IT’s Waste Management Job With Software Applications

Shelfware is precisely that: applications and systems that sit on the physical or virtual shelf because nobody uses them. They could even be installed, where they take up storage space. Shelfware doesn’t start out that way. Someone at some point purchased that software because they thought it would address a company's need. Then, through either disappointment with the product or product obsolescence, they find out that the product doesn’t meet their need. There will always be well-intentioned software failures like this in companies, but if IT doesn’t sweep out the debris by getting rid of the software and cancelling contracts, shelfware will continue to show up as an expense in the IT budget. ... There are few more painful software installation issues than system integration, especially when vendors tell you that they have interfaces to your systems, and you discover major flaws in the interfaces that you must manually correct. Complicated integrations set back projects and are difficult to explain to management. If an integration becomes too difficult, the software likely gets dumped, but someone forgets to dump it from the budget.
Securing open source software: Whose job is it, anyway?
"We at CISA are particularly focused on OSS security because, as everyone here knows, the vast majority of our critical infrastructure relies on open source software," Easterly declared in her keynote. "And while the Log4Shell vulnerability might have been a big wakeup call for many in government, it demonstrated what this community has known and warned about for years: due to its widespread deployment, the exploitation of OSS vulnerabilities becomes more impactful," she added. In addition to holding software developers liable for selling vulnerable products, Easterly has also repeatedly called on vendors to support open source software security – either via money or dedicated developers to help maintain and secure the open source code that ends up in their commercial projects. ... Easterly repeated this call to action at this week's Summit, citing a Harvard study [PDF] that estimates open source software has generated more than $8 trillion dollars in value globally. "I do have one ask of all the software manufacturers," Easterly noted – though it ended up being technically two asks. "We need companies to be both responsible consumers of and sustainable contributors to the open software they use," she continued.
Anatomy of a BlackCat Attack Through the Eyes of Incident Response

“When responding to an incident, one of the areas that should be looked at is
‘What will the attacker understand and how will they react?’ – this is one of
the areas that makes IR work for professionals,” Elboim explained. “On one hand,
response activities should do the maximum to contain and remediate, but on the
other, they should be done carefully so that the attacker will not know that
activity is taking place – or at least not fully understand the type and scope
of activities that are being done.” It was too late in this instance. “Cutting
the Internet connection is a severe action that was unavoidable in this specific
case, but there are many cases where we have taken a more careful approach and
planned our activities so that the attacker isn’t informed of our activities,
until we and the company we assist, are fully ready,” he added. The important
point here, however, is that the victim’s senior management was brave enough to
take that severe action. By now, the attackers had succeeded in exfiltrating
data, but had not yet commenced encryption. That encryption was blocked. It did
not prevent BlackCat from attempting to extort the victim over the stolen data,
and for the next three weeks the attacker attempted to do so.
The Hidden Cost of Using Managed Databases
As an engineer, nothing frustrates me more than being unable to solve an
engineering problem. To an extent, databases can be seen as a black box. Most
database users use them as a place to store and retrieve data. They don’t
necessarily bother about what’s going on all the time. Still, when something
malfunctions, the users are at the mercy of whatever tool the provider supplied
to troubleshoot them. Providers generally run databases on top of some
virtualization (Virtual Machines, Containers) and are sometimes even operated by
an orchestrator (e.g., K8s). Also, they don’t necessarily provide complete
access to the server where the database is running. The multiple layers of
abstraction don’t make the situation any easier. While providers don’t offer
full access to prevent users from "shooting themselves in the foot," an advanced
user will likely need elevated permissions to understand what’s happening on
different stacks and fix the underlying problem. This is the primary factor
influencing my choice to self-host software, aiming for maximum control. This
could involve hosting on my local data center or utilizing foundational elements
like Virtual Machines and Object Storage, allowing me to create and manage my
services.
