If you want to make it big in tech, these are the skills you really need

Technical skills are not the only thing businesses need. Increasingly, employers
are looking for candidates with the qualities and attributes that can bring
teams together, make them more productive, and help companies navigate a work
landscape that can change at a moment's notice: qualities that have proven
indispensable in getting employers through the tumult of the COVID-19
pandemic. ... According to the recruitment specialist, tech workers,
particularly at middle and senior levels, are now expected to be business
partners, and as such they need to be able to clearly communicate their
strategies, activities and the impact of those on the wider business. This means
good communication skills and interpersonal skills are more valuable than ever –
particularly for companies that have had to adopt or scale out digital solutions
quickly in response to pandemic-era working. "There are businesses out there
that are tech businesses now that perhaps weren't before," says Phil Boden,
Robert Half's director of permanent placement services, technology.
Is Storage-as-Code the Next Step in DevOps?

“Large storage teams and IT organizations are looking to move into this kind of
model,” he said. “People are excited to get out of that drudgery piece and build
something as code.” And while developers aren’t the decision-makers or the
budget holders for the storage market, Ferrario says, they are also a key
influencer audience. “The IT developer knows they are responsible for building
and automating their own infrastructure services,” he said. “And while they
don’t hold the purse strings, they are the executors.” This is a logical trend
to follow the popular Kubernetes abstraction, Ferrario said; there’s a
widespread demand for infrastructure to be generic enough for everyone to access
what they need to build, without having to bug infrastructure engineers all the
time. Move faster, with guardrails and policy in place. “If you look at the
origin of the cloud operating model years ago, the infrastructure that you as a
developer or app owner need is on-demand — and you don’t have to worry about
what’s going on behind the scenes,” Ferrario said. But when it’s on-premises,
the process is still manual. “You need that Infrastructure-as-a-Service in
place, with policy definition and so on.”
3 ways building digital acumen can impact business success

Seeking to build digital acumen skills across the organization has provided
several opportunities for cross-functional career moves and peer mentoring. Our
IT colleagues are taking opportunities to lead and hone the soft skills they
need today, like design thinking and agile working methods. In our manufacturing
plants, for instance, digital procedures help to minimize the potential for
human error because they strengthen our work processes and improve reliability.
This data is vital to making timely decisions, whether someone is performing
maintenance or an inspection. Our IT team is teaching plant employees how to use
those tools because they play a critical role in developing the capabilities and
maintaining them in the long term. With 130 different manufacturing sites with
multiple plants at each site and tens of thousands of procedures, it has a key
impact on productivity and reliability when employees have digital skills on the
field versus needing to rely on the IT organization. Other areas in which our IT
team is helping to build digital acumen include sales, marketing, and public
affairs.
Can't Fight That REvil Ransomware Feeling Anymore?
None of REvil's likely now-former, core members appear to have been brought to
justice. Perhaps that's because they reside in Russia, which has historically
ignored cybercrime, provided the criminals never hack Russia or its neighbors,
as well as do the occasional favor in return. The new version of REvil's
business plan may simply be to bring that name recognition to bear as the
group attempts to scare as many victims as possible into paying a seven-figure
ransom. The ideal scenario for criminals is that victims pay, quickly and
quietly, to avoid news of the attack becoming public, which helps attackers by
making their efforts more difficult for law enforcement agencies to trace. If
the ransomware group now using the REvil brand name can keep the operation
afloat for even a month before again getting disrupted by law enforcement
agencies, its members stand to make a serious profit, so long as they remain
out of jail long enough to spend it. Unfortunately, the odds are on REvil
Rebooted's side.
9 most important steps for SMBs to defend against ransomware attacks

