The SEC action against SolarWinds highlights how tough it can get for CISOs

The SEC has accused Brown of misleading investors by not disclosing "known risks" and not accurately representing the company’s cybersecurity measures during and before the 2020 Sunburst cyberattack that affected thousands of customers in government agencies and companies globally. ... The claimed failures, including not abiding by the statements that the company made on its website regarding their patterns and practices for developing their software as well as password policies internal to the company. The SEC complains in its filings that the company did not disclose cybersecurity risks independently from other risks, given SolarWinds' role and industry, nor pay extra risk attention to targeted attacks and the disclosure needs surrounding them. ... The SEC also indicated that SolarWinds did not limit administrative access to those who needed access. Too often in developer networks administrative rights are used too widely and not limited. Internal staff expressed concerns that user access would lead to losses of organizational assets and personal data.
Deriving Actionable Insights and ROI from AI

To increase the ROI of AI, large language models (LLMs) must ingest clean and high-quality data for accurate, meaningful insights. This is only possible by investing in data discovery and data classification solutions and processes. Organizations will also face growing AI-related security challenges in 2024. This will lead them to set up guardrails that protect corporate and customer data. Businesses must also consider that company-specific or proprietary data ingested by LLMs could put organizations at risk if company financials or other private information are replicated to a public AI engine and exposed. ... There are many opportunities for businesses to benefit from AI; however, there also needs to be a rapid evolution of data classification and data life cycle management before businesses will be able to derive the value they expect from AI. This is especially important if companies are trying to justify ROI from their AI investment. Sustainability took a back seat during the pandemic and long after the worst of it passed, as organizations made major adjustments to operations and tried to find their new (or old) normal.
Startup Oxide Computer puts the ‘cloud’ back in on-prem private clouds

