Want to build a relationship with your CIO? 5 things you shouldn't do

Increasingly, CIOs are tasked with the adoption and orchestration of many
technology platforms that influence digital transformation and enable the
business strategy. This adoption involves a delicate balance of ensuring
adequate guardrails exist through technology and security governance, while at
the same time striving for speed and agility. When an employee develops a
reputation for being a blocker, it starts to create an adversarial relationship
between the business and IT. That often leads to shadow IT, in which employees
start going around the IT or information security departments to get things
done. Certainly, IT and information security need to have a strong voice in
highlighting risks or technical barriers, but it’s equally important that we do
our best to be solution-oriented, finding creative ways to make technology work
for the business and implementing it securely. When an employee becomes a
chronic blocker to business objectives and every issue becomes an immovable
object, it undermines the trust and collaboration that the CIO is working to
promote with the business.
In search of elegance

Unfortunately, many respond to complexity by increasing complication—and thus
increasing inelegance—through extensive bureaucracy with a rule for every
contingency. Instead, leaders would be wise to pursue elegant simplicity: the
fewest rules possible or, even better, a few rock-solid principles. This
enables and empowers individuals and teams to quickly respond to the dynamism
inherent in complexity. For example, look at Netflix’s five-word expense
policy—“Act in Netflix’s best interest”—or Metro Bank’s customer service
principle that requires only one person to say “yes” to a customer request,
but two to say “no.” Authors Marc Effron and Miriam Ort, in their book, One
Page Talent Management: Eliminating Complexity, Adding Value, argue,
“Simplicity plays to basic human desires and cognitive processes. We crave
it.” Insisting on simplicity rewards concise, coherent thinking and action;
elegance recognizes and works with our core humanity. How better to engage and
energize your workers? A fundamental challenge for leaders today is to reset
and refocus their organizations to move with hope and confidence into an
uncertain future.
Utilizing biological algorithms to detect cyber attacks

A standard approach to addressing spoofed domains is to compare them to a
database of known domains and to look for differences. When an email arrives,
the cybersecurity solution counts the number of changes between the attacker’s
signature and each instance in the known domain database. If there are a few
changes, the domain is deemed suspicious. Measuring the number of changes
between two sequences in this traditional way is done via the Levenshtein
distance. While this technique works in some instances – such as when it detects
a spoofed domain like m1crosoft – it struggles to identify more significant
obfuscations such as MlCR0S0FT (with an “L” in place of an “I” and zeros in
place of the letter “O”). The Levenshtein distance metric also finds it
challenging to distinguish between microsoft-support and a microsoft domain.
Since the traditional method is sometimes insufficient in detecting phishing
scams, researchers have turned to nature and to a method called biomimicry.
The Machines Are Coming: Financial Services Can Reduce the Blast Surface with Zero Trust

