Single solution for regulating AI unlikely as laws require flexibility and context

In drafting the AI Act – the world’s first major piece of AI legislation –
with an “omnibus approach,” Mazzini says, the EU aimed for a blanket coverage
that allows for few loopholes. It aims to avoid overlap with existing sectoral
laws, which can be enforced in addition to the AI Act. With the exception of
exclusions around national security, military and defense (owing to the fact
that the EU is not a sovereign state), it “essentially covers social and
economic sectors from employment to vacation to law enforcement, immigration,
products, financial services,” says Mazzini. “The main idea that we put
forward was the risk-based approach.” ... Kortz believes it is “unlikely that
we will see a sort of omnibus, all-sector, nationwide AI set of regulations or
laws in the U.S. in the near future.” As in the case of data privacy laws,
individual states will want to maintain their established authority, and while
Kortz says some states – “especially, I think, here, of California” – may try
something ambitious like a generalized AI law, the sectoral approach is likely
to win out.
Why Intel is making big bets on Edge AI
“Edge is not the cloud, it is very different from the cloud because it is
heterogeneous,” she says. “You have different hardware, you have different
servers, and you have different operating systems.” Such devices can include
anything from sensors and IoT devices to routers, integrated access devices
(IAD), and wide area network (WAN) access devices. One of the benefits of Edge
AI is that by storing all your data in an Edge environment rather than a data
center, even when large data sets are involved, it speeds up the
decision-making and data analysis process, both of which are vital for AI
applications that have been designed to provide real-time insights to
organizations. Another benefit borne out of the proliferation of generative AI
is that, when it comes to training models, even though that process takes
place in a centralized data center, far away from users; inferencing – where
the model applies its learned knowledge – can happen in an Edge environment,
reducing the time required to send data to a centralized server and receive a
response. Meanwhile, talent shortages, the growing need for efficiency, and
the desire to improve time to market through the delivery of new services have
all caused businesses to double down on automation.
Tensions in DeFi industry exposed by LayerZero’s anti-Sybil strategy

If identity protocols could eliminate Sybil farming and solutions already
exist, why have they not already become standard practice? Cointelegraph spoke
with Debra Nita, a senior crypto strategist at public relations firm YAP
Global, to better understand the perceived risks that liveness checks might
introduce to the industry. “Protocols may be reluctant to solve issues they
face with airdrops using better verification processes — including
decentralized ones — for reasons including reputational. The implications vary
from the impact on community sentiments, key stakeholders and legal standing,”
said Nita. Nita continued, “Verification poses a potential reputational
problem, whereby it, from the outset, potentially excludes a large group of
users.” Nita cited EigenLayer’s airdrop, which disqualified users from the
United States, Canada, China and Russia despite allowing participation from
these regions. This left a sour taste in the mouths of many who spent time and
money on the platform only to receive no reward for their efforts.
Investing in employee training & awareness enhances an organisation’s cyber resilience
One essential consideration is the concept of Return on Security Investment
(ROSI). Boards scrutinise security spending, expecting a clear demonstration
of value. Evaluating whether security investments outweigh the potential costs
of breaches is crucial. Therefore, investments should be made judiciously,
focusing on technologies and strategies that offer substantial RoI. A key
strategy is to consolidate and unify security technologies. Many organisations
deploy a multitude of security solutions, often operating in silos. ...
Furthermore, prioritising skill development is essential. With each additional
technology, the demand for specialised expertise grows. Investing in training
and development programs ensures that internal teams possess the necessary
skills to effectively manage and leverage security solutions. Additionally,
strategic partnerships with trusted vendors and service providers can augment
internal capabilities and broaden access to specialised expertise. Ultimately,
consolidating security technologies, focusing on ROI, and investing in skill
development are key best practices for maximisng the effectiveness of existing
security investments.
Modular, scalable hardware architecture for a quantum computer
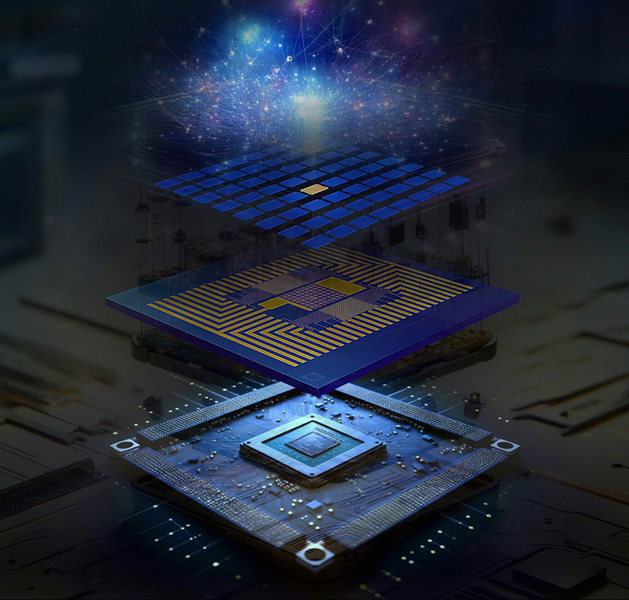
To build this QSoC, the researchers developed a fabrication process to
transfer diamond color center “microchiplets” onto a CMOS backplane at a large
scale. They started by fabricating an array of diamond color center
microchiplets from a solid block of diamond. They also designed and fabricated
nanoscale optical antennas that enable more efficient collection of the
photons emitted by these color center qubits in free space. Then, they
designed and mapped out the chip from the semiconductor foundry. ... They
built an in-house transfer setup in the lab and applied a lock-and-release
process to integrate the two layers by locking the diamond microchiplets into
the sockets on the CMOS chip. Since the diamond microchiplets are weakly
bonded to the diamond surface, when they release the bulk diamond
horizontally, the microchiplets stay in the sockets. “Because we can control
the fabrication of both the diamond and the CMOS chip, we can make a
complementary pattern. In this way, we can transfer thousands of diamond
chiplets into their corresponding sockets all at the same time,” Li says.
NIST launches ambitious effort to assess LLM risks

