Digital Transformation: Are you digitally distraught or digitally determined?

Online orders are rarely a roadblock in B2B sales. The challenge of self-service lies in presenting complex product information and pricing in a system that’s fast, intuitive and capable of recommending the best solutions for a given customer. Businesses often buy products from manufacturers with varied configurations, order sizes and contract terms. Seemingly similar deals can vary in significant ways, and market prices in B2B aren’t always visible. Nonetheless, buyers expect to find pricing information as easily as they might look up product specs online. ... An online B2B purchase is likely to involve pricing algorithms, product databases, chatbots, market data, automated email and detailed customer profiles built across marketing, sales and support. AI can help instantly identify the optimal next steps for customers by analysing thousands of data points gathered during this process. Customers already expect companies like Netflix and Amazon to anticipate what they need. The same will soon be true of product configurations, add-ons and services. As online transactions become the majority of manufacturers sales, successful implementation of AI will become critical to success.
How industry cloud technology is changing healthcare

There is a role for both large providers and smaller ones to help the healthcare sector make the digital transition. Large cloud computing providers have superior computing power, but not the industry expertise and dedicated support to work with healthcare clients, according to Gartner analysts Gregor Petri and Anurag Gupta. This creates a significant opportunity for managed service provider partners. Smaller cloud computing providers can work with Amazon and Microsoft to build and deliver services while establishing direct relationships with healthcare stakeholders. Smaller providers also can help with implementation and ongoing management of cloud-based applications. In addition, these providers can use HIPAA expertise to satisfy the regulatory requirements that healthcare providers must meet. For Phil Misiowiec, the Chief Technology Officer of Healthcare Blocks, most of his clients already have a cloud strategy in place when they contact him. Systems being deployed to the Healthcare Blocks platform fall into one of three buckets, Misiowiec said
Why the road to 5G might be longer than expected

"From a consumer's perspective, there will certainly be a transition period," Mark McCaffrey, PwC's US technology, media, and telecommunications leader, told TechRepublic. "We won't simply go from 4G/LTE to 5G overnight and a 5G network won't necessarily be maximized with a device meant for 4G. And as 5G is a new technology, we can expect there to be bugs and glitches that need to be worked out along the way." Creating a 5G network comes with a whole new set of roadblocks that didn't exist when creating 4G, according to the report. This higher density network brings regulatory, cost, and operational challenges. "The biggest hurdles to 5G are simply logistical ones. To get to the point of widespread adoption on any scale, we must solve regulatory and infrastructure issues," said McCaffrey. "Each federal, state and local community may have unique requirements in its deployment of 5G. All carriers and equipment manufacturers will need to develop their own path to 5G deployment that meets the regulatory requirements including cybersecurity." 5G implementation also requires hundreds of thousands of small cells to be installed across the country, which calls for large bands of spectrum that aren't yet available, the report found.
Five examples of user-centered bank fraud
SMS swapping has become quite common in the banking industry. First, the attacker steals a victim’s private phone number, along with the phone’s Security ID. Then the attacker calls the SIM card call center claiming they lost their phone, have bought a new SIM card and now need to get their old number back. Using the Security ID and other private information, possibly gathered from snooping on social media accounts, they convince the telecommunication support person to perform the phone swap. This scam can even evade security protections. Most banking institutions that offer multi-factor authentication (MFA) to protect online banking sessions and applications rely on SMS-based MFA instead of using mobile tokens. Once hackers steal people’s phone numbers, they have access to these SMS messages. That means they can access the victim’s account even if it has SMS-based MFA in place. Another old but effective tactic is the Man In-The-Middle (MITM) attack, in which attackers target banking platforms that do not adequately protect their infrastructure. This not only allows hackers to steal money, but also negatively affects the bank’s reputation by making their infrastructure seem fragile and vulnerable.