Oxide's main mission is to put the "cloud" back in private cloud computing.
The company is built on the premise that you should be able to choose to rent
or own cloud capacity, depending on the workload, not losing the benefits of
cloud computing like elasticity when you choose the latter. To accomplish
this, the Oxide team set out to build an entirely new cloud hardware rack that
would deliver all of the advantages public cloud vendors enjoy, without
sacrificing on control, efficiency, and flexibility. Another issue that limits
private clouds is that many enterprises attempt to build their private clouds
on Kubernetes. The problem is that Kubernetes was not designed for
multitenancy, and, thus, it does not offer a true cloud experience. That's not
a knock on Kubernetes, but the container orchestration software is typically
deployed on top of bloated layers of software, adding complexity and making it
difficult to manage at scale. ... According to Oxide, this design allows
enterprises to be fully deployed within a few hours of unboxing the system,
versus what typically takes weeks or months using the "kit car" build of OEM
hardware.
We’re in a truly important phase of change due to the impact of artificial
intelligence. In fact, I believe people have been quite amazed at how good it
is. Even industry professionals have been quite surprised at how powerful it
is. But it comes with dangers, and I think that’s the important point I talked
about a few years ago and still find very important today; you really need to
understand how this works to use it effectively, because you still have to
understand that it works statistically, in the sense that it understands what
the most probable words are to follow the paragraphs it has already seen. ...
I think we will have to ask the question of whether we are developing a new
species, whether this is an evolution of what we are doing, or whether we are
going to have to consider a new hybrid species, which is probably the
perspective of integrating artificial intelligence into our own species. Elon
Musk is considering the idea with Neuralink. His response to the existential
threat of artificial intelligence is that no, we must become it, we must
integrate artificial intelligence and humans, which will generate new
philosophical, social, and legal dilemmas in the future.
Quantum-Computing Approach Uses Single Molecules As Qubits For First Time
Some of the first demonstrations of the basic principles of quantum computing,
in the late 1990s, used large numbers of molecules manipulated in a solution
inside a nuclear magnetic resonance machine. Since then, researchers have
developed a variety of other platforms for quantum computing, including
superconducting circuits and individual ions held in a vacuum. Each of these
objects is used as the fundamental unit of quantum information, or qubit — the
quantum equivalent of the bits in classical computers. In the past few years,
another strong contender has emerged, in which the qubits are made of neutral
atoms — as opposed to ions — trapped with highly focused laser-beam
‘tweezers’. Now, two separate teams have made early progress towards using
this approach with molecules instead of atoms. “Molecules have a bit more
complexity, which means they offer new ways to both encode quantum
information, and also new ways in which they can interact,” says Lawrence
Cheuk
DevOps and Automation
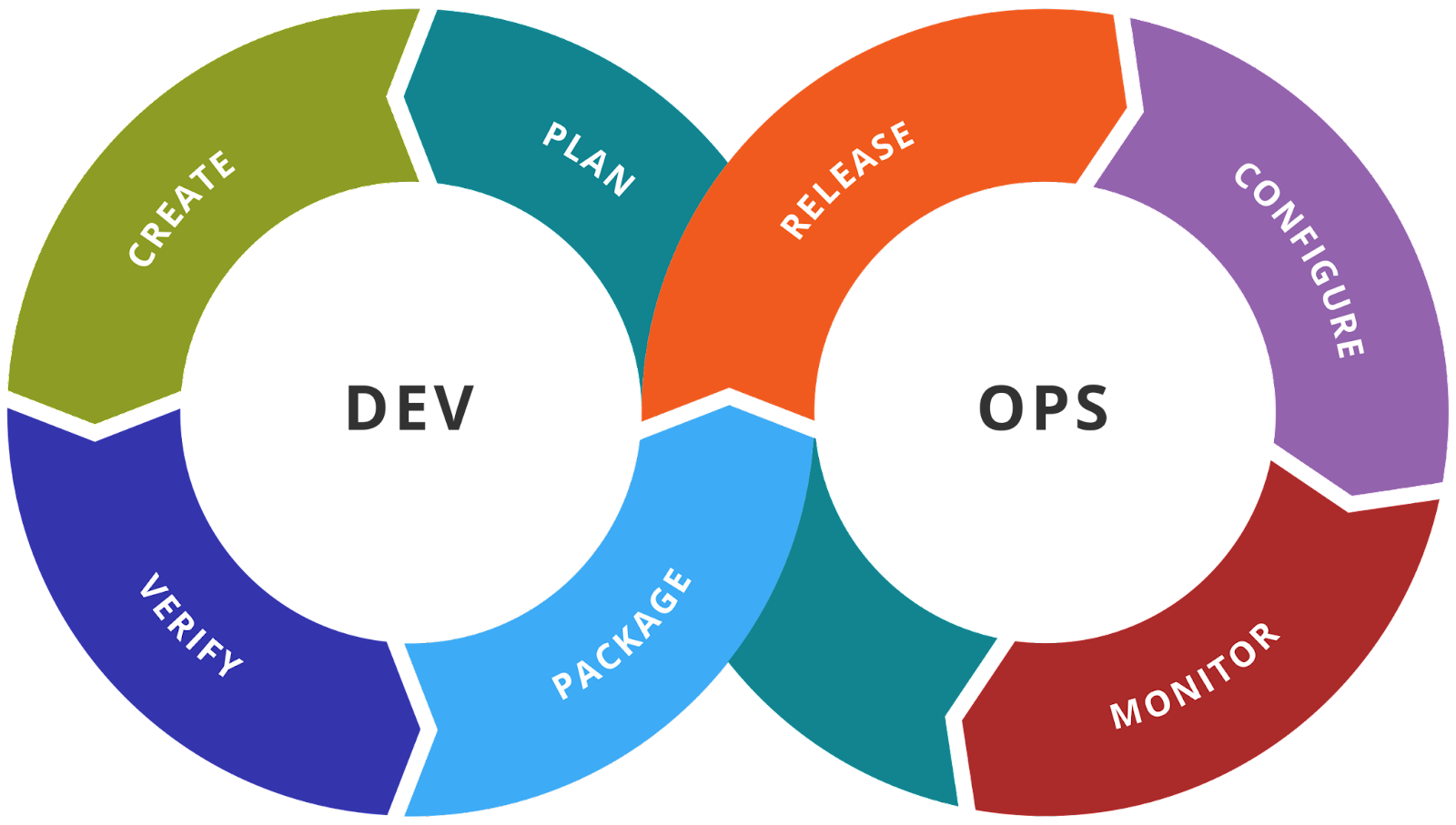
Continuous Integration (CI) and Continuous Deployment (CD) are critical
components of DevOps software development. CI is the practice of automating
the integration of code changes from multiple contributors into a single
software project. It is typically implemented in such a way that it triggers
an automated build with testing, with the goals of quickly detecting and
fixing bugs, improving software quality, and reducing release time. After the
build stage, CD extends CI by automatically deploying all code changes to a
testing and/or production environment. This means that, in addition to
automated testing, the release process is also automated, allowing for a more
efficient and streamlined path to delivering new features and updates to
users. Docker and Kubernetes are frequently used to improve efficiency and
consistency in CI/CD workflows. The code is first built into a Docker
container, which is then pushed to a registry in the CI stage. During the CD
stage, Kubernetes retrieves the Docker container from the registry and deploys
it to the appropriate environment, whether testing, staging, or
production.
Unveiling the 'Willingness Pyramid' across generations and cities