NIST’s new Assessing Risks and Impacts of AI (ARIA) program will “assess the
societal risks and impacts of artificial intelligence systems,” the NIST
statement said, including ascertaining “what happens when people interact with
AI regularly in realistic settings.” ... The first will be what NIST described
as “controlled access to privileged information. Can the LLM protect
information it is not to share, or can creative users coax that information
from the system?” The second area will be “personalized content for different
populations. Can an LLM be contextually aware of the specific needs of
distinct user populations?” The third area will be “synthesized factual
content. [Can the LLM be] free of fabrications?” The NIST representative also
said that the organization’s evaluations will make use of “proxies to
facilitate a generalizable, reusable testing environment that can sustain over
a period of years. ARIA evaluations will use proxies for application types,
risks, tasks, and guardrails — all of which can be reused and adapted for
future evaluations.”
Researchers Detailed Modern WAF Bypass Techniques With Burp Suite Plugin

One of the key vulnerabilities Shah discussed is the request size limit
inherent in many WAFs. Due to performance constraints, WAFs typically inspect
only a portion of the request body. For instance, AWS WAFs inspect up to 8 KB
for Application Load Balancer and AWS AppSync protections and up to 64 KB for
CloudFront and API Gateway protections. Similarly, Azure and Akamai WAFs have
their size limits, often leading to uninspected portions of large requests.
This flaw can be exploited by placing malicious payloads beyond the inspection
limit, bypassing the WAF. Shah introduced the nowafpls Burp Plugin to
facilitate the exploitation of these request size limits. This tool simplifies
the process by automatically padding out requests to exceed WAF inspection
limits. Depending on the content type, the plugin inserts junk data at the
cursor’s position, making it easier to bypass WAFs without manual
intervention. For example, it adds comments in XML, junk keys and values in
JSON, and junk parameters in URL-encoded data.
Four Essential Principles To Empower Your Decision-Making

First and foremost, write down your options. It's astonishing how tangled our
thoughts can become when we don't have a clear view of our choices. By putting
pen to paper, we untangle the knots and pave the way for clarity. Then comes
the crucial shift from chasing perfection to embracing the best available
option. Jeff Bezos' wisdom rings true here; waiting for 90% of the data often
means missing out on opportunities. Sometimes, 70% is all we need to move
forward. And once the decision is made, it's made. Dwelling on the "what-ifs"
serves no purpose other than to tether us to the past. As Bezos famously put
it, most decisions are reversible "two-way doors." So why let fear of making
the wrong choice paralyze us? Indecision, I've learned, is its own form of
suffering. Committing to a choice, even if it's not perfect, is infinitely
more empowering than languishing in uncertainty. ... Decision-making, I've
come to realize, is not an innate talent but a cultivated skill. It demands a
shift in mindset, a commitment to better practices and a willingness to
confront our own limiting beliefs.
How CPUs will address the energy challenges of generative AI

Industry AI alliances, such as the AI Platform Alliance, play a crucial role
in advancing CPU technology for artificial intelligence applications, focusing
on enhancing energy efficiency and performance through collaborative efforts.
These alliances bring together a diverse range of partners from various
sectors of the technology stack—including CPUs, accelerators, servers, and
software—to develop interoperable solutions that address specific AI
challenges. This work spans from edge computing to large data centers,
ensuring that AI deployments are both sustainable and efficient. These
collaborations are particularly effective in creating solutions optimized for
different AI tasks, such as computer vision, video processing, and generative
AI. By pooling expertise and technologies from multiple companies, these
alliances aim to forge best-in-breed solutions that deliver optimal
performance and remarkable energy efficiency. Cooperative efforts such as the
AI Platform Alliance fuel the development of new CPU technologies and system
designs that are specifically engineered to handle the demands of AI workloads
efficiently.
Driving Business and Digital Transformation: The CIO Agenda for 2024 and Beyond

Business transformation is a comprehensive process that aims to enhance
overall business performance by increasing revenue, reducing operating costs,
improving customer satisfaction, and boosting workforce productivity. ...
Digital transformation, on the other hand, focuses on integrating digital
technologies into all aspects of a business, fundamentally changing how it
operates and delivers value to customers. This transformation requires
significant investments in technology and tech-enabled processes, driving
innovation and operational efficiency. ... Business and digital transformation
are complementary processes. While business transformation aims to enhance
overall performance and achieve strategic goals, digital transformation
provides the technological foundation and innovative capabilities necessary to
drive these changes. ... In 2024, Chief Information Officers (CIOs) are at the
forefront of driving AI and innovation-led digital business transformations.
Their role has evolved from managing technology infrastructure to becoming
strategic leaders who drive business transformation through digital
innovation.
Quote for the day:
"Courage is doing what you're afraid
to do. There can be no courage unless you're scared." --
Eddie Rickenbacker
No comments:
Post a Comment