Thinking beyond BitLocker: Managing encryption across Microsoft services

There is more than BitLocker in an operating system that will allow control over
encryption settings. Often you are mandated in a firm to ensure that all
sensitive data at rest is kept secure. Older operating systems may not natively
provide the necessary internal encryption of application-layer encryption.
Specific group policies are included in Windows that target how passwords are
stored. A case in point is the setting “Store passwords using reversible
encryption”. This policy, if enabled, would lower the security posture of your
firm. Older protocols being used in such locations as web servers and IIS may
mandate that you enable these settings. Thus, you may want to audit your web
servers to see if any developer mandate has indicated that you must have lesser
protections in place. For example, if you use challenge handshake authentication
protocol (CHAP) through remote access or internet authentication services (IAS),
you must enable this policy setting. CHAP is an authentication protocol used by
remote access and network connections. Digest authentication in internet
information services (IIS) also requires that you enable this policy
setting.
EU’s use of Microsoft 365 found to breach data protection rules

More broadly, the EDPS’ corrective measures require the Commission to fix its
contracts with Microsoft — to ensure they contain the necessary contractual
provisions, organizational measures and/or technical measures to ensure personal
data is only collected for explicit and specified purposes; and “sufficiently
determined” in relation to the purposes for which they are processed. Data must
also only be processed by Microsoft or its affiliates or sub-processors “on the
Commission’s documented instructions”, per the order — unless it takes place
within the region and processing is for a purpose that complies with EU or
Member State law; or, if outside the region to be processed for another purpose
under third-country law there must be essentially equivalent protection applied.
The contracts must also ensure there is no further processing of data — i.e.
uses beyond the original purpose for which data is collected. The EDPS found the
Commission infringed the “purpose limitation” principle of applicable data
protection rules by failing to sufficiently determine the types of personal data
collected under the licensing agreement it concluded with Microsoft Ireland,
meaning it was unable to ensure these were specific and explicit.
State Dept-backed report provides action plan to avoid catastrophic AI risks

The report focuses on two key risks: weaponization and loss of control.
Weaponization includes risks such as AI systems that autonomously discover
zero-day vulnerabilities, AI-powered disinformation campaigns and bioweapon
design. Zero-day vulnerabilities are unknown or unmitigated vulnerabilities in a
computer system that an attacker can use in a cyberattack. While there is still
no AI system that can fully accomplish such attacks, there are early signs of
progress on these fronts. Future generations of AI might be able to carry out
such attacks. “As a result, the proliferation of such models – and indeed, even
access to them – could be extremely dangerous without effective measures to
monitor and control their outputs,” the report warns. Loss of control suggests
that “as advanced AI approaches AGI-like levels of human- and superhuman general
capability, it may become effectively uncontrollable.” An uncontrolled AI system
might develop power-seeking behaviors such as preventing itself from being shut
off, establishing control over its environment, or engaging in deceptive
behavior to manipulate humans.
Threat Groups Rush to Exploit JetBrains’ TeamCity CI/CD Security Flaws
Most recently, researchers with cybersecurity vendor GuidePoint Security that
the operators behind the BianLian ransomware were exploiting the TeamCity
vulnerabilities, initially trying to execute their backdoor malware written in
the Go programming language. After failed attempts, the group turned to
living-of-the-land methods, using a PowerShell implementation of the backdoor,
which provided them with almost identical functionality, the researchers wrote
in a report. They detected the attack during an investigation of malicious
activity within a customer’s network. It was unclear which of the two
vulnerabilities the BianLian attackers exploited, they wrote. After leveraging a
vulnerable TeamCity instance to gain initial access, the bad actors were able to
create new users in the build server and executed malicious commands that
enabled them to move laterally through the network and run post-exploitation
activities. ... “The threat actor was detected in the environment after
attempting to conduct a Security Accounts Manager (SAM) credential dumping
technique, which alerted the victim’s VSOC, GuidePoint’s DFIR team, and
GuidePoint’s Threat Intelligence Team (GRIT) and initiated the in-depth review
of this PowerShell backdoor,” the researchers wrote.
How cookie deprecation, first-party data and privacy regulations are impacting the data landscape