There have been many examples of seemingly well-prepared financial institutions caught off-guard by rogue units or rogue traders who weren’t properly accounted for in risk models. To that end, SR 11-7 recommends that financial institutions consider risk from individualmodels as well as aggregate risks that stem from model interactions and dependencies. Many ML teams have not started to think of tools and processes for managing risks stemming from the simultaneous deployment of multiple models, but it’s clear that many applications will require this sort of planning and thinking. Health care is another highly regulated industry that AI is rapidly changing. Earlier this year, the U.S. FDA took a big step forward by publishing a Proposed Regulatory Framework for Modifications to AI/ML Based Software as a Medical Device. The document starts by stating that “the traditional paradigm of medical device regulation was not designed for adaptive AI/ML technologies, which have the potential to adapt and optimize device performance in real time to continuously improve health care for patients.”
Black Hat: A Summer Break from the Mundane and Controllable
Security might be your job, but it's just one more additional thing for laypeople in your organization to worry about. Aside from clear mandates on the topic, compliance-driven requirements, or a recent "near-death" experience, most organizations are still balancing security needs with day-to-day pressing needs in order to win more customers and increase revenue. This is a good thing. Security is asking other people to improve the organization above and beyond what individual workers are held accountable for on a daily basis. It's important to understanding that this is the natural order and that security leaders are likely to encounter pushback on additional security controls. ... To make substantial progress on a security problem in a large 20,000-seat corporate environment you need technology. However, when the underlying risk decisions, business processes, and operations have not been addressed in a meaningful way, products only solve part of the problem and give security leaders a false sense of security.
Researchers Leigh-Anne Galloway and Tim Yunusov say they were able to manipulate two data fields that are exchanged between the card and the terminal during a contactless payment. This was done by using a proxy machine that manipulates the transaction data between the card and the payment gateway, essentially creating a man-in-the-middle attack, the researchers report. The researchers successfully tested a proxy machine with five U.K. banks, which they did not name. They discovered that the vulnerability is common to all Visa-issued contactless cards regardless of the bank and the locality of the person using the card, according to the blog. "Positive Technologies tested the attack with five major U.K. banks, successfully bypassing the U.K. contactless verification limit of £30 on all tested Visa cards, irrespective of the card terminal," the researchers note. The researchers say that an attack using the proxy machines can go through Google Pay by adding Visa to a digital wallet.
Cyber Warfare: Army Deploys 'Social Media Warfare' Division To Fight Russia
What's as interesting is the West's own use of the mainstream and social media to ensure that Russia and its proxies don't have it all their own way. We have always seen that battle for hearts and minds in the physical sphere. What we've started to see with news of cyberattacks on energy grids in Russia and command and control networks in Iran is the beginnings of the same in cyber. "State and non-state actors are continually seeking to gain an advantage in the grey zone that exists below the threshold of conventional conflict," as General Jones put it. And so, moving forward, you can expect much more of the same. "This restructuring is not the answer to everything," Ingram said, "and nor will or can it meet all current threats, but it is the first step in a journey and that first step gives a series of capabilities—and for the new division with psychological warfare in its structure, that rebranding is important in influencing future Army force development."