The 'Willingness Pyramid' stands as a compelling representation of the
shifting attitudes towards work models in bustling metropolises. At its core,
it underscores a marked inclination towards the "only office" work model, with
a notable emphasis on the younger, tech-savvy workforce in these urban hubs.
For the emerging generations of Late millennials and Gen Z, the physical
office environment is not merely a place of work but a dynamic space that
fosters productivity, innovation, and collaboration. The younger workforce's
enthusiastic embrace of the "only office" model is rooted in a confluence of
factors. Raised in the digital age, these individuals have grown up with
technology seamlessly integrated into their lives. As a result, they perceive
the physical office as a hub for face-to-face interactions, spontaneous idea
exchanges, and a breeding ground for innovation that cannot be fully
replicated in remote settings. The office, for them, is not just a workplace
but a social and creative nexus. This trend, however, exhibits a nuanced
dynamic as we traverse through different age groups within the same urban
landscapes.
Why FinOps Must Focus on Value, Not Just Cost

It’s not necessarily the fault of those teams. Rather, FinOps in its earliest
iterations has suffered from some of the same problems that plagued its
predecessors — namely, an approach to cost management that focuses on the “what”
— how much the bill says you spent, and only after it arrives — versus the
“why,” which should accurately reflect the business reasons for consuming cloud
resources in the first place, as well as the results those choices produced.
Moreover, FinOps, even while the name suggests tight collaboration, often still
relies on fragmented and retroactive processes and information, according to
Williams. ... Moving to a value-focused approach to FinOps is akin to the “shift
left” mindset that is increasingly popular in security and other IT domains that
have historically been dealt with via lagging indicators. Some organizations try
mandating discipline with regard to cloud usage — the “do this or else”
approach. “That never works,” Williams said. Instead, consumption policies and
technical guardrails need to be implemented before resources are ever
provisioned and deployed.
Researchers Unmask Sandman APT's Hidden Link to China-Based KEYPLUG Backdoor

"We did not observe concrete technical indicators confirming the involvement of
a shared vendor or digital quartermaster in the case of LuaDream and KEYPLUG,"
Aleksandar Milenkoski, senior threat researcher at SentinelLabs, told The Hacker
News. "However, given the observed indicators of shared development practices,
and overlaps in functionalities and design, we do not exclude that possibility.
Noteworthy is the prevalence of similar cases within the Chinese threat
landscape, indicating there could be established internal and/or external
channels for supplying malware to operational teams." "The order in which
LuaDream and KEYPLUG evaluate the configured protocol among HTTP, TCP,
WebSocket, and QUIC is the same: HTTP, TCP, WebSocket, and QUIC in that order,"
the researchers said. "The high-level execution flows of LuaDream and KEYPLUG
are very similar." The adoption of Lua is another sign that threat actors, both
nation-state aligned and cybercrime-focused, are increasingly setting their
sights on uncommon programming languages like DLang and Nim to evade detection
and persist in victim environments for extended periods of time.
The skills and traits of elite CTOs
Strategic thinking is essential for a CTO to align technology initiatives with
the overall business strategy, Kowsari says. “A successful CTO should be able to
set a clear technology vision, identify opportunities for innovation, and make
informed decisions that drive the company’s growth,” he says. Without a
strategic mindset, technology investments and initiatives might lack direction
and fail to contribute to the organization’s success, Kowsari says. The ability
to set and execute a vision is indeed a fundamental aspect of the CTO’s role,
Clemenson says. “This encompasses aspects such as design, funding, efficient
resource allocation, buy vs. build strategy, while simultaneously emphasizing
short- and long-term considerations,” he says. At the same time, CTOs must be
strong leaders. “CTOs are responsible for leading and managing technology
teams,” Kowsari says. “Strong leadership and team-building skills are vital.
Effective team management can lead to increased productivity, innovative
solutions, and the successful execution of technology projects. It also helps
retain top technical talent, which is essential in a competitive job market.”
Quote for the day:
"Don't be buffaloed by experts and
elites. Experts often possess more data than judgement." --
Colin Powell
No comments:
Post a Comment