U.S. elections,
attempts to subvert the vote have been largely unsuccessful in past elections.
CISA's continued expansion of advanced threat detection and response
strategies in 2016 and 2020 played a significant role in thwarting attempts by
Russia and others to compromise the integrity of the electoral process. The
agency has recently issued warnings about "increasingly aggressive Iranian
activity during this election cycle," including reported activities to
compromise former President Donald Trump's campaign. The Department of
Homeland Security designated election infrastructure as a subset of the
government facilities sector in 2017, further recognizing the vast networks of
voter registration databases, information technology systems, polling places
and voting systems as critical infrastructure. ... The agency over the last
six years has rolled out a wide range of no-cost voluntary services and
resources aimed at reducing risks to election infrastructure, including
vulnerability scanning, physical security assessments and supporting the
nationwide adoption of .gov domains, which experts say enhance trust by
ensuring that election information is verified and comes from official,
credible sources.
The Gen Z Guide to Getting Ahead at Work

As a young person entering the workplace with new ideas and fresh eyes and
perspectives, you have unique value, experts said. Don't be shy to share your
thoughts. You might know something others don't. That could look like sharing
tools or shortcuts you know within apps, ideas or stories about how you've
solved problems in the past, Paaras said. You might have valuable experience
related to a particular topic or insight into how other people your age see
things. Or you might be able to spot the inefficiency or error of how things
are regularly done. "You're seeing things for the first time, and you can
highlight that," Abrahams said. "Focus on the value you bring." ... Set time
aside for chatting, by video or in person, with your colleagues and
supervisor. Building good relationships can help foster people's trust and
willingness to collaborate with you. It also could be a differentiator in your
career advancement. "Your presence needs to be felt by others," Wilk said.
Seek out one-on-one meetings and casual conversations. Be ready with thoughts,
questions and goals for the conversation, Wilk said. When in doubt, remember
people love to talk about themselves, she added. Ask them about their career
or experience on the job.
Unified Data: The Missing Piece to the AI Puzzle
“A unified data strategy can significantly reduce the time data scientists
spend on accessing, re-formatting, or creating data, thereby improving their
effectiveness in developing AI models,” Francis says. Yaad Oren, managing
director of SAP Labs US and global head of SAP BTP innovation, explains that
incorporating AI across an organization is not possible without trusted and
governed data. “A unified data strategy simplifies the data landscape,
maintains data context and ensures accurate training of AI models,” he says.
This leads to more effective AI deployments and allows customers to harness
data to drive deeper insights, faster growth, and more efficiency. “A unified
date architecture is crucial for creating a holistic view of business
operations and avoiding the ramifications of flawed AI,” he adds. By bringing
together disparate data from across the business, a data architecture ensures
data context is kept intact, providing a picture of how the data was
generated, where it resides, when it was created, and who it relates to. “A
strategy that incorporates a data architecture empowers users to access and
use data in real time, creating a single source of truth for decision making,
and automating data management processes,” Oren explains.
The Next Business Differentiator: 3 Trends Defining The GenAI Market
Different industries have distinct needs and like with cloud, standardized or
general GenAI models and services can’t support the specialized requirements
of specific industries. This is especially true for regulated industries that
have stringent governance, risk and compliance standards — industry or
domain-specific GenAI models will help organizations comply with regulations
and compliance standards, ensuring data security and ethical considerations
are adhered to. ... The main reason for prioritizing responsible AI is to
mitigate bias. Mitigating bias is fundamental in delivering GenAI solutions
that have true market applicability and relevance. Ultimately, bias comes from
three areas; algorithms, data and humans. Bias from AI algorithms has
plummeted exponentially in the last decade. Today, algorithms are mostly
trustworthy and the biggest source of bias in AI comes from data and humans.
When it comes to data, bias exists because of a lack of quality and variety,
as well as often incomplete datasets used to train the algorithm. With humans,
there is an inherent lack of trust when it comes to AI, whether because of
reported threats to people’s livelihoods or due to AI hallucinating certain
information.
Miniaturized brain-machine interface processes neural signals in real time

The MiBMI's small size and low power are key features, making the system
suitable for implantable applications. Its minimal invasiveness ensures safety
and practicality for use in clinical and real-life settings. It is also a
fully integrated system, meaning that the recording and processing are done on
two extremely small chips with a total area of 8mm2. This is the latest in a
new class of low-power BMI devices developed at Mahsa Shoaran's Integrated
Neurotechnologies Laboratory (INL) at EPFL's IEM and Neuro X institutes.
"MiBMI allows us to convert intricate neural activity into readable text with
high accuracy and low power consumption. This advancement brings us closer to
practical, implantable solutions that can significantly enhance communication
abilities for individuals with severe motor impairments," says Shoaran.
Brain-to-text conversion involves decoding neural signals generated when a
person imagines writing letters or words. In this process, electrodes
implanted in the brain record neural activity associated with the motor
actions of handwriting. The MiBMI chipset then processes these signals in real
time, translating the brain's intended hand movements into corresponding
digital text.