While advertisers must focus on forging their paths forward in a cookieless
landscape, it’s worth considering what comes next for Google. As privacy
concerns dwindle with the deprecation of third-party cookies, there’s good
reason to believe that antitrust concerns will grow regarding the industry
titan. The timing of Google’s deprecation of third-party cookies on Chrome,
coming years after Safari and Firefox made the same move, is telling. The simple
reality is that Google did not want to make this move until it could develop an
alternate approach that enabled the tracking, targeting and monetization of
logged-in Chrome users. Now that Google has had the time to secure its ad
revenue against any major disruptions, it will end the cookie’s reign. This move
will garner added scrutiny from regulators who have already set their antitrust
sights on Google in the past. With the deprecation of third-party cookies,
Google retains end-to-end control of a massive swath of the advertising
technology that powers the internet, and the company is going to be sharing less
and less of that power (in the form of data and insights) with its clients and
other parties.
Typosquatting Wave Shows No Signs of Abating

Typosquatting criminals are constantly refining their craft in what seems to be
a never-ending cat and mouse conflict. Several years ago, researchers discovered
the homograph ploy, which substitutes non-Roman characters that are hard to
distinguish when they appear on screen. ... In an Infoblox report from last
April entitled "A Deep3r Look at Lookal1ke Attacks," the report's authors stated
that "everyone is a potential target." "Cheap domain registration prices and the
ability to distribute large-scale attacks give actors the upper hand," they
wrote in the report. "Attackers have the advantage of scale, and while
techniques to identify malicious activity have improved over the years,
defenders struggle to keep pace." For instance, the report shows an increasing
sophistication in the use of typosquatting lures: not just for phishing or
simple fraud but also for more advanced schemes, such as combining websites with
fake social media accounts, using nameservers for major spear-phishing email
campaigns, setting up phony cryptocurrency trading sites, stealing multifactor
credentials and substituting legitimate open-source code with malicious to
infect unsuspecting developers.
Are private conversations truly private? A cybersecurity expert explains how end-to-end encryption protects you
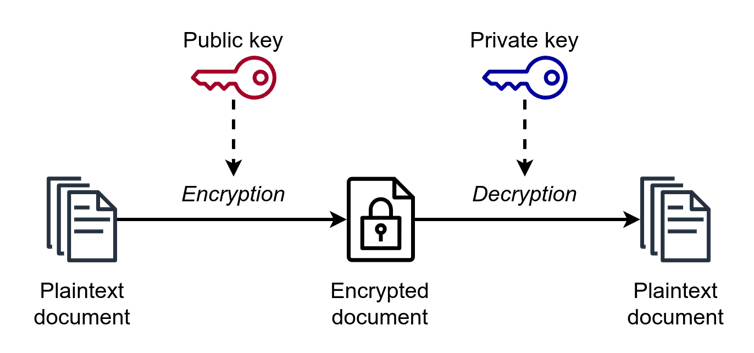
The effectiveness of end-to-end encryption in safeguarding privacy is a subject
of much debate. While it significantly enhances security, no system is entirely
foolproof. Skilled hackers with sufficient resources, especially those backed by
security agencies, can sometimes find ways around it. Additionally, end-to-end
encryption does not protect against threats posed by hacked devices or phishing
attacks, which can compromise the security of communications. The coming era of
quantum computing poses a potential risk to end-to-end encryption, because
quantum computers could theoretically break current encryption methods,
highlighting the need for continuous advancements in encryption technology.
Nevertheless, for the average user, end-to-end encryption offers a robust
defense against most forms of digital eavesdropping and cyberthreats. As you
navigate the evolving landscape of digital privacy, the question remains: What
steps should you take next to ensure the continued protection of your private
conversations in an increasingly interconnected world?
Tax-related scams escalate as filing deadline approaches

