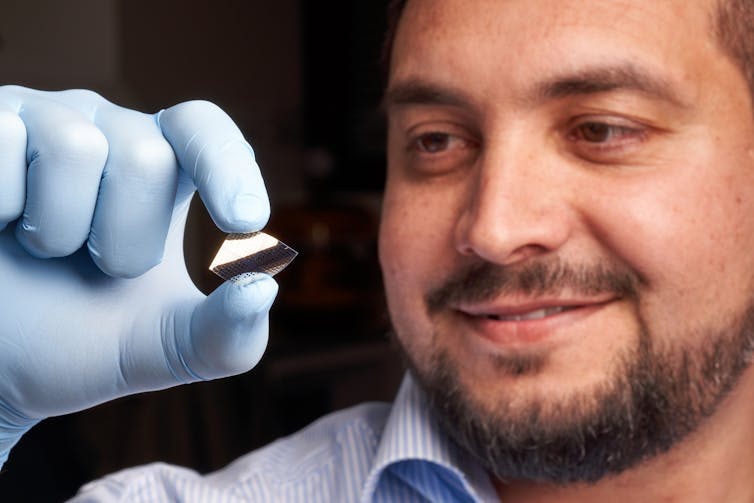
Being able to replicate neural behaviour on an electronic chip also offers exciting avenues for research to better understand the brain and how it is affected by disorders that disrupt neural connections, such as Alzheimer’s disease and other forms of dementia. The human brain is made up of billions of neurons in connected networks. They communicate with each other by using a sequence of electrical signals to express different behaviours, such as learning through sensory organs or more complicated processes like emotions and memory. Any disruption to these signalling sequences can lead to a loss of these vital neural connections, potentially causing memory loss and dementia. Curing these disorders would require identifying the faulty neurons and restoring their signalling routine, without affecting the functioning of other neurons in the network. So by having a computer model of the brain, neuroscientists would be able to simulate brain functions and abnormalities, and work towards cures, without the need for living test subjects. Our technology could also potentially be incorporated into wearable electronics, bionic prosthetics, or smart gadgets imbued with artificial intelligence.
Securing Our Infrastructure: 3 Steps OEMs Must Take in the IoT Age
In the manufacturing world, specifically the operations technology (OT) sphere, legacy operational standards such as OPC and Modbus are still in use today but were designed more than 20 years ago using old technologies, including COM. They were not designed for communication over modern IP networks with multiple security layers and, due to a general lack of cybersecurity sophistication, traditional OT networks have most security options disabled to simplify configuration. By its nature, a large open network of connected devices opens many new attack vector threats, even if individual devices may be secure when used independently. Because the weakest point in the system determines its overall security level, a comprehensive end-to-end approach is required to secure it. The lack of industry standards within the manufacturing space makes it difficult to develop such an approach because hackers concentrate on breaching a specific element within the technology stack.
Ransomware has evolved into a serious enterprise threat

In addition to a ransomware revival, the report highlights that more than 2.2 billion stolen account credentials were made available on the cyber criminal underground in the first quarter and that 68% of targeted attacks used spear phishing for initial access. “This shows how the cyber crime economy works,” said Samani. “Credentials are sold online, other criminals buy the credentials and then use them to get into organisations and use the ransomware they are an affiliate for to infect an organisation and demand tens of thousands of dollars in ransom. “The purpose of the threat report is not just to give the hard stats, but to encourage organisations to look at everything that is going on and see it is all connected and contributes to the wider ecosystem of crime.” The findings on ransomware targeting businesses are consistent with the fact that ransomware and other forms of cyber extortion are currently the most popular forms of cyber criminal activity in the UK, according to Rob Jones
The World Is Taking The Future Of Payments Seriously. Why Isn't The United States?

Let’s start with the simplest of the three: technological history. When modern-day payment systems were first developed, the United States was at the forefront of innovation and adoption. Debit and credit cards picked up significant momentum in the second half of the twentieth century. While shopping and paying online are now a global standard, it took time to filter into society. At the center were the thousands of e-commerce websites and companies that developed in the United States, particularly in Silicon Valley, in the late 90s and early 2000s. In the United States, all cards operate on the same point-of-sale systems to streamline the process for merchants. These outdated systems have left debit and credit cards as the historic standard, which is difficult to break out of. Point-of-sale systems have made China a fascinating case study. Historically, China has been slow to embrace new technologies, particularly in the consumer sector. Until about 10 years ago, the majority of transactions were made with cash; credit and debit cards were relatively rare in China’s payment ecosystem. When payment alternatives started to develop, it was roughly around the same time smartphones began to flood the market.
Do Self-Service and Low-Code Curb Shadow IT?