From Transparency to the Perils of Oversharing
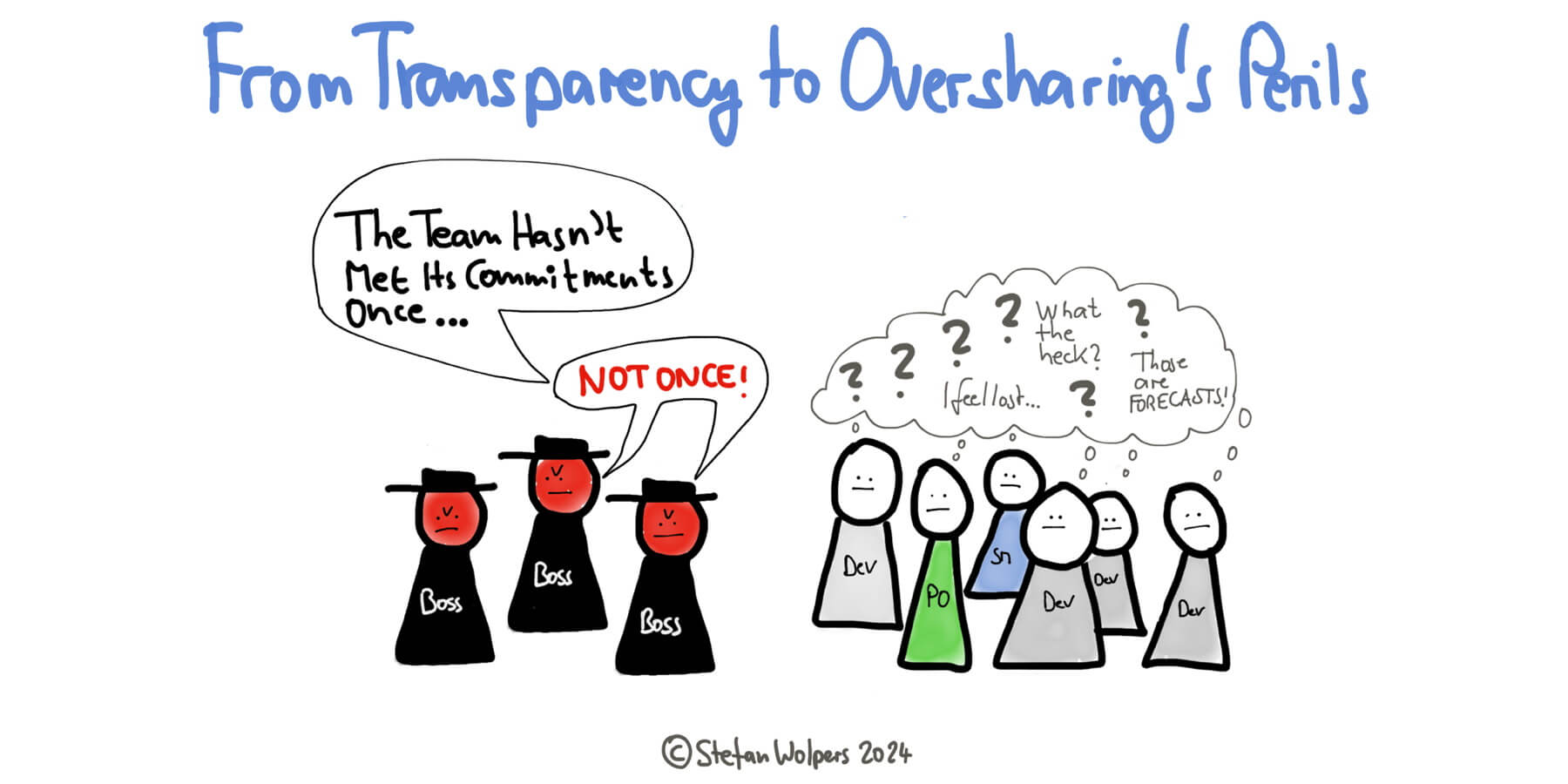
While openness fosters collaboration and trust, oversharing can inadvertently
lead to micromanagement, misinterpretation, and a loss of trust, undermining
the foundations of a healthy team dynamic. ... Transparency without trust can
create a blame culture where team members feel exposed to criticism for every
minor mistake. This effect can result in individuals trying to cover their
tracks or avoid taking risks, undermining the very principles of Agile.
Decision paralysis: When too much transparency leads to stakeholders or
managers second-guessing every team decision, it can create decision
paralysis. The team may feel that every move is under a microscope, leading
them to slow down or become overly cautious, eroding the trust that they can
make decisions independently. ... It’s not just the team that needs to manage
transparency effectively; stakeholders also need guidance on interpreting the
information they receive. Educating stakeholders on Agile practices and the
purpose of various metrics can prevent misinterpretation and unnecessary
interference. In other words, run workshops for stakeholders on interpreting
data and information from your team.
Quote for the day:
"Success is the progressive
realization of predetermined, worthwhile, personal goals." --
Paul J. Meyer
No comments:
Post a Comment