How To Improve Your DevOps Workflow
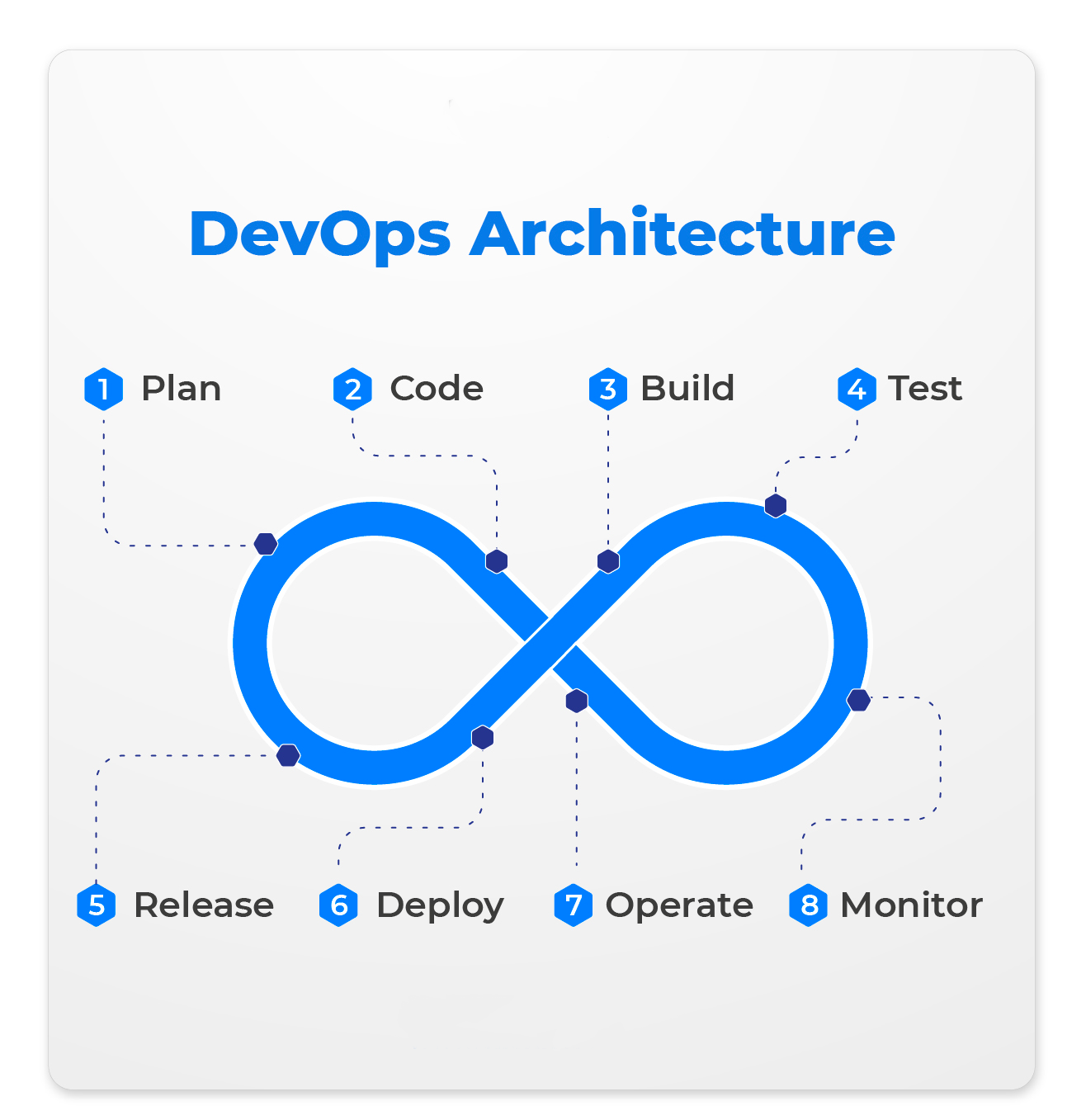
When you think about DevOps, the first thing that comes to mind is
collaboration. Because the whole methodology is based on this principle. We
know the development and operations teams were originally separated, and there
was a huge gap between their activities. DevOps came to transform this,
advocating for close collaboration and constant communication between these
departments throughout the complete software development life cycle. This
increases the visibility and ownership of each team member while also building
a space where every stage can be supervised and improved to deliver better
results. ... The second thought we all have when asked about DevOps?
Automation. This is also a main principle of the DevOps methodology, as it
accelerates time-to-market, eases tasks that were usually manually completed,
and quickly enhances the process. Software development teams can be more
productive while building, testing, releasing code faster, and catching errors
to fix them in record time. ... What organizations love about DevOps is its
human approach. It prioritizes collaborators, their needs, and their
potential.
How to Successfully Implement AI into Your Business — Overcoming Challenges and Building a Future-Ready Team
Creating a future-ready team involves the strategic use of AI technologies to
enhance human capabilities. Organizations need to focus on upskilling their
employees as the AI landscape continues changing and ensure a workforce that
is digitally literate to be able to interact with intelligent systems. It is
critical to develop a culture of continuous learning and flexibility. In
identifying the tasks that are best to be automated and powered by AI, teams
can concentrate on complex problem-solving and creativity. The collaboration
between human workers and AI algorithms increases productivity and innovation.