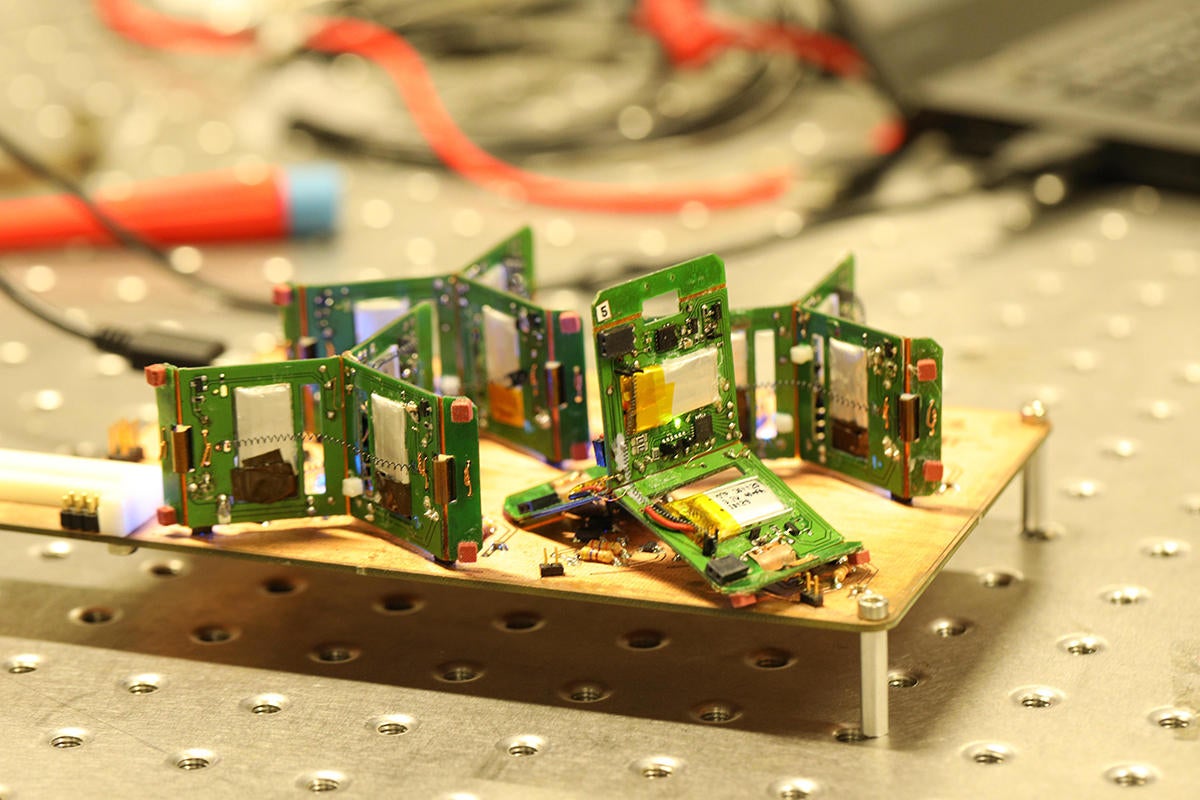
The robots already jump, and now they self-organize. The Swiss school’s PCB-with-legs robots, en masse, figure for themselves how many fellow microbots to recruit for a particular job. Additionally, the ad hoc, swarming and self-organizing nature of the group means it can’t fail catastrophically—substitute robots get marshalled and join the work environment as necessary. Ad hoc networks are the way to go for robots. One advantage to an ad hoc network in IoT is that one can distribute the sensors randomly, and the sensors, which are basically nodes, figure out how to communicate. Routers don’t get involved. The nodes sample to find out which other nodes are nearby, including how much bandwidth is needed. The concept works on the same principal as how a marketer samples public opinion by just asking a representative group what they think, not everyone. Ants, too, size their nests like that—they bump into other ants, never really counting all of their neighbors. It’s a strong networking concept for locations where the sensor can get moved inadvertently.
Forced to choose, my guess is most enterprises want the higher-order services from particular clouds more than they want that portability across clouds. The latter may appeal to accounting, but the former appeals to the teams tasked with driving agility and innovation within an enterprise. If you had to pick one of those teams to appease, pick the developers. Every. Single. Time. However, siding with developers doesn’t mean that an enterprise needs to cede control of its IT to a vendor. Rather, by going deep with a vendor, not only does that enterprise put itself in a position to develop more expertise with that cloud, but it also sets itself up as a VIP with that cloud. Anyone who has worked in enterprise software knows that while “all animals are created equal,” following Animal Farm logic, “Some animals are more equal than others.” Vendors always tend to listen to their most committed customers, and that “commitment” isn’t merely a matter of money. The cloud vendors, like all enterprise IT vendors, will tend to partner with those customers who help them to push the envelope on innovation and publish success stories (case studies, conference keynotes, etc.).
Quote for the day:
"It is better to be hated for what you are than to be loved for what you are not." -- André Gide



No comments:
Post a Comment