While the financial services industry has always been an attractive target
for hackers, the impact of how work has changed during COVID-19 has raised
the stakes even higher. Research done with UK-based IT and security
professionals points out that most believe COVID-induced work-from-home
practices and remote work are accelerating attack risks in the financial
services industry. I’m sure no one was surprised by these revelations, given
the attractiveness of financial services data, such as customer records and
personally identifiable information…let alone the ability to actually steal
money and other financial assets. Many of us also know that cyber thieves
are using “machines” to do their dirty work, such as automated attack tools,
as well as artificial intelligence and machine learning algorithms. Another
challenge is that our industry has an increased use of what I call
“ephemeral computing,” such as cloud services and on demand technology
services. While cloud is arguably more secure than any single organization’s
data center, misconfigurations and oversight can leave an organization’s
crown jewel data exposed in public, as we’ve seen with an increased number
of highly public stories.
Using Patterns to Drive a Transformation towards Agility
Looking at stories like the one outlined before, a pattern becomes visible:
adaptability is mainly about organisational capabilities like situational
awareness, clear alignment and focus on goals, and the ability to react fast
to changes and to learn and improve and to deliver customer value
constantly. Practically, there are many ways this can be accomplished. There
is not “the one” blueprint that fits all organisations because much depends
on the business, the environment, the evolution, and last but not least, the
culture. This key insight triggered the idea to work on the travel guide for
growing an adaptive organisation to give guidance, inspiration, orientation
and ideas for experimenting in your concrete context so that you can find
out what works for you - every transformation journey is different in the
end. The idea of the travel guide is, that while we cannot give people a
recipe for doing an agile transformation, we can share the transformation
journeys we have lived through and show emerging success patterns that can
guide others in their journey.
An Introduction to Bluetooth Mesh Networking
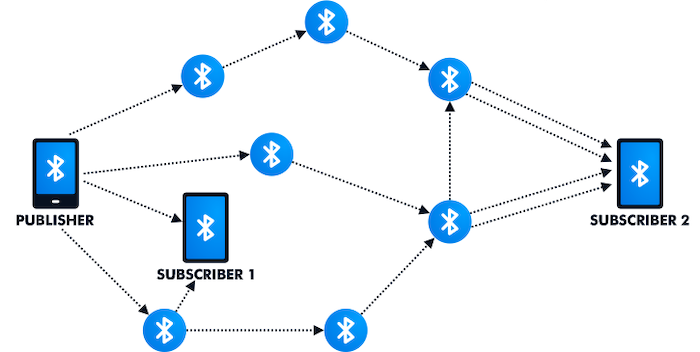
Since the nodes in a mesh can act as repeaters, the range of the network
can be extended beyond that of a single radio. Due to these advantages,
wireless communication protocols that are designed for IoT applications
have included mesh networking capability in their standards to enable
scaling the network geographically through multi-hop operations. ... Many
basic features of mesh networking are supported by all of these three
protocols. For example, they all include the ability to self-heal, meaning
that if a node is disabled or removed, the network reconfigures
automatically to repair itself. However, there are major differences
between these protocols. For instance, Bluetooth mesh uses a technique
known as managed flooding to route data packets through the network where
messages are simply broadcast to all nearby nodes, while Zigbee and Thread
use the full routing technique in which. a specific path is chosen for the
messages going from node A to node B. Such differences can have a
significant impact on the network performance depending on the application
requirements and conditions. Evaluating certain aspects of the Bluetooth
mesh technology, such as the network latency, reliability, scalability,
etc., might not be straightforward in some cases.
How retail is using digital twins
The biggest takeaway is how digital twins make it easy to visualize
complex relationships between physical things, including product
placement, physical customer journeys and the paths robots might take
down store aisles for inventory and floor cleaning. Managers and staff
can explore how layouts, schedules, team movements and customer journeys
interact in one visualization tool. They can also visually assess the
impact of a new store layout, schedule or technology might impact
cleaning, restocking and staffing requirements. Digital twins also have
the potential to improve customer experiences in various ways. They
could help customers connect the dots between home improvement projects,
required materials and materials costs. They could also help improve
physical customer journeys within stores by organizing the order
shopping lists to line up with a route through the store. ... Emerging
tech like digital twins, mixed reality and computer vision help capture
data about the home and keep track of all the details to reduce this
friction. The Lowe’s app takes advantage of the lidar built into the
latest iPhones to capture home measurements quickly.
The Black Swan Events in Distributed Systems
When a system is asked to do more work than it possibly can, something
is eventually going to fail. Maybe the CPU usage is very high that it
has become the bottleneck and user requests start to time out suggesting
the users that system is down. Or maybe the disk space has become the
bottleneck and system can not store any more data. In a normal system
overload case, if the source of load or trigger is removed, the problem
goes away and everything sets back to normal state or stable state.
... Once we put a blocklist to stop the traffic from offending IP
addresses, the trigger will go away , load on the network returns back
to normal , user traffic begins to go through and the system comes back
to its stable state. It’s hard to prevent such overloading incidents
but, usually easy to recover from them. There’s another class of
overloading incidents that are much harder to resolve, where the system
does not recover back to its stable state by just removing the initial
trigger These incidents can cause system outages down for a long period
of time, it could be hours or even days in some cases. This class of
incidents that continue to keep going even after the initial trigger has
been removed are called metastable failures.
Citrix® Modernizes Security to Accommodate Hybrid Work
Citrix Secure Private Access is a cloud-delivered, ZTNA solution that
provides contextual access to IT-sanctioned applications whether they
are deployed on-prem, or in the cloud and delivers security controls
for managed, unmanaged and BYO devices. Using the solution, IT
organizations can: Provide zero trust network access to all apps, with
adaptive authentication to continually evaluate access based on end
user roles, locations, device posture, and user risk profiles.
Securely support distributed work and BYO programs without risking
exposure to malicious content and web-borne threats.
Simplify IT
while enhancing the digital workspace experience for users. They can
also enact a fresh approach to security that accommodates the
realities of work today by giving employees the flexibility to work
where they want using the devices of their choice, while ensuring that
corporate data and assets remain safe. And many already are. Take HDI
Global. With a rapidly growing work-from-home staff in Brazil, the
international insurance company had a choice to make: increase
investments in traditional servers and virtual machines, or enact a
more modern approach to securely delivering apps.
Generations in the Workplace: Stereotypes and Facts
According to this report, ingrained stereotypes about age are actually
far more likely to damage an IT team than failing to account for
generational differences. It says, “What might really matter at work
are not actual differences between generations, but people’s beliefs
that these differences exist. These beliefs can get in the way of how
people collaborate with their colleagues and have troubling
implications for how we people are managed and trained.” That's not to
say that there are not some true differences among the generations.
For example, when you look at the age when people get married (or if
they get married at all), you will spot some notable disparities among
various age groups. But those disparities might be smaller than you
think. And even if many people in an age category share a particular
trait, it doesn't mean that every person you work with from that
category will have the characteristics you expect. So how should IT
managers handle teams with members of varying ages? A good way to
start is by examining your own attitudes to see if you are being
shaped by prevailing opinions.
Quote for the day:
"Listening to the inner
voice trusting the inner voice is one of the most important
lessons of leadership. " -- Warren Bennis
No comments:
Post a Comment