It’s important to point out there's an entire spectrum of low-code/no-code tools aimed at different audiences. Some are targeted at professional developers while others are targeted to web developers or citizen developers. The latter group tends to use “no-code” tools because the mechanics of writing code have been abstracted into visual drag-and-drop tools. Fintech company NES Financial standardized on Outsystems, which is an enterprise-class low-code platform because NES Financial voluntarily complies with Systems and Organizational Controls reporting (SOC 1), the Bank Secrecy Act (BSA), United States Citizenship and Immigration Service (USCIS) and Securities Exchange Commission (SEC) regulations. "Building systems and controlling data is an art in itself. You have to be aware of new regulations, requirements, and constraints, which is a full-time job," said Izak Joubert, CTO at NES Financial. "I think the ability for a marketing organization to implement something as a shadow IT organization is great conceptually, but it has massive risks for an organization if you look at it from a bigger perspective."
Tracking The Trajectory Of Cloud Computing

Despite the lack of coherent regulations, clients can use the cloud with confidence provided they know where their data is kept, which data protection laws apply, and whether the provider meets internal security policy. The cloud is multi tenancy by design – in other words, it brings lots of clients and third parties into the same network. Knowing which other organisations exist within the network, and how much data they will be able to access, is also a good move for service users. Cloud computing is changing: it’s smarter, faster, more powerful, and more popular than ever before. As technologies and industries converge, cloud applications will increase. However, the maturity of cloud computing has not been matched by regulations. Users are often uncertain about cloud compliance, and therefore less willing to rely on cloud based systems. Legal bodies and corporations need to come up with a prescriptive regulatory framework to enable the cloud to rise to its full potential.
Mitigating social engineering attacks with MFA

Providing a tool for employees to report phishing incidents, even just an email address for forwarding suspected phishing emails, can also help organisations. ... One technological solution that has proven successful against social engineering attacks, especially when the goal has been for acquiring access details, is the implementation of two-factor authentication. Two-factor authentication (2FA), and multifactor authentication (MFA), are access management systems that require two – or more – pieces of evidence, whether it be knowledge (such as passwords), possession (a physical token for example) or inherence (eg fingerprints) in order for access to be granted. The reason that 2FA/MFA is so successful is that should one of their verification stages (such as a password) become compromised, a hacker will still be unable to gain access to the organisation’s network without the other pieces of authentication.
Creating a 'Defensible' Cybersecurity Program
Business units also need to have input on the security steering committee to ensure that the security team is aligned with business goals. "It's very difficult to convince people that you are governing your security program from a business perspective if the business does not have a seat [on the steering committee]," Scholtz says. Dashboards or scorecards can be helpful for showing how security relates to the business and what the risk position is, Scholtz says. But implementing those takes time. Progress reports for executive boards can be tricky, Scholtz says. Executives don't need day-to-day operational information. Providing too much information may get executives interested in granular details that they ultimately have no control over, he points out. Scholtz's tips seem to offer a helpful start for setting up a cybersecurity program that supports business goals. But are they, indeed, practical? Let us know what you think.
Blurring the lines between RPA platforms and APIs

The capabilities of both RPA platforms and APIs are evolving to support use cases primarily handled by the others. The combination of RPA and APIs is a natural outgrowth of the modern business systems environment, particularly driven by the adoption of SaaS platforms and API-first becoming the new software mantra. Traditionally, RPA has been marketed to work with the complex mix of legacy, third-party and modern business applications that most organizations have accumulated. When delivering an RPA platform, it is nearly always best to use APIs when available, as the combination of these technologies delivers an extensive and change-resistant experience by removing the inherent change-prone UI layer from the equation. "Counter to what some may assume, the existence of an API does not negate the usefulness of RPA," Cottongim said.
A new IOT botnet is infecting Android-based set-top boxes
In a report published today and shared with ZDNet, WootCloud Labs said Ares operates by randomly scanning the internet for Android devices with open ADB ports. When it finds a vulnerable device, the Ares operators download a version of the Ares malware on the exposed device, which then acts as another scanning point for the Ares operators. Ares-infected devices will scan for both other Android systems with open ADB ports, but also for devices running Telnet services, specific to Linux-based servers and smart devices. While Ares operators are obviously trying to infect any device they can, WootCloud said it's seen the botnet infecting set-top boxes from HiSilicon, Cubetek, and QezyMedia. These attacks started in July, Srinivas Akella, Founder & Chief Technology Officer of WootCloud, told ZDNet in an email today. The exec also doesn't exclude the possibility that other types of Android systems were also infected. "To protect against the ADB being misused in these cases where it is left enabled, routers can be configured to block the ingress and egress network traffic to TCP port 5555, which is the ADB port," Akella said.
Quote for the day:
"Enthusiasm is excitement with inspiration, motivation, and a pinch of creativity." -- Bo Bennett
No comments:
Post a Comment