Investigate whether you can retire out of date servers. Microsoft recently
released a toolkit to allow customers to possibly get rid of the last Exchange
Server problem. For years the only way to properly administer mailboxes in
Exchange Online where the domain uses Active Directory (AD) for identity
management was to have a running Exchange Server in the environment to perform
recipient management activities. ... The role eliminates the need to have a
running Exchange Server for recipient management. In this scenario, you can
install the updated tools on a domain-joined workstation, shut down your last
Exchange Server, and manage recipients using Windows PowerShell. ...
Investigate the consultants and their access. Attackers look for the weak link
and often that is an outside consultant. Always ensure that their remote
access tools are patched and up to date. Ensure that they understand that they
are often the entry point into a firm and that their actions and weaknesses
are introduced into the firm as well. Discuss with your consultants what their
processes are.
Delta: A highly available, strongly consistent storage service using chain replication
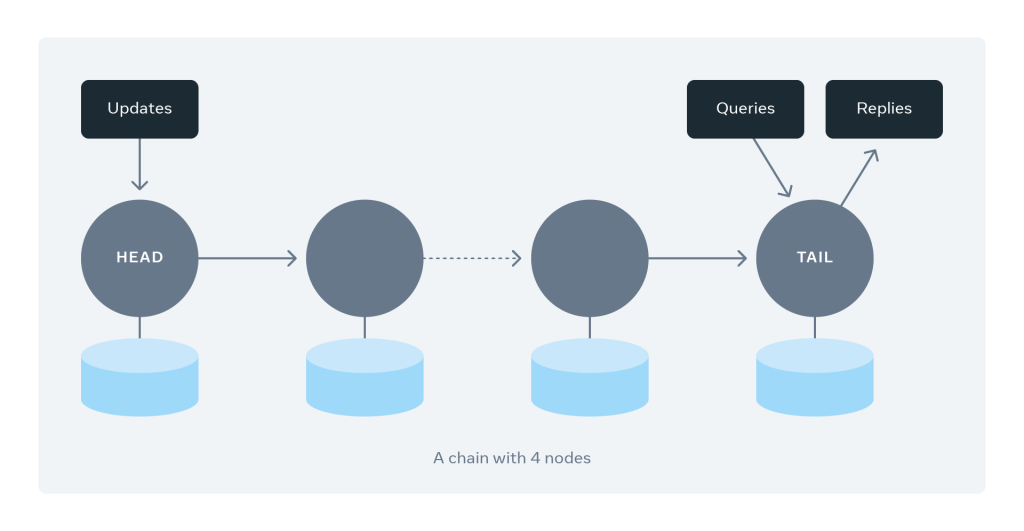
Fundamentally, chain replication organizes servers in a chain in a linear
fashion. Much like a linked list, each chain involves a set of hosts that
redundantly store replicas of objects. Each chain contains a sequence of
servers. We call the first server the head and the last one the tail. The
figure below shows an example of a chain with four servers. Each write request
gets directed to the head server. The update pipelines from the head server to
the tail server through the chain. Once all the servers have persisted the
update, the tail responds to the write request. Read requests are directed
only to tail servers. What a client can read from the tail of the chain
replicates across all servers belonging to the chain, guaranteeing strong
consistency. ... Delta supports horizontal scalability by adding new servers
into the bucket and smartly rebalancing chains to the newly added servers
without affecting the service’s availability and throughput. As an example,
one tactic is to have servers with the most chains transfer some chains to new
servers as a way to rebalance the load.
Leaving cloud scalability to automation
The pushback on automated scalability, at least “always” attaching it to
cloud-based systems to ensure that they never run out of resources, is that in
many situations the operations of the systems won’t be cost-effective and will
be less than efficient. For example, an inventory control application for a
retail store may need to support 10x the amount of processing during the
holidays. The easiest way to ensure that the system will be able to
automatically provision the extra capacity it needs around seasonal spikes is
to leverage automated scaling systems, such as serverless or more traditional
autoscaling services. The issues come with looking at the cost optimization of
that specific solution. Say an inventory application has built-in behaviors
that the scaling automation detects as needing more compute or storage
resources. Those resources are automatically provisioned to support the
additional anticipated load. However, for this specific application, behaviors
that trigger a need for more resources don’t actually need more
resources.
Ethernet creator Metcalfe: Web3 will have all kinds of 'network effects'
Metcalfe is still refining his pitch for his Law and learning at the same
time. "There are going to be all kinds of network effects in Web3," said
Metcalfe, during an informal gathering in Williamsburg, Brooklyn, on the
sidelines of The Knowledge Graph conference, a conference where enthusiasts of
knowledge graphs share technology and techniques and best practices. "For the
first time, I am trying to say exactly what kinds of value are created by
networks," Metcalfe told ZDNet at the Williamsburg event. "What I have learned
today is that knowledge graphs can go a lot farther if they are
decentralized," said Metcalfe. "The key is the connectivity." Earlier in the
day, Metcalfe had given a talk at the KGC main stage, "Network Effects in
Web3." In the talk, Metcalfe explained that "networks are valuable," in many
ways. They offer value as "collecting data," said Metcalfe, the ability to get
data from many participants. There was also sharing value, sharing disk
drives, say, or sharing files. Netflix, said Metcalfe, has "distribution value
— they distribute content and it's valuable."
NOAA seeks input on new satellite sensors and digital twin

“The ultimate goal is to improve the forecast skills of NOAA,“ Sid Boukabara,
principal scientist at NOAA’s Satellite and Information Service Office of
System Architecture and Advanced Planning, told SpaceNews. “These technologies
have the potential to take us a leap forward in our ability to provide good
data to our customers.” Gathering data in the microwave portion of the
electromagnetic spectrum is a key ingredient of accurate weather forecasts.
NOAA currently relies on the Northrop Grumman Advanced Technology Microwave
Sounder, which gathers data in 22 channels, flying on polar-orbiting weather
satellites. Future microwave sounders could “sample at a much higher spectral
resolution and would have potentially hundreds of channels,” Boukabara said.
“By having a lot more channels, we will be able to better measure the
temperature and moisture in the atmosphere.” Measuring the vertical
distribution of atmospheric wind from space is another NOAA goal. For now,
meteorologists determine wind direction and intensity by observing the motion
of moisture in the atmosphere.
4 Database Access Control Methods to Automate

The beauty of using security automation as a data broker is that it has the
ability to validate data-retrieval requests. This includes verifying that the
requestor actually has permission to see the data being requested. If the
proper permissions aren’t in place, the user can submit a request to be added
to a specific role through the normal request channels, which is typically the
way to go. With automated data access control, this request could be generated
and sent within the solution to streamline the process. This also allows
additional context-specific information to be included in the data-access
request automatically. For example, if someone requests data that they do not
have access to within their role, the solution can be configured to look up
the database owner, populate an access request and send it to the owner of the
data, who can then approve one-time access or grant access for a certain
period of time. A common scenario where this is useful is when an employee
goes on vacation and someone new is helping with their clients’ needs while
they are out.
Quote for the day:
"A positive attitude will not solve
all your problems. But it will annoy enough people to make it worth the
effort" -- Herm Albright
No comments:
Post a Comment