In addition, promoting diversity and inclusivity in AI development helps to
ensure a variety of opinions that will lead to ethical and unbiased solutions.
... In addition to technological integration, creating a future-ready team
requires not only embracing the concept of lifelong learning but also an
attitude toward change and inclusivity. As the business world continues to
evolve in this ever-expanding technological environment, careful integration,
continuous adaptation and fostering human skills are vital for long-term
success and a balanced relationship between people and AI systems at work.
Data Management Predictions for 2024: Five Trends

In a data mesh context, business stakeholders will need to be able to define
and create data products and govern the data based on their domain needs. IT
will need to deploy the right infrastructure to enable business users to be
more self-sufficient. In this data-centric era, it is not enough to merely
package data attractively; organizations need to enhance entire end-user
experience. Echoing the best practices of e-commerce giants, contemporary data
platforms must offer features like personalized recommendations and popular
product highlights, while also building confidence through user endorsements
and data lineage visibility. ... GenAI will have a huge impact on data
management and result in tools and technologies that are more business
friendly. However, in an increasingly distributed data landscape, without the
ability to assure access to high quality, trusted data, a GenAI-enabled data
management infrastructure will be of little or no use. Organizations are
encountering several additional challenges as they attempt to implement GenAI
and large language models (LLMs), including issues with data quality,
governance, ethical compliance, and cost management.
Risk mitigation should address threat, vulnerability and consequence
/dq/media/post_banners/wp-content/uploads/2023/08/cyber-4610993-1280.jpg)
To devise effective risk mitigation strategies, it’s critical to assess all
three factors: threat, vulnerability, and consequence. If you focus only on
threats and vulnerabilities without understanding the consequences, you might
end up with risk assessment and mitigation gaps. CISOs must be able to
identify and assess potential threats, including those from both external and
internal sources. They must also comprehensively understand the organization's
assets and vulnerabilities, including the IT infrastructure, data systems, and
employee workforce. And they must be able to quantify the potential
consequences of a cyberattack, including financial losses, reputational
damage, and operational disruptions. ... Effective cyber-risk management needs
to involve the entire organization, particularly as everyone has a role to
play in identifying and managing the consequences of a cyber incident. CISOs
must effectively communicate cyber risks and its implications to all of the
employees at the company and give them the required training and resources
they need to protect the organization.
Researchers Develop Self-Replicating Malware “Morris II” Exploiting GenAI

GenAI attacks of this type have not yet been seen in the wild, and the
researchers demonstrated this approach under lab conditions. But security
researchers have been warning that state-sponsored hackers have been observed
experimenting with the offensive capability of ChatGPT and similar tools since
they became available. The self-replicating malware functions by identifying
prompts that will generate output that serves as a further prompt, in a
process that is not very different from how common buffer overflow attacks
operate. The approach also exploits a feature of GenAI called
“retrieval-augmented generation” (RAG), a method by which LLMs can be prompted
to retrieve data that exists outside of their training model. Ultimately the
researchers blamed poor design for opening the door to this approach, urging
GenAI companies to go back to the drawing board and improve their
architecture. GenAI email assistants of the sort that were attacked here are
already a popular type of automation and productivity tool, performing
features that range from automatically forwarding incoming emails to relevant
parties to generating replies.
Microsoft says Russian hackers stole source code after spying on its executives
:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/24347780/STK095_Microsoft_04.jpg)
It’s not clear what source code was accessed, but Microsoft warns that the
Nobelium group, or “Midnight Blizzard,” as Microsoft refers to them, is now
attempting to use “secrets of different types it has found” to try to
further breach the software giant and potentially its customers. “Some of
these secrets were shared between customers and Microsoft in email, and as
we discover them in our exfiltrated email, we have been and are reaching out
to these customers to assist them in taking mitigating measures,” says
Microsoft. Nobelium initially accessed Microsoft’s systems through a
password spray attack last year. This type of attack is a brute-force
approach where hackers utilize a large dictionary of potential passwords
against accounts. Microsoft had configured a non-production test tenant
account without two-factor authentication enabled, allowing Nobelium to gain
access. “Across Microsoft, we have increased our security investments,
cross-enterprise coordination and mobilization, and have enhanced our
ability to defend ourselves and secure and harden our environment against
this advanced persistent threat,” says Microsoft.
Quote for the day:
"The best preparation for tomorrow
is doing your best today." -- H. Jackson Brown, Jr.
No comments:
Post a Comment