“[A] new scheme involves a mailing coming in a cardboard envelope from a
delivery service. The enclosed letter includes the IRS masthead with contact
information and a phone number that do not belong to the IRS and wording that
the notice is ‘in relation to your unclaimed refund’,” the agency noted. Another
scam involves phone calls: scammers, pretending to be IRS agents, call the
victims and try to convince them that they owe money. They often target recent
immigrants, sometimes contacting them in their native language, and threaten
them with arrest, deportation, or license suspension if they don’t pay. Some
additional tax-related scams the IRS is warning about: Tax identity theft –
Scammers use a person’s identity number to file a tax return or unemployment
compensation and claim refunds Phishing scams – Scammers send convincing emails
posing as the IRS to make victims disclose personal and financial information
Unethical tax return preparers – Individuals that pose as tax prepaprers
but don’t actually file tax returns on behalf of the tax payer despite getting
paid for the service. Or, if they do, they direct refunds into their own bank
account rather than the taxpayer’s account.
Why cyberattacks need more publicity, not less

Regulators worldwide have recognized this lack of transparency and are
tightening legislation to improve the disclosure of security incidents. New
rules from the U.S. Securities and Exchange Commission (SEC) require companies
to disclose a material cybersecurity incident publicly within four days of its
discovery. The European Parliament’s Cyber Resilience Act (CRA) is also seeking
to impose further reporting obligations regarding exploited vulnerabilities and
incidents. These tougher obligations will force more transparency, although
forward-thinking organizations are already championing the benefits of
disclosure for the wider community. Supporting the argument for openness stems
from a genuine fear of cyberattacks taking out the UK’s mission-critical
infrastructure, such as energy, communications, and hospitals. But there’s added
value to be gained, as visibility and accountability can be positive
differentiators for businesses. Clear disclosure and reporting procedures
demonstrate that an organization understands what’s required to maintain
operational resilience when under attack.
10 things I’d never do as an IT professional

Moving your own files instead of copying them immediately makes me feel uneasy.
This includes, for example, photos or videos from the camera or audio recordings
from a smartphone or audio recorder. If you move such files, which are usually
unique, you run the risk of losing them as soon as you move them. Although this
is very rare, it cannot be completely ruled out. But even if the moving process
goes smoothly: The data is then still only available once. If the hard drive in
the PC breaks, the data is gone. If I make a mistake and accidentally delete the
files, they are gone. These are risks that only arise if you start a move
operation instead of a copy operation. ... For years, I used external USB hard
drives to store my files. The folder structure on these hard drives was usually
identical. There were the folders “My Documents,” “Videos,” “Temp,” “Virtual
PCs,” and a few more. What’s more, all the hard drives were the same model,
which I had once bought generously on a good deal. Some of these disks even had
the same data carrier designation — namely “Data.” That wasn’t very clever,
because it made it too easy to mix them up. So I ended up confusing one of these
hard drives with another one at a late hour and formatted the wrong one.
AI-generated recipes won’t get you to Flavortown
:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/13292777/acastro_181017_1777_brain_ai_0001.jpg)
“There are gradients of what is fine and not, AI isn’t making recipe development
worse because there’s no guarantee that what it puts out works well,” Balingit
said. “But the nature of media is transient and unstable, so I’m worried that
there might be a point where publications might turn to an AI rather than recipe
developers or cooks.” Generative AI still occasionally hallucinates and makes up
things that are physically impossible to do, as many companies found out the
hard way. Grocery delivery platform Instacart partnered with OpenAI, which runs
ChatGPT, for recipe images. The results ranged from hot dogs with the interior
of a tomato to a salmon Caesar salad that somehow created a lemon-lettuce
hybrid. Proportions were off — as The Washington Post pointed out, the steak
size in Instacart’s recipe easily feeds more people than planned. BuzzFeed also
came out with an AI tool that recommended recipes from its Tasty brand. ... That
explained why I instantly felt the need to double-check the recipes from
chatbots. AI models can still hallucinate and wildly misjudge how the volumes of
ingredients impact taste. Google’s chatbot, for example, inexplicably doubled
the eggs, which made the cake moist but also dense and gummy in a way that I
didn’t like.
Quote for the day:
“Expect the best. Prepare for the worst.
Capitalize on what comes.” -- Zig Ziglar
No comments:
